About
Quick write-up on the Anthem box, not going to go into huge detail but should be enough for people to be able to complete it.
Link: https://tryhackme.com/room/anthem
This is my first write up, any comments or questions are welcome.
Thoughs
Although this box is listed as easy it can be hard and frustrating, it took me a couple of extensions to work my way through it. The flags in Task 2 cost a few points as it was not clear which flag was which.
[Task1] Website Analysis
The following are basic CTF bits, if you do not know how to use NMAP and the basic ports used by services / operating systems then I suggest you go do the Beginner Learning Path
- Let's run nmap and check what ports are open.
- What port is for the web server?
- What port is for remote desktop service?
The below are bit more involved
- What is a possible password in one of the pages web crawlers check for?
What files do crawlers look for on a website ?
- What CMS is the website using?
You should be able to use the above file to find this
- What is the domain of the website?
This can found in the title of the website
- What's the name of the Administrator
This was a bit of PIA and took a while, few people have said the hint doesn't help. There is a post thanking the admin of the site which contains a poem, have a google of the poem.
- Can we find find the email address of the administrator?
Again there is a post where another employee lists their email address, use this format with the name you found above
[Task2] Spot the flags
The flags are hidden in the source code of the website, some in the body text and some in the meta data.
- What is flag 1?
- What is flag 2?
- What is flag 3?
- What is flag 4?
[Task3] Final stage
- Let's figure out the username and password to log in to the box.(The box is not on a domain)
This one took me longer than I'd like to admit but people re-use usernames and passwords. Users windows usernames are normally the first part of their emails in most orgs.
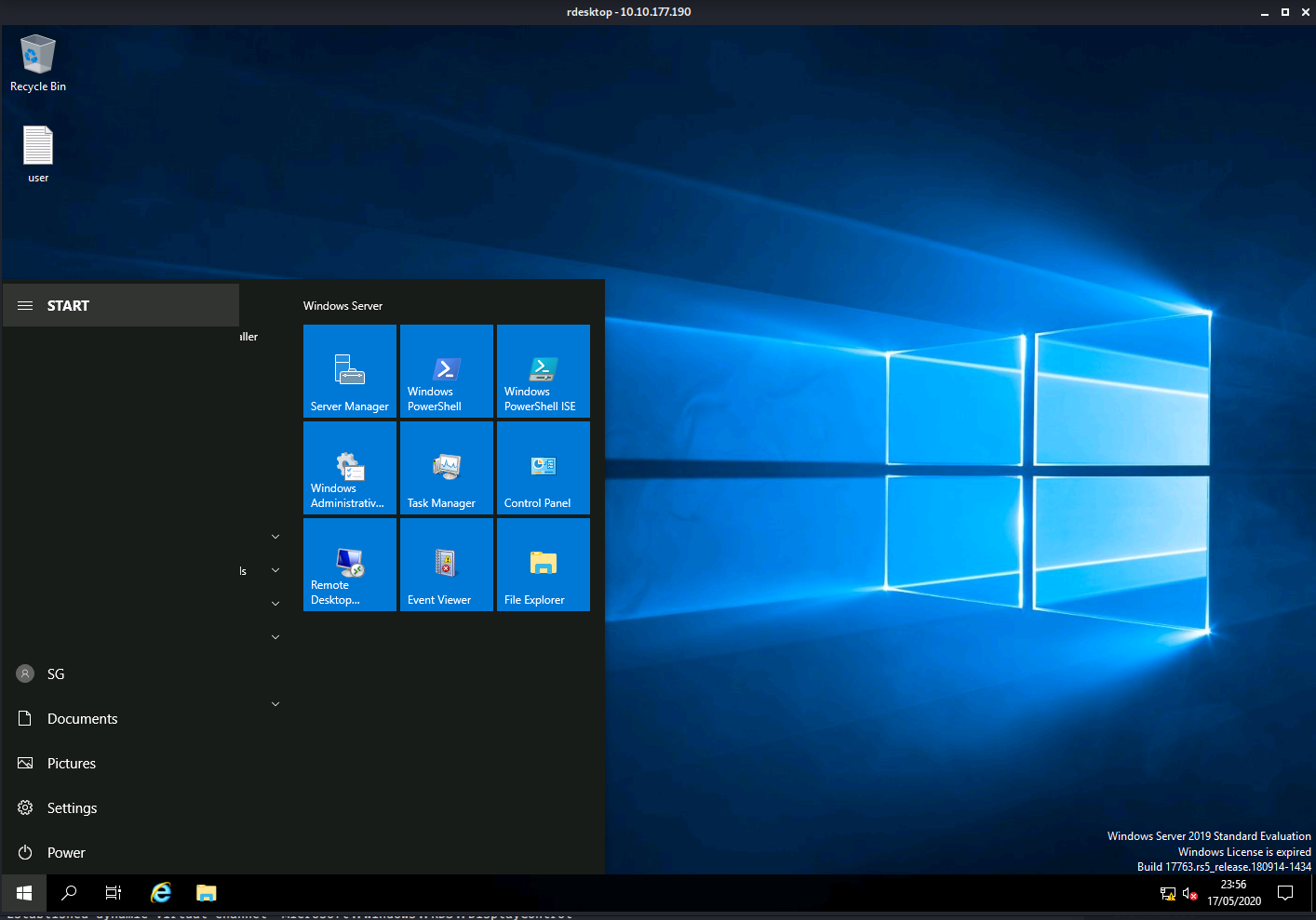
- Gain initial access to the machine, what is the contents of user.txt?
This is on the users desktop when you log in via RDP/SMB using the credentials above.
- Can we spot the admin password?
The file is in a hidden folder in the root of the C:\ drive, you will need to change the permissions of the file to read it though.
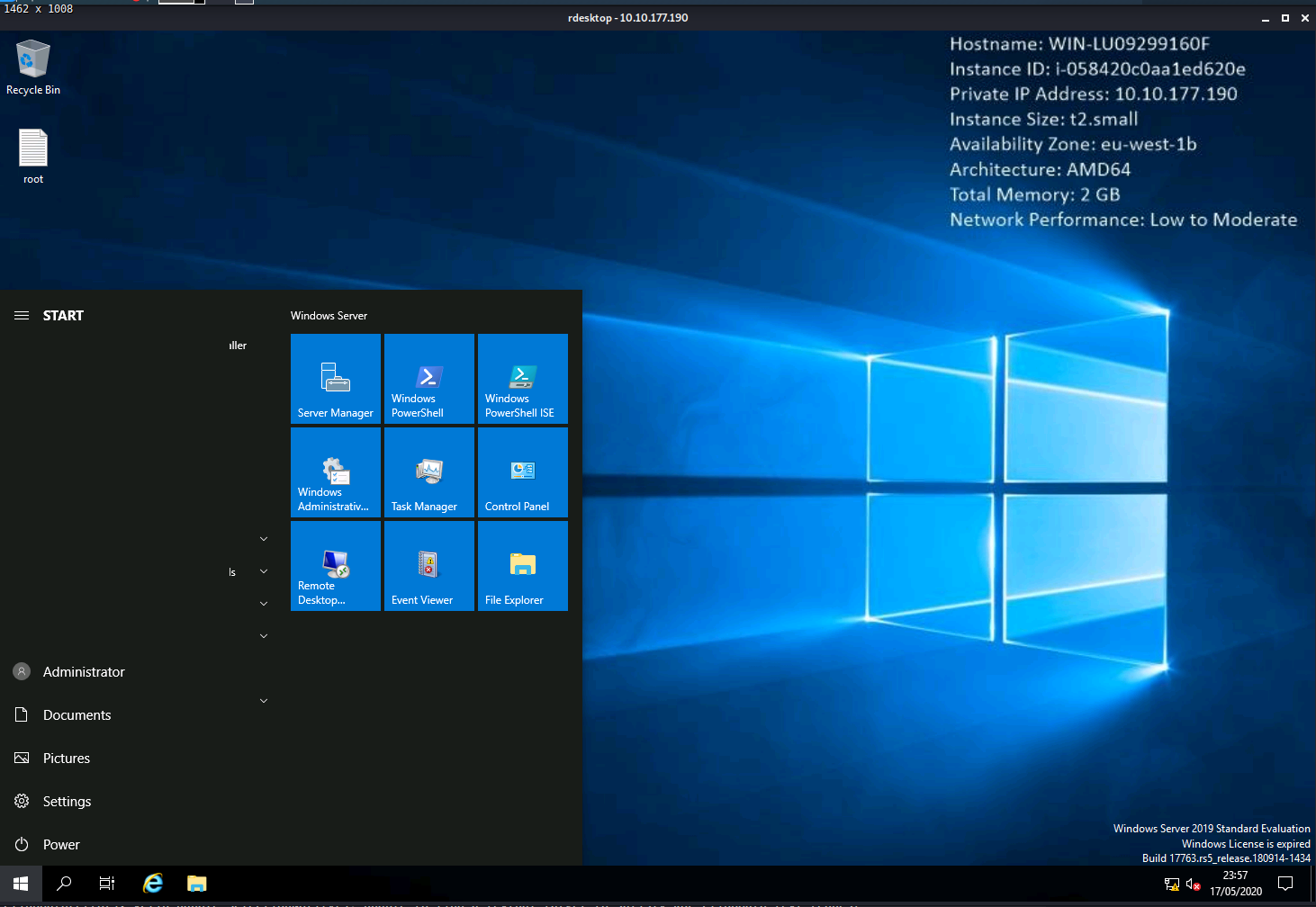
- Escalate your privileges to root, what is the contents of root.txt?
Again this is on the desktop once you log in as the Administrator